How To: ALL-in-ONE HACKING GUIDE
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

As crazy as it sounds, there are times when bottles of wine go unfinished. I love a glass or three of vino, but am often guilty of not finishing the bottle. Sometimes I don't have the time to finish it, and other times I like it so much that I open bottle number two and can't finish that.
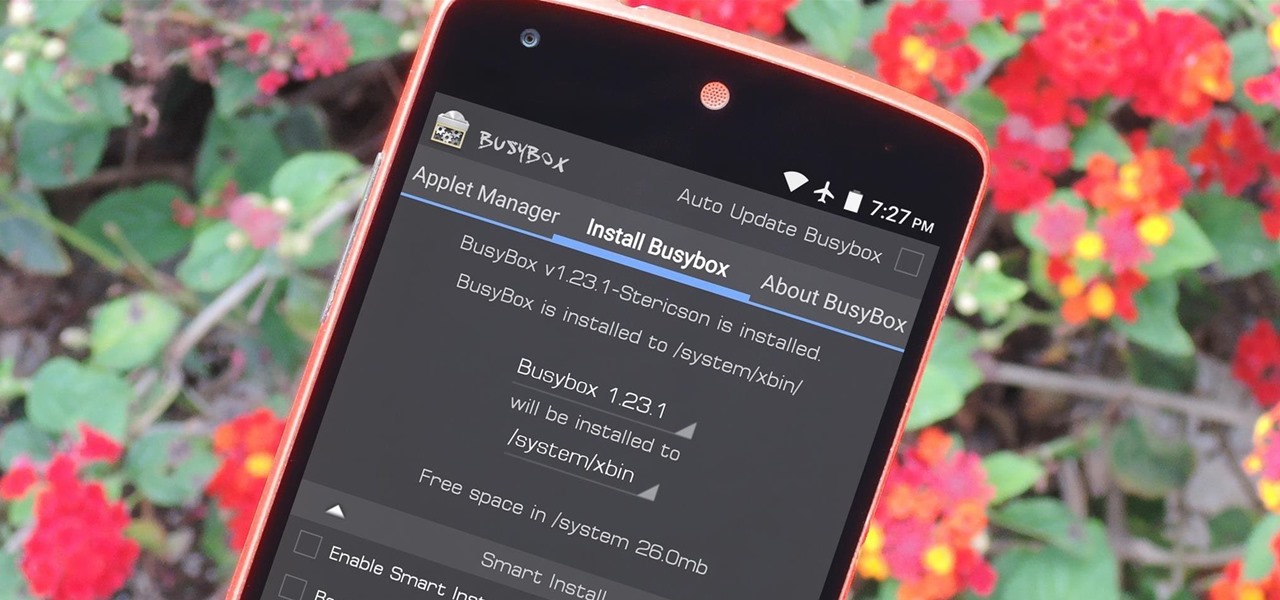
If you're a rooted user, you've probably heard the term "BusyBox" by now. Many mods require