One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.
The famous Flappy Bird (technically Flappy Droid) game is still around in Android 9.0 Pie. First introduced in 5.0 Lollipop, the game was originally the version number easter egg for the new Android update. But after Android Marshmallow, Google began to hide it from its usual location, and Pie continues this tradition.

Another entrant into the do-it-yourself AR content creation market has emerged, as Zappar has updated its ZapWorks Studio software to include features for development newbies.

When you've had enough of someone's annoying baby videos or cat photos on Instagram, you would have to either unfollow them or even block them outright. Now, you don't have to cut ties with them completely — you can just mute them instead, a feature that Instagram's parent company, Facebook, has allowed on its platform for some time.

Despite the fact that Snap Inc.'s Spectacles weren't the hit some were expecting, the company is nevertheless taking another swing at it by releasing an updated version.

While some in the augmented reality space are tweeting about future amazing immersive experiences and others are showing off cool experiments, Microsoft continues to move forward with tangible business solutions right now that show how the HoloLens can improve business.

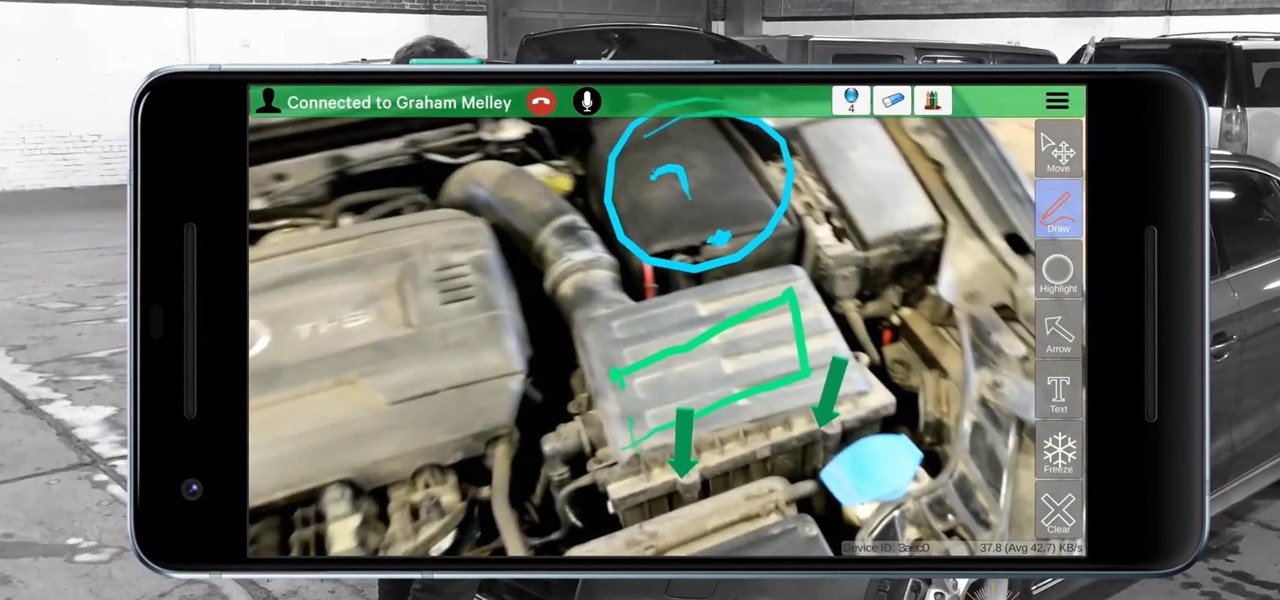
Scope AR has decided to take its live remote assistance enterprise application, Remote AR, further into the mobile augmented reality realm by harnessing the powers of Google's recently released ARCore.

Mobile augmented reality developer Blippar's mission is to construct a computer vision map the world, with visual recognition of thousands of notable buildings, bridges, castles, holy places. A major step toward that goal has been taken by the company this month with the announcement of its landmark recognition API.

