The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.
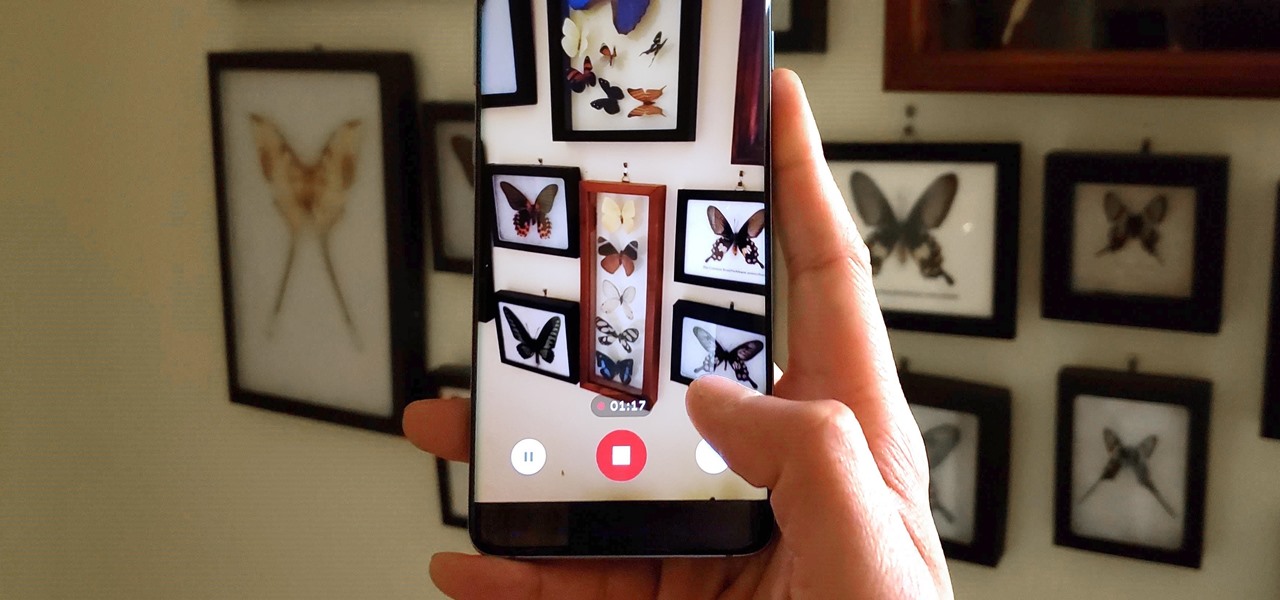
Though primarily a Pixel exclusive, Google Camera has become the go-to camera app for many Android users. Not only does come with a standout features like Night Sight and capture better photos than most stock camera apps, but it's also packed with functionality that makes it a one-stop-shop for all your photo and video needs.