these powerful root commands, but the process of installing BusyBox can be a bit confusing for the uninitiated.
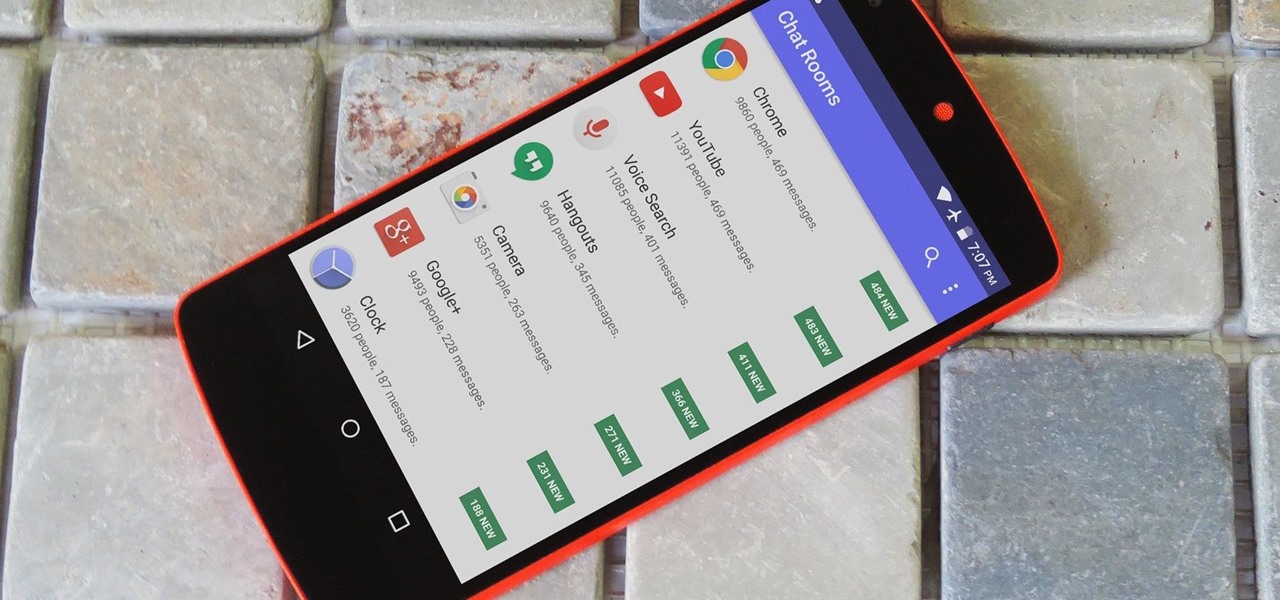
As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.
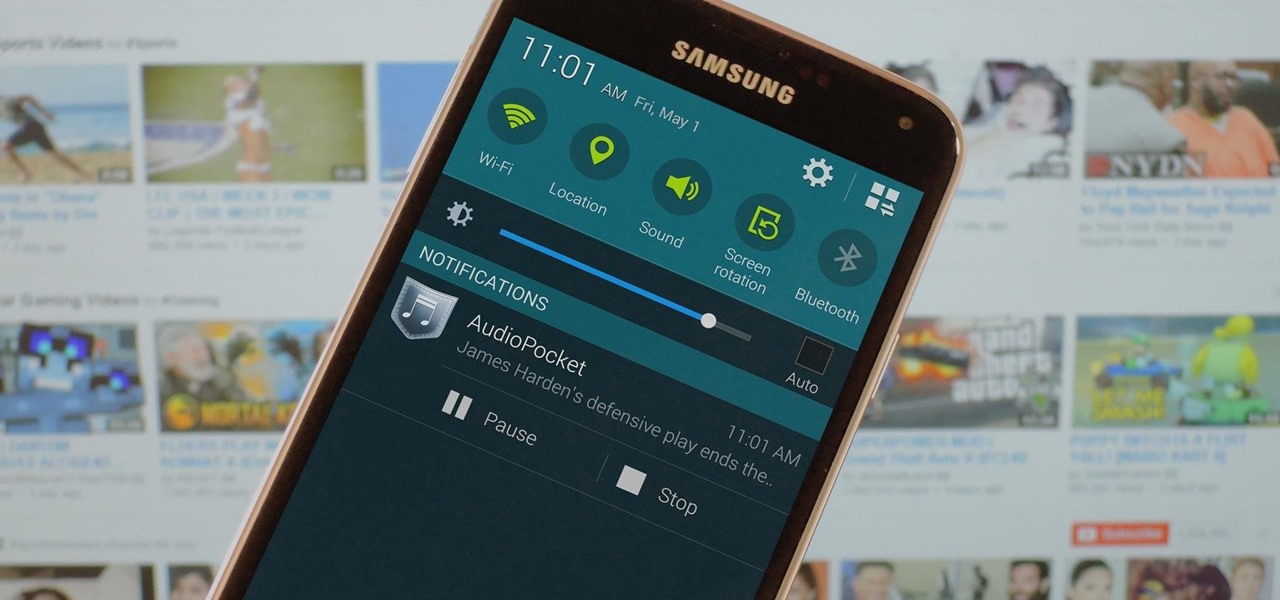
When you think about it, YouTube may actually have one of the largest music collections on the planet. This is why, at $10 per month, Google's new YouTube Music Key subscription is a solid value for many users, especially with its inclusion of Google Play Music.

