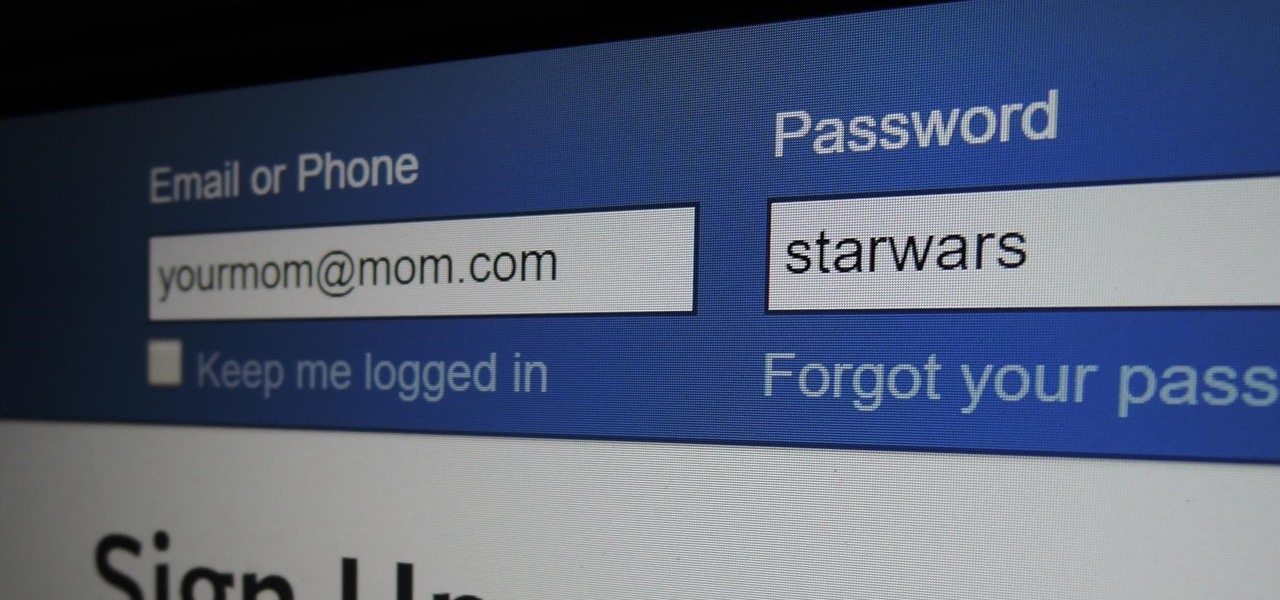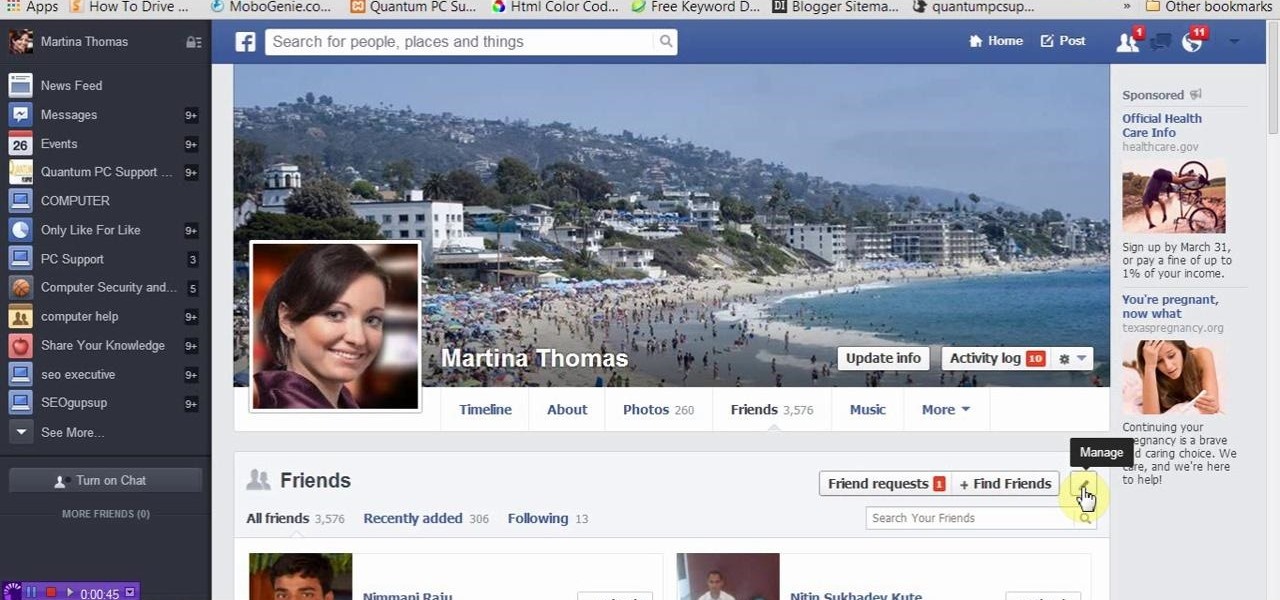
This tutorial video will show you how to hide Facebook friends list from public. With the help of this video you should restrict others from watching your Facebook friends list. Watch the video and employ the technique in your Facebook account.
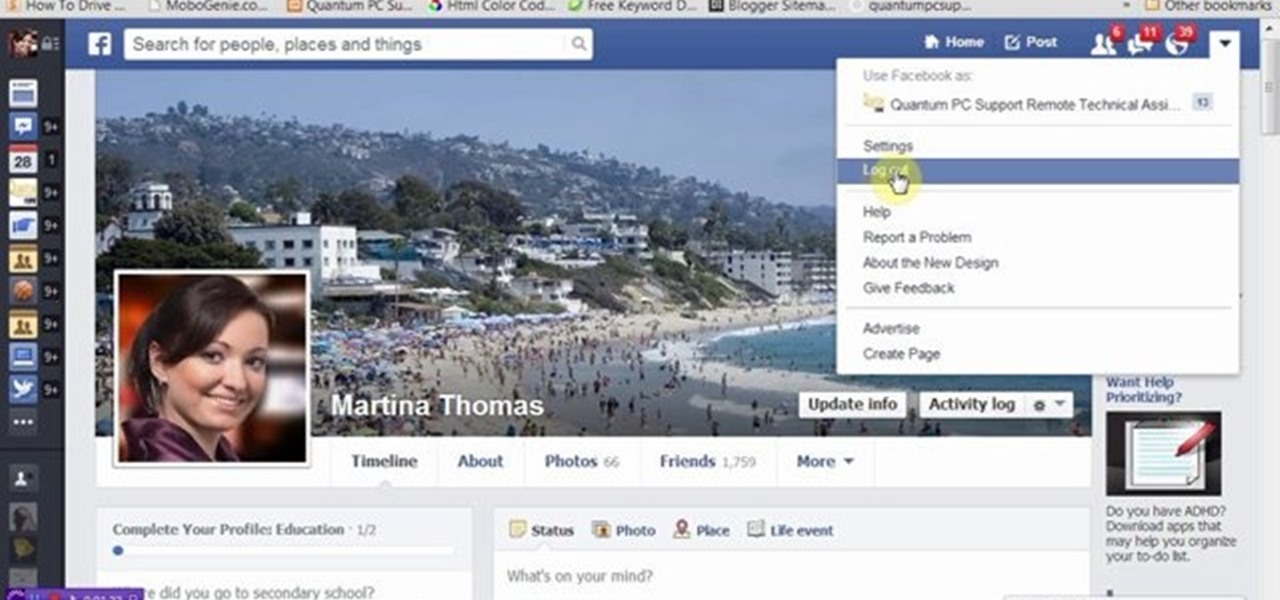
This video will provide an idea how you could hide your friend related information on Facebook and list from the public or your friends also. Especially the list is hidden from those who are not your friends in Facebook.
My standard text greeting to friends is something along the lines of "Wazzup biznitch?"—but apparently the auto-correct function on my Samsung Galaxy S3 has a problem with that. Time after time I have to retype it or just add all my made-up words to the word list—and I use a lot of made-up words, because that's what bosses do. But texting isn't the only way I communicate. I also use email, chat, and social media on a daily basis—and I don't always use my phone. So, wouldn't it be awesome if m...

