
How To: Survive an airplane crash
In the unlikely event you're ever in a plane crash, these tips will dramatically improve your odds of walking away from it alive.


In the unlikely event you're ever in a plane crash, these tips will dramatically improve your odds of walking away from it alive.

Getting a good break in life is always nice. But when you're playing pool, it's essential. You Will Need

Low battery – two words you never want to hear. Banish them with these tips. You Will Need

Dhokla is a gujarati snack item traditionally made from rice and daal. Try this super simple, super quick recipe using sooji (suji, semolina or cream of wheat). Watch this how to video and learn to make Instant sooji dhokla, serve with tea and impress your guests with your Indian cooking.

Hot and sour soup is a popular Chinese dish that is loaded with veggies and usually chicken. Try this flavorful and hearty Indian Chinese version which is completely vegetarian and can be made vegan also. It’s simply delicious! Just watch this how-to video to learn how.

In this video, you'll learn how to get rid of a dry and itchy scalp with a hot oil hair treatment. Just follow along with Akiyia's instructions, and you'll soon have beautiful, non-dry hair that you can work with and braid.

Dogensangha describes in this video how one may experience the universe in body and mind through apparent non-action.

Here's a Math Craft project that takes less than 20 minutes, has an attractive, practical result, and is at least a little mind-blowing due to folding along curves.

Since PDF files are so popular in both our daily life and work, we see them everywhere. And sometimes we find there are terrfic images or text in the PDF files and we want to save them as seperate files for future use, such as in a presentation or post. Here's the question: how can we save those elements from the non-editable file formats?

Ingredients 16 ounces lump crab meat

Raw Truffles - Chocolate Truffles & Crispy Peanut Butter Truffles

With the Oscar nomination of "Exit Through the Gift Shop" and Banksys rise to global fame, street art is becoming more and more accepted into the global art establishment and mainstream culture. Shepard Faireys "Hope" poster is now one of the most recognized posters in the world, some experts saying that it will become just as unmistakably american as uncle Sams "i want you!" WWII army recruitment poster. Banksys work sells for thousands of dollars in auctions, and has fans in mainstream holl...

Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to the surface.
Type: Digital, Theme Theme: Kid Toys Model

Try out this basic hot milk sponge cake, which is a kind of egg foam cake, that you can use as a base for any cake art creation. It's super tasty, and you can add anything you want to it. Try it out and see for yourself.

I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermitereaction.

