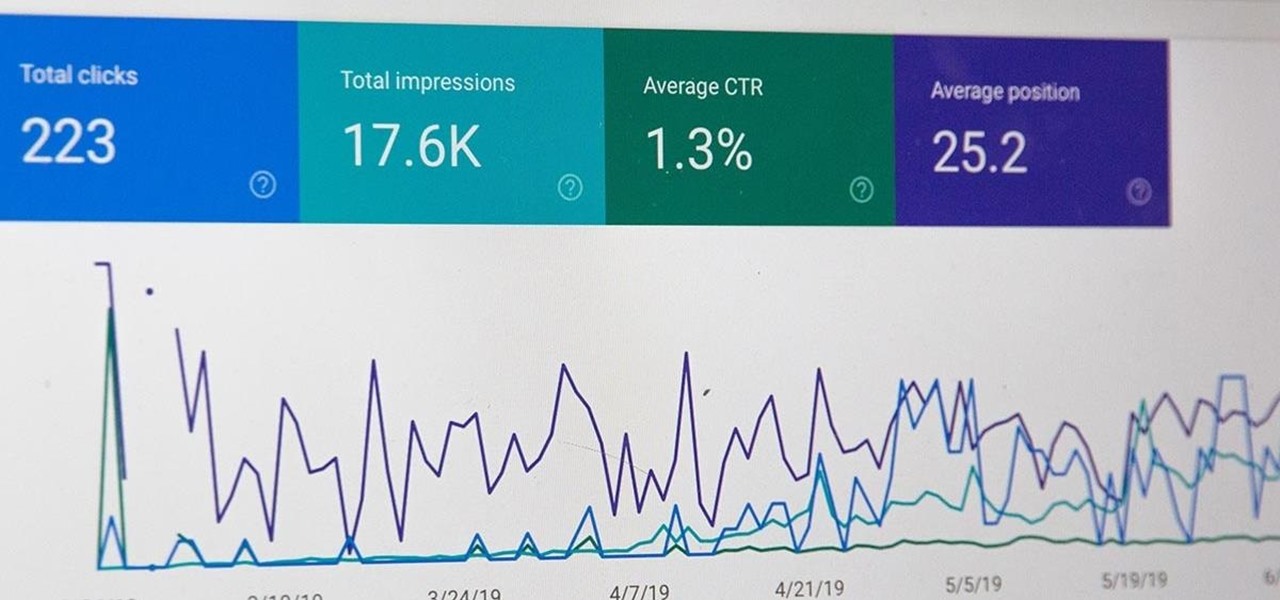
All modern entrepreneurs know that your business is as strong as its SEO. Whether you want to Rank #1 on Google to increase your personal branding, traffic to your online storefront, or to add the skills to your resume, you can now get a Complete SEO Training course for just $14.99, in the Gadget Hacks Shop, 92% off the regular cost of $199.
There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.
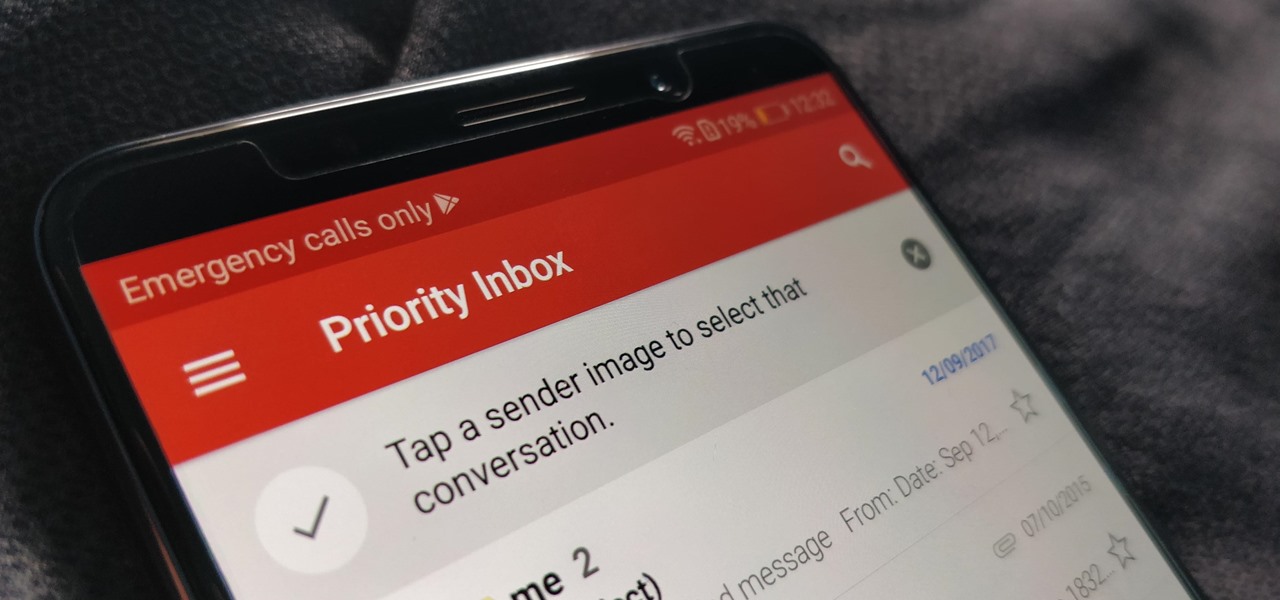
On average, an office worker receives 121 emails a day. Many of these emails are trivial and don't require immediate attention. While Gmail's automatic spam filters catch plenty of irrelevant emails, some still make their way into your inbox. Fortunately, Gmail's tools aren't limited to just spam filters.
