Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

While Siri came up on the scene with hardly any competition back in 2011, Google Now has not only caught up to Apple's intelligent personal assistant, but also excelled in certain areas—with its ability to quickly answer questions, give recommendation, and even deliver information that it predicts a user will want.

Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all the emails, has been compressed after the mail was deleted. If this hasn't been done it is possible to hack into this file and recover the deleted email. Text-based emails, like those one creates on programs like Eudora,...

I am constantly hitting Apple's limit of 500 open tabs in Safari on my iPhone, so it's safe to say that I have way too many tabs to sort through. With that many tabs open in the browser, it can be impossible to track down the one needed at any given moment. If that sounds like you, stop browsing tab after tab to locate the right one because there are hidden tricks to searching those tabs that make it easy.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Internal linking is a valuable way to improve search engine optimization on your website or blog. This component of organic search engine optimization we going to focus on web copy threading.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

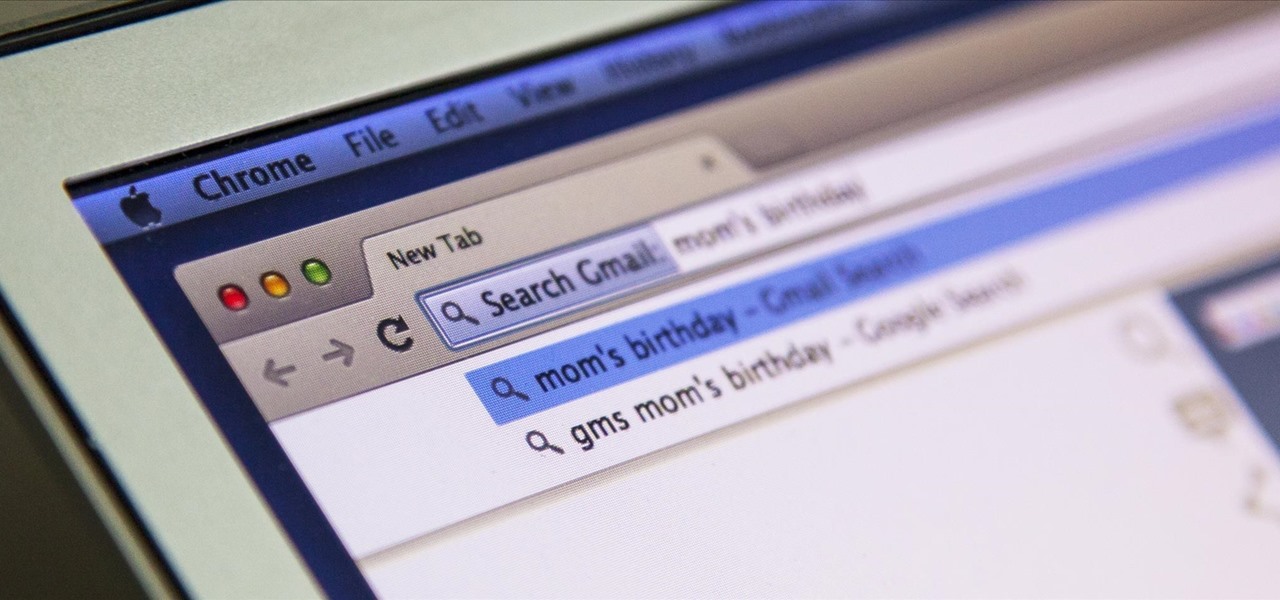
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