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients
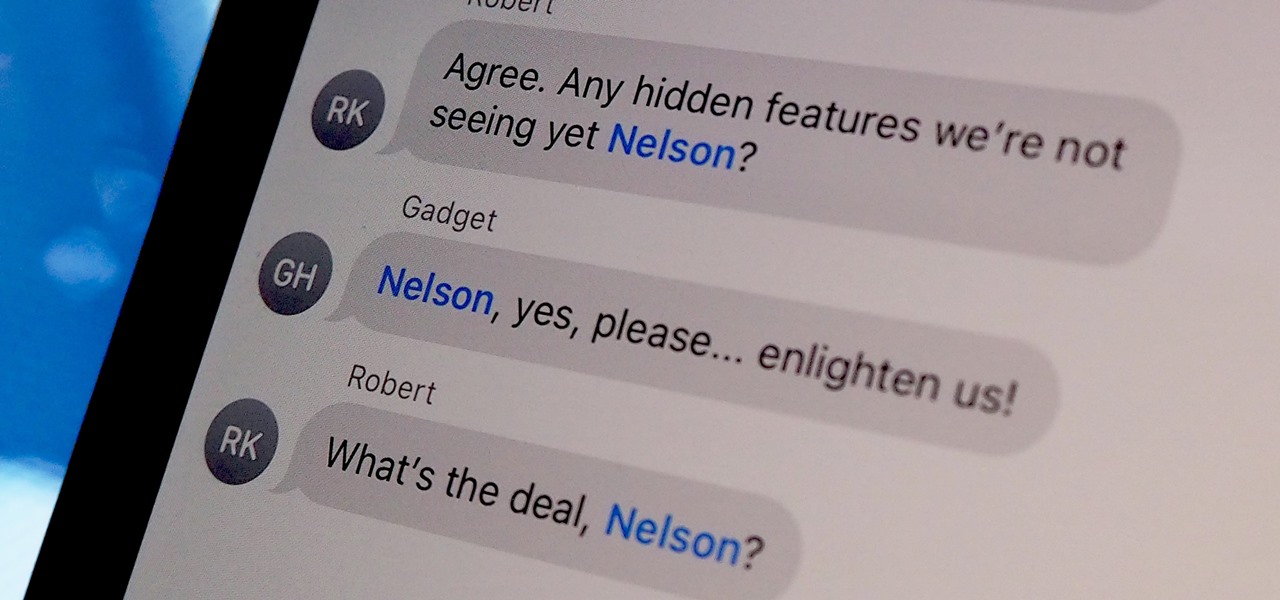
One of iOS 14's more exciting features lets you tag someone in a group iMessage chat in the same way you would @ someone on Twitter, Instagram, and other social media platforms. Even if the conversation is muted, you can get notified when you're mentioned, which helps you jump in only when needed. But if you want complete silence, then disable contact tagging notifications altogether.
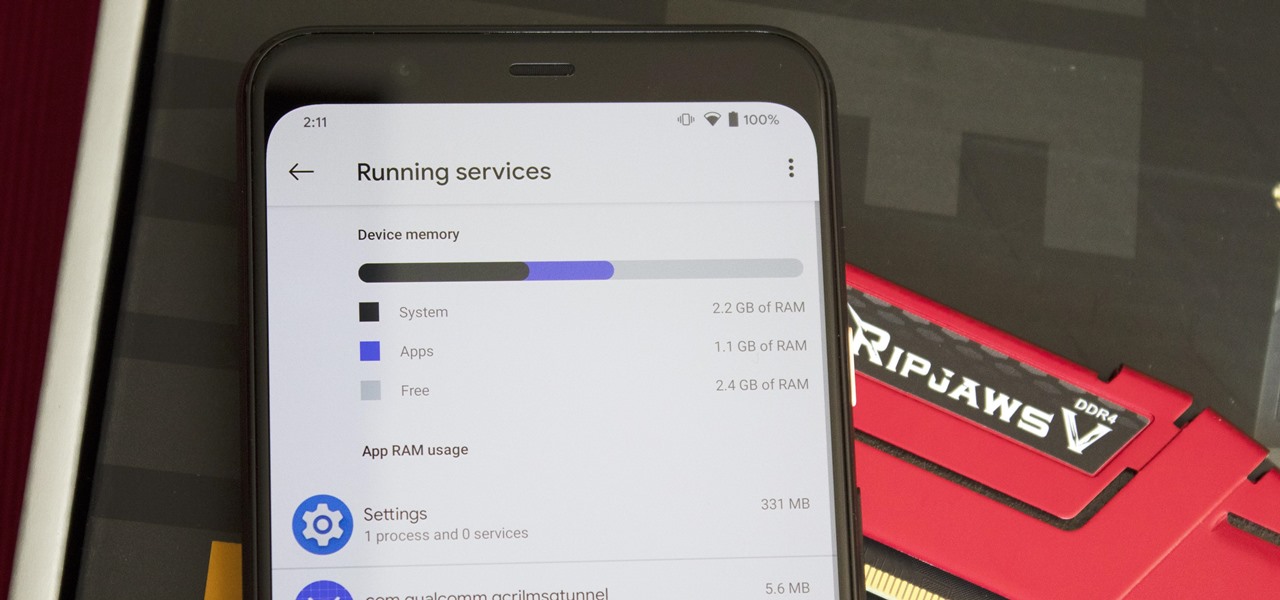
Not every app is designed well. With nearly 3 million apps on the Play Store and countless more that you can sideload from other sources, there are bound to be a few stinkers. And many of them do a terrible job using RAM.

