Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.
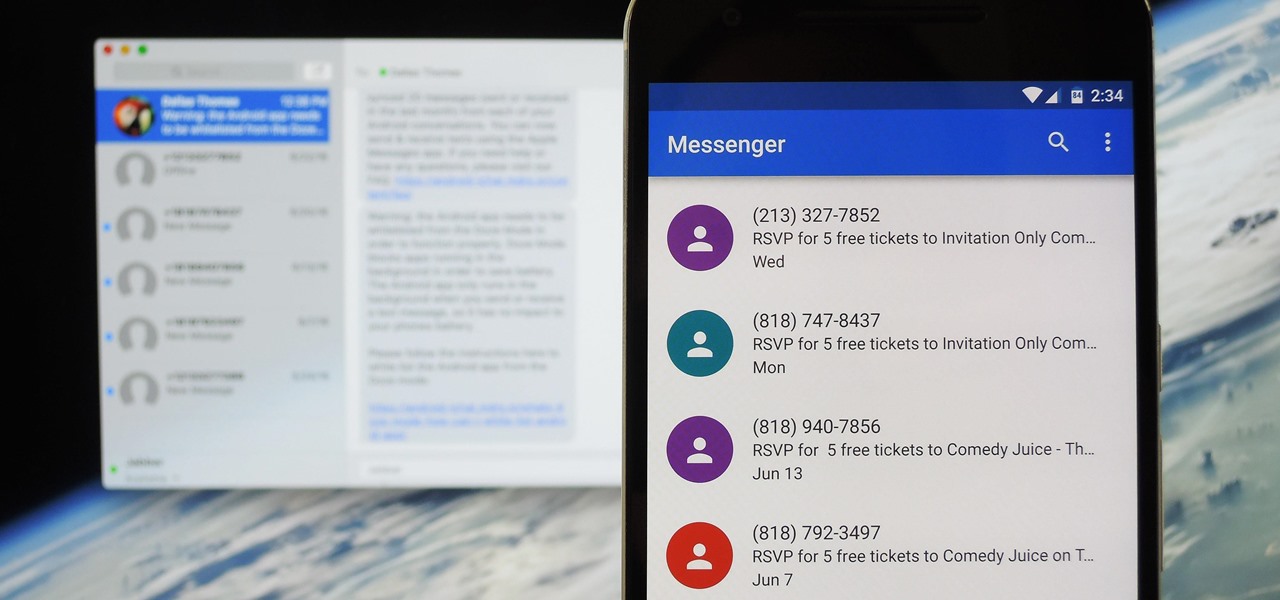
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

Vacuum sealers keep food fresher longer by first removing the air from plastic food preservation bags and heat sealing the bag to keep air out. They have rapidly become a popular way to keep your frozen food fresh.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Bubble, bubble, toil, and trouble... it's time for another Halloween-themed food hack. This time, we'll be tackling the pumpkin cooler—an idea that has been done to death on DIY blogs around the internet. And there's no point in reposting something that everyone else has done, so I decided to change things up a little bit.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

The grill isn't just a place for burgers, dogs, and corn anymore. Fresh fruit has made its way into barbecue territory, with results so good, you'll think twice about settling for fruit salad. While some fruits are common enough on the grill (like pineapple), these six are more off the beaten trail: peaches, watermelon, strawberries, mango, and pears.

Watched a great guide on hacking things through time by the most powerful hacker on the planet, Hackerman.

On the Apple Watch, along with the conventional emojis we've grown to love, there are new animated emojis that add a new dimension of fun for you and your friends. Unbeknownst to many, these animated faces also include a feature that allow you to change their color.

There are a lot of frustrations when you're dealing with cramped living quarters, but you can do a lot of good cooking in your tiny kitchen if you make the most of your space. These storage hacks will make it easy to cook delicious meals, no matter how limited your square footage.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

You can make Siri do all kinds of things it was never designed to do. From installing it on older jailbroken iDevices to using it to bypass an iPhone's lock screen, people have managed to come up with some interesting hacks—and that's only the beginning.

There isn't as much use for old-school four-function calculators anymore since we all have them on our cell phones now. If you've still got one lying around, you can hack it to play recorded sounds, use it to make a metal detector, or turn it into a custom name plate that says anything you want...