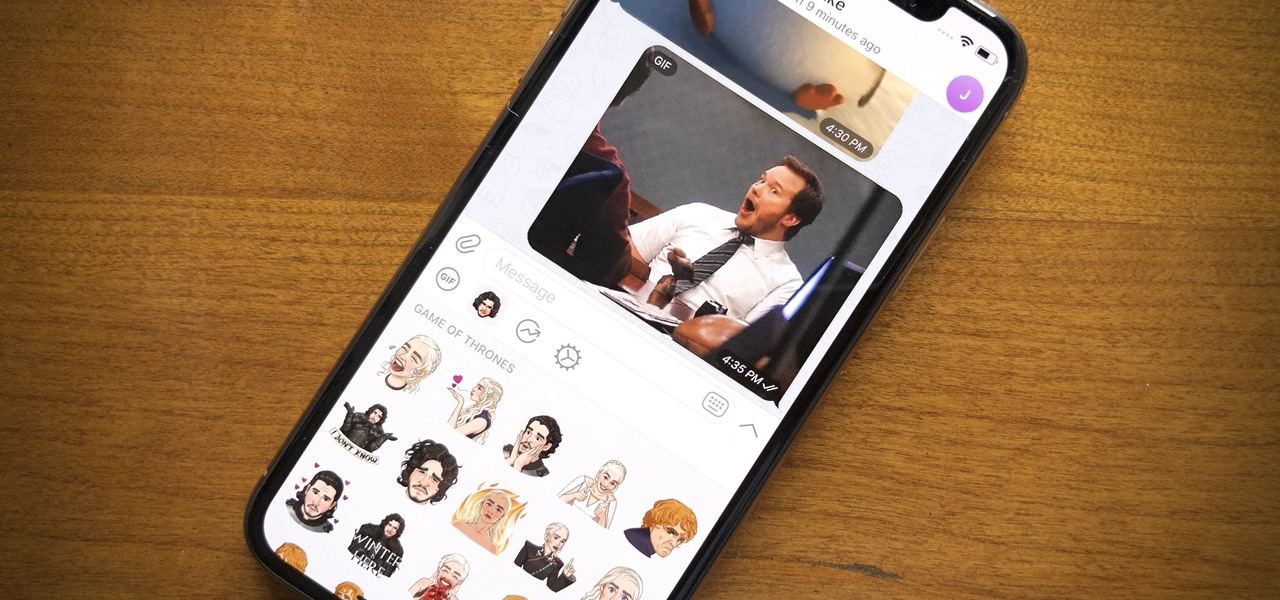
Remember trying to express yourself over the 160-character limit on SMS texts? We've come a long way since then, and messaging services have nearly taken over with emoji, chat effects, custom interface colors, and other personalizations. Necessities for messages these days include GIFs and stickers, and Telegram makes it easy to find those perfect reactions for any moment.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Messages is arguably the most important app on your iPhone, which is why it's always exciting when Apple pushes out new features for it. With the iOS 14 update, there a few critical changes as well as interface improvements and customization options that make the experience even more personalized than it already was.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

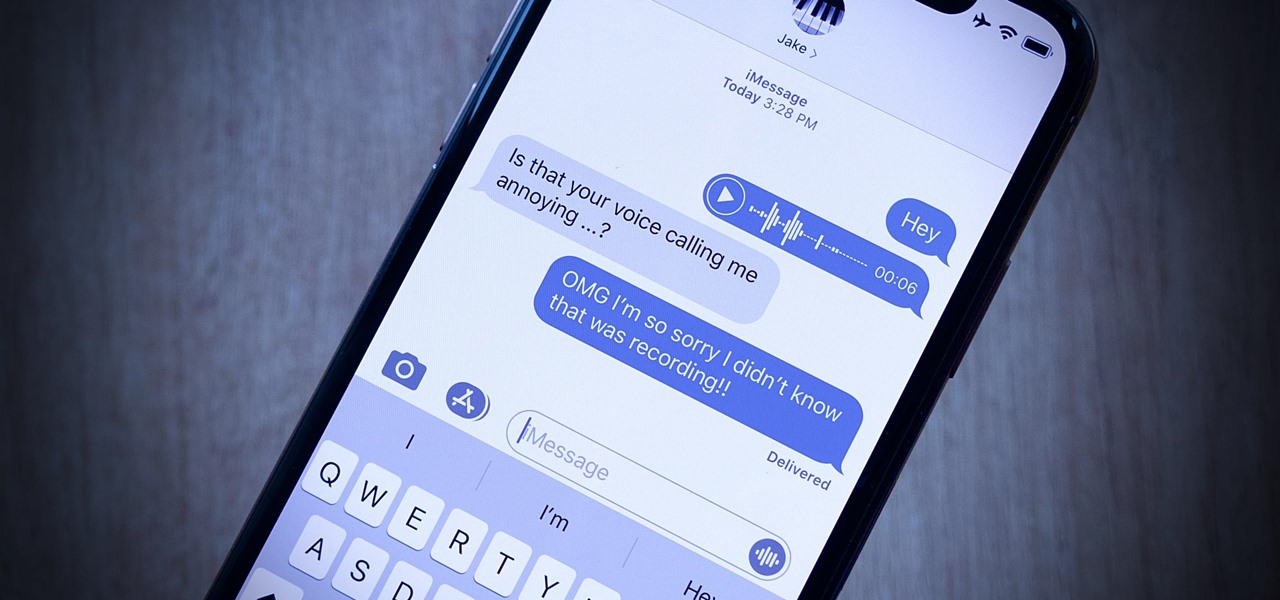
Your iPhone's audio messages may get you in trouble if they haven't done so already. It's way too easy for your iPhone to start recording without your knowledge, only to send a friend or family member a conversation you're having about them. (Awkward.) Luckily, protecting yourself takes only the flick of a switch.