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...
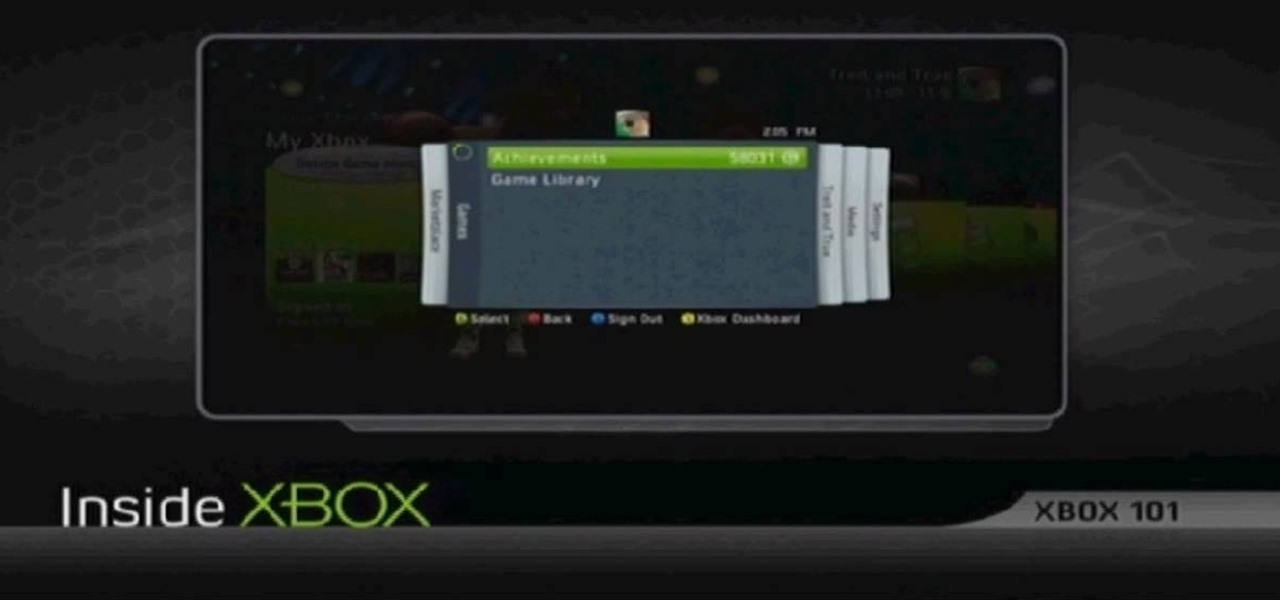
Learn how to delete the game history on your Xbox 360 from Ryan Treit in simple steps. You can get rid of the nasty unused game history from your Xbox 360 by following the steps below: 1. First go to your profile, press the guide button and then slide to the left one tab to Games and choose 'Achievements'. 2. Now a list of all the games you used will be displayed in order. 3. Select the game you wish to delete and press the X button and select 'Yes' to delete the game history. 4. Delete all t...