LED throwies are cheery glow-dots you can make in seconds from simple components and stick to any ferro-magnetic surface. But that's just the beginning — here's how to hack and modify them.

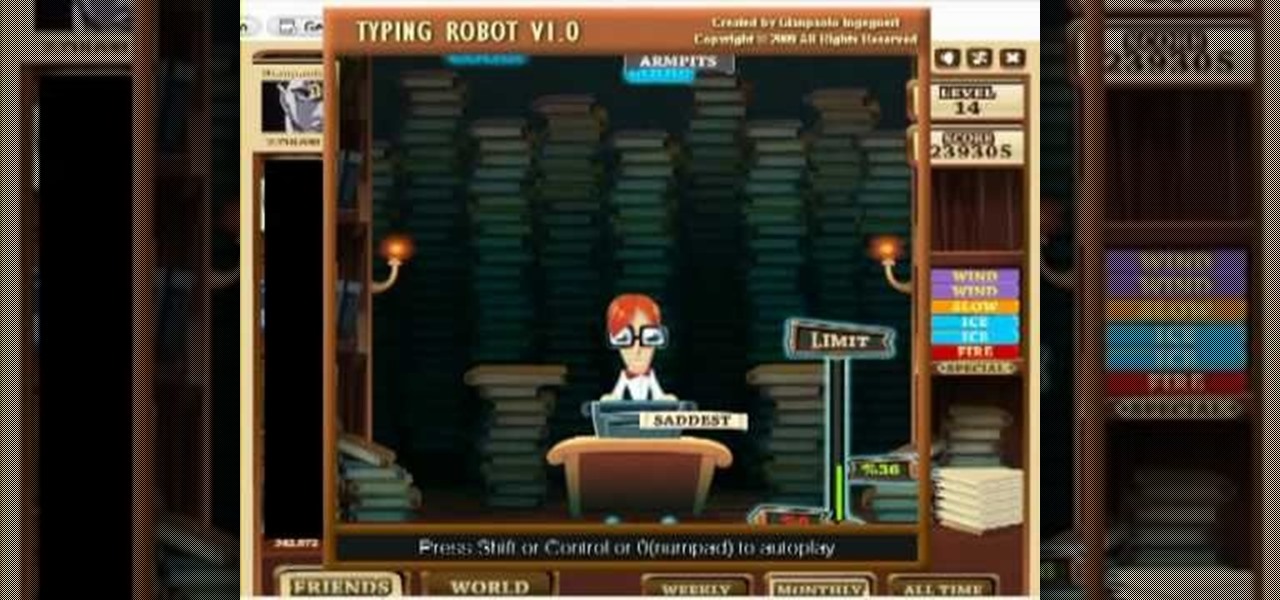
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

Are your DVDs piling up? Want to get rid of a few, but don't think you can sell them to anyone? No problem— recycle them! If your desktop is in need of some zest, this hack will show you how to light things up— in style! It's an electric rotating disc that's powered by a motor and has LEDs that create a cool lighting effect.

MAKE and Collin Cunningham brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

RSbot is no more, long live powerbot! If you want to hack Runescape this program, no matter it's name, has been the authority since 2006. If you've ever wanted to use it or tried to and had problems, this video is for you. It will teach you how to download and install powerbot 2.+ in Windows 7, fix the JDK error that plagues so many users, and how to load scripts into the program and implement your cheats. One-stop Runescape cheat shopping!