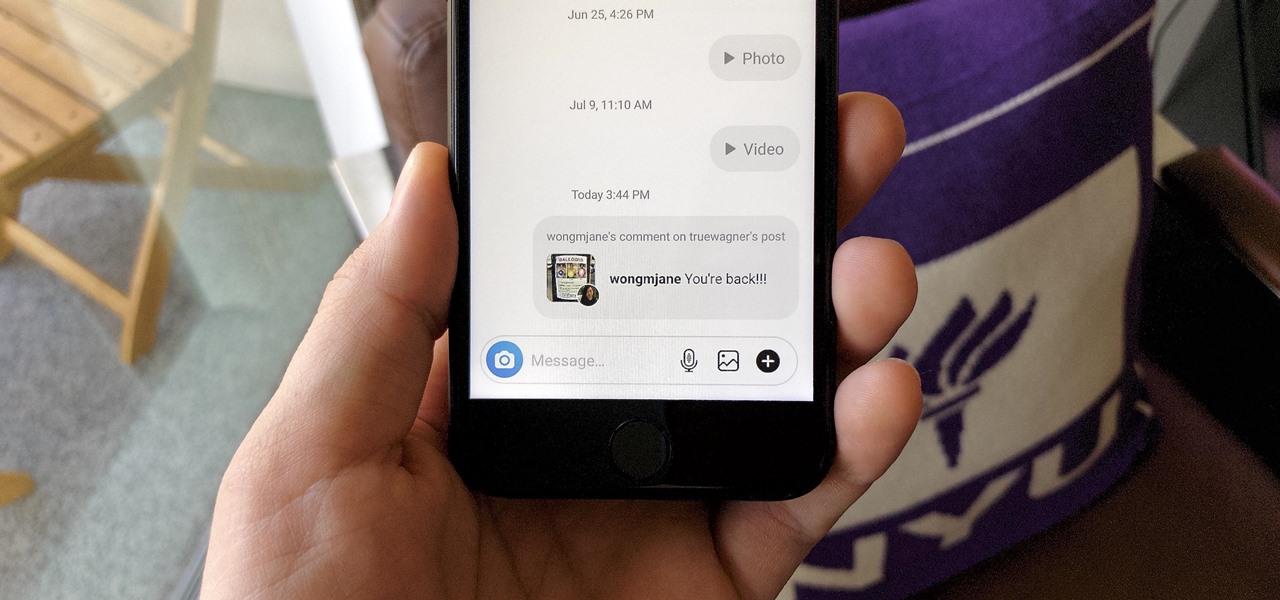
Sometimes, you'll see a comment on Instagram that you really need to share. Maybe it's something funny, possibly offensive. Whatever the case, the only thing to do is screenshot it and share that, right? Hopefully, not for long. Instagram is currently testing a feature that would allow you to share comments with others via a direct message and maybe even to stories and other apps.