OnePlus releases some unique and exciting features before they start catching on with everyone else. Their OxygenOS is often considered the cleanest and most useful variant of Android. However, there are still a few key features OnePlus has yet to bring to their devices. This includes a proper lift to wake option.
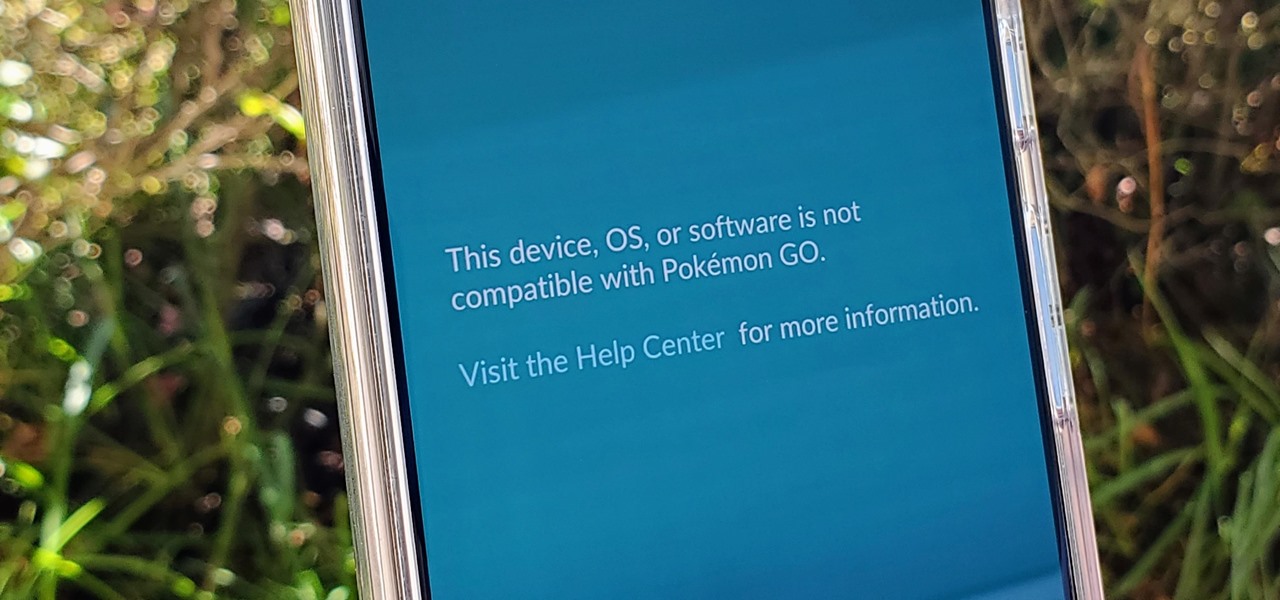
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