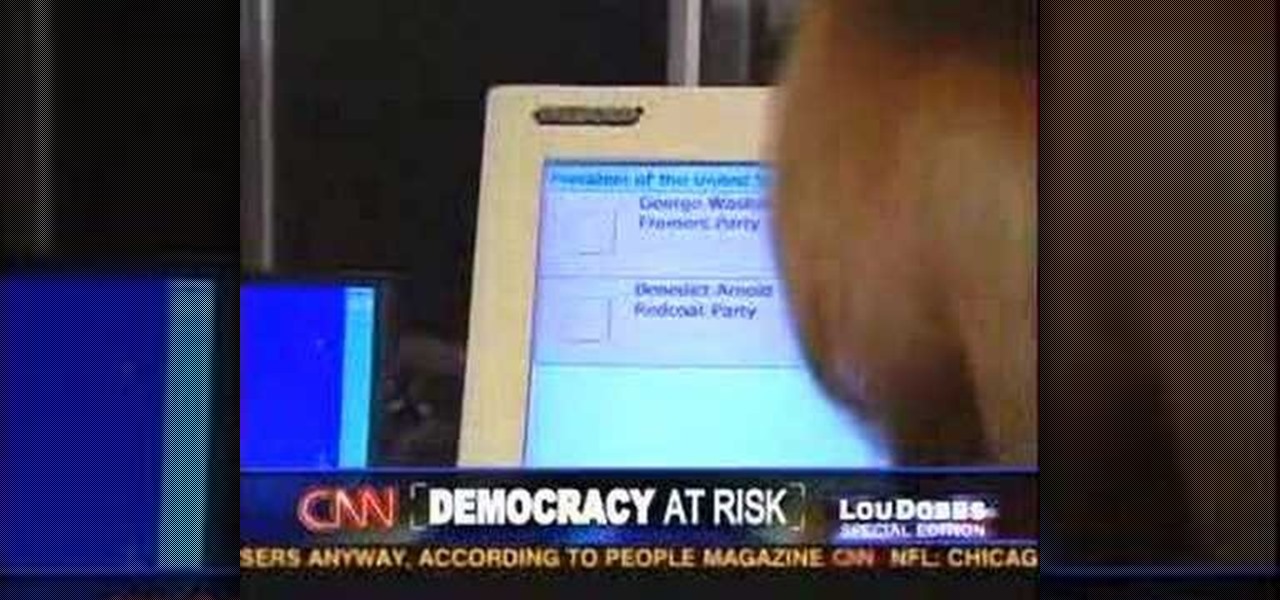
It only takes a minute to steal a U.S. Election!

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

If you are looking for a UAV code for homebrew then this is the video for you. Check out this site for codes and follow the video to learn how to hack COD: Black Ops with a UAV code.

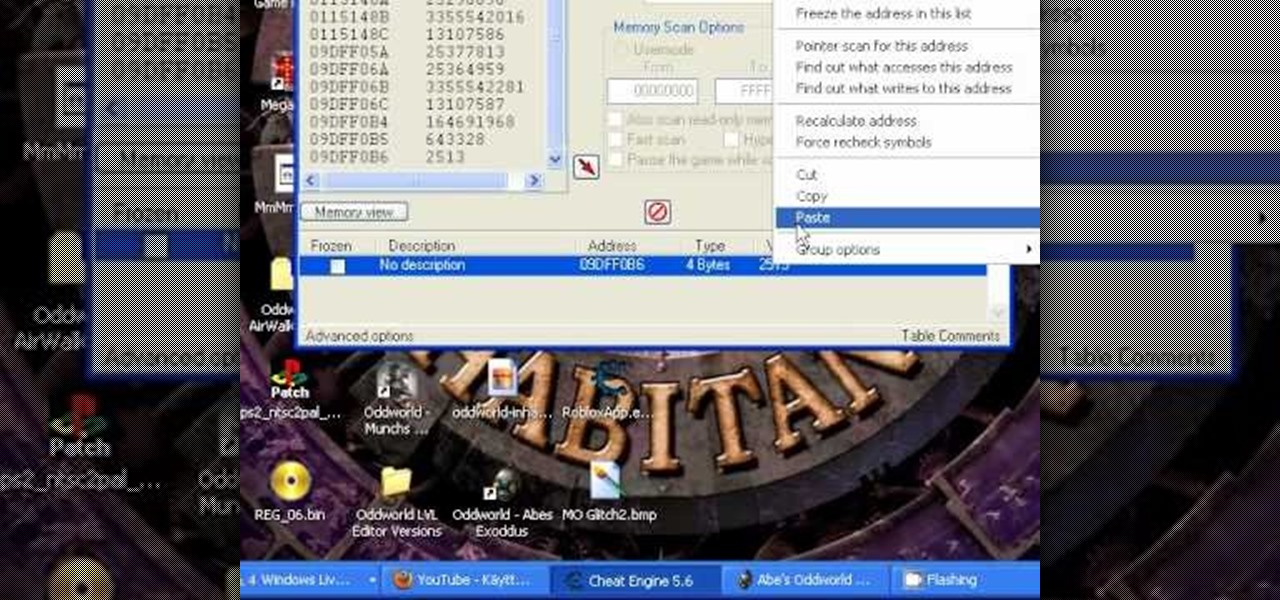
If your health is high enough, the zombies will never be able to defeat you! This tutorial shows you how you can use Cheat Engine to reprogram your avatar's health score. It's easy, and you can do it as often as you need.