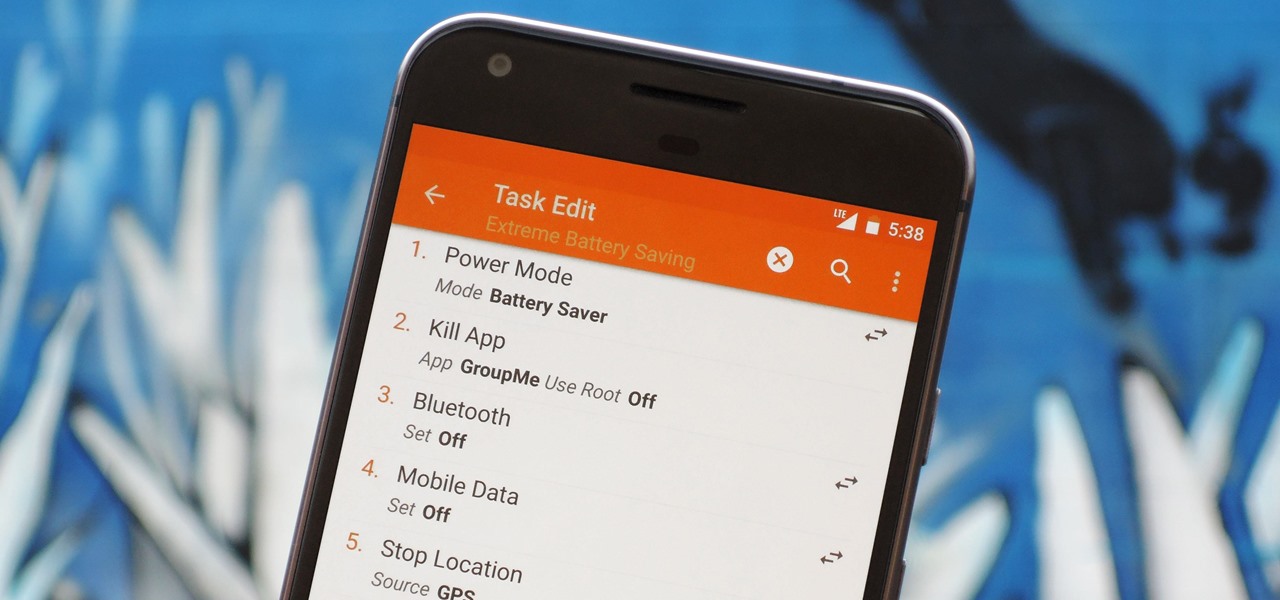
There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. Think of them like triggers and actions, respectively. Or a cause and an effect.
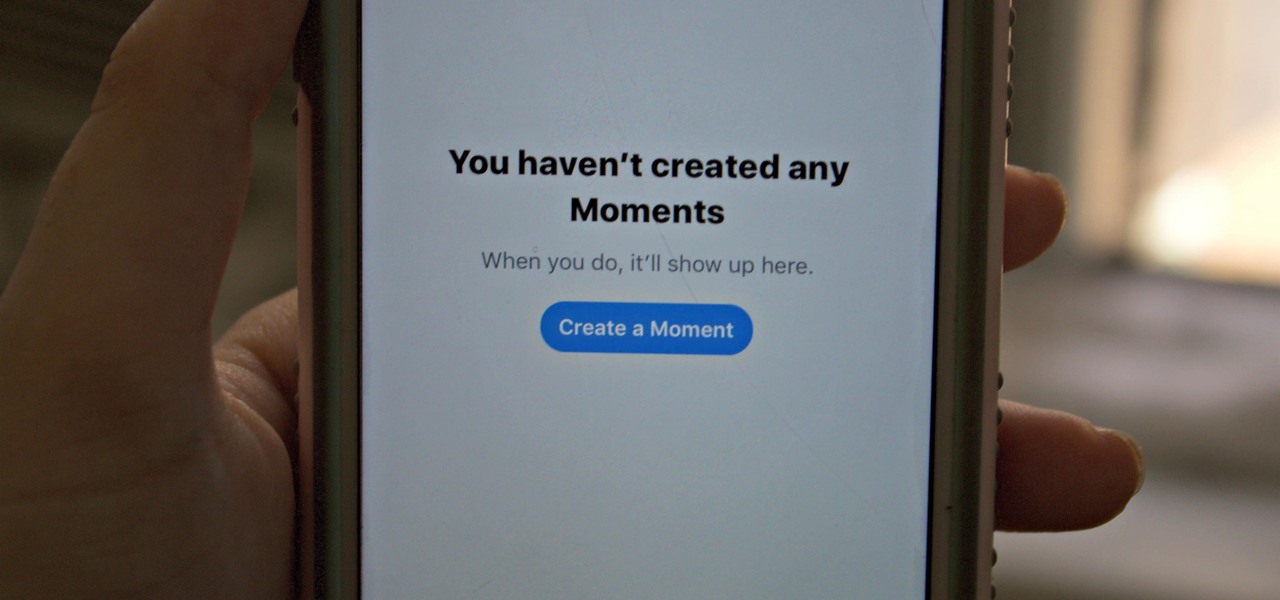
Twitter's Moments feature stitches together multiple tweets into a slideshow-esque story. This is particularly cool for you to keep up with major things that are happening in the world without having to follow and search for a ton of people to figure out the scoop.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have access to everything you've ever said on Facebook, public or private.