Internal linking is a valuable way to improve search engine optimization on your website or blog. This component of organic search engine optimization we going to focus on web copy threading.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

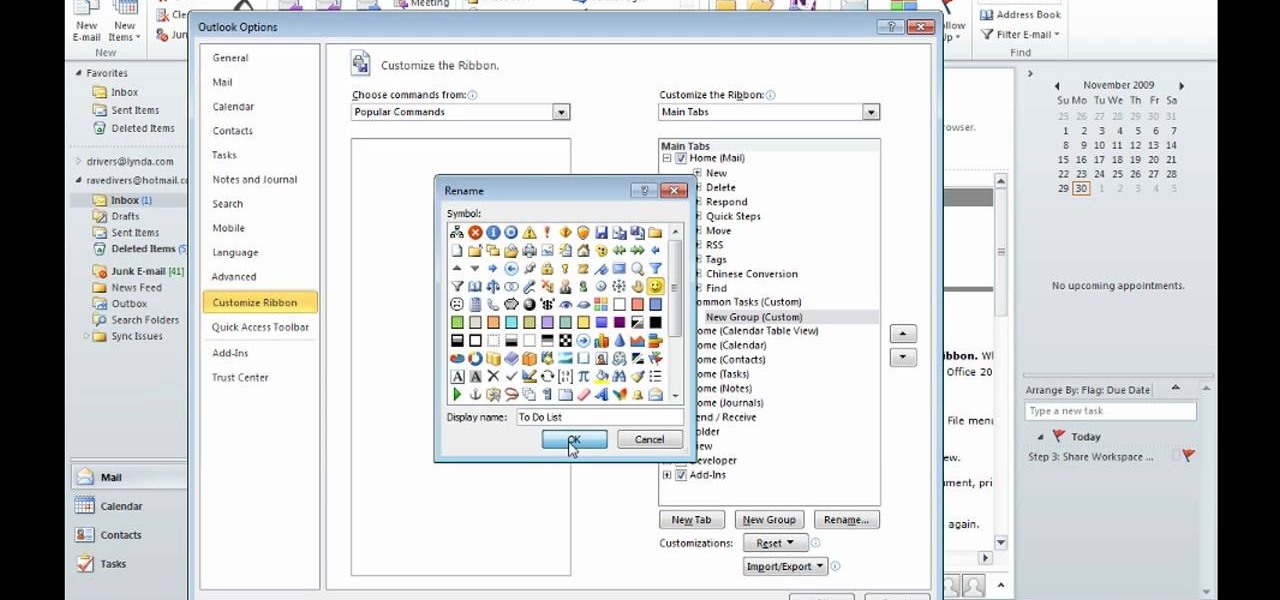
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...

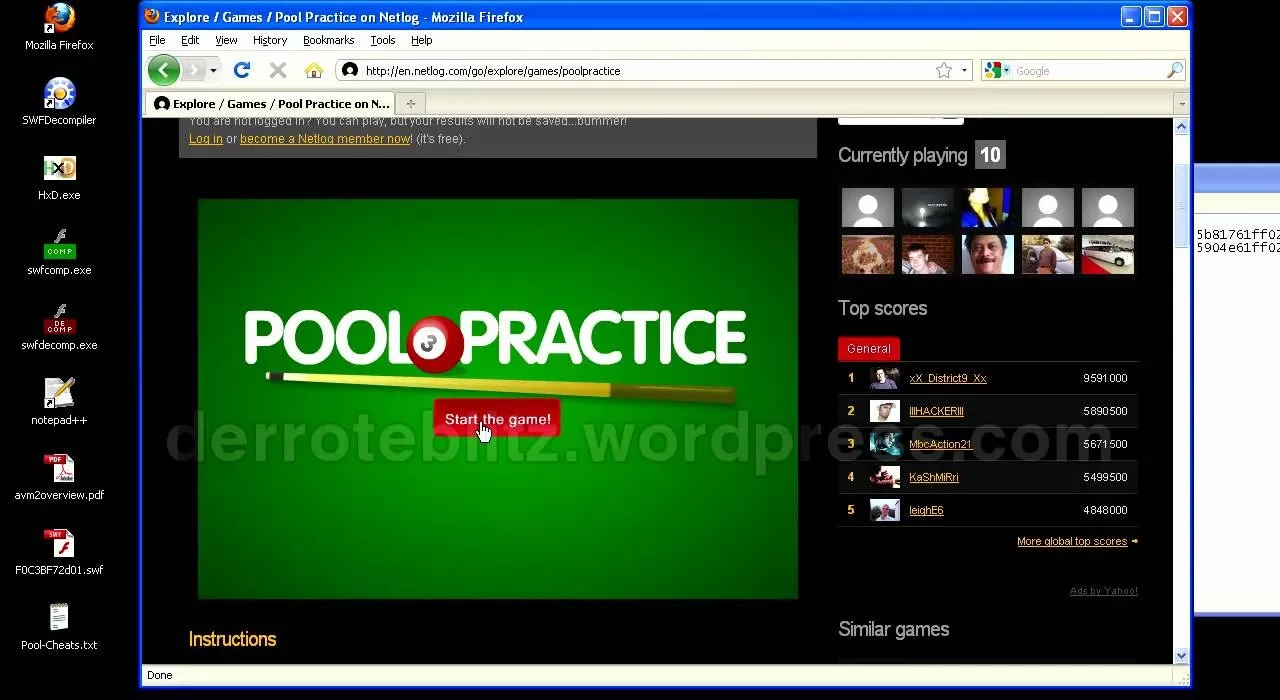
You want to know how to get extreme scores in the flash game Pool Practice? This is how. Watch this video tutorial to learn how to cheat in the flash game Pool Practice (01/01/10).