Mobile service providers have an uncomfortably strong grip on the Android platform as a whole. For instance, all four U.S. versions of the Galaxy S6 and S6 Edge play their carrier's obnoxious jingle every time they boot up. You don't get any say in the matter—if you buy your phone from one of the big 4, you're a walking audible billboard.
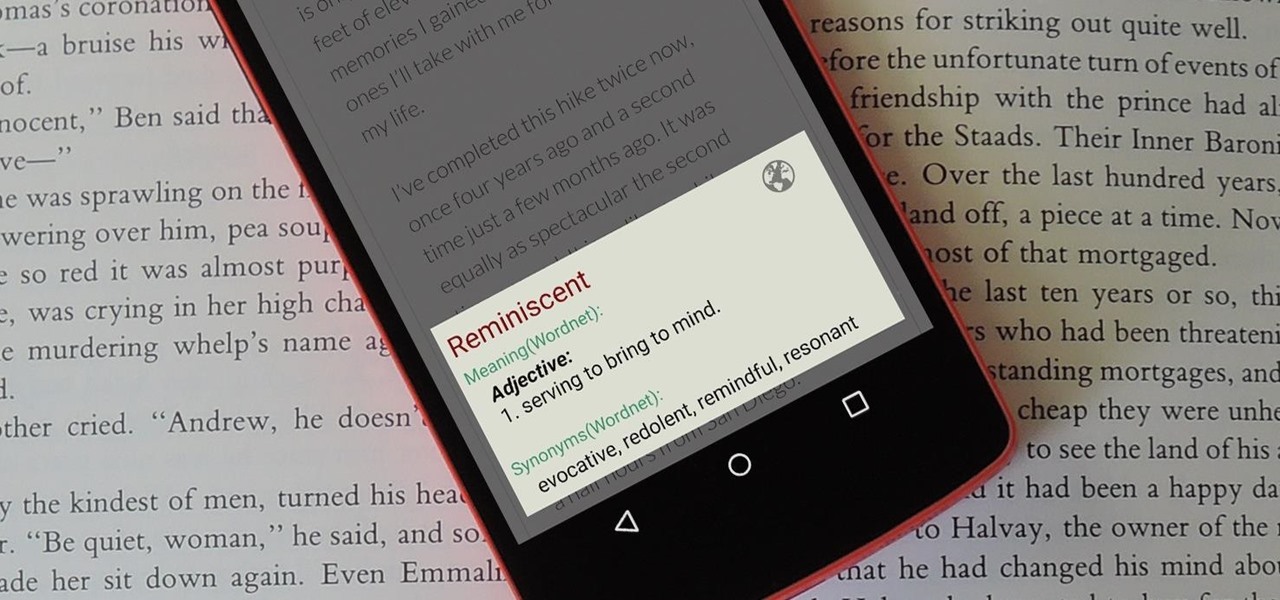
When you're browsing the web, going through emails, or reading a book or magazine, you'll occasionally come across a word or phrase that you haven't seen before. This would be a perfect time to have some sort of built-in dictionary lookup service, but most Android apps lack such a feature.
We all have those moments where we're bored or lonely, and in those times, just having anyone to talk to would be awesome. But maybe your friends are all busy, or everyone you know is at work and nobody's responding to your text messages.

