The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Safari has a new feature that helps you discover the most beneficial aspects of a webpage without having to dig through the page or read the entire thing — and it works on iPhone, iPad, and Mac. It can make web browsing more efficient and websites easier to navigate while ensuring the visibility of important details.

It's easy to lose the TikTok video you were watching when you accidentally refresh your For You feed, but it's not gone forever. TikTok has a new feature for your iPhone, iPad, or Android device that can show you all your watched videos over the last seven days. There are also other, more hidden ways to see your watch history — one that goes well beyond a week.

A low-key iPhone feature that's been around since iOS 10 can make the iMessages you send to family and friends more exciting overall. One particular element is, if you'll forgive my decades-old slang, "da bomb" for emoji.
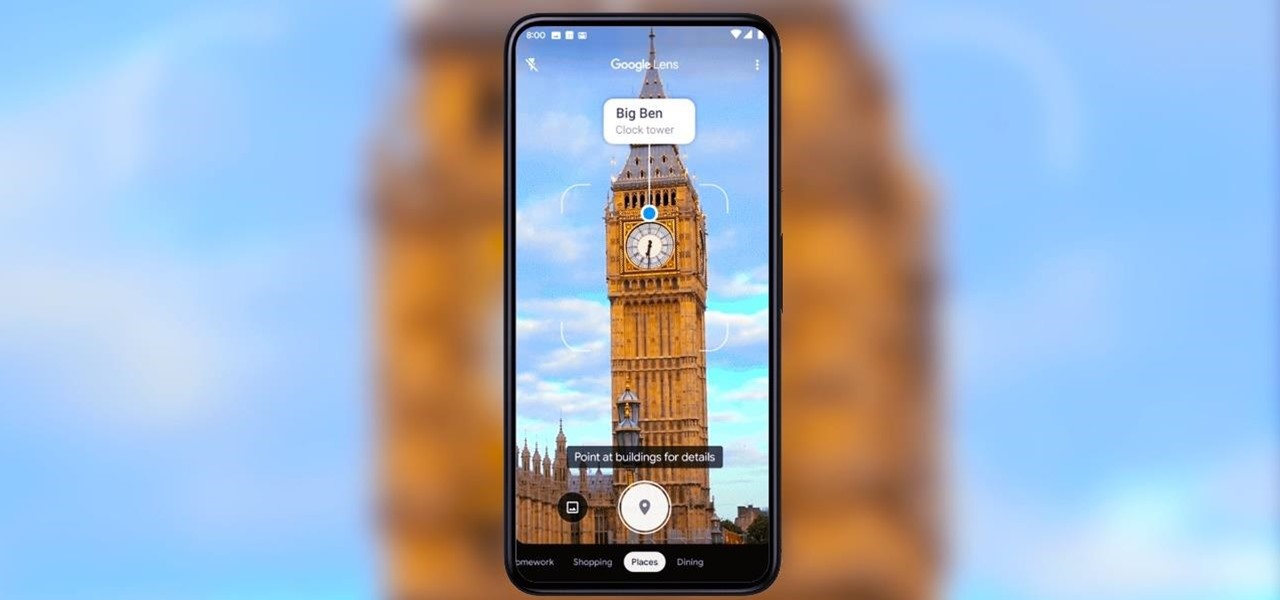
This week, Apple unveiled its own version of Google Lens in the form of Live Text. In response, Google just hit back with a new feature for its visual search tool called Places, a new search category that can recognize landmarks and return information on them within the camera view, which Apple touted as a capability of Live Text during its WWDC keynote.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).

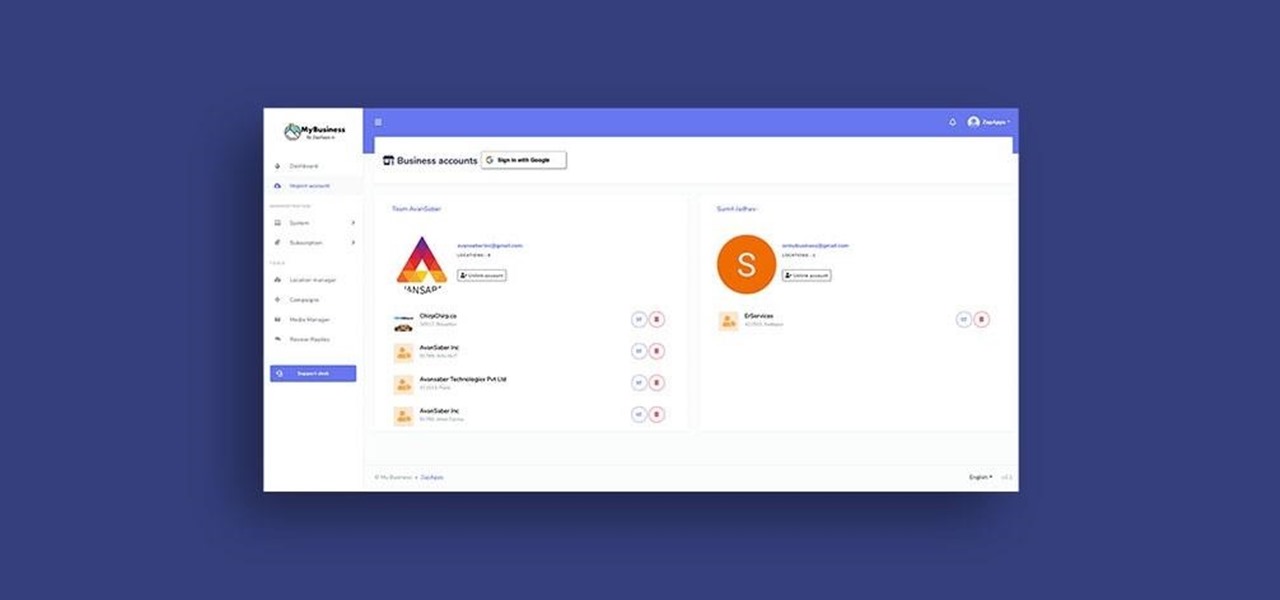
Google My Business lets you connect with customers across Google Search and Maps through a unique business profile. The web app allows you to connect and chat with customers in real-time and provides rich analytics to help you manage and grow your company.