Can't tell if you need sunscreen or a rain poncho? Checking the forecast is a breeze. Learn how to check the weather on your iphone.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

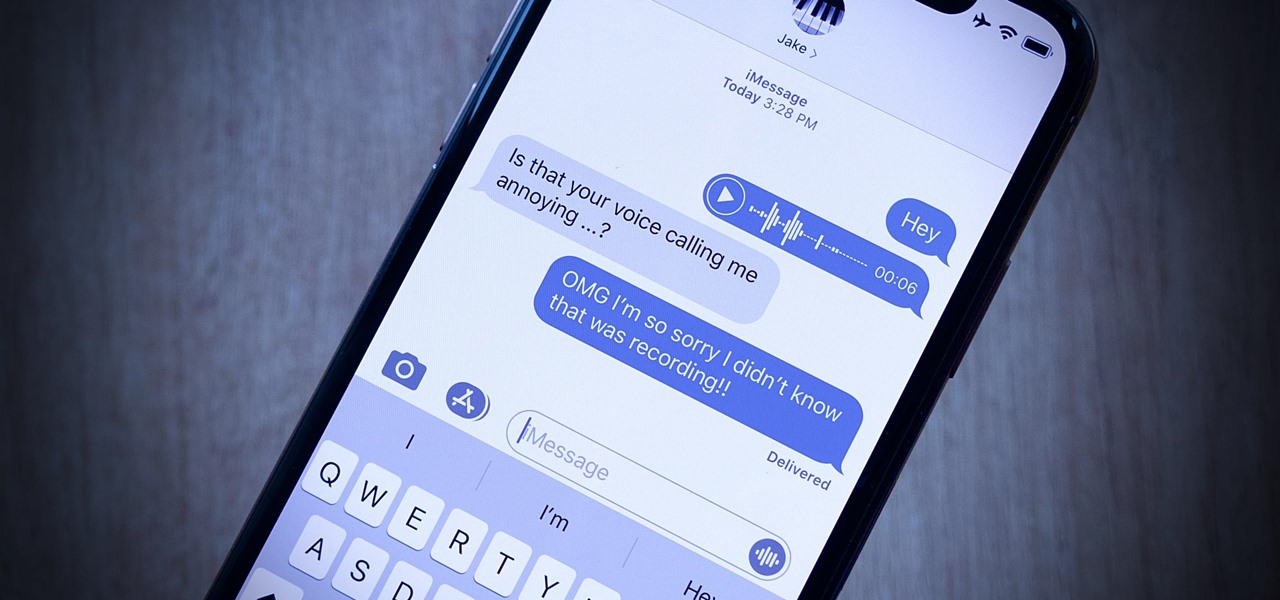
Your iPhone's audio messages may get you in trouble if they haven't done so already. It's way too easy for your iPhone to start recording without your knowledge, only to send a friend or family member a conversation you're having about them. (Awkward.) Luckily, protecting yourself takes only the flick of a switch.

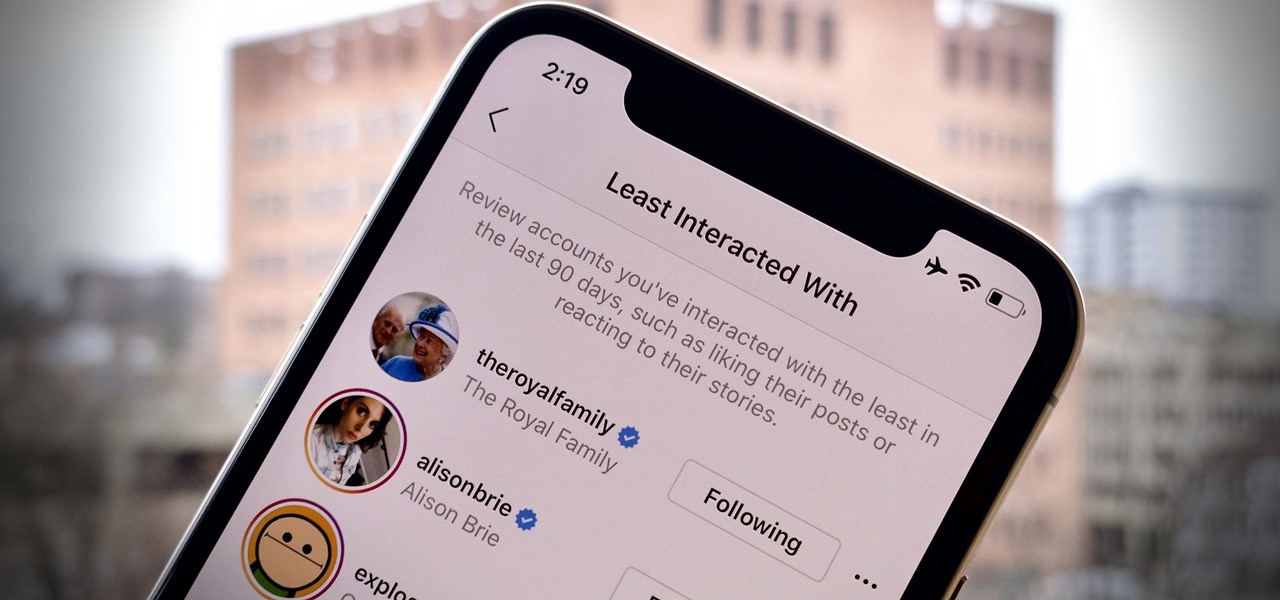
Is your Instagram feed a bit cluttered? Maybe you're seeing posts from people you don't even recognize. Perhaps the content isn't interesting. Whatever the case, it's common after years of having an account to follow too many users whose posts just aren't doing it anymore. Luckily, Instagram has an easy way for you to purge unwanted accounts from your following list.