Slow motion recording is an incredibly handy feature that works by capturing moments at a higher frame rate than they're played back at. Timing is everything when recording in this setting, so if you want a user-friendly app that keeps device interactions to a minimum and leaves you to focus on capturing your subject, Google Camera will surely fit the bill.
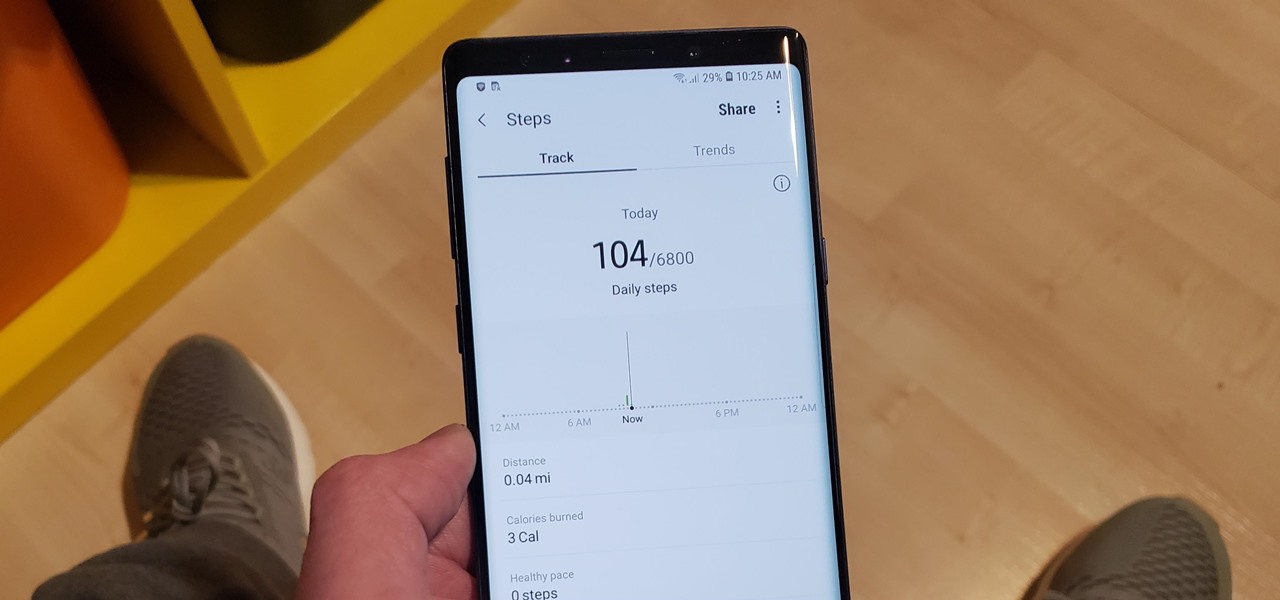
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Any sufficiently cool new technology will be immediately repurposed to do something even cooler. Such is the case with Apple's iPhone X and its Animoji feature, which has led to something completely unanticipated: Animoji karaoke.

Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others, such as the Chicago Cubs winning the World Series.

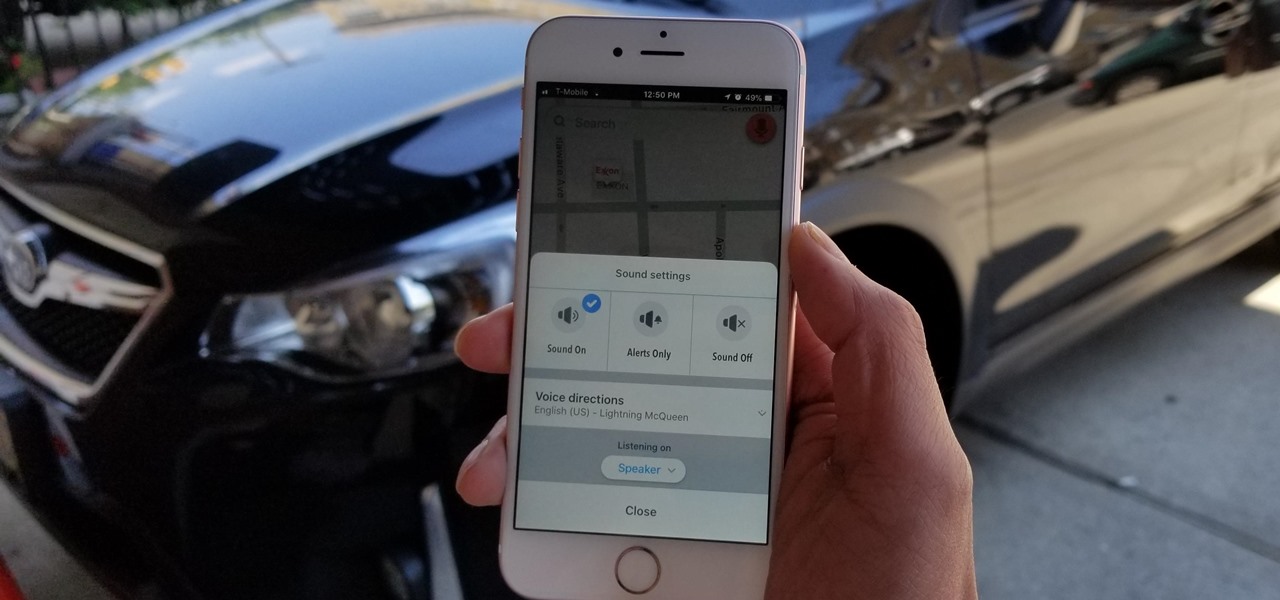
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

You were the chosen one, Snapchat! The new download numbers for the social media app show just how hard it will be to bring them back to the light after the rise of the Instagram empire.