In the revamped Messages app in iOS 10, you can now send animated GIFs from your iPad, iPhone, or iPod touch without a third-party keyboard like Giphy or GIF Keyboard.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

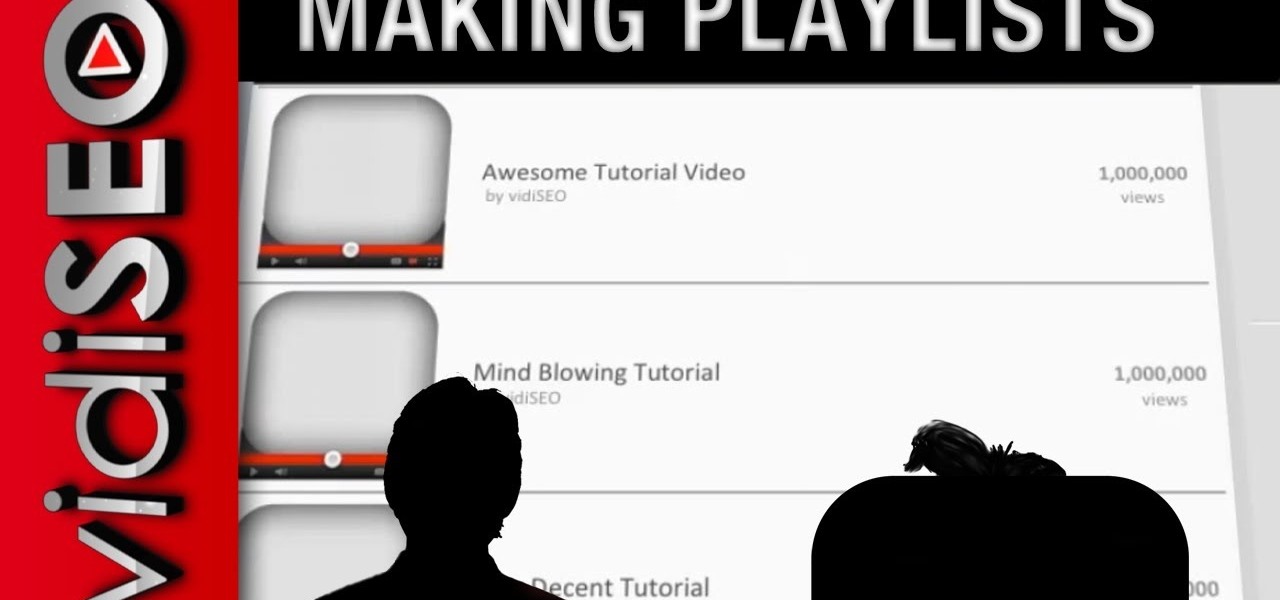
Playlists are a great way to organize and share groups of videos on YouTube. Playlists can consist of your videos, someone else's videos, or a combination of the two.