Some variants of the Galaxy S6 will allow you to silence the camera shutter sound with an option in the app's settings menu. But this is not true of all models, plus there's an additional annoyance—when you're filming video and you get a notification, you'll actually hear this tone on the final recording.

One of Android's biggest strengths relative to iOS was the ability to switch to a third-party keyboard. While Apple has finally included this feature in its latest OS and leveled the playing field a bit, the variety of options still pales in comparison to what's available on Android.

Android has a permission that allows apps to draw on top of other apps, but as fun as that may sound, it has mostly been used to create floating multitasking utilities. While these can certainly be useful, it would still be nice if this permission were taken literally and we could actually draw on top of apps.

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:
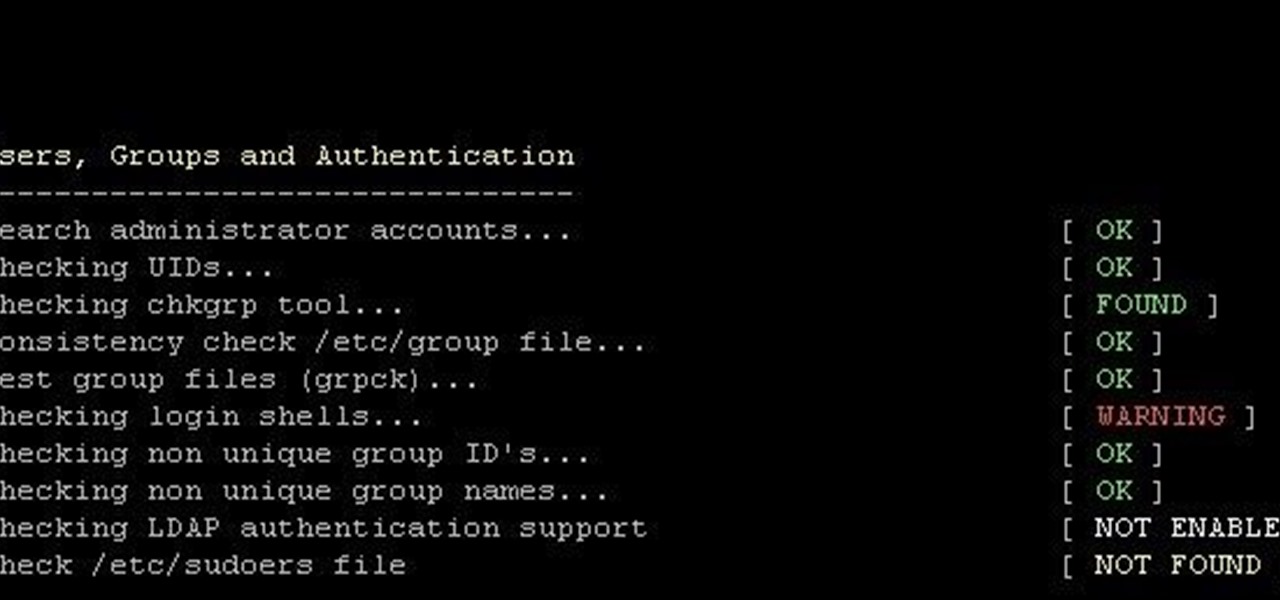
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

Pizza. It's seen you through your best and worst times. It was there during your first relationship and the subsequent dumping. It got you through college, and maybe even your twenties. Domino's phone number is programmed in your speed dial, and though you won't admit it out loud, you love pizza, you really do.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

We've already shown you how to dunk a regular-sized Oreo cookie while keeping your fingers pristine, how to upgrade Oreos into different desserts, and even make them into lazy ice cream sandwiches. Now we're going to introduce you to a few other essential Oreo hacks that will give you a brand-new outlook on a classic snack.

Parties are a great way to celebrate and have fun with your good friends, so to make sure your next party rocks, I've assembled some of the biggest life-hackers on YouTube to bring you 10 outrageous party tricks your guests will not forget.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

When our Nexus 7s upgraded to KitKat, one key piece of functionality was lost in the mix—Flash support. Of course, even before that we never had official support on the Nexus 7, but hacks seemed to do the job just fine. As it stands now, Google remains on the warpath against Flash, opting instead for HTML5 use, specifically in Chrome (where Flash never worked anyway), and of course Adobe stopped supporting Android long ago.
Rounded rectangle icons are so 2007. Sure iOS 7 tweaked them a bit, but with the clean new approach to design that software is taking today, they're starting to look dated. Today I'm going to show you how to go full circle with your iPhone's icons, and the results are actually pretty awesome.

Holidays can be challenging, especially around Christmastime—but not if you invoke your inner MacGyver spirit. In my latest "life hacks" guide, I show you 10 amazing tips and tricks that'll hopefully make your holiday season a little more merry.

Welcome back, my aspiring hackers!