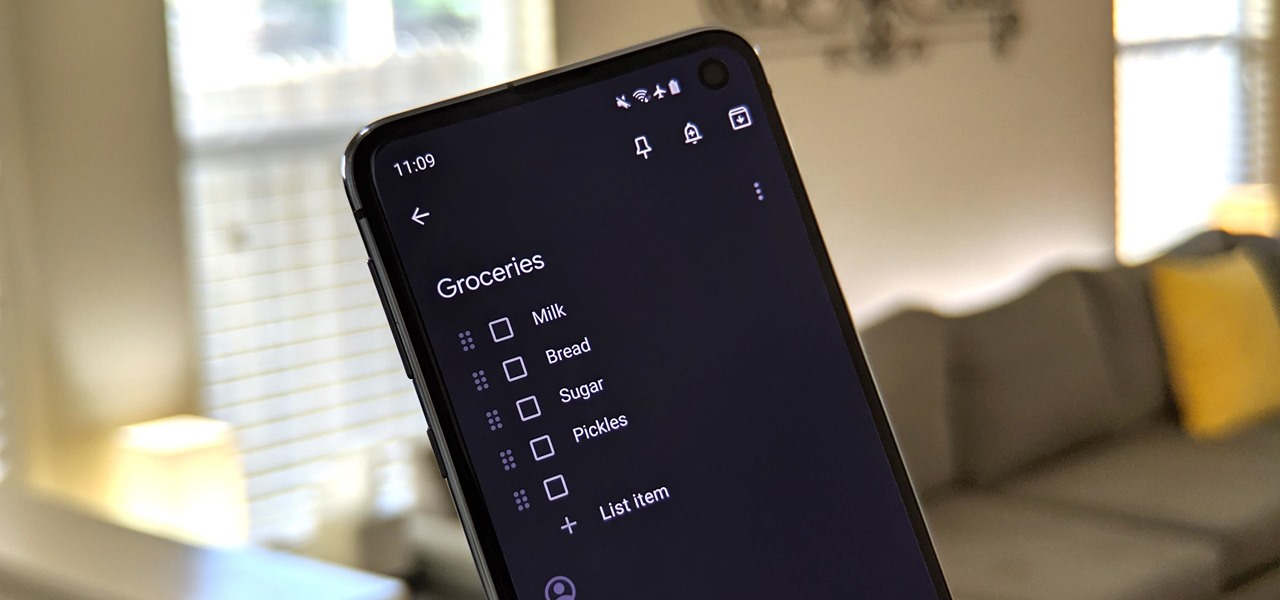
Life can get busy. Between work, school, and all the extracurricular activities, weekly chores like making a grocery list can get pushed to the back burner. But with a little help from the Google Keep app for Android or iPhone, you can at least make one thing easier.

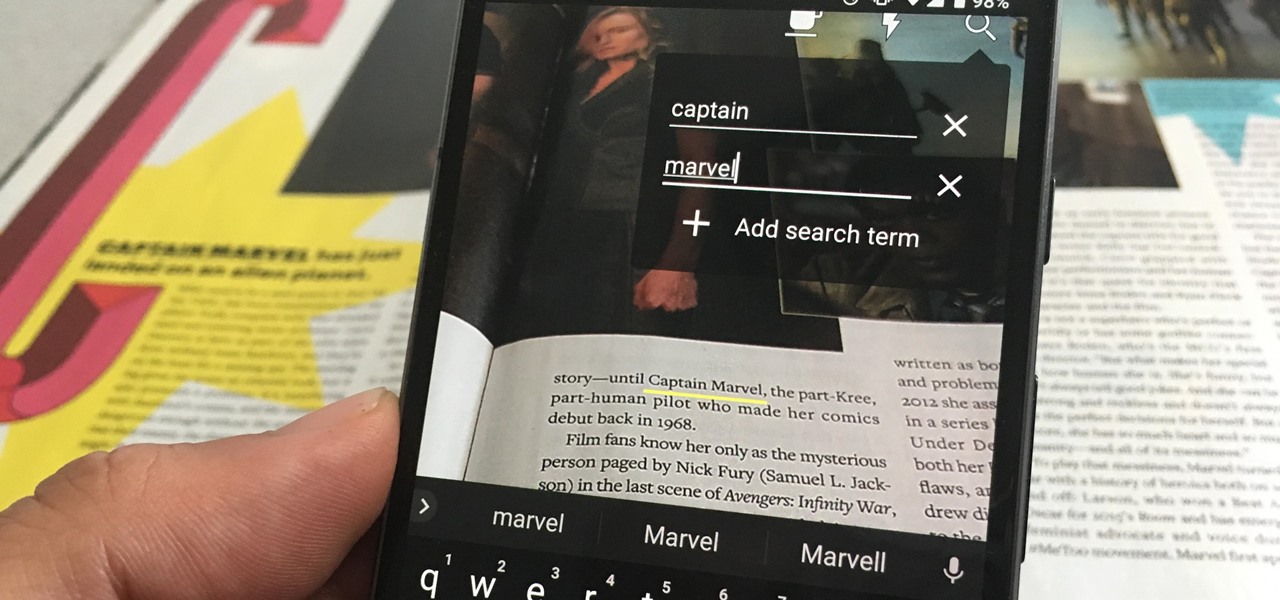
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