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

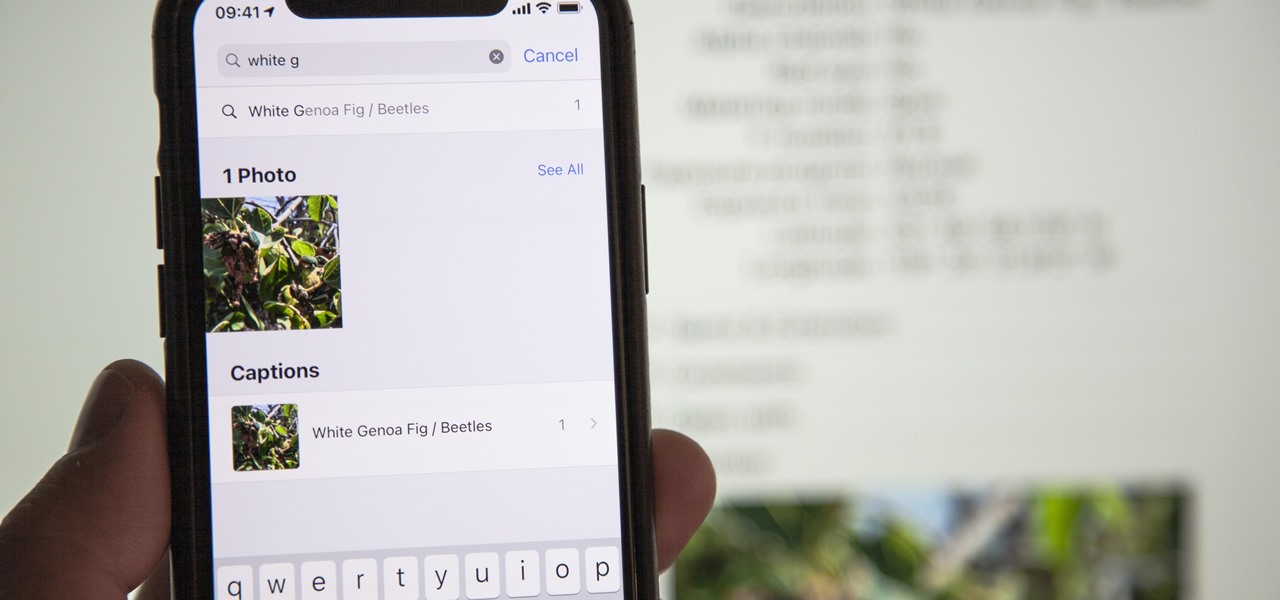
If you've been an iPhone user for quite some time, you probably have quite a bit of photos and videos in iCloud or on your device. Unless you know the date, location, or event, it can be pretty hard to find a specific memory. Even with intelligent search suggestions, AI-created categories, and multi-keyword filters, you still may not be able to find what you want. The new iOS 14 update changes that.

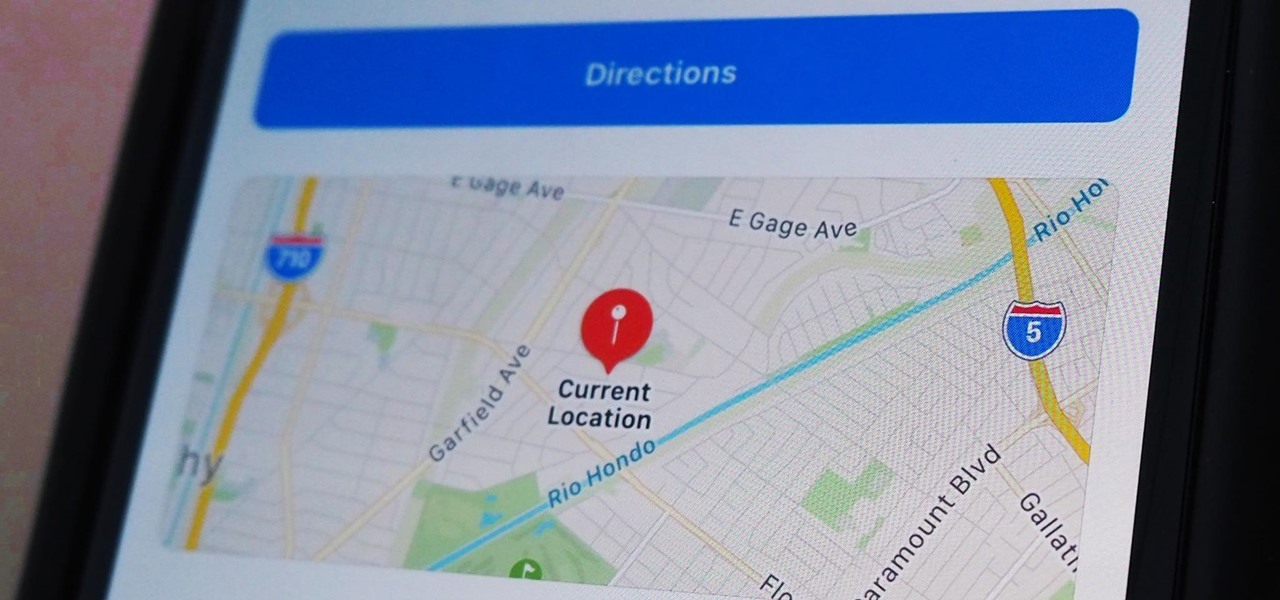
Apple makes it simple to share your location with your family and friends using tools built into the "info" page for each conversation thread in Messages. With those tools, you can send your current location or share trackable real-time coordinates. But iOS always has a few hidden tricks to make things easier than they seem, and that's precisely the case if all you need to do is share your current location.