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Are you a messy burger eater? Ants and fruit flies invading your home? Hate drinking warm drinks? Find out the quick and easy DIY solutions to these problems with these 10 amazing tips and tricks for the summer.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.
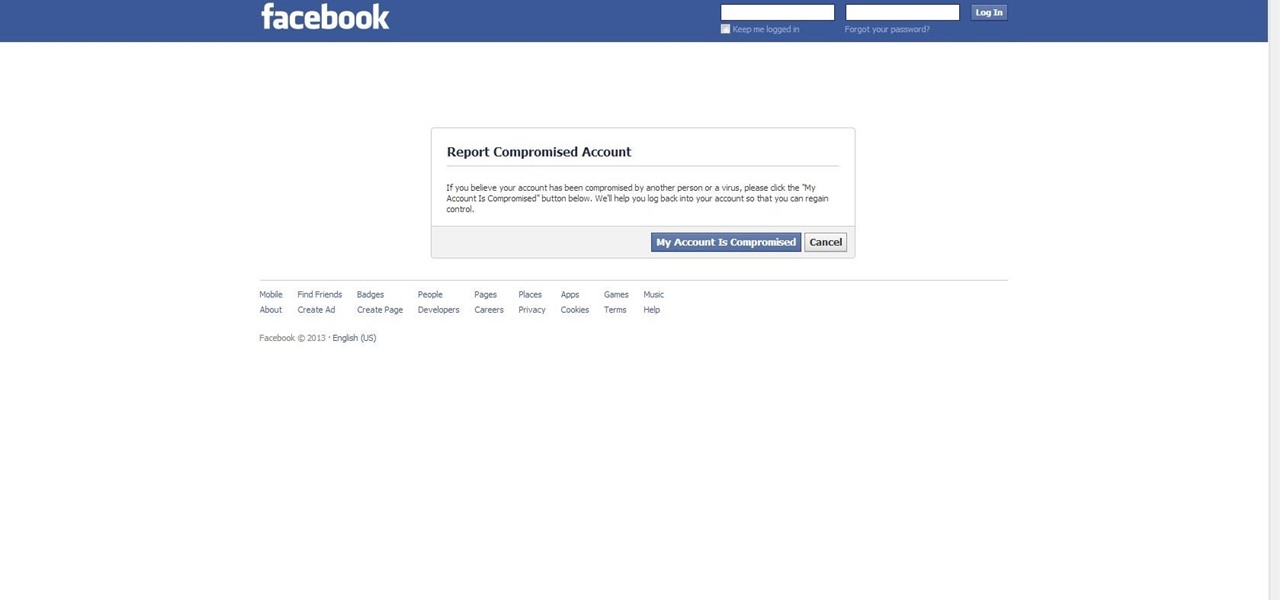
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Here's a fun hack! In this clip, we learn of a bug that will permit you to circumvent the passcode lock screen on any iOS 4.1 iPhone 4. For detailed, step-by-step instructions, and to get started using this exploit yourself, watch this video guide.
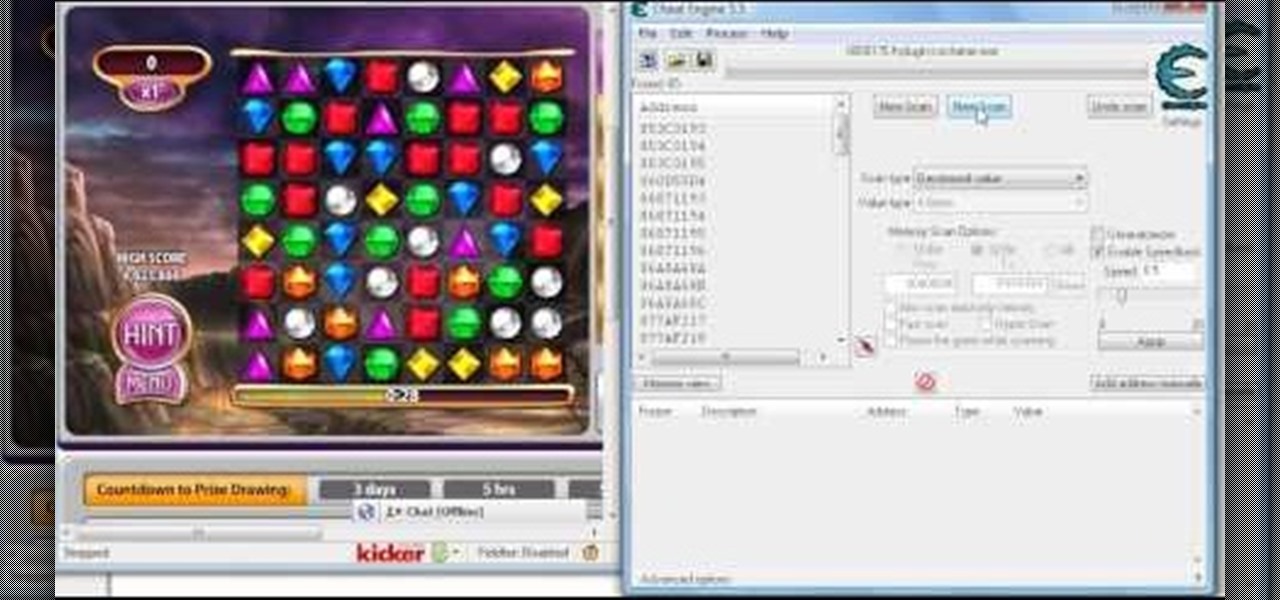
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).
In this video tutorial, we learn how to use advanced search parameters like "define" and "site" to access hidden functions of the Yahoo! search engine. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this how-to from the folks at CNET TV.

Love We Rule? Looking to line your virtual pockets with digital lucre? Earn coins in We Rule can be easy! This gamer's guide presents a complete overview of the process. For more information, including detailed, step-by-step instructions, and to get started earning your own coins in We Rule without use of hacks or cheats, take a look.