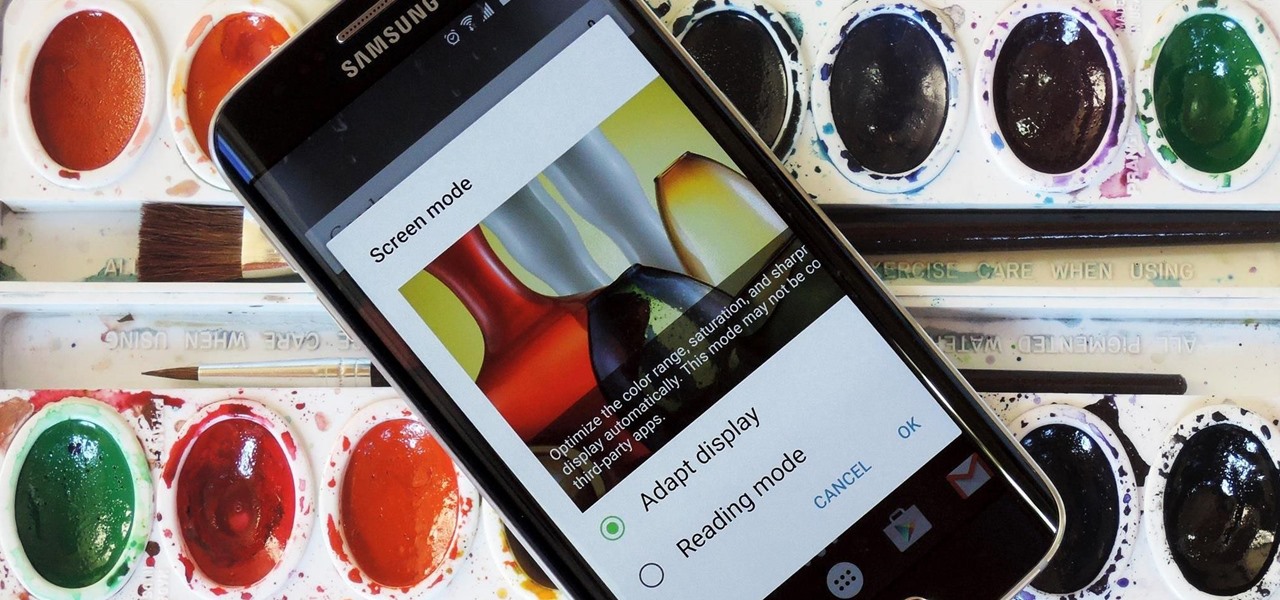
AMOLED display panels like the one found in most Samsung Galaxy devices, including the Galaxy S6 models, are known for their deep blacks and vivid colors. The downside here is that the colors tend to be over-saturated and not very realistic.
Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or right-click, but it usually requires special hardware to detect the amount of pressure you've applied.

Believe it or not, not every Apple lover is willing to make the commitment and fork over $350+ for the Apple Watch. Like many others, I'm not willing to put that much faith into Apple's first attempt at wearable tech.
The Galaxy S6 Edge comes with a very nice pair of earbuds, which might possibly be the best set I've ever owned. They're quite comfortable, and they provide clear and robust sound, but they could still use just a little boost in volume.

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

For every contact photo you add, Android keeps two copies. The first is stored at a 720p resolution, and this is used for high-definition imagery when you're looking at a full-sized contact card. But the second image is only 96 pixels by 96 pixels, and this is used for all thumbnails throughout the operating system.

It's hard to not to like the look of iOS emojis. Sure, Samsung and other Android phones have emojis, but they're all kind of goofy-looking. And since iPhone emojis continue to be viewed as the standard, it comes as no surprise that you can actually get them on Android—and without root!

As it stands, Android's notification system is one of its biggest strengths—but that doesn't mean it couldn't use a few tweaks here and there. For one thing, when you receive multiple notifications from the same app, there is no indication as to exactly how many notifications you've received.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

Your Apple Watch only looks as good as the band that it's bound to, but if you're looking to purchase one directly from Apple, expect to spend anywhere from $149 (for the Milanese Loop) to $449 (for the Link Bracelet).

