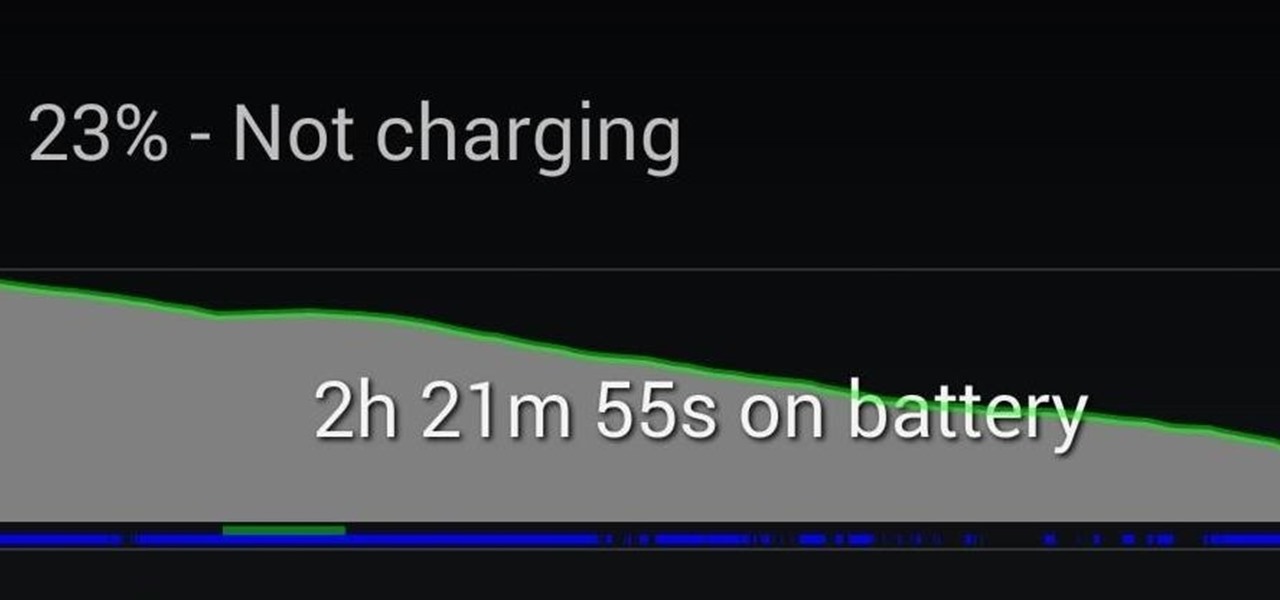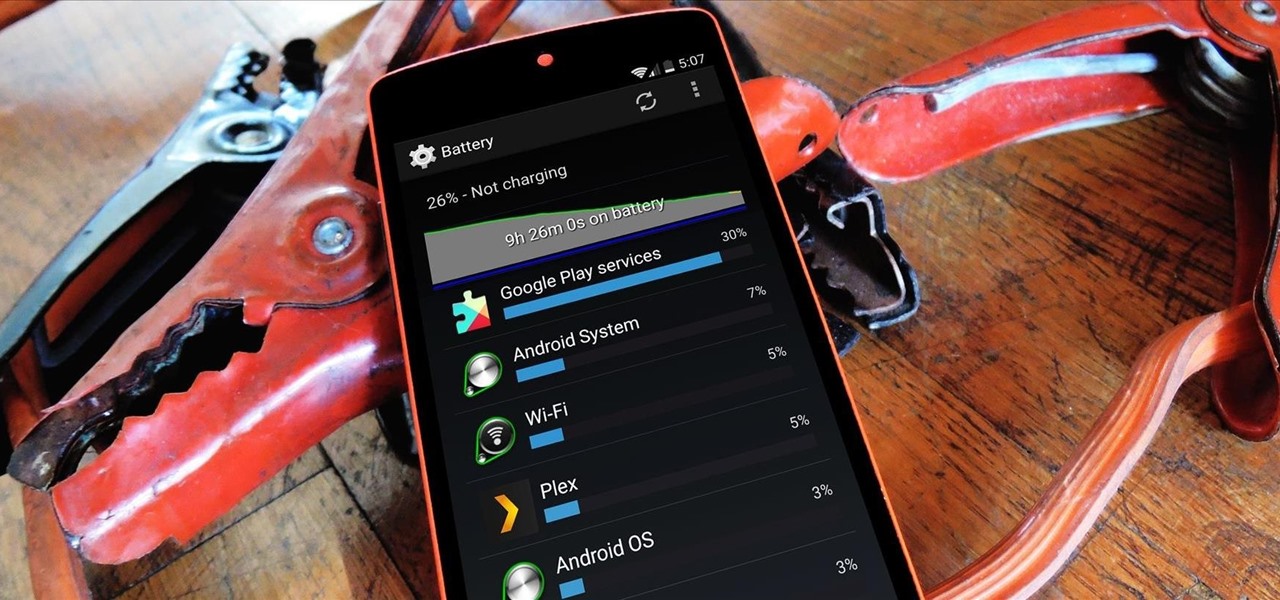
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.