While the job market is slowly rebounding, competition remains fierce. Don't get caught behind when a new opportunity presents itself. Preparation is key to landing your new big job.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Apple's latest update for iPhones, iOS 13, introduces over 200 new and exciting features. Many of those changes come to Siri, resulting in a better, more useful version of the digital assistant we've known for years. If you simply look at iOS 13's webpage, however, you wouldn't realize just how much Siri has changed this time around. We're here to fill in the blanks.

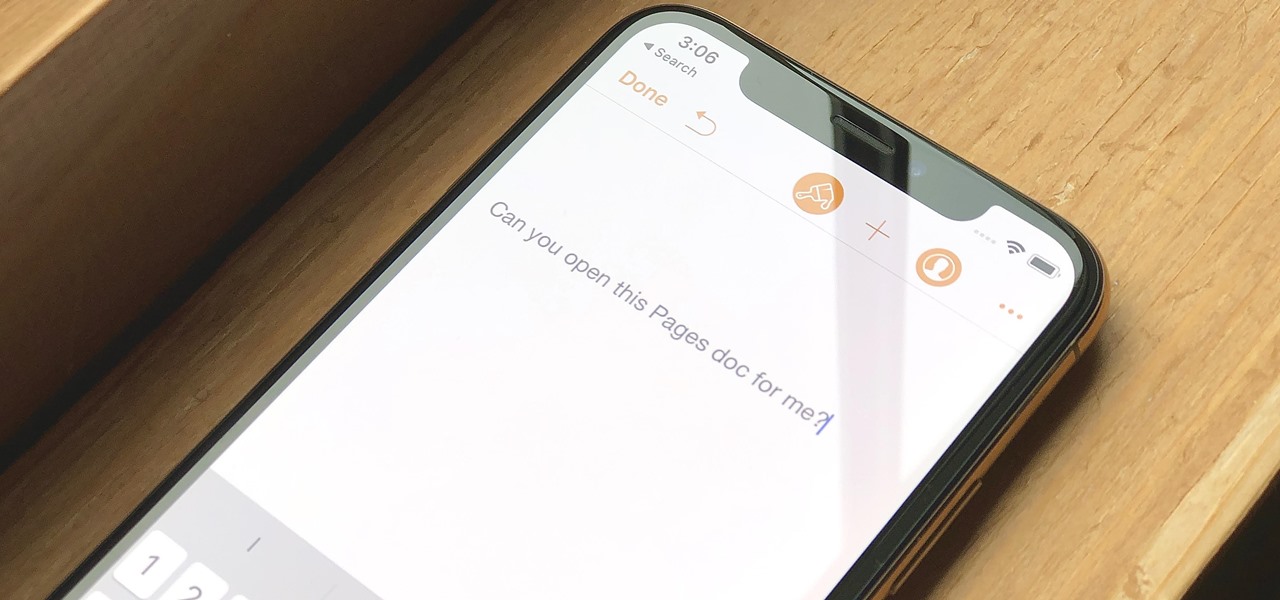
Let's say you have an important report to submit, but you want to check it over for any last-minute edits or changes. Times running out, and you simply can't find this Pages document anywhere. Wouldn't it be great if you could just ask your iPhone to open the report for you, so you could stop wasting time searching and finish the paper? Well, thankfully, Siri can help you out with that.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Magic Leap CEO Rony Abovitz doesn't engage in tweetstorms often, but when he does, those tweets are bold, exceedingly confident, and there's usually a strong takeaway regarding what the company is or isn't doing. But on Thursday, Abovitz's latest tweetstorm sent an unusually flustered message: We promise, the magic we're telling you about it better than anything you've seen on video.

The great thing about competition is it drives innovation. But when a company tries to one-up its competitor, it's not always with something brand new. Sometimes, one party will draw heavy inspiration from the other — but hey, it's still all good, because the consumers benefit either way.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

The Pixel 2 debuted a really cool feature that identifies any songs playing nearby and automatically displays the track's name on your lock screen. It's honestly one of the most inventive smartphone features we've seen in a while, especially considering how Google did it — but strangely, it's not enabled by default.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.