This is a quick and easy tutorial that shows you how to find out your character coordinates in a 2D game using the free game hack program Cheat Engine. It's not very difficult, just follow along with the steps in the video!

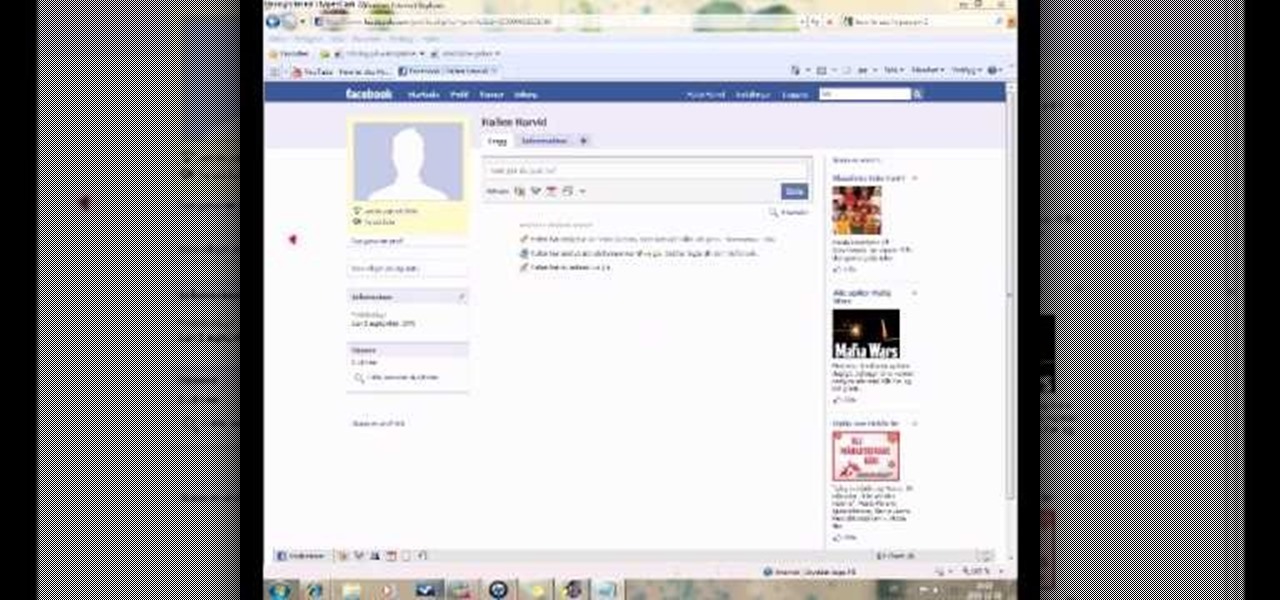
This is a fun little Facebook hack you can use to make floating circles appear on your profile page. Make sure that you don't do this in a text box - just click anywhere on the page and then enter the secret code!

Why should PC users have all the fun? This video shows you how you can download and install a copy of Cheat Engine onto your Mac computer. Now you too can hack all the online games like FarmVille and Pet Society!

Cheat Engine is a free program you can download that will allow you to hack into any web or Flash game and alter the code so you can cheat. While many tutorials show you how to do one or two things with Cheat Engine, this tutorial focuses on how to use it in general.

Be able to defeat any enemy with just one blow from your mighty ninja weapon! This video shows you a fun cheat you can use to hack Ninja Saga, and make your character powerful enough to kill any enemy with only one hit.

You'll need to be playing Ninja Saga in Mozilla Firefox, and have access to Cheat Engine 5.5. If you have both of these, then you can use the cheat method shown in this video to give your ninja lots of extra money!