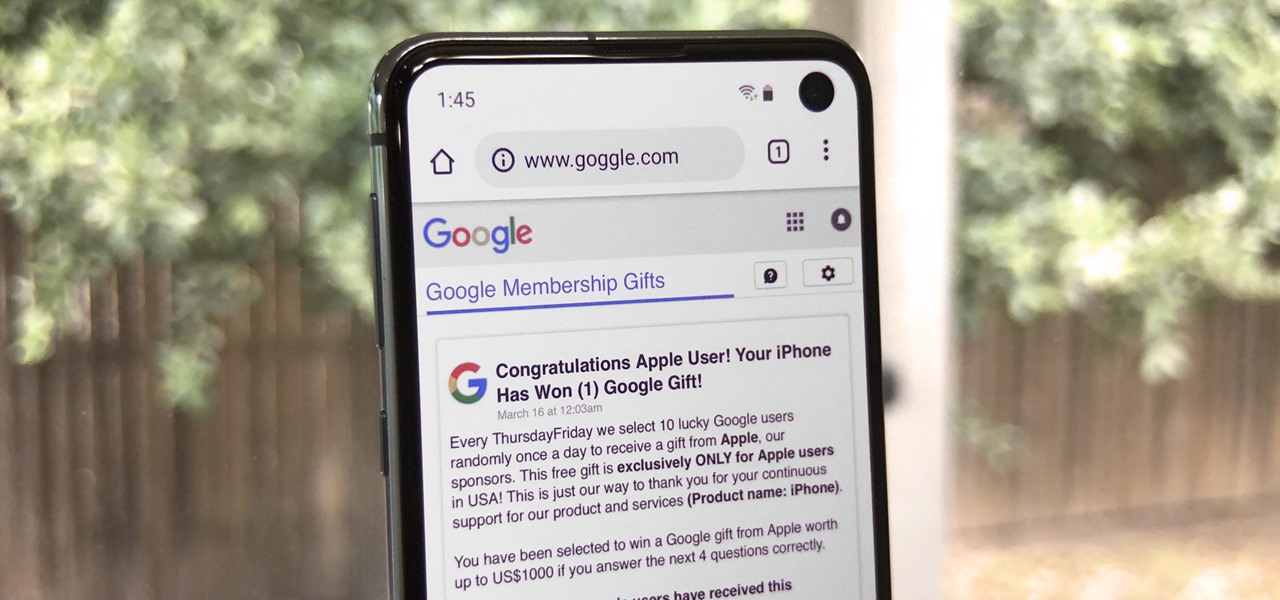
"Why do I keep getting popups on my phone when I'm not even doing anything?" I see this question asked all the time. The answer? You have a shady app on your phone and it started showing full screen ads. But people either don't know this (so they don't know they just need to find and uninstall the problematic app), or if they do know it's a bad app, they don't know which app is causing it.