It's time to enjoy one of America's longest lasting favorite pastimes. No, not baseball—pranking our friends! With the internet currently overrun with countless pictures and memes of cats, there's no way for your feline-hating friends to surf the web without coming across a kitten or two. But things can get worse for them. Way worse...

I love cheap, nutritious food: lentils, rice, toor dal, and other beans and grains. Even popcorn. The only problem is that they usually come in floppy plastic bags that make measuring ingredients more difficult. I usually open up one corner of the bag only to have everything come spilling out all at once whenever I try to pour out measured amounts.

There are two types of bricks ("brick" as in "bricking your phone")—soft and hard. Soft bricks are recoverable—something has probably gone wrong with some critical system partition, causing a bootloop or inability to boot in some way. Fine. Re-flashing everything should fix that instantly. Hard bricks are not recoverable—if you manage to hard-brick your Nexus, you are in trouble.

Replacing your wallpaper is one of the easiest and quickest things you can do to keep your device from going stale, but it goes way beyond just picking an image from your gallery. If you use the Google Camera, you can create some really awesome 3D lens blur backgrounds, but what if you want more wallpapers on your wallpaper?

So you've decided to transform your drab backyard into a Japanese Zen garden. You've made the right choice. Yes, tire swings and crab grass can slowly kill the soul. That being said, a bit of planning lies ahead. This article offers a list of How To tips, culled from the Landscape Network and other professional Japanese style landscapers, for planning an effective Japanese style landscape in your home. Step 1: Research.

The fact that we own a Nexus means we get to experience the Android interface exactly as Google intended it. But that doesn't mean we can't make a UI tweak here and there, does it?

If you've followed our guide on unlocking KitKat's real full screen capability using the immersive mode mod, then your status and navigation bars will be hidden when not in use, giving you a more expansive full screen experience.

I'll be the first to admit how horrible my memory is, whether it's remembering to take out the garbage or paying a bill on time. That's why I regularly utilize the stock Reminders app on my iPhone; it's definitely compensated for my memory deficiencies.

If you're a Febreze fanatic, you're well aware that the "odor eliminator" can be pretty pricey, and that's reason enough to stop buying it.

Battery life is precious to all mobile device users, and nothing is worse than running out of it. The only thing that can save a device from the dreaded low battery warning is the charger, but who carries those around?