While the consensus among some in the augmented reality community is that the Microsoft HoloLens is the best device available at present, it also remains the most cost-prohibitive option, with the development edition costing $3,000.

French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.

When playing word association with Star Trek, the first thing to come to mind with regards to augmented reality is likely Holodeck, not The Game, an obscure episode from season five of Star Trek: The Next Generation.

The iPhone X is almost within reach. In fact, you can preorder right now. We know you've been itching to get your hands on Apple's newest iPhone, but before you give up over $1,000 of your hard-earned money, make sure your iPhone X knowledge is up-to-snuff.

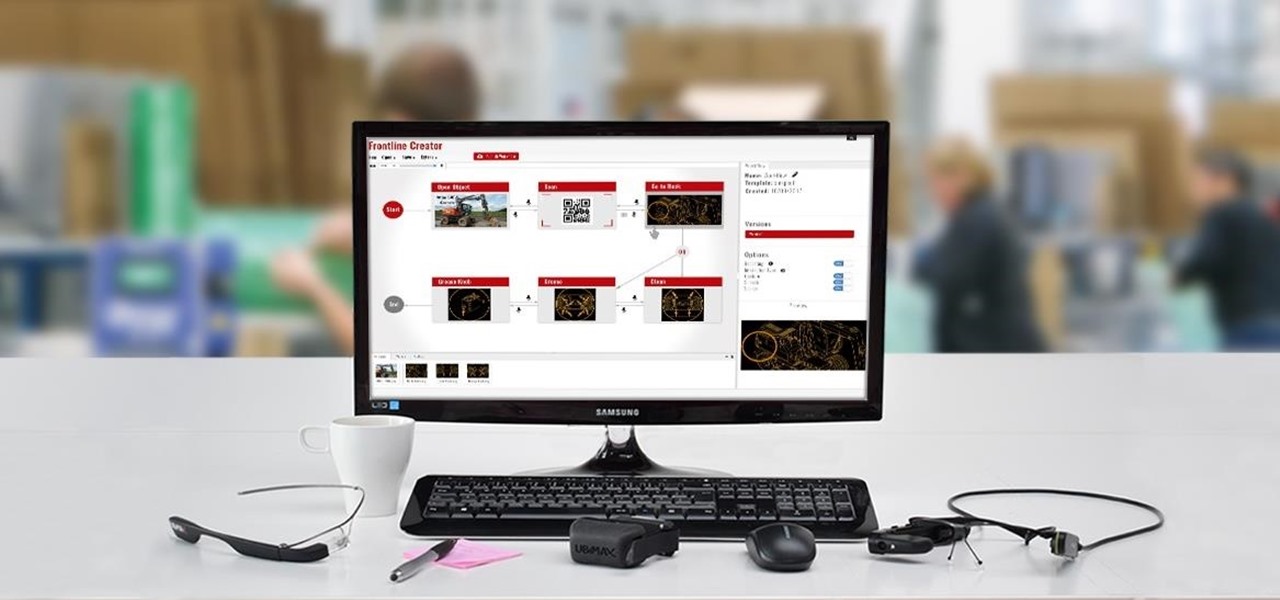
Augmented reality software provider Ubimax unveiled their graphical authoring and publishing tool for their Frontline enterprise platform to attendees at Augmented World Expo Europe today.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

In off-record discussions with AR experts, the consensus on ARKit is that it takes a software approach to the depth-sensors available on Tango devices. As a result, the toolkit has shortcomings, such as detecting walls and vertical surfaces.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