If reaching up to access Camera controls like the flash, HDR, and timer wasn't bad enough, it's gotten a lot more tedious on recent iPhones like the X, XS, and 11 series thanks to their tall displays. If you have a jailbroken iPhone, however, you can easily fix this issue using a free tweak.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.
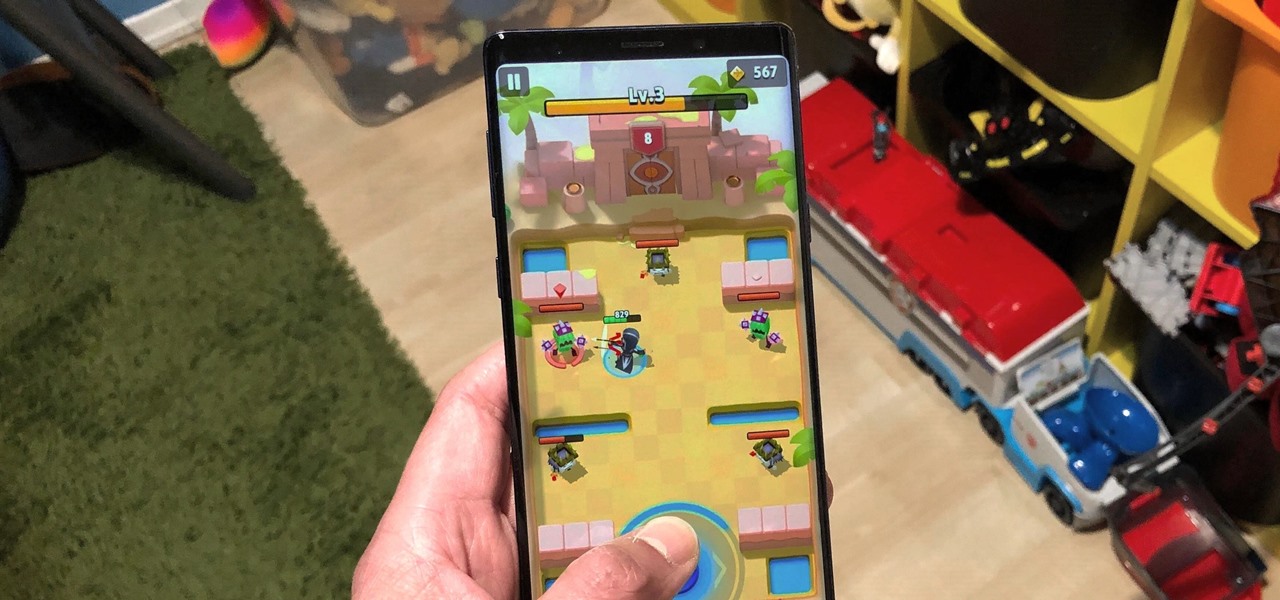
When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

Just when we thought the AT&T partnership with Magic Leap wouldn't really take off until the latter launched a true consumer edition of the Magic Leap One, the dynamic duo jumped into action this week to offer the current generation headset to customers.

The era of AT&T and Magic Leap has quietly entered a new phase that ramps up the mainstreaming of the cutting edge augmented reality device.

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.

Last year, Razer kicked off a new trend by building a smartphone from the ground up with mobile gamers in mind. At the time, many thought the Razer Phone solved a problem that no one really had — but a year later, we're starting to see that gaming phones are perfect for more than just Fortnite players.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

The game wizards at Insomniac take pride in diving deep when it comes to world-building, and the same is true for the studio's latest title for Magic Leap One called Seedling.

While last year's revelation that Apple slows down iPhones with aging batteries left a bad taste in users' mouths, the company's $29 battery replacement program was a step in the right direction. However, all good things must come to an end; Apple will soon shut down the program, leaving users to pay the full $79 to replace their faulty batteries.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.
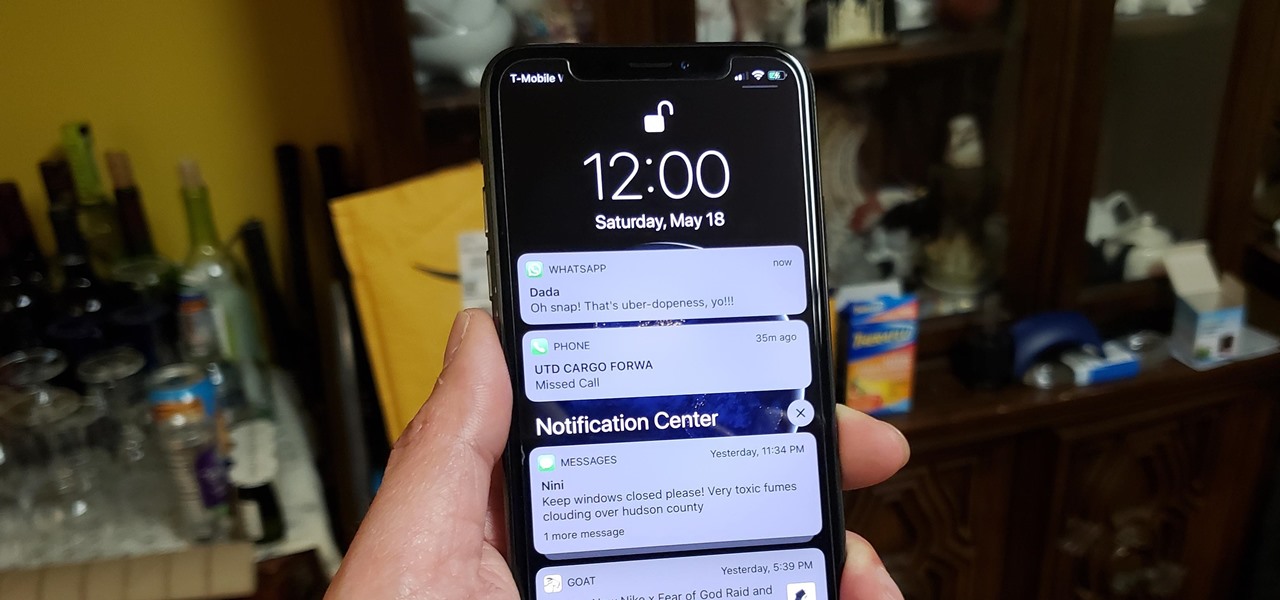
WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the sender, however, there are simple tricks you can perform to give yourself plausible deniability.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