Our attention spans have vastly shortened thanks to the Internet and our subsequent procurement of information from it at a rapid pace. It's tough to pay attention to something for a good amount of time, unless it's ridiculously interesting and stimulating. It's gotten so bad for me that I keep checking my phone every ten minutes—I even did it during a midnight showing of The Dark Knight Rises.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

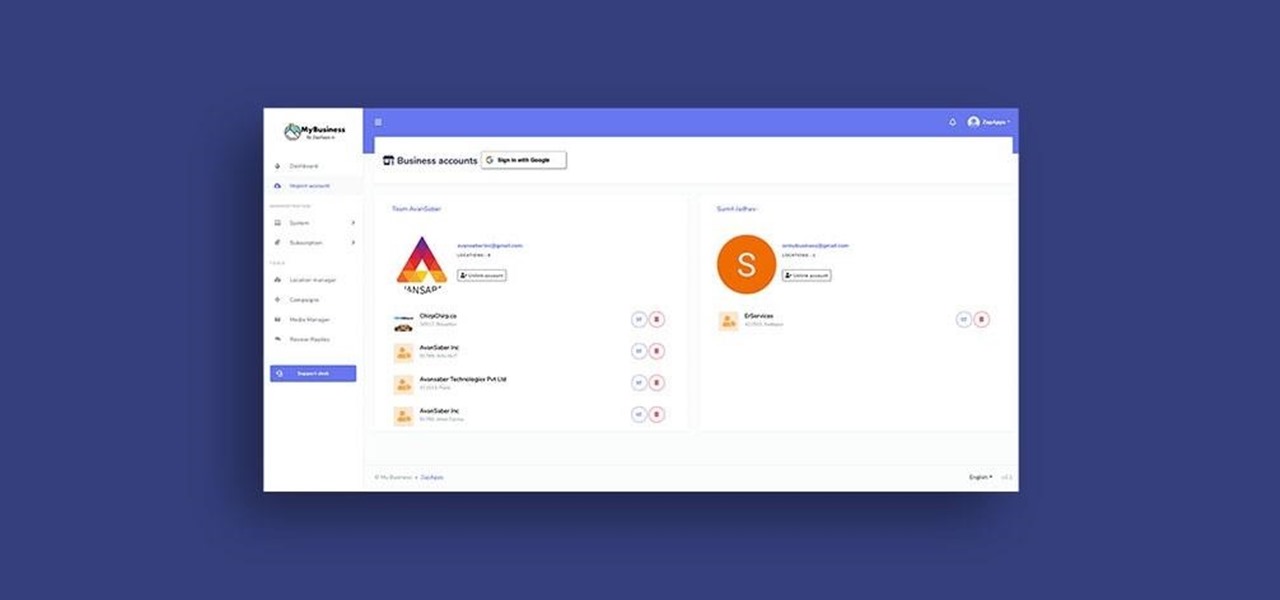
Google My Business lets you connect with customers across Google Search and Maps through a unique business profile. The web app allows you to connect and chat with customers in real-time and provides rich analytics to help you manage and grow your company.

