While it is common knowledge that peanut butter can help ease chewed-up gum out of your hair, what happens if you don't have any peanut butter—or you have somehow gotten gum stuck on your shoes, clothes, or carpet?

There's been a lot of craziness from the far East lately on WonderHowTo... A Chinese farmer builds an army of robots, a Thai baker makes horror movie-esque bodies out of bread, a Chinese James Bond enthusiast hacks together his own submarine, and don't forget the Japanese cooking show narrated by a poodle named Francis...

Mom, watch your back. I kid you not. Stealth. Super-annoying without being dangerous. No trace. Sublime in that Ian Fleming kind of way.

Mom, watch your back. I kid you not. Stealth. Super annoying without being dangerous. No trace. Sublime in that Ian Fleming way.

Science-fiction writer Jules Verne predicted many scientific breakthroughs, including the moon landing, tasers, and nuclear submarines. In his 1874 book The Mysterious Island, Verne writes:

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.

A couple months ago, the world was supposed to end. It didn't. But that didn't stop the Centers for Disease Control and Prevention (CDC) from warning citizens of one global possibility besides complete destruction—ZOMBIES. They used the farcical flesh-eating living dead as an excuse to teach you about the necessity of real-life emergency planning.

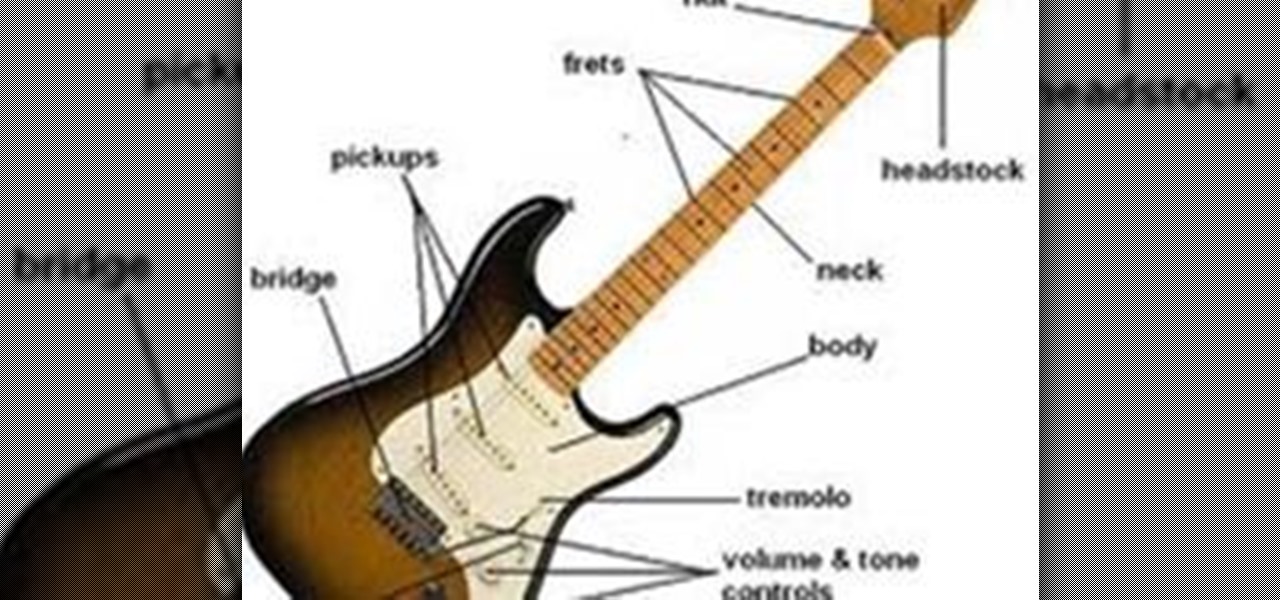
How to be a better guitarist

It was bound to happen. And just as anticipated, it took less than a day before someone successfully rooted the new Nexus S smartphone from Google and Samsung.

This is a Photoshop tutorial for digital photographers. Learn how to improve the midtone contrast of your images with this Photoshop tutorial. You can really improve the midtone contrast of your images just by following a few simple step. Watch this tutorial to find out how.