From its official launch back in September, iOS 11 has been equal parts revered as it has been criticized. Even with all the great, new features we've come to expect from a major iOS update, plenty of bugs and glitches have forced users to overlook the positives. Perhaps that is why, four months later, 25% of iPhone owners are still running iOS 10.3 or earlier.
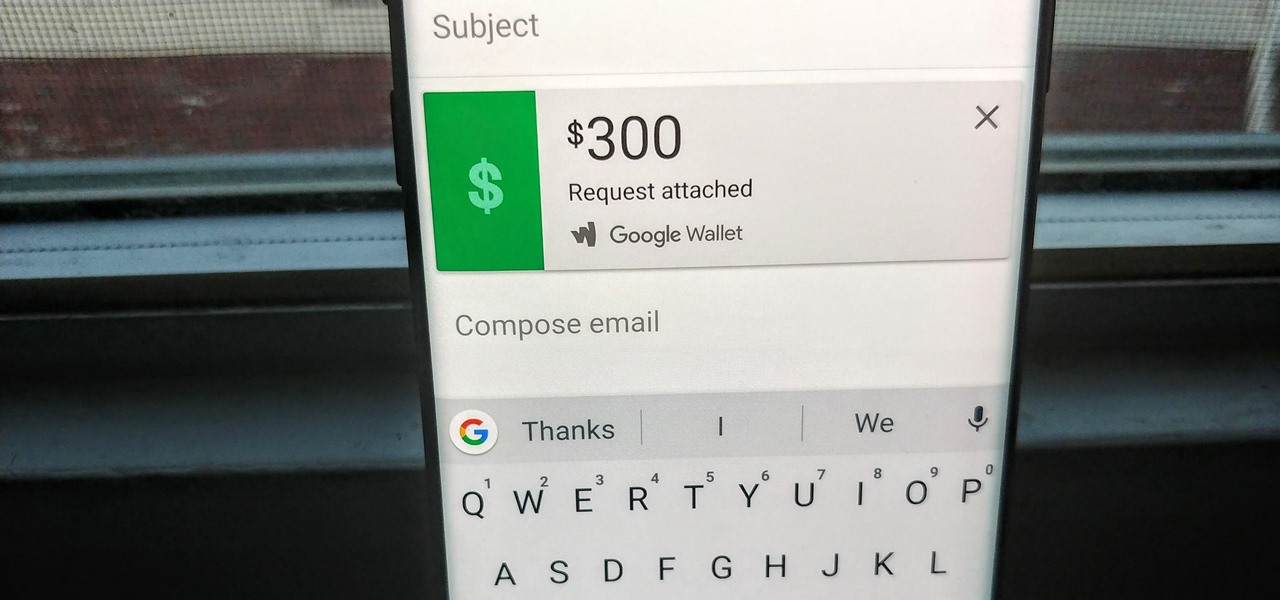
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.