While the job market is slowly rebounding, competition remains fierce. Don't get caught behind when a new opportunity presents itself. Preparation is key to landing your new big job.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

If you're looking for a new Reddit client on your iPhone, look no further than Apollo. Launched with iOS in mind, Apollo is a free app that offers an exceptional Reddit experience, but some of its excellent features — as well as some necessary ones — are hidden behind its "Pro" paywall. Are these extras worth your money?

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

Software takes time to create, and time is money, so a lot of great apps aren't free. But to generate interest, some developers will make their paid apps free for a limited time. The potential for a long-term increase in daily active users more than offsets the short-term lost revenue. So for us end users, the trick is knowing when these sales are going on.

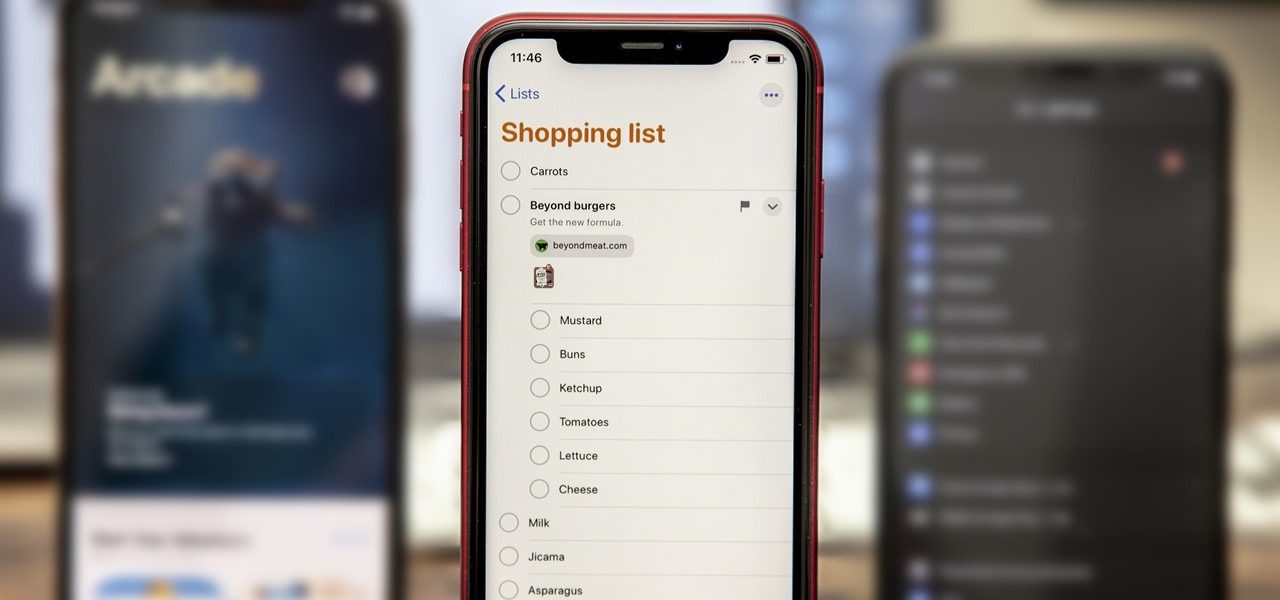
While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Reminders a shot, you may want to ditch that third-party to-do app you've been using.

