
News: Why Newbies Deserve Respect
Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.


Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

YouTube and the National Football League have announced a partnership that should greatly improve the online experience for gridiron fans. In a posting on their official blog, YouTube outlines a deal that will bring NFL video clips to their immensely popular site while bumping official NFL pages up to the top of relevant Google search results.
So, you wan't to become a Xbox Community Ambassador? Wan't to give support to other Xbox Customers and Earn loot doing it? Want to be different from a "normal" Xbox Customer? Want to share your knowledge to others who want it? Come on over here, friend! In this How-To, I will tell you how to become a Xbox Community Ambassador in the most correct way possible! In 3 Easy Steps! Here is the Link to the Website : http://ambassadors.xbox.com/

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

Just in case you weren't aware, Google has more money than you and I will probably ever see in our lifetime, and now it seems that the search giant will be spending that money sending satellites into space.
Learn how to setup up a basic structure for a HTML web design document, define the HTML version, open and close HTML tags and learn how to apply the proper file extensions when saving document in notepad. This web design tutorial is by no means a complete structure for HTML coding and is only a brief introduction to HTML web design. This video will only go over a brief introduction to the structure of an HTML document and in a future tutorial we will go over additional components that are nee...

Keyboard shortcuts are super useful for multitasking and saving time on the computer. But if you're like me, you might only know a few of the million of keyboard shortcuts that are out there. I pretty much know the most basic of basic shortcuts: copy, cut, paste, save, select all, and screenshot.

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

As we approach the holiday (i.e. gift-giving) season, don't forget to make sure to include the usual notes in your gifts indicating that they can be returned. Otherwise, you'll just cause the recipients to save your gifts until they can be properly regifted onto some other ungrateful chump.

Did you know that the average cost to make a penny is about 2.4 cents?!? That's why the Obama administration asked Congress earlier this year for permission to change the metals in the penny, hoping to get the cost back down where it makes sense.

Looking for a way to make your bike stand out? You could light it up with LED rim lights or turn signals. Or if you're looking for something a little less flashy, you could make your own set of custom wooden handlebars like these by furniture designer David Moore. To actually make these wooden handlebars, you will need some woodworking tools, not to mention some actual woodworking skill, or at least the tools and some knowledge on bending and forming wood. In his video below, David shows exac...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

Apple just seeded developers and public beta testers the GM (golden master) for iOS 14 on Tuesday, Sept 15. The update (18A373) comes just after Apple's "Time Flies" event, and six days after Apple released iOS 14 beta 8 for both developers and public testers.

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.
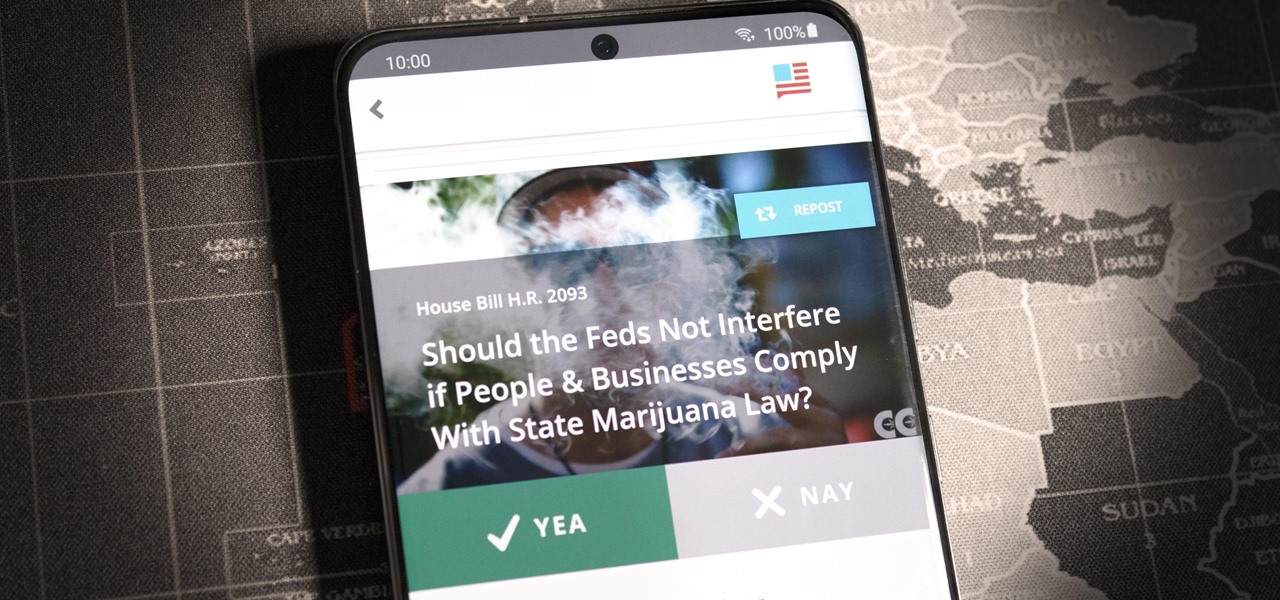
If you live in the US, it's your civic duty to understand our governing bodies and the political system that puts them in place. It doesn't matter what your age is, knowing who to vote for is as important as voting at all. That starts with policing your own representatives to help decide whether or not we should re-elect them.

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

To stand out on Instagram, you need more than just the great camera on the Galaxy S20. You have to think like a professional photographer, which means two things: using manual mode and editing your photos. It is only with the latter that what you imagine becomes a reality.

You've spent untold hours playing your favorite games. You know what you love. More importantly, you know what can be improved upon. The distance between vision and reality is not as far as you think. You just need a bit of training.
As we settle into our new normal, this extra time provides a perfect opportunity to learn new skills. Speaking a foreign language is a great way to expand your cultural boundaries while also training your brain. Not only will you pass the time more effectively, but you'll also be doing something positive for your health.
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

With the iOS 13 beta right around the corner, Apple is churning out the betas for iOS 12.4 with developer beta 3 out today, May 28. It's the third beta in just 14 days and just eight days after developer beta 2 and public beta 2. The third beta may only house improvements overall, as iOS 12.4 is pretty bare bones as is, despite some hints at Apple Card support.

While North has yet to add third-party app support to its Focals smartglasses, the company has been diligent as of late in its efforts to add more functionality to the bare-bones AR device.

While the tech industries giants and eager startups chase the dream of widespread consumer augmented reality, enterprise AR is living the dream today.

So, you accidentally sent a voice message to someone in an Instagram DM. Maybe it contains an unflattering conversation about the recipient. Maybe it's a record of something embarrassing you said. Whatever your message contains, it's out there, on someone else's smartphone. You might think you're out of luck, and that your life is over. If you act quick, however, it won't be.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.