Welcome, everyone! While Linux distributions are almost always used for exploits, security, pentesting and other stuff covered in Null Byte, knowing the Windows Command Line (or Command Prompt) is a useful skill that can help you in various ways, such as using exploit programs made for Windows or using the command line on someone else's Windows computer.

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

There are many advantages to knowing how to speak in foreign languages, whether it's for traveling, business, or simply for the pleasure of getting to know a culture that is completely different from your own.

1- We removed the screws holding the lid of the box, with the help of a screwdriver. 2- After we removed the part unscrew the machinism and we took it off. 3- To remove the mechanism, we leave the loose wires, knowing which is which. 4- When we have the new mechanism, we bring them back to the cables that we loose. 5- Finally, we bring them back to the cover with the screws and a screwdriver.
If you just gave up drinking soda and you don't know what to do with the six-pack of Coke gathering dust in your garage, then this article is perfect for you. The acidity, sugar content and carbonated nature of most soda drinks are perfect for a number of surprisingly practical uses for DIY home projects, garden work, kitchen cleanup, car maintenance, cooking and more.

Google is God of the internet. The clouds in the sky, the light at the end of the tunnel, the all knowing mysterious field of pure white. And soon they will have an optional home page that aesthetically expresses their God-like super spartan minimalism.

I have the honor of knowing a woman who lived in Taiwan for a couple years back in the day, as a missionary. One of the things she brought back from her time spent there was the Pei Mei Chinese Cookbook Vol. 1 published in 1969. You can grab a decent used copy on Amazon for about $15. I knew I wanted my own copy after my friend invited me over for a Chinese feast one afternoon, where we sampled no less than half a dozen dishes from the book.

As discussed earlier, there are many ways to view the upcoming solar eclipse, whether it be with actual eclipse glasses, welder's lenses, eclipse-approved filters, or a solar telescope. If you can't get your hands on any of those, the safest way to view the solar eclipse this Sunday, whether it be annular or partial, is with a projection method.

If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!

Here is my investigation on Teen Stress Base on FTA. QR/ER on Stress

It’s that time of year (in the U.S. anyway) when people are focused on getting organized -- or rather wishing they were organized. Being organized is great, it affords physical space, mental space and all but insures higher efficiency. But wishing and doing are two entirely different things. Wondering how to achieve the bliss of knowing where your stuff is? It’s easy... if you start small and don’t waste your valuable time watching TV shows or reading magazine articles on “how to” do it.

Last week I reviewed Kinotopic, the iPhone app that lets you easily create cinemagraphs. While I loved the result, I found the app hugely flawed. Kinotopic forced you to use a Facebook log-in, and didn't store the finished video on your phone itself. Instead, you had to visit the Kinotopic website to see your cinemagraphs or link to your Kinotopic page using Twitter, Facebook or Tumblr.

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

In 1969, the Apollo 11 crew were the first to walk on the Moon, the New York Jets defeated the Baltimore Colts in the third Super Bowl ever, Led Zeppelin released their first studio album, and one of the most pivotal moments in music history happened—Woodstock.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

This Null Byte is a doozey.

Listen up Scrabblers... you finally have something to brag about besides knowing what MUZJIK is, and if you think it's elevator music, put those tiles back in the bag and pack up your Scrabble board because this doesn't apply to you.

The indie game scene is constantly expanding, but in 2008, Minecraft, Braid and Angry Birds had not been released, along with all of the other indie games that established the financial viability of the format. Indie games were the all-but-exclusive purview of free Flash game sites and the proud users of TIGsource.com. The Independent Gaming Source is a massive forum for indie game developers to share their projects with like-minded individuals, while seeking help and approval of their games.

Although circles are Google+'s answer to the problem of social network relationship management, that's not the only thing it's good for. People on Google+ are using circles for all sorts of creative activities, some of which aren't obvious as first glance.

Back in the Super Nintendo days, playing one RPG after the other, memorizing maps and mazes became second nature if you didn't want to look at the mini map or get lost often. I would make it a point to memorize corners and the overall structure of the dungeon or location, so that graphically I would know where I am at all times. It's not like today, where major games come out with 200+ page guides detailing every last inch or going online where you can download a map or look at Youtubes for h...

Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to the surface.

