Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my hacker novitiates!

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

We're always looking for great food hacks to help us become better cooks who can create delicious food with less waste, fuss, and hassle. You never know where the next good tip will come from, so we've all learned to keep our eyes and ears wide open.

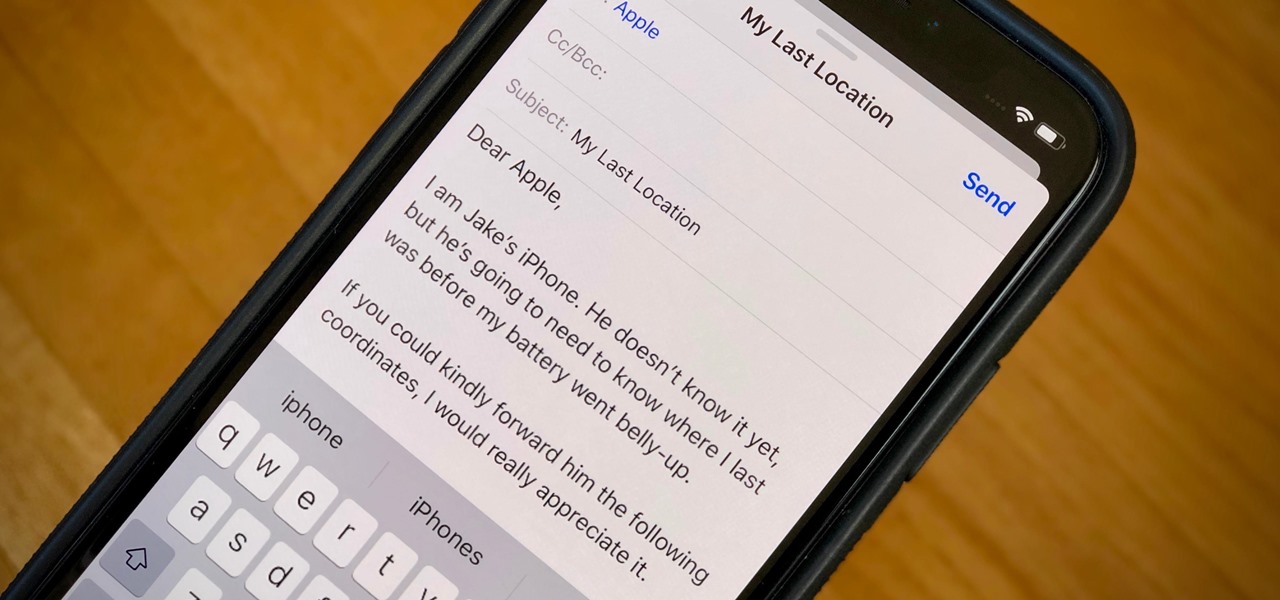
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Creating a class in Black Ops 2 is kind of like an art form. Every player has an insane amount of options for creating a character for all sorts of situations. Combining perks, with secondary weapons, and attachments allows for a wide range of killing options. But in order to unlock a lot of these perks and attachments, you need to gain XP. Gaining XP and collecting tokens is the lifeblood of the online gaming experience.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

Wouldn't it be awesome if your glasses could detect when it's bright outside and automatically darken? Well, the technology has been around for a while, but it'll set you back a few hundred bucks.

If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Given that megastar internet search engine Google became its own verb a few years ago, we've all come to acknowledge that the wide and ever-expanding engine is becoming more powerful than ever before. You can take a look at your own house from outer space via Google Earth, you can look at famous paintings - down to the very last grizzly brushstroke - via Google Art Project, and you can look at what's hot and what's not in Spain - or anywhere in the world - with Google Trends.

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

With custom ROMs said to be impossible on Verizon's new Motorola Droid X, thanks to something called eFuse, many users will be deterred from trying to mod their Droid X mobile device. But it's only a matter of time before a hacker figures out a workaround for the Droid X, but if you want to try to hack it yourself, this video tutorial will get you started. It will show you how to get into the Droid X bootloader. It could possibly help you "root" the cell phone, if you're lucky.