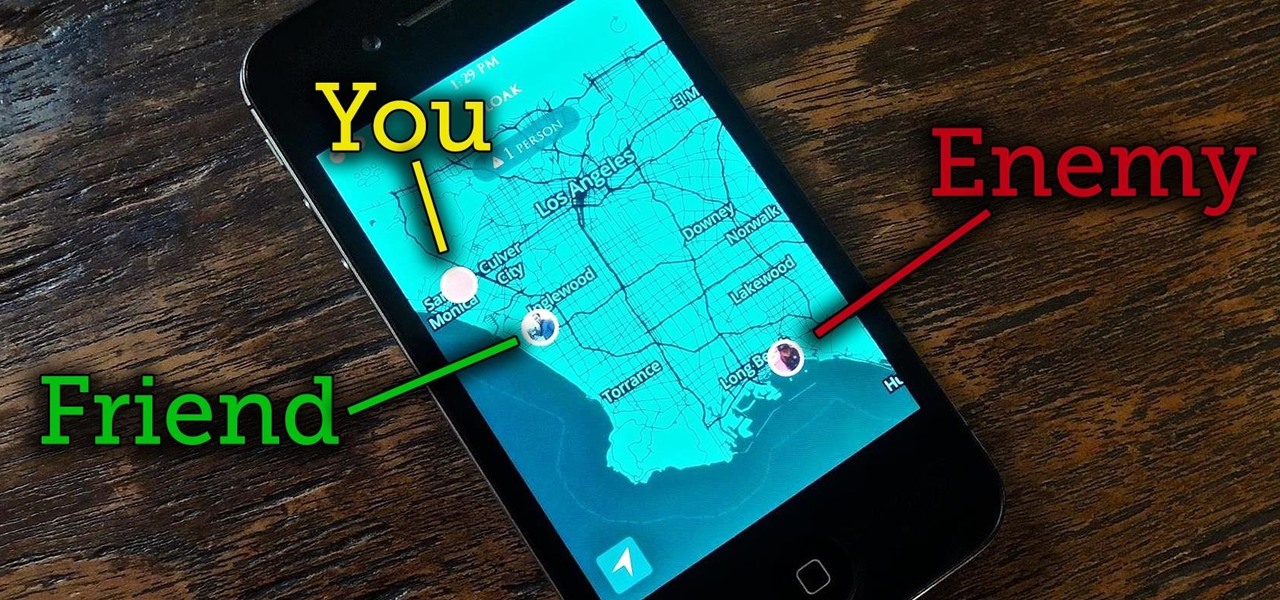
I never want to bump into my ex-girlfriend while out in the city (talk about a buzz kill), so if I could get an alert telling me that she's at Shortstops down the street, I'll avoid that area completely. This is where the new, interesting app Cloak - Incognito Mode for Real Life from dev Brian Moore comes in.

In direct competition with Pandora, iTunes Radio, and Spotify, Samsung has just launched Milk Music—a strangely named, yet completely free music streaming service for Android.

Update (March 18, 2014): Skype has issued an update to their Android app, and among other things, has "fixed" the runaway camera process issue by creating a workaround...and that's about all we know. No details were provided, but with the considerable uproar over the bug, let's hope it's been squashed for good.