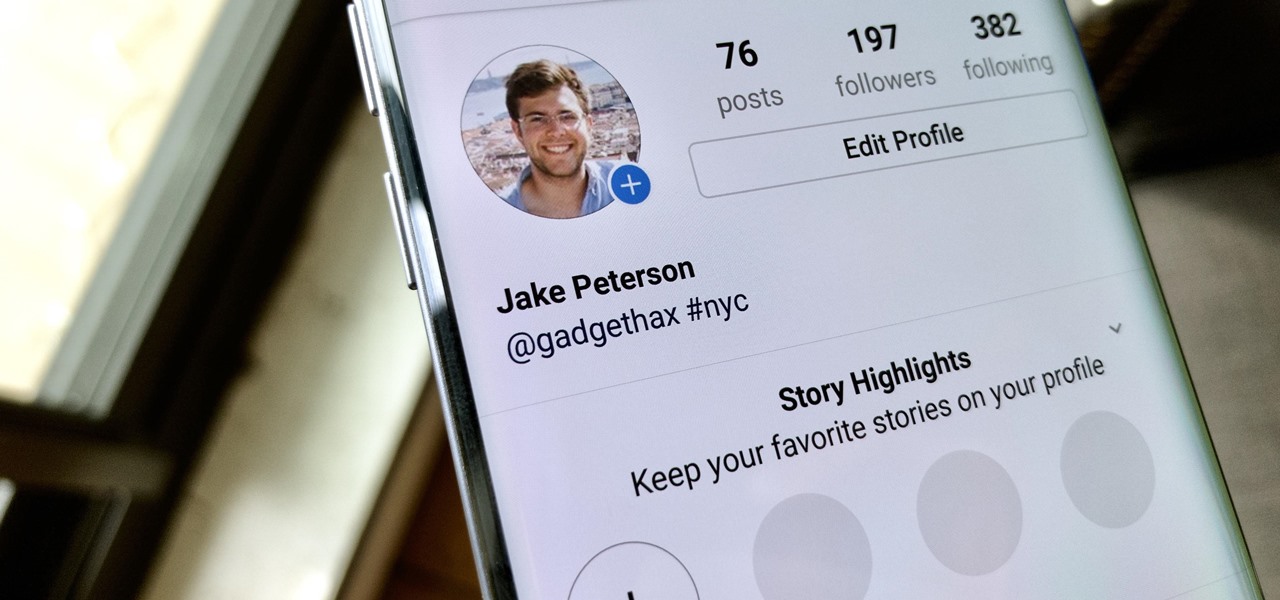
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

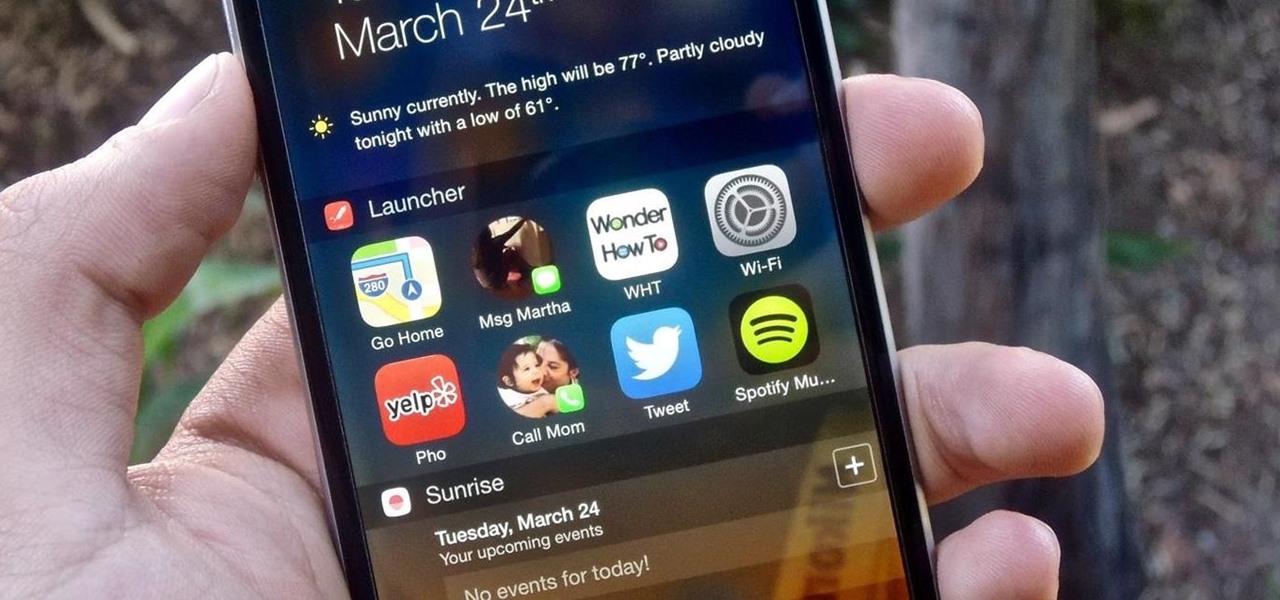
An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

Silencing my phone always gives me mild anxiety; while my Android is muted, my girlfriend or boss may be trying to reach me with some urgent news or task. On the one hand, I want to enjoy some peace and quiet, but on the other, I don't want to come back to a phone with 100 missed calls and countless exclamatory texts.