The alluring and stylish GiannyL is the DIY fashion design guru of the web. Do-it-yourself has never been so sexy before. Her fashion design video tutorials make new outfits not only hot, but cheap and easy. And recycling and reusing old clothing is not only practical, but eco-friendly.

This is episode 3 of the series. You will learn how to hack a basic combination lock. Using some basic household items such as a can of soda, scissors and the lock. He demonstrates and takes you through 7 steps, such as cutting the top of the can off, cutting a rectangle size of the aluminum from the can, cut some lines and shapes into it, fold the tops inward and back. He then uses this contraption on the combination lock arm to slip the aluminum piece down into the lock to release the lock....

Trevor4Ever595 shows us how to hack Hell Tour on Kongregate tours. First start the game by clicking 'New Game'. Complete the first level. Once you're on level two complete it as usual, and at level three you can start doing stuff. Open the cheat engine, click the process list, and click on your browser. Multiply your souls by 8 and put it into first scan. Go back to the game use some of your soul and then open cheat engine and multiply it by 8 again. Go down and click the frozen box on your c...

Trevor4Ever595 teaches you how to hack the game Space Attack using Cheat Engine. You start the game, select a level and pause it using P. Open up Cheat Engine, open the process list, select Firefox or whatever internet browser you are using. Then you will want to use the search box to search for the amount of money you have in the game. A lot of values will come up to the left of the search box. Go back to the game, earn more money and then search for that new amount. Cheat Engine will only r...

If you're looking to get on top of the game Plock for Facebook, then sometimes cheating is the best answer (and easiest). With Cheat Engine, you can easily hack Plock.

Find out a quick and easy way to level up in Ninja Warz. It's pretty simple and no cheating app like Cheat Engine is required.

FarmVille hacks, cheats, glitches! FarmVille is the hottest application on Facebook from Zynga which lets members manage a virtual farm by planting, growing, and harvesting crops, trees, and livestock. Grow delicious fruits and vegetables and raise adorable animals on your very own farm!

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get to do tricks in Wizard101. This video will teach you how to these simple tricks if you don't already know how.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.

Follow these step by step instructions to learn how to hack a vending machine, giving you two Cokes for the price of one. You and your friends will love this cool vending machine con. Never go thirsty again. Just check out this instructional video and start hacking vending. Machines nowadays are SO smart that they know you haven't received your drink and give your money back. Humans nowadays are SO smart that we can make ourselves not receive drinks we paid for, get our money back, and then b...

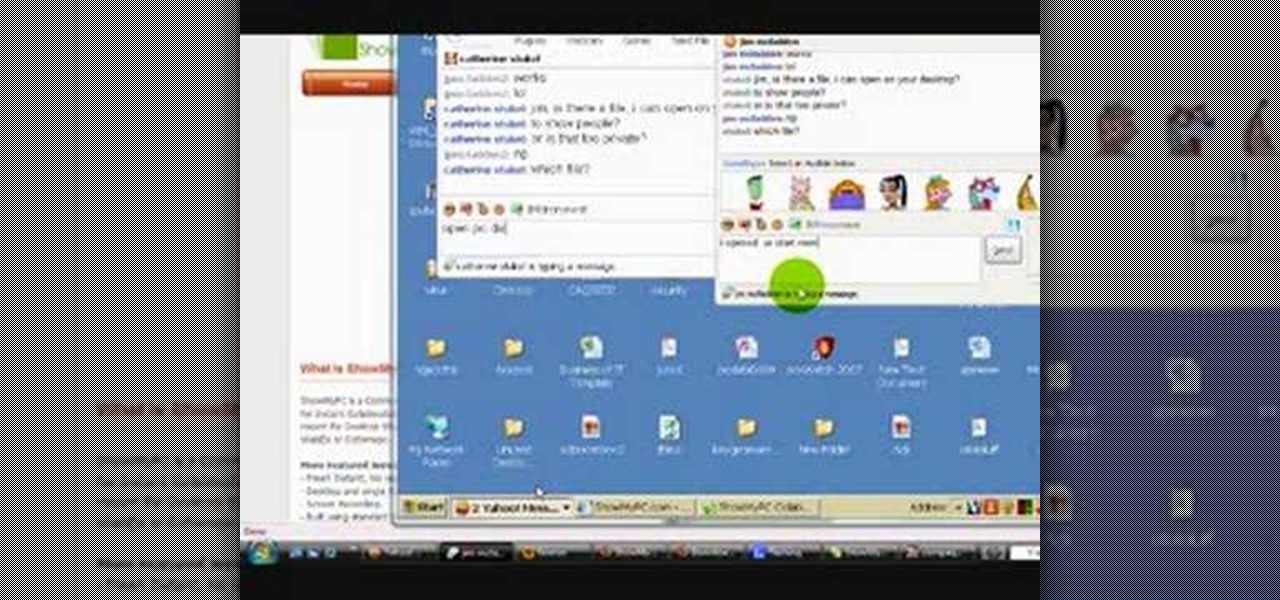
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the website ShowMyPc.com and be able to see what your target has been up to. Even better, you can use that computer and the files on it as if it were your own desktop!