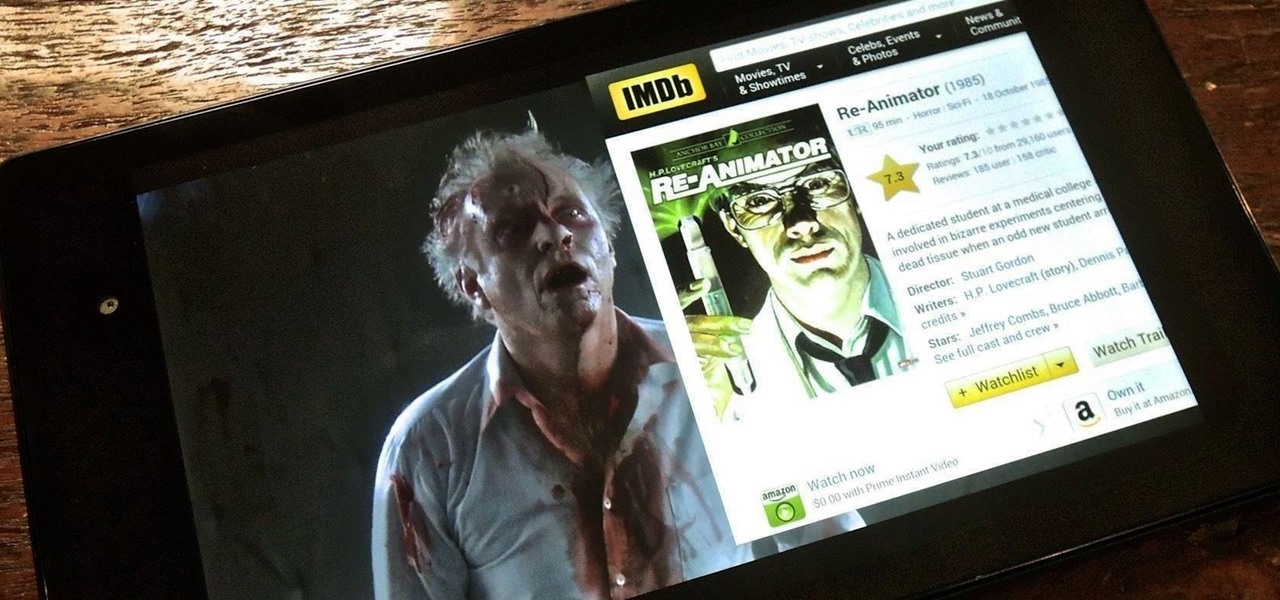
Efficiency is one integral attribute that I need from my Android device. I want to be able to multitask like a maniac and do things on the fly. While multitasking itself is nothing new, actually being able to watch Netflix while scrolling through IMDB at the same damn time was reserved mainly for newer Samsung-ier devices.

Having instant access to monitoring your battery level is critical, especially when you're traveling or forget your charger at home. You need to know how much juice you have so you can adapt accordingly.

Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon:

There used to be a time when I thought that gift cards were whack. And then I realized that I would basically be picking my own presents. And as much as I love my grandma, you really only need so many sweaters.

Phone interruptions are commonplace, as is evident by my historically epic missed phone call list, ranging from annoying sales people to my mom checking in every five minutes to see if I'm still alive.

According to the CDC, less than 33 percent of adults eat the recommended servings of fruit each day in the United States. When it comes to vegetables, Americans are even worse, averaging less than 27 percent. Most adults should consume at least 2 servings of fruit and 3 servings of vegetables each day, depending on age, gender, and level of physical activity. Eating lots of fruits and veggies has been linked to a better immune system, faster weight loss, and way too many other health benefits...

First off, let me say this—using real steam power is dangerous, and heavy, and just generally not worth it when you have modern alternatives. Except, you know, if you're a Steampunk. Or this guy:

UPDATE: The whitehouse petition has received enough signatures to require a response from the government. Your voices have been heard! Now we wait...