A new name isn't the only thing iBooks received in the iOS 12 update for iPhones. Aside from streamlining the name to "Books," Apple added a wish-list feature to its reading app so you can keep track of all the e-books and audiobooks you'd like to read from the Books Store.

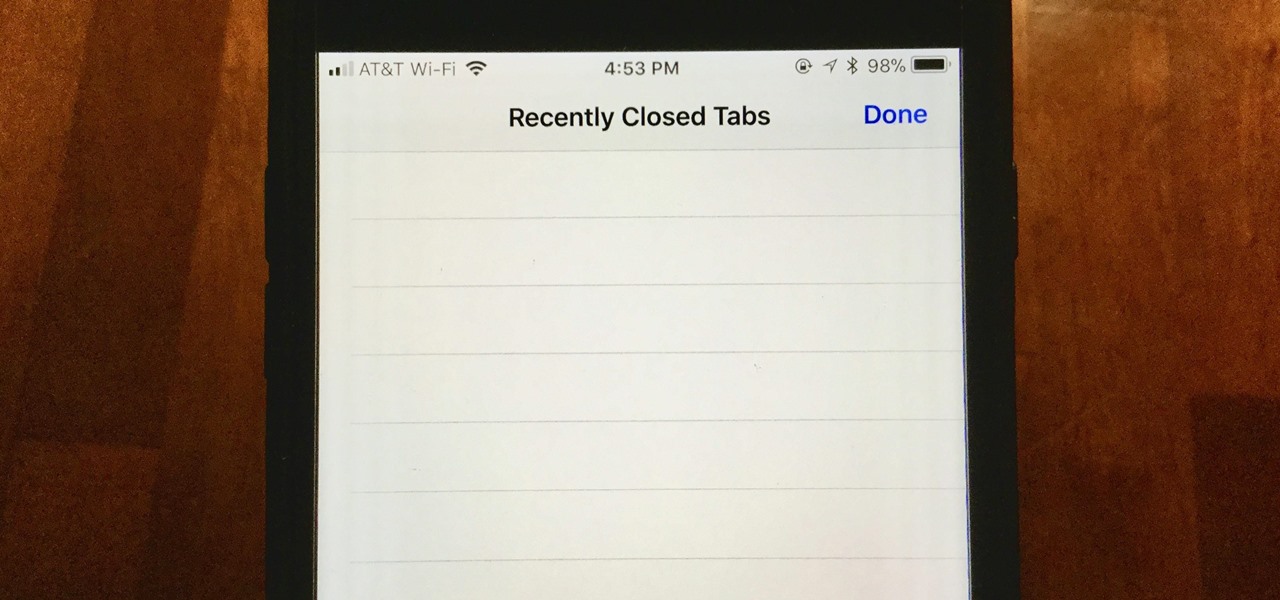
When you accidentally close out of an important tab on your iPhone, Safari's "Recently Closed Tabs" list really comes in handy. However, when it comes time to clear the list, things get a bit complicated. There's no "Delete" or "Erase" button on this page, but don't let that fool you — there are three easy ways to clear your recently closed tabs list.

When it comes to note-taking, Google Keep is one of the most diverse and functional applications on the Android platform. Sure, there are a plethora of other note-taking apps to choose from, such as ever popular OneNote and Evernote, but Google Keep differentiates itself from the crowd with its user-friendly interface and Google Now integration.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

When you're expecting an important call or text, it's pretty annoying to hear or feel your phone go off just to find out it was your reminders app telling you that you need to buy more contact lenses. Not quite as annoying as phantom phone vibrations, but it's up there.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

