Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...
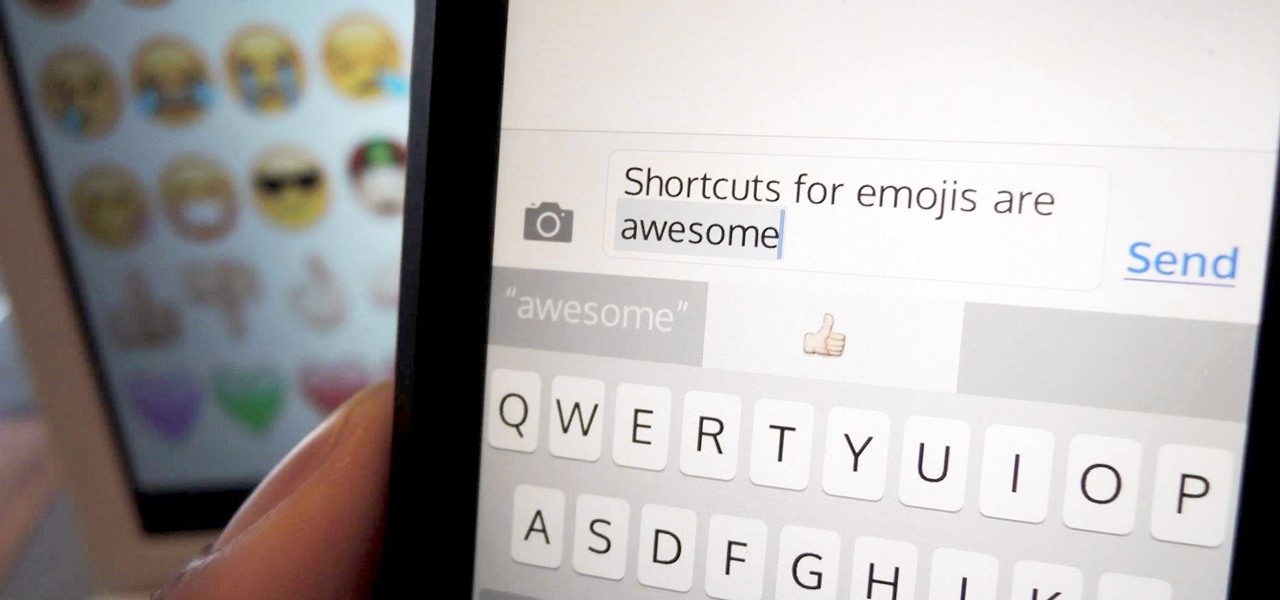
If I told you that people who use emojis in their conversations have more sex than plain-text users, would you believe me? According to a recent study launched by Match.com, men and women that use emojis have more sex than those who do not. If you were looking for an excuse to increase your emoji output, you may not find a better one than that. To make your emoji typing as smooth and seamless as possible, I'm going to show you how to create shortcuts in iOS 8 for all your favorite use cases. ...
Left-handers only make up about ten percent of the world, which means they typically have to use things made for the majority, i.e., right-handed people. If that wasn't annoying enough, there are studies that show that lefties actually get paid less.

Coffee shops are great places to unwind and get some free Wi-Fi, but all the bandwidth in the world can be ruined by someone being a noisy jerk. I usually start blasting music through my headphones whenever that happens, but that isn't always the most ideal situation, especially if I'm trying to study or work.

Whether I'm writing up something online, playing games in Chrome, or just browsing the annals of the Internet, I always like to keep a tab open for YouTube so I can listen to interviews, trailers, and music videos at the same time. But a tab can get lost, and it's not easy to "watch" if I don't have a second display to utilize—even with snapping windows.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Interesting reaction coke and milk The reaction of phosphoric acid (V) to proteins in the milk - they are cut and causes a precipitate

Imagine this: You're driving on the freeway in Canada, enjoying the view and sipping Tim Horton's, when all of the sudden you see something out of the corner of your eye. You expect it to be a moose, obviously, but instead you see a robot with his thumb hitched up. So, after insuring that you didn't accidentally take some hallucinogens a few miles back, do you pick it up?

Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it feels.

Apple computers have long been maligned as the computer for Starbucks aficionados and graphic artists. "Dude, have you used Excel on a Mac? It's terrible," says everyone that owns a Dell. The whole PC versus Mac battle was encapsulated in what I think to be the greatest ad campaign of all time, "I'm a PC and I'm a Mac." And yes, I know that PC really stands for Personal Computer, which means that a Mac would be a PC, but for the sake of the article, it will mean all things non Mac.

If you're studying human anatomy (or have ever visited a doctor's office), you're no doubt familiar with those plastic anatomical models with removable pieces meant to teach the different parts of the body. Before those, there were illustrated pop-up books. If you need to know the difference between the latissimus dorsi and the multifidus, you're probably better off sticking with your textbook diagrams. But if you prefer a more artful approach (and have a lot of time one your hands), this pap...

Electronic devices seem to have an uncanny ability to make noise at the worst possible times. It's always during an important meeting, a quiet study session at the library, or a biology final that your laptop or smartphone decides to play some obnoxious or embarrassing sound.

Throughout history, almost every superstition dealing with evil has had something to do with left hands. In the seventeenth century, it was thought that the Devil himself baptised his followers using his left hand. Today, studies show that left-handed people are more likely to be schizophrenic, alcoholic, delinquent, dyslexic, have Crohn's disease and ulcerative colitis, and a slew of other medical problems. To top it all off, left-handed people have an average lifespan that is 9 years shorte...

I learned the hard way that boxed dyes just don't work well for me. A few months ago, I tried one that had a pretty name like "soft violet black." Sounds nice, right? What I ended up with was brown hair and hot pink roots. Trust me, it wasn't cute.

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

How much time do you spend outside, as opposed to inside? Whether it's because you're working, studying or just have a bunch of errands to run, it may seem like the majority of your day is spent indoors. Ever wondered exactly how much time you spend indoors and outdoors? Now you can, thanks to this DIY Arduino-powered tracking device by Instructables user Gramsky.

Believe it or not, it's possible to make your very own lava—if you have a furnace capable of heating up to 1,200 degrees Celsius, that is. Bob Wysocki and Jeff Karson started the Syracuse University Lava Project to study basaltic lava and give students a hands-on way (hypothetically, of course) to learn about it. Oh, and they also want to use it for art projects. Sign me up for that class! It all starts with 1.1 billion-year-old basalt gravel, which apparently anyone can buy. They put the gra...

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Create sexy leopard print eyes. Fresh Face: Start with what I call a fresh face, which is your clean slate for all of your looks. A fresh face is after you have put concealer and foundation all over the face or only where needed, which ever you prefer. Also groom the eyebrows at this point, if needed, to avoid smudging shadow or liner while trying to groom. Apply a generous amount of loose powder to the eye to catch little stray make-up pieces. Shadow base: Apply a shadow base to give a good ...

In this language tutorial, you will learn how to use the vocative case in biblical Greek (Koine). The vocative case is the case used for a noun identifying the oblect being addressed. This is a perfect lesson for those who wish to study this ancient language. Listen and repeat the words in this language tutorial and you will be speaking biblical Greek in no time.

In this language tutorial, you will learn how to determine whether a nouns is dative, locative, instrumental, masculine, singular and plural in biblical, Koine Greek. This lesson is excellent for scholars wanting to study this ancient language of Greece. Watch this how to video and you will be speaking biblical Greek in no time.

In this language tutorial, you will learn how to use the definite article in biblical Greek (Koine). This is a perfect lesson for those scholars wishing to study this ancient language of Greece. Watch this how to video and you will be speaking biblical Greek in no time.

In this how to video, you will learn how to pronounce and memorize your first biblical Greek (Koine) vocabulary words. This is a perfect lesson for those who wish to study this ancient language. Listen and repeat the words in this language tutorial and you will be speaking biblical Greek in no time.

In this language tutorial you will learn how to use personal pronouns in biblical Greek (Koine). This is a perfect lesson for the scholar looking to study the ancient language of Greece. Watch this how to video and you will be speaking the biblical Greek language in no time.