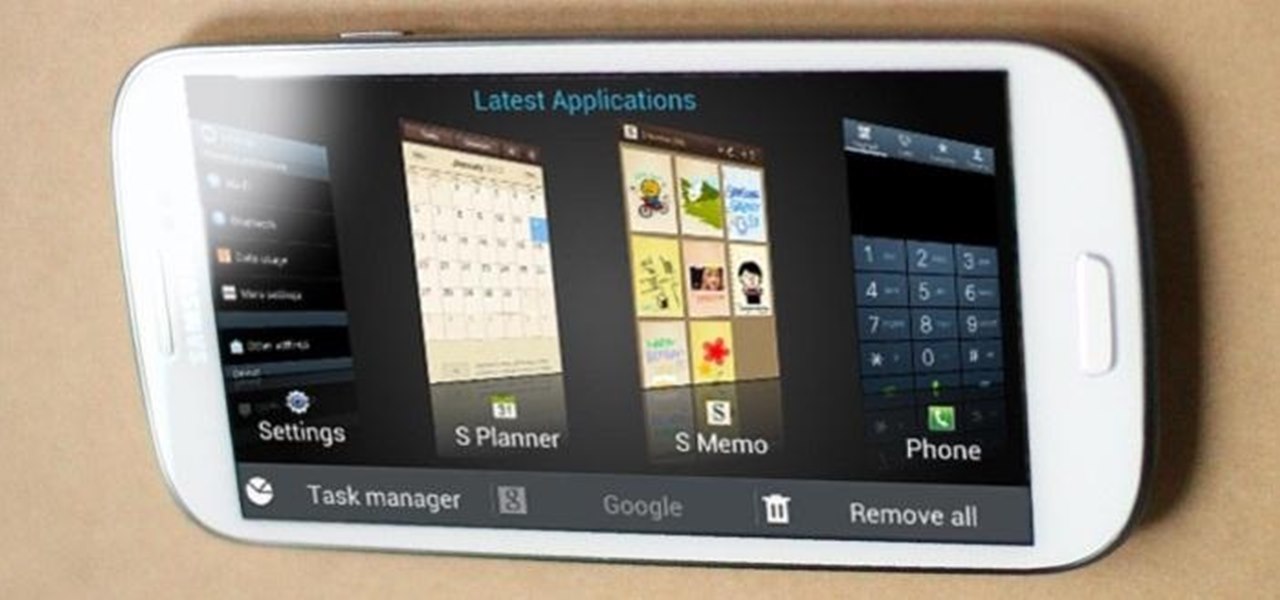
As much as I love my Samsung Galaxy S3, I'm always on the lookout for cool features I can borrow from other smartphones. One of the most recent "borrowed" features I've added to my S3 is the Galaxy Note 2's smart rotation feature, which uses the front camera to detect my face-to-screen angle, which then rotates my screen accordingly. But the S3 already comes packed with some awesome features, as well as some less-than-stellar ones. One of these less-than-stellar features is the task manager, ...

Believe it or not, capturing a beautiful shot of a vehicle is more difficult than you think. Sure, you can just snap a photo, but capturing the design, detail, and essence of the car is a whole other story. Lighting, location, settings, and angles are play into how well the photographic representation turns out.

As a kid, I remember hearing the myth that Twinkies could last forever. The rumor was that they were made from chemical ingredients that caused the Twinkies to stay fresh and edible for years and years. Right along with the cockroach, Twinkies were supposed to be the only survivors of the nuclear holocaust that would destroy the entire world. As I got older, I realized the rumor wasn't true. Twinkies actually have a shelf life of just 25 days. And with the news that Hostess is going out of bu...

When you're a kid, the best part about Halloween is the free candy, but if you're past your trick-or-treating years, there are still plenty of things you can do. With all the costumes, scary stories, and pranks, what's not to love? And now, you can even use your smartphone to celebrate.