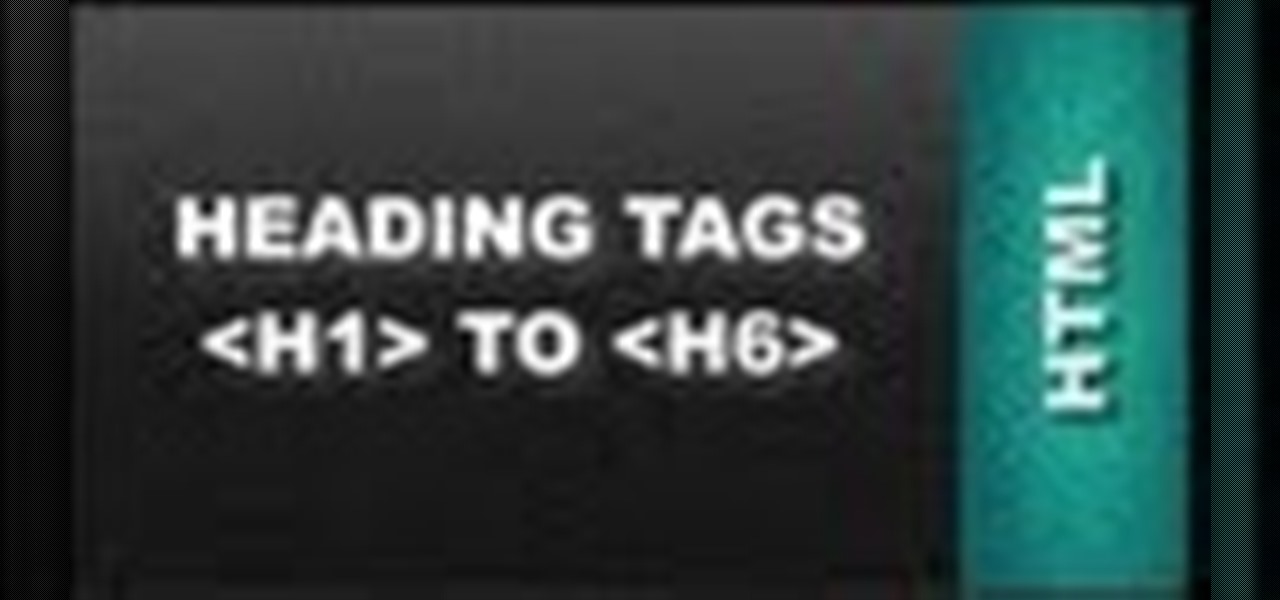
This HTML Web Design tutorial will explain how to add a Heading tag for your website. The heading tag is very important because it helps search engines to determine what the main topic is on a particular web page within your website. The HTML codes for heading tags range from h1 to h6 with h1 being the most important or in other words the main heading HTML web design tag. Make sure to give the h1 tag the most importance in terms of titles on your web page for headings. Another rule I recommen...

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 616th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the LARGE and SMALL functions to retrieve the 1st, 2nd, and 3rd largest values from a list. You'll also see how to do each of the following:

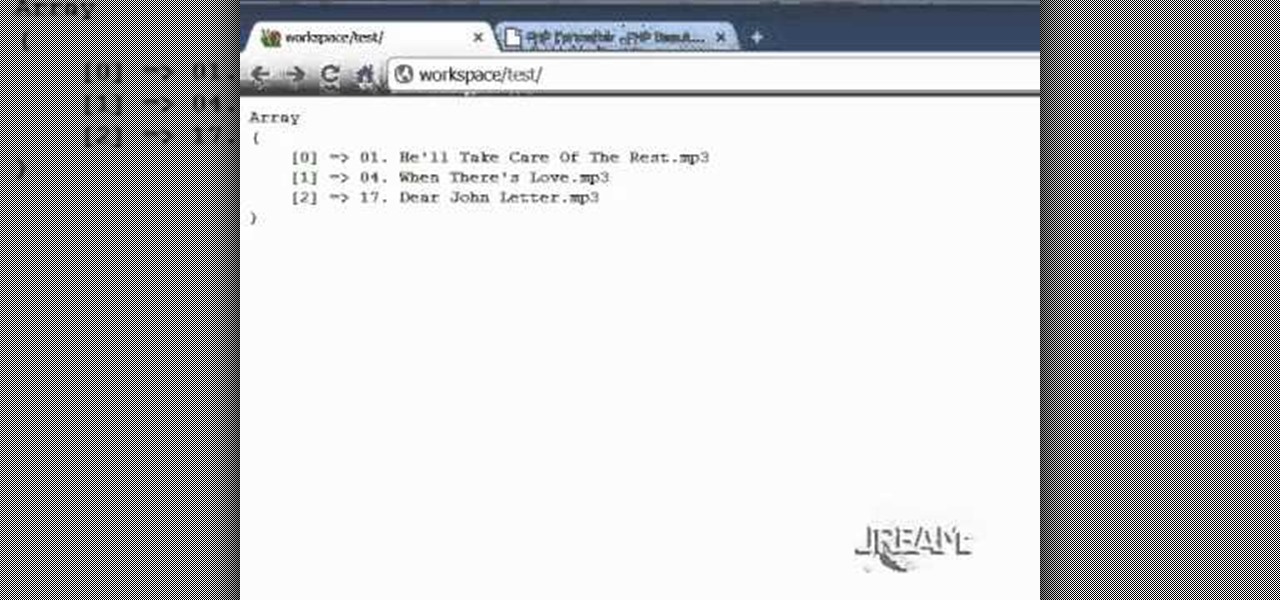
If you're programming with PHP and you generate a list of music files, you'll want to find a way to play them. This video shows how to use the Yahoo Media Player to play the list of mp3s you've created, with your PHP coding.