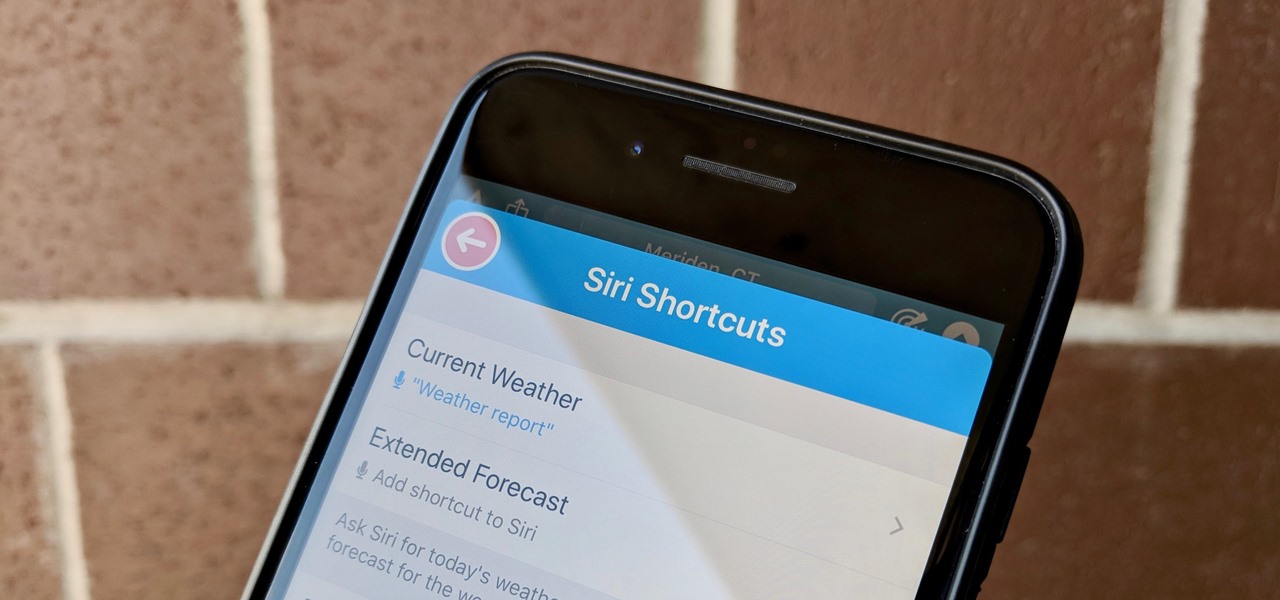
Since its humble beginnings on the iPhone 4S, Siri has come a long way. While each iteration of iOS sees new features for the iPhone assistant, iOS 12 offers users some of the best advancements in Siri we've seen in a long time, not the least of which is support for Shortcuts, Apple's replacement to the Workflow app.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

Hey, all you Instagram lovers, haters, or people who have no choice but to submissively bow down to the social app giant for other reasons, you've come to the right place. Today, I'm going to walk you through a very simple marketing trick to start boosting traffic to your IG account.

By combining years of web search advancements, natural language processing, and even DeepMind's artificial intelligence, Google Assistant hopes to change the way you interact with your devices. If you're familiar with Google's previous services, Google Assistant is like Google Now, Voice Search, and Now on Tap rolled into one service, with an extra layer of personality added on top. The end result is one central location for all of your Google needs, be it web search, screen search, playing m...

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.