Third-party keyboards have become a game changer for iPhone owners since their integration in iOS 8. And while the major players from the Android realm—Fleksy, SwiftKey, Swype—already have their keyboards on the iOS App Store, their products are relatively standard fare.

Update: April 24, 2014 Looks the the one day availability was a precursor to a wider launch, as now anyone can buy a pair of the Glass Explorer Edition without needing an invite. Check out Google's Glass Shop for some easy ordering, still with the $1500 price tag.

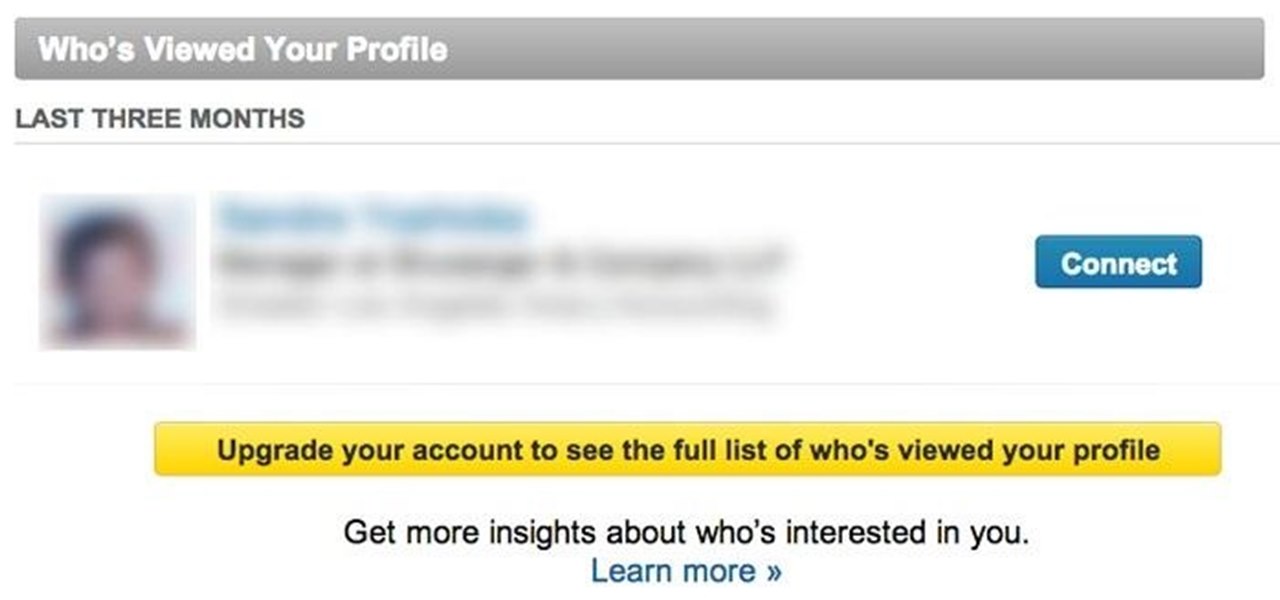
When LinkedIn first arrived on the scene, I thought it was a great resource for staying connected and getting in touch with those people in your desired career path. Keyword: Thought. Like most businesses, money and shareholders seem to have taken over the driver's seat, pushing the company towards a business-first, users-second approach.

There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages.

Things just got a lot better in your iPhone's Messages app, and the most significant change lets you text Android users with iMessage-like features such as typing indicators, read receipts, large file sharing, high-quality photos and videos, and even emoji reactions.

Apple Notes started with humble beginnings as a scratchpad of sorts, a place for us to stash some simple text for later. It's received many upgrades over the years, but Apple's latest iPhone software update is a game-changer.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.