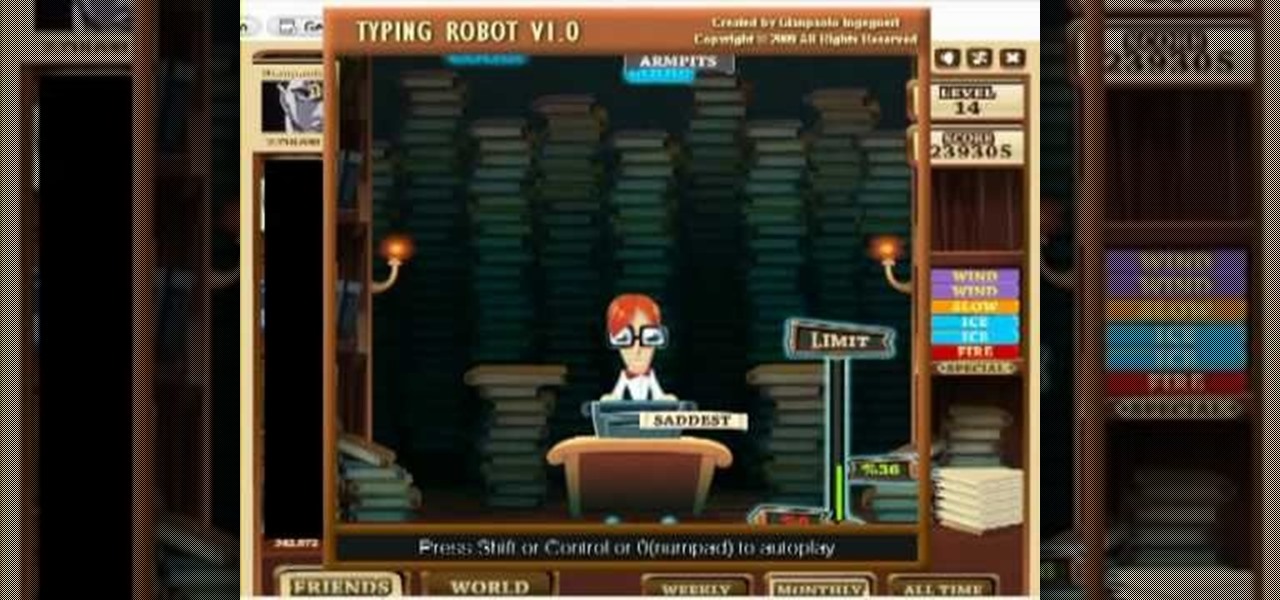
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Learn how to get your body bikini ready. Try these proven methods to get an awesome bathing suit bod.

Creating high-quality marketing content for your brand is labor-intensive to the point that it could be a job of its own.