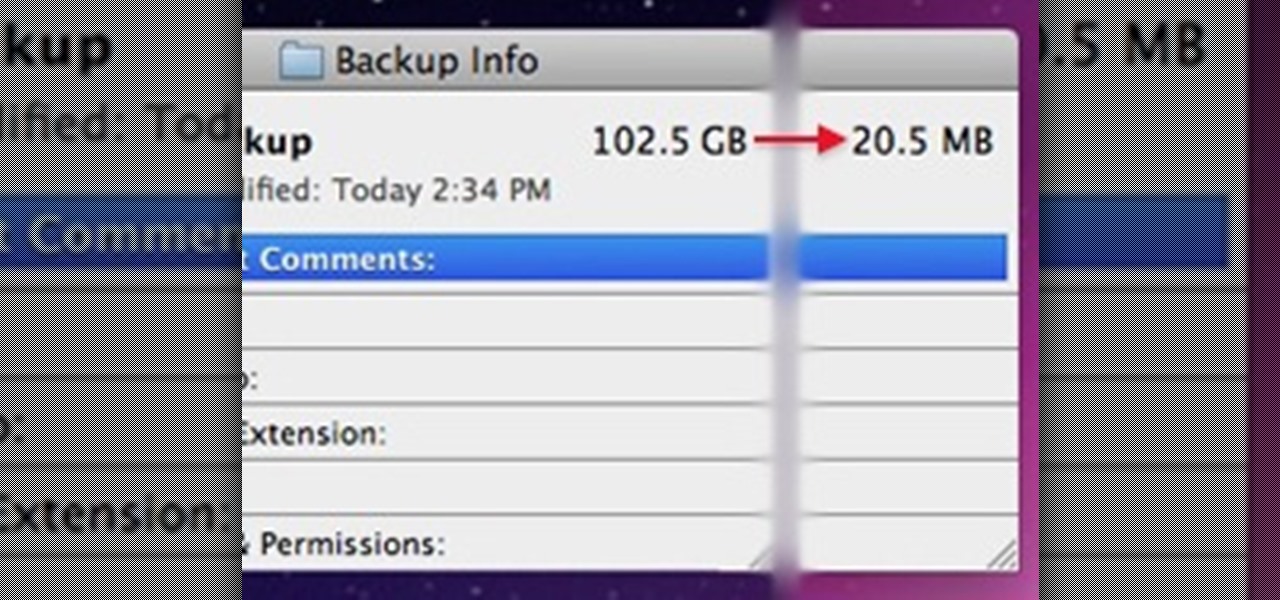
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

Note: Little Brother is available as a free ebook download. Warnings

Huzzah! My sentences have been recorded! This is normally the most exciting part of beginning a language with this method, because you actually had another person do something for you that is really of great value. I remember receiving my first recording in Japanese. I listened to that thing about 100 times. I shadowed it, repeated it to my family multiple times and still hear it in my head from time to time.

SCRABBLE may seem like a board game for word nerds only, but believe it or not, SCRABBLE can be used to lure thousands of hot women into your bed... at least that's what Clive Worth claims.

Here at WonderHowTo, we appreciate the fine art of photography (including its extensively vast bag of mind boggling tricks). We also enjoy playing with fire. Sorry, most of us are little boys at heart, and we can't get enough tutorials that fall within the playing-with-matches realm.

Chi gyo ichi nyo is a familiar expression in the dojo. The word chi means knowledge. Gyo means doing, or action. Ichi nyo means inseparable. Action and knowledge are one! Acting without adequate knowledge or understanding is a constant source of frustration and problems. In our lives we are often busy and active without really understanding the basis of our actions and their full impact. Some people practice karate without really knowing why they are training. In class they do the techniques ...
Microsoft SharePoint is a business management system introduced by MICROSOFT. It has many build in functions to work in web based environment easily. Microsoft SharePoint 2010 is released on April 17, 2010. It is introduced with the promise of better performance than its predecessor version for both developers and IT professionals. It is entitled as “Business Collaboration Platform for the Enterprise and The Web”.

If you've checked out my SCRABBLE World, you may have read "How Controversy Changed SCRABBLE". In that case, you know that the word JEW is not allowed in regular play, because it was deemed an offensive and obscene word.

If you've read my blog "How Controversy Changed SCRABBLE", then you know that the word JEW is not allowed in regular play, because it was deemed an offensive and obscene word.

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

For our final part of recognizing crowd control, we shall look at the mind. It's the most complicated thing in the universe, but also the most easily influenced. What makes us to gullible? What methods to commercials, companies and the media use to influence our position on things? These are just a few of the questions we will answer.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

Last week I had a quick look at V.I.K.T.O.R, the anthropomorphized automated editing app that lives on your iPhone, and today it’s time to put it to work.

Facebook's new Timeline feature has been rolling out gradually since its unveiling in September, but yesterday it finally became available to Facebookers everywhere. It's even available on your mobile device, too. Those who want to upgrade to the radical new profile design can do so by simple logging into their Facebook account and visiting the About Timeline page on Facebook.

This week seems to have gone by in a flash. Maybe it was the three day weekend, but I don't think it accounts for the flurry of activity I've been seeing on Google+. Updates, debates, and new initiatives are unfolding every day, and the best part is that most of them are coming from outside of Google. People love Google+ so much that they want to evangelize to others about it. What more could Google+ ask for?