Beginning in November, National Football League (NFL) fans visiting New York's Times Square can come as close as any civilian can to stepping onto a professional football field. All for less than the price of a pair of cleats.

We know your time is valuable to you, so starting this week — and continuing every Wednesday — we are going to release weekly Dev Reports that quickly highlight important news and updates that augmented and mixed reality developers should know about.

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

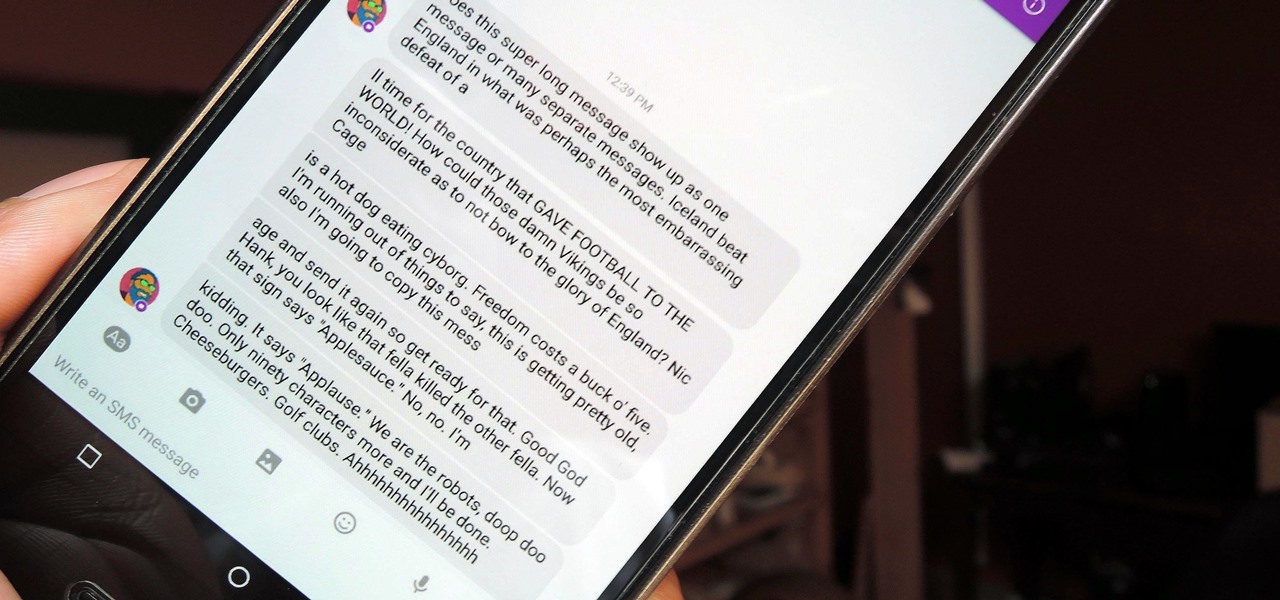
Depending on your carrier and the texting app that you use, sending long SMS messages from an Android phone often results in the recipient being hit with a barrage of fragmented, out of order texts.

When you wear a holographic computer on your face, you gain some things and lose others. That's certainly the case when using Skype in Microsoft's HoloLens. Some video chats will work better because your caller can see what you see, rather than your face—but others just feel weird.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

So, how does someone keep their hacking life completely secret? What This Is:

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

Bored of your old casual tees? Try these hacks to make them snazzy in a jiffy!

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Check out this video from CouponCodesHero on hacking a vending machine in no time. All you need is a little packing tape and some paper money, then fool the machine to either get free stuff, or use the "change" to get free money!

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

This video has 7 fraction hacks that can save you time when working with fractions. The hacks are: Adding fractions without a LCM

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

10 Life Hacks: 1.Wifi Booster

How to hack an Oreo, i.e. dunk an Oreo in milk perfectly.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence.

In a 10 button Nesquik vending machine or other 10 button vending machines, you can hack to get credited for free drinks.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang for your buck, here are a few ways you can hack your own Nook.