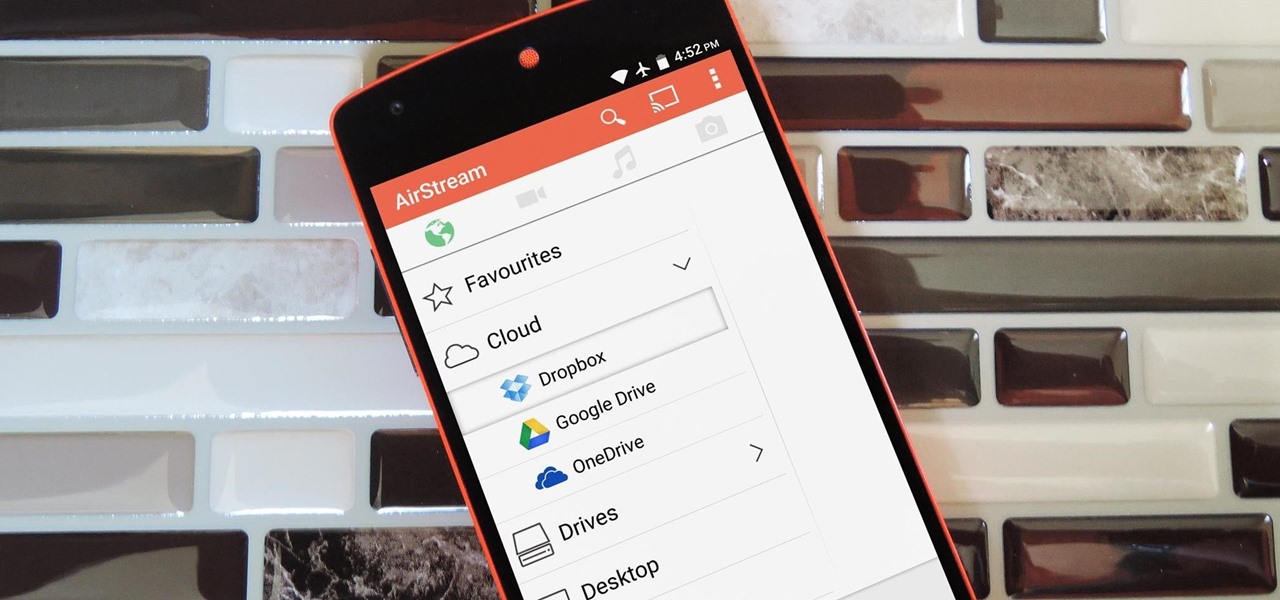
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

It probably doesn't happen much, but occasionally you'll run into a frozen or bugged-out app on your iPhone or other iOS device. That's where force-closing comes in, allowing you to close any app manually through a few clicks and swipes.

There's a built-in timer feature on the iPhone's Camera app that helps you set up your device, step back, and take a photo before time runs out. This feature is useful when there isn't another person around to take a photo of you, or when you don't want to be missing from a memorable group picture. Unfortunately, timers don't always work well. With a timer, no one can sit behind your iPhone to see if the picture is perfectly focused and framed, but that's where your Apple Watch comes in.

The buttons on most Android devices are laid out (from left to right) in a Back, Home, Recent Apps format. Samsung is the lone exception to this rule, which flip-flops them, so this can make for an inconsistent experience if you own multiple Android devices.

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head to your home screen, switch over to your phone app, paste it into your dialer, and finally make the call.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

I always over-order when I call in for pizza delivery, because I love having leftover pizza. Because there's so much flavor packed into the sauce, cheese, and whatever toppings you've ordered, pizza adds flavor to salads, cocktails, and can even act as the base to a quiche. Press it into a waffle iron to make a pizza panini, cut it into triangles and make the best Bloody Mary ever, or use it as the base for a lively quiche.