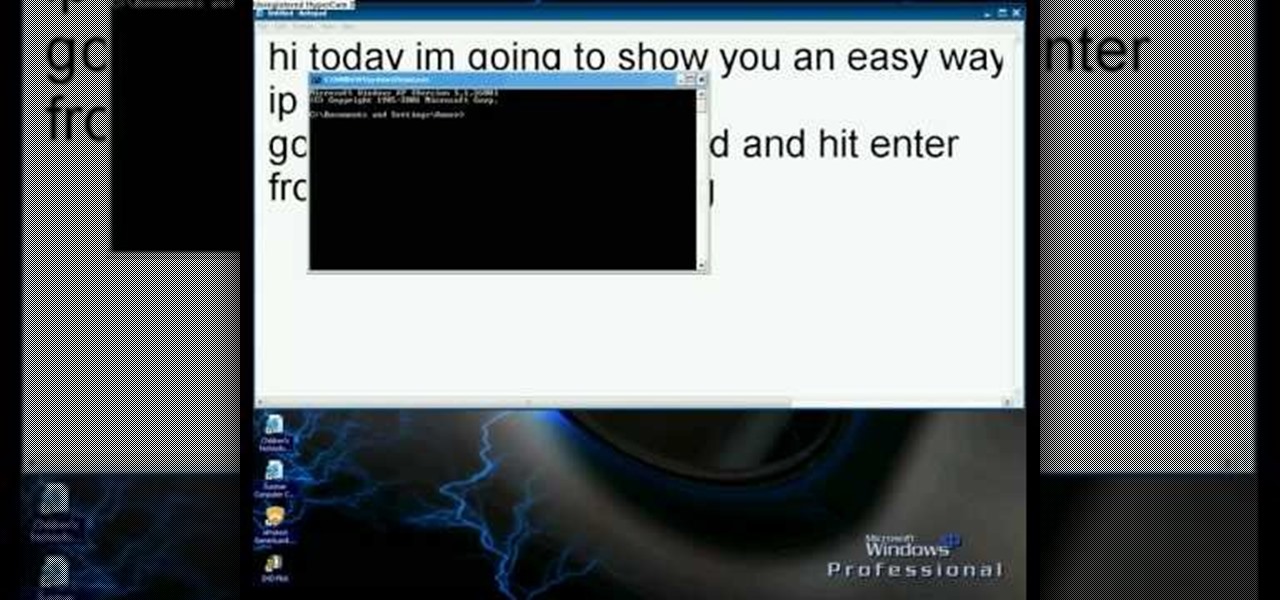
In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

In this clip, you'll learn how to make and set up a mailing list with GoDaddy and Mailman. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the process in just over three minutes. For more information, including detailed, step-by-step instructions, take a look.

Using the Cydia App, you can delete individual calls in your recent caller list. This enables you to delete single calls, line by line, instead of having to clear your entire recent call list.

This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

David Strom shows you how to pick from aong Google Groups, Mailman hosted by EMWD.com, and iContact and how to get started with your own mailing list

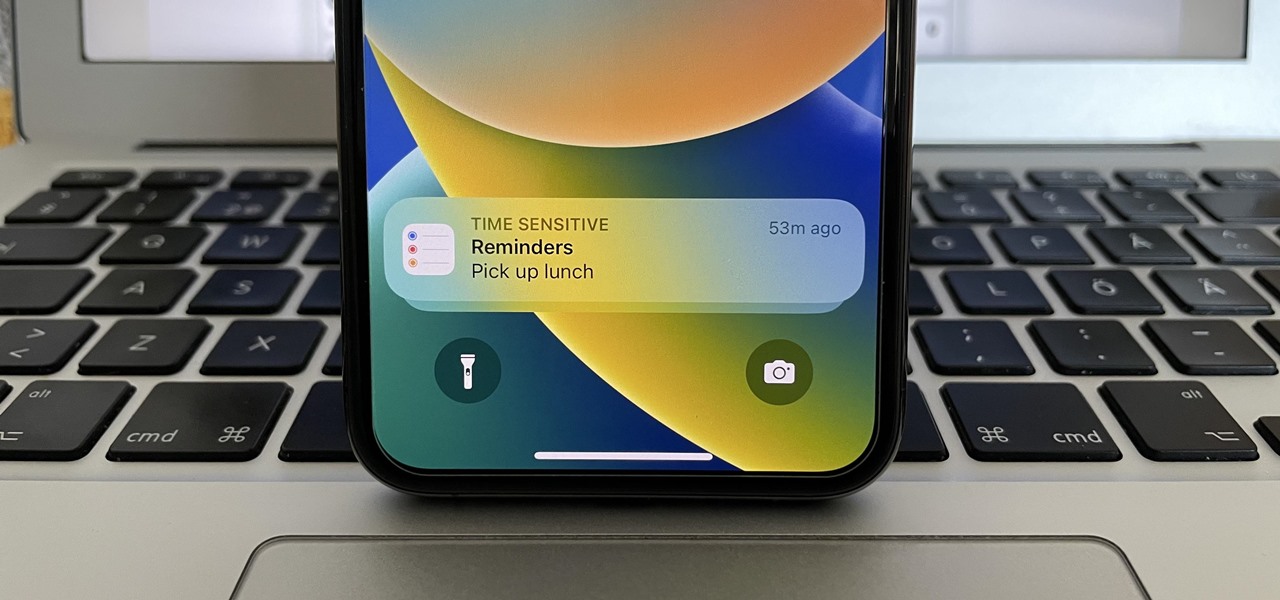
Apple just upgraded its Reminders app for iPhone, and there are some powerful new tools and improvements for task management that'll make you wonder how you ever lived without them.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.