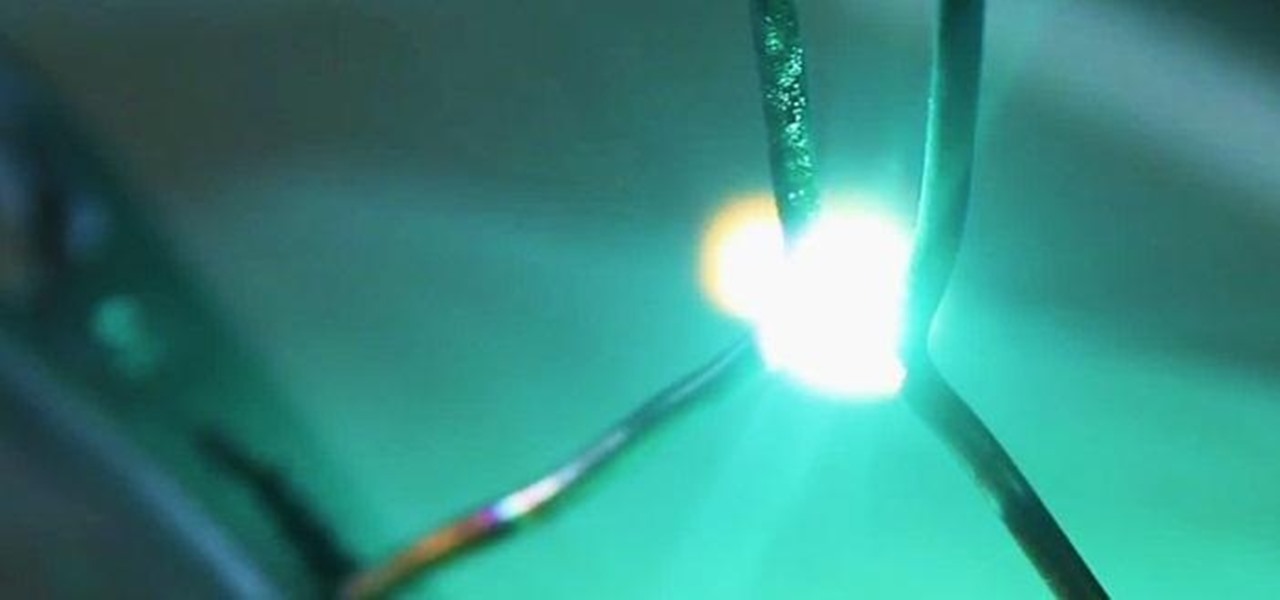
With the microwave oven transformer (M.O.T.) salvaged in a previous project, a simple electrical circuit can be rigged to get high voltage arcs to fly outward and upward along a "V" shaped spark gap.

If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots.

Traps are great, but sometimes you don't want to kill anyone, you just want to know when they're around. When that's the case, check out this handy alarm system that uses the power of doors! Doors, you say? Yes, doors! Some of you may already be familiar with how obnoxious doors can be in Minecraft, but if not, check out this video of it in action:

In this how-to video series, learn how to play disc golf from expert disc golfer C.R. Willey. C.R. will teach you what you need to know to get started playing disc golf, with tips such as what equipment you need, what accessories are good to buy for playing disc golf, and how to play with proper disc golf etiquette.

Check out this three-part series on how to play Super Smash Bros. Melee (advanced). This is not a beginning tutorial for all you newbie gamers, it's more detailed and advanced for pros, or semi-pros.

Dr. Christopher Lepisto on a study that proves Kolorex (Horopito) is as effective as the leading pharmaceutical drug to killing fungus, without the side effects.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Pumpkin carving and decorating is a favorite October pastime. After you've carved an amazing design or face into a pumpkin or two, you want to show it off through your window or set it out on your porch for the neighbors to see.

There's an ongoing debate about whether or not it's safe or even desirable to rinse meat before you cook it. Many fall into the anti-rinsing camp, saying that it's not effective at dislodging bacteria, especially on poultry, as we've discussed before. Meanwhile, some argue that rinsing certain meats, like bacon, could be beneficial since it possibly prevents it from shrinking.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Do you have what it takes to join the elite and become a sniper? Maybe not in real life, but in a video game, you surely have the guts to become a military sniper. In Sniper: Ghost Warrior, you control a highly trained sniper, amongst a team of US Special Forces, as you try to control a military coup d'état (or just "coup") in the island of Isla Truena, which is a small fictional Latin Amercian country. Can you and your sniper team save the country from ruin?

If you like 2D side-scrolling video games, then Shank's your man. Shank is full of "beat 'em up" action and combat, perfect for any gamer addicted to the old style of play. Shank is available on both the Xbox Live Arcade (Xbox 360) and PlayStation Network (PS3). But this Mahalo walkthrough for Shank is for the PlayStation 3.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.