Whether you live in foggy California or icy Massachusetts, you've more than likely struggled with a cloudy, vision-impairing window that makes even the shortest commute impossible.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

There are a few ways to successfully cheat on a test without getting caught, Here's one of them! Like most, office and school supplies will be needed. For this one though all you pretty much need is an eraser. By the time you're done with this hack, you'll be getting straight As for sure.

Are you stranded in a hotel room with no kitchen, but craving the comfort of a home-cooked meal? Fear not, I have found some interesting ways to cook food without the luxury of an oven, stove, microwave, or even a toaster!—also known as "hotel room cooking."

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Despite what some in the tech-world would like you to believe, iOS isn't totally locked down, free from user customization. Take your home screen, for example. Not only can you change your app icons and move them wherever you'd like, you can actually choose to hide them all. If you have a wallpaper that's just begging to be shown off, this trick is for you.

With a 13 megapixel camera that can record in full 4K, there's a lot to love about the Samsung Galaxy Note 3 from a photographer's perspective. The image quality in my photos and videos are top-notch and nothing to complain about, but as with all things tech, things could always get better.

Impress your friends with this simple yet great way to serve a watermelon. Perfect for parties. You'll never create triangle-shaped slices of watermelon ever again with this hack. You only need a watermelon (could also work with other melons), a sharp knife, a cutting board, and some friends!

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

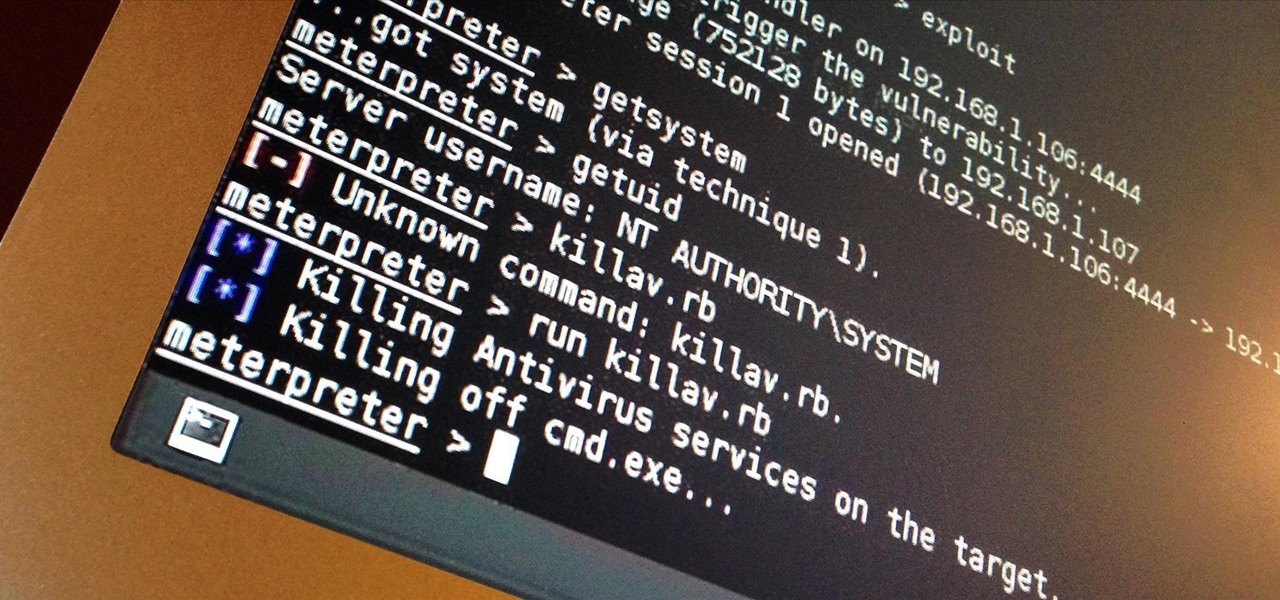
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.