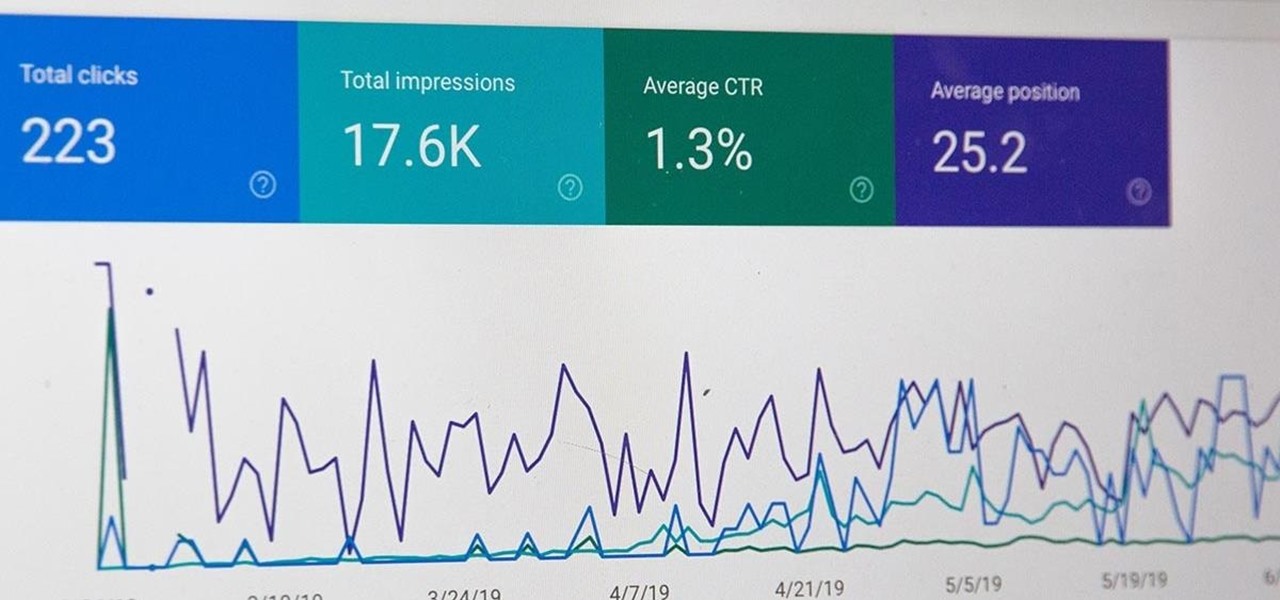
All modern entrepreneurs know that your business is as strong as its SEO. Whether you want to Rank #1 on Google to increase your personal branding, traffic to your online storefront, or to add the skills to your resume, you can now get a Complete SEO Training course for just $14.99, in the Gadget Hacks Shop, 92% off the regular cost of $199.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

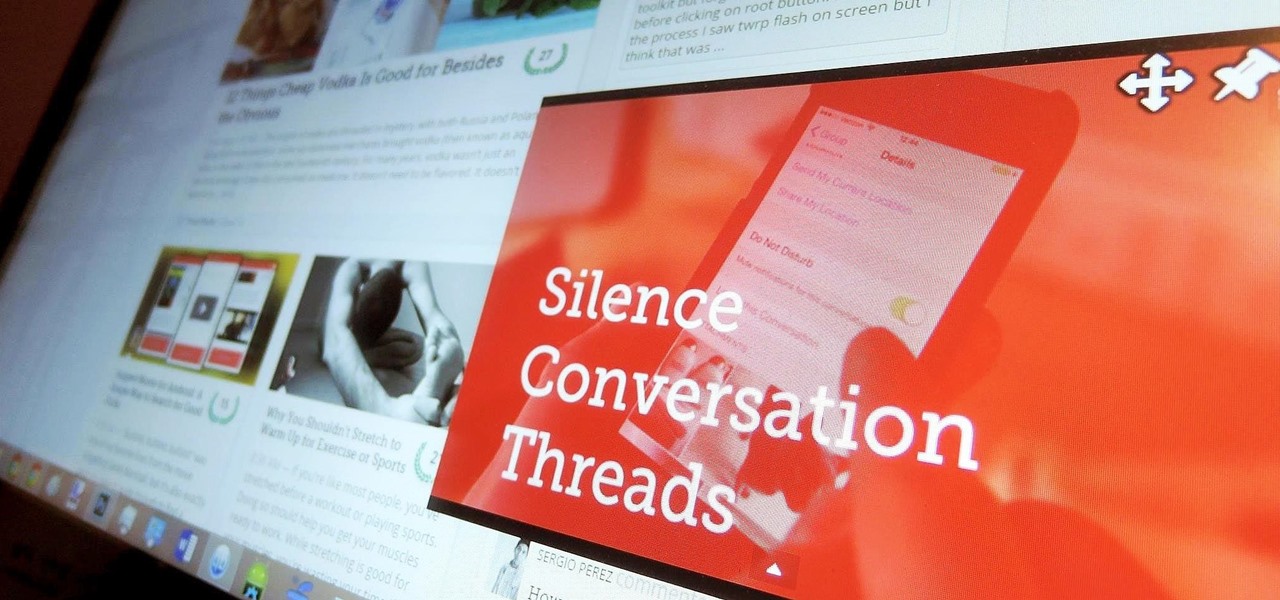
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of — you don't even need the barcode.