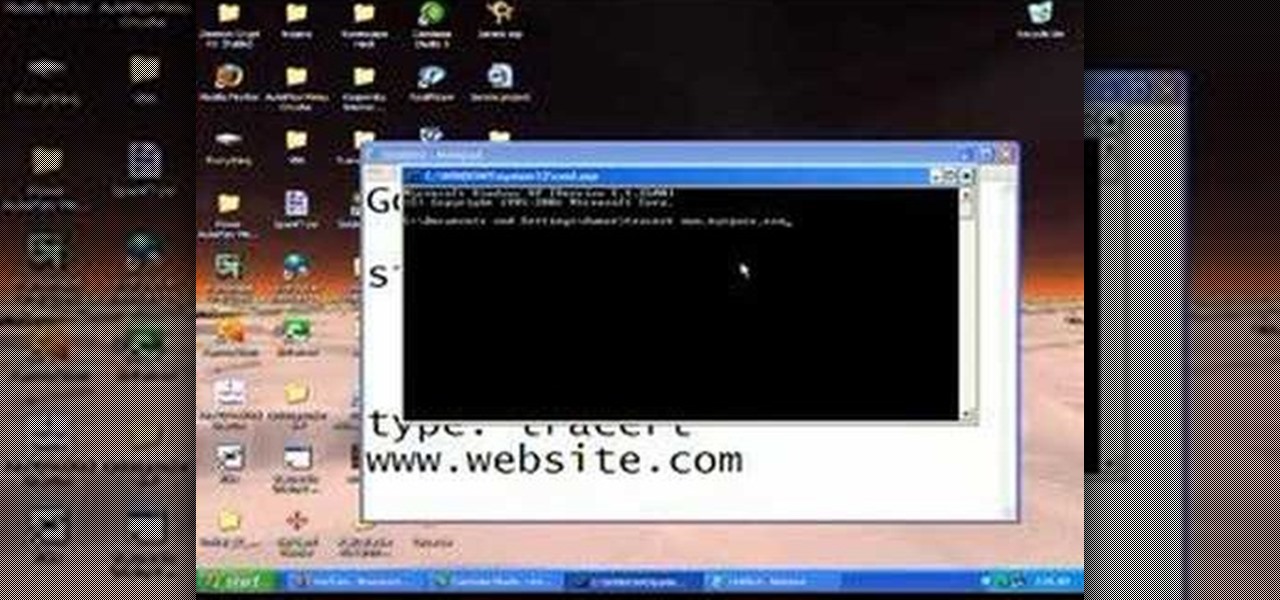
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black screen. Then, copy and paste the IP address that appears inside. Now you can take this and use it to go to Facebook while you are at school. Or, you can go to any website that you'd like to that you normally can't go to at sc...