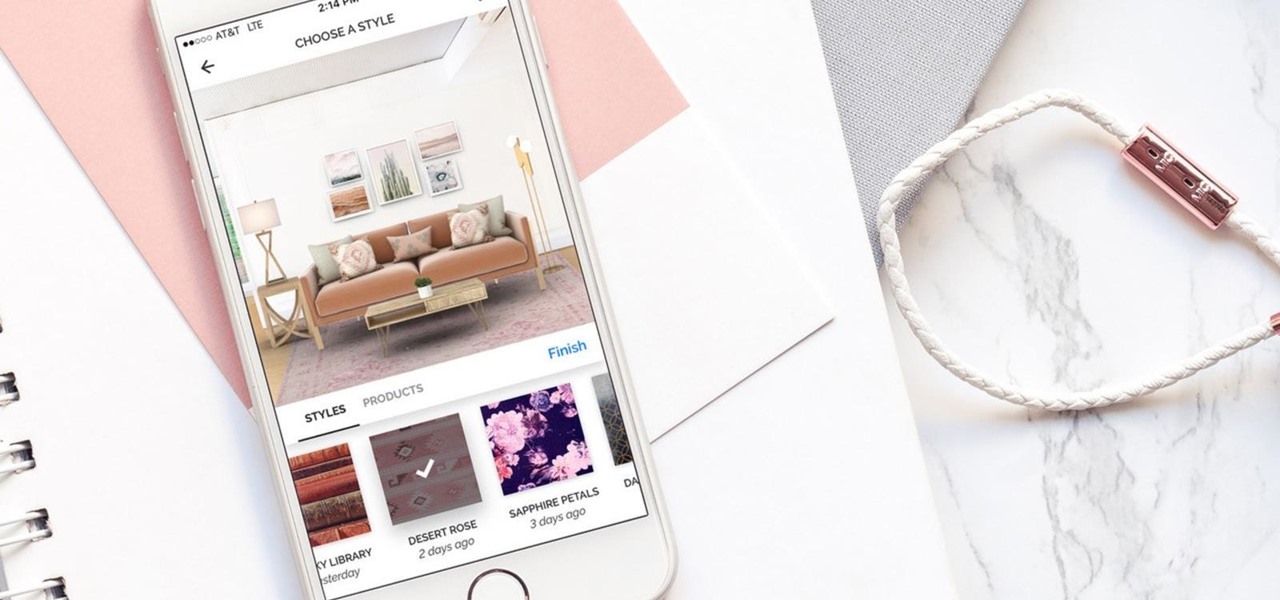
Hutch Interiors, Inc., makers of an eponymous augmented reality home design app for iOS and Android, has closed a series A round of funding, led by online real estate company Zillow Group, totaling $10 million.

German groups ZF Friedrichshafen AG and HELLA are collaborating to add to their autonomous portfolios with camera and radar development.

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

Customer service just got a lot more interesting. Construction equipment manufacturer Caterpillar just announced official availability of what they're calling the CAT LIVESHARE solution to customer support, which builds augmented reality capabilities into the platform.

Today, at Abundance 360, an exclusive event for tech entrepreneurs in Beverly Hills, California, Boston Dynamics unveiled a video of "Handle," a humanoid-like robot with wheels instead of feet.

For those of us that were blown away by the spatial mapping and user experience in Fragments and Young Conker, the version of spatial mapping that came stock in the HoloToolkit was lackluster at best. It became apparent really quick that to get an amazing presentation would require some heavy shader knowledge and some badass mesh culling skills, at the very least.

It's no surprise that the Microsoft Kinect can provide far better motion tracking than the HoloLens currently can on its own, but at least one developer didn't want to wait for the company's own eventual implementation. Kyle G, founder and CEO of Wavelength Studios, projected his movements using a Kinect into a holographic zombie.

Onion scrubs, salt and olive oil blends, a baking soda slurry... despite the many methods already out there to clean your (old or brand-new) cast iron cookware, there's one you may not have considered: using a potato.

At their annual I/O event, Google introduced their latest app to the public: Allo. The messaging app is the company's latest and most powerful entry into the expanding world of similar apps, with one twist—the inclusion of artificial intelligence.

Verizon customers who use the Samsung Galaxy S7, beware: a recent update installs new bloatware over your existing bloatware that installs new bloatware. Confused or pissed off? You should be, as this app can install new apps onto your phone without you knowing.

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.