This is a Photoshop tutorial for digital photographers. Learn how to create HDR images in Photoshop. We'll be taking an extensive look at the process of creating HDR images. Take note that Photoshop doesn't do a good job of creating HDR's. We'll also explore other 3rd party options for better results. In Part Two, we'll be looking at a 3rd party application which simplifies the HDR process.

This beginner's guide is designed for people with little or no prior knowledge of computer languages, who want to learn to program by using the Visual Basic language. If you have some previous programming experience, maybe in another language or from a few years ago, then you may also find this guide useful. Whether or not you have programmed before, you should already be familiar with computers before reading this guide. It assumes that you can perform simple tasks like starting a program, a...

What's your training about? Would any of it matter if your life depended upon it? If not, what is your training providing you with?

To start developing your own 3D games and programs, you're going to need to know the basics of C++, like shaping.

Mike from the SubStream's "Film Lab" has some tips regarding video camera lenses. In part one, Mike talks about the basics of lenses, starting with focal length and angle of view. It's a lesson on the analog collections of lenses cinematographers use with their cameras. For people who like to point lenses at things, here is the functional knowledge.

Check out this science video tutorial on how to apply a C. elegans dopamine neuron degeneration assay for the validation of potential Parkinson's Disease genes.

If Null Byte had a large Batman-like spotlight calling for help, we would definitely be using it right now. However, we don't, so this is my digital equivalent. Information security is a huge field, far too much for one man to cover adequately, so I need your help!

Here at Null Byte, we try to inform and teach the community on ways to navigate the Internet in that special way, as well as staying safe along the trip. That being said, I need some help from all of you! There is a lot of information to cover and I know we have some smart users lurking around. We would love to hear from you.

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

At Kaplan University, our main focus in developing our online MBA programs is career development. We believe the time and effort that is required to obtain a master’s degree online should be apparent the first day the student begins their new career. Earning an MBA could be a step in the right direction towards a fulfilling and satisfying career.*

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

What Hand Do I Read - And Why ?This is the first tumbling block for some budding palmists, so let me give you some real begginning tips.

What's the geekiest way to propose to your girlfriend? Make a robot do it for you. As a self-declared dork, RangerX52 wanted to take a simple task like proposing and make it as utterly complicated as possibly—by having a DIY robot do it for him. With knowledge of his lady's infatuation with the childlike personality of GIR, one of the main characters from the animated Invader ZIM series, he went ahead and built a tiny robotic replica of GIR to do his bidding.

Welcome to Compute & Conquer! This article may seem a little basic. We all have an idea of what a computer is but the fundamentals are necessary. Without knowing how something works, how can we determine a problem and find a solution when something goes awry? Way too often, I find myself helping someone with a very "easy to fix" problem on their computer. A problem which could have either been avoided or fixed had they had the basic knowledge of how to use a computer. Even worse, I've seen to...

Your boss is pursing her lips and drumming her fingers on the table during your presentation. Your best friend is gazing downwards and crossing his arms when you ask him why the car you lent him for the weekend has a big dent. What could these body language signals all mean?

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about posting peaceful poetry.

Friday's mission was to accomplish solving HackThisSite, basic mission 7, which required us to learn some basic Unix commands. If you have any prior experience using Unix commands, this should be a breeze for you if you sit and think for a second.

Astronomy World will be posting a weekly blog post that informs fellow observers upcoming interesting events in the sky. These will include:

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

I was working on a different Google+ Insider's Guide post when suddenly, my Google+ stream started filling up with news of Steve Jobs' death. Since that moment, many people in the tech industry have paused to reflect on the legacy that Steve Jobs left behind, and talk about what his vision meant for the rest of the industry, and for them personally. There's no tech sector that was untouched by Steve Jobs' influence, and that includes Google.

Welcome to Canon 5D World. Alright, let's face it... there's not much in here right now, but hopefully one day this World will be the go-to destination for anyone with questions on their Canon 5D or 5D Mark II. Maybe the Canon 5D Mark III, if it ever comes to that.