In this video, we learn how to hack your iPhone 3G. To do this, you will need: iPhone 3G, Firmware 3.0 or 3.1 file, charger cable, and the Redsn0w program. First, connect your phone to the computer and then start up the Redsn0w program on your computer. Turn the phone off, then restart it. The phone will now connect to the program on the phone and it will say "downloading jailbreak data". You will see a pineapple walking around on the screen. After this, restart your phone again and it will b...

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

Hacking the Wii is a fun, easy, and rewarding process for any of the more geekily-inclined. This two-minute video will walk you through the whole process except for the first bit where you copy the files here to an SD card and insert it into your Wii. This video will get you the rest of the way, which is pretty simple and should allow you to do all sorts of fun new things with your Wii. Check this out and crack your wii console today!

Unlocking all of the features in a game is one of the most annoying parts of owning one oftentimes, especially if the unlockable content is a major part of the game and the game is less fun without it. This video will teach you how to hack Call of Duty: Modern Warfare 2 for the Playstation 3 to unlock all of the Special Ops missions in the game. Don't waste your time playing through all of single player, do this and unlock the potential of your game!

Nothing says chic like DIY. With spring and summer just around the corner, this breezy and elegant tube dress is all you need to stay cool. See how to make a DIY chic tube dress in this video from GiannyL.

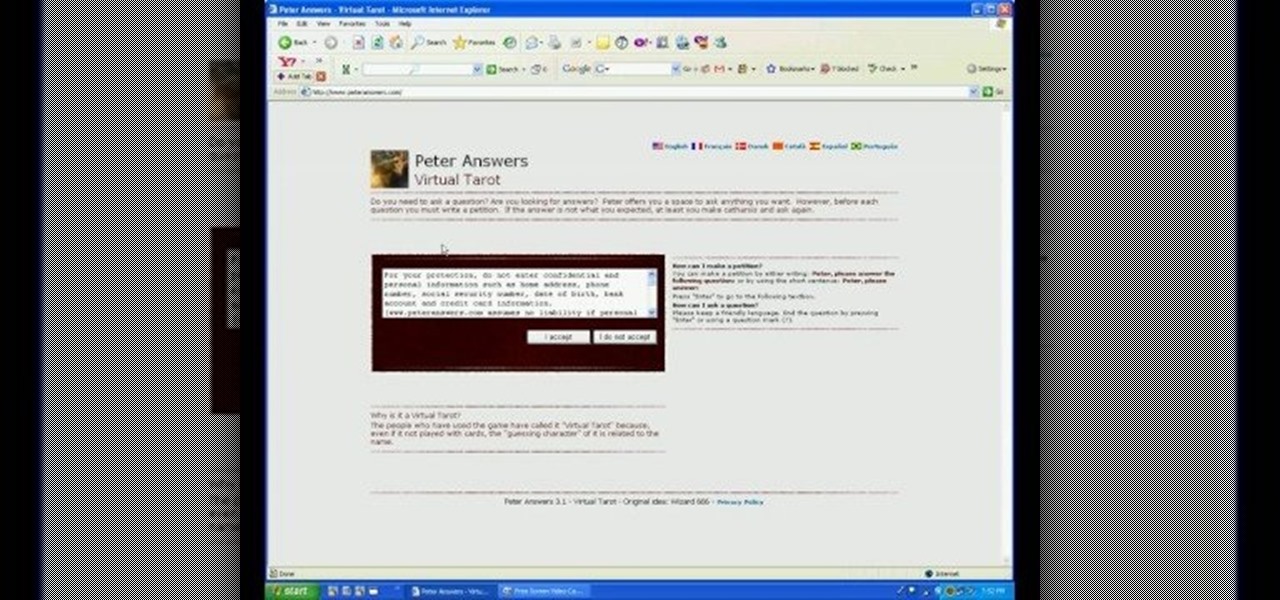
Peter Answers is a fun website online that you can use to play pranks on your friends. This site is easy to access, free and requires no downloads.