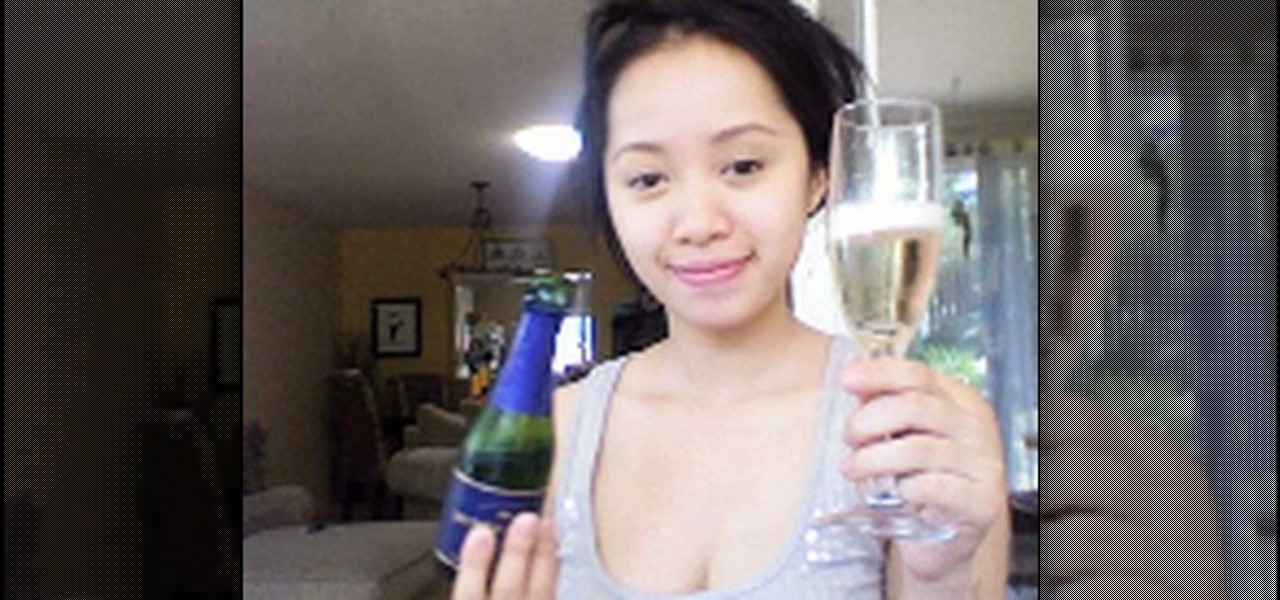So, you've got your new iPhone 5 from Apple, but wait—where do you get a case for it? Since its launch, Apple Stores across the country have been carrying absolutely zero iPhone 5 cases. In fact, the only thing they seem to be carrying right now as far as iPhone 5 accessories goes is the new Lightning cable. So, when will they be getting cases? Rumors state October sometime, but there's no telling if it's now or at the end of the month.

Motorola launched a new webpage on Friday that tells Android users how to unlock the bootloaders on a limited number of new Motorola smartphones and tablets. This new 'Unlock My Device' page helps demystify the process and make it easier for users to customize their phones.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Back in 2008, media artist Kyle McDonald created a 3D interface that could track movement, which he turned into a virtual Tic-tac-toe game.

Yep Kitty Litter, but DON'T FREAK OUT! Read or watch the video before you make any assumptions. This mask is perfect for oily, dirty, large pores skin! If you need to detoxify your skin, this is the best mask to use, and you can make it right at home! Use this once every 2 weeks. You should deep cleanse your face once every 2 weeks to remove impurities. Unscented Kitty Litter is made out of Clay, Bentonite clay to be excat. Bentonite is clay that is is rich in minerals and it comes from volca...

This video tutorial shows you how to use a free program to customize the HTC Home plug-in for Windows Mobile touchscreen devices. You can use any Windows Mobile cell phone or other device for this hack. YOu can run applications like Streaming Media on your HTC Home site from your smartphone. Just watch and learn.

See the low cost fluorescent lights Bill Myers uses when shooting video, and how to quickly set your camcorder to get perfect color under these lights.

Join parallel sticks with shear lashing. Potentially--if you did this to enough sticks--you could build a house this way. It might take one hundred years but, let's face it, you probably have time if you are on this site.

Got some home-recorded video on DVD you want to put on your Web site? Tom Merritt from CNET shows you how.

This tutorial shows you how to use iPhoto '08 to create a book (or photo album) of your photos. The cool part is when you're done making it, you can upload it to the Apple site to buy your book and have it printed and shipped to your door.

Kongregate is a site that allows users to upload games. Users must go to the site to download the hack. On the site, select Kongregate. Then select the first topic and click on KBH 2.0.14. Once downloaded, you can extract the files onto your desktop. Open up the file and follow the video on how to use it. It also comes with the auto rater. This video will benefit those viewers who play games on the Kongrgate website and would like to earn badges.

How far would you go to save your life? For James Franco, who plays real-life hiker Aron Ralston in Danny Boyle's "127 Hours", staying alive means cutting off your own arm with a dull pocketknife. If you've seen the movie (or even heard about all the people who fainted and threw up after watching it), you know that it presents one of the most grueling self-amputation and bone breaking scenes in movie history.

These videos will take you through the fifth episode in Alan Wake on the Xbox 360. You're almost to the point of discovering where Alan's missing wife is. Is she in Bright Falls or is she dead? Before you can find out, you have to defeat Episode 5 - The Clicker. Watch the gameplay on Nightmare Difficulty.

Michelle Phan presents this tutorial video on caring for your skin with champagne. You can use less than a sip of your champagne as a detoxifying cleanser/ toner.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to fix, enhance, and retouch photos in Photoshop.

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In recent weeks, Google managed to capitalize on the hype surrounding the Star Wars streaming series The Mandalorian with an AR app that was not only exclusive to Android but also available only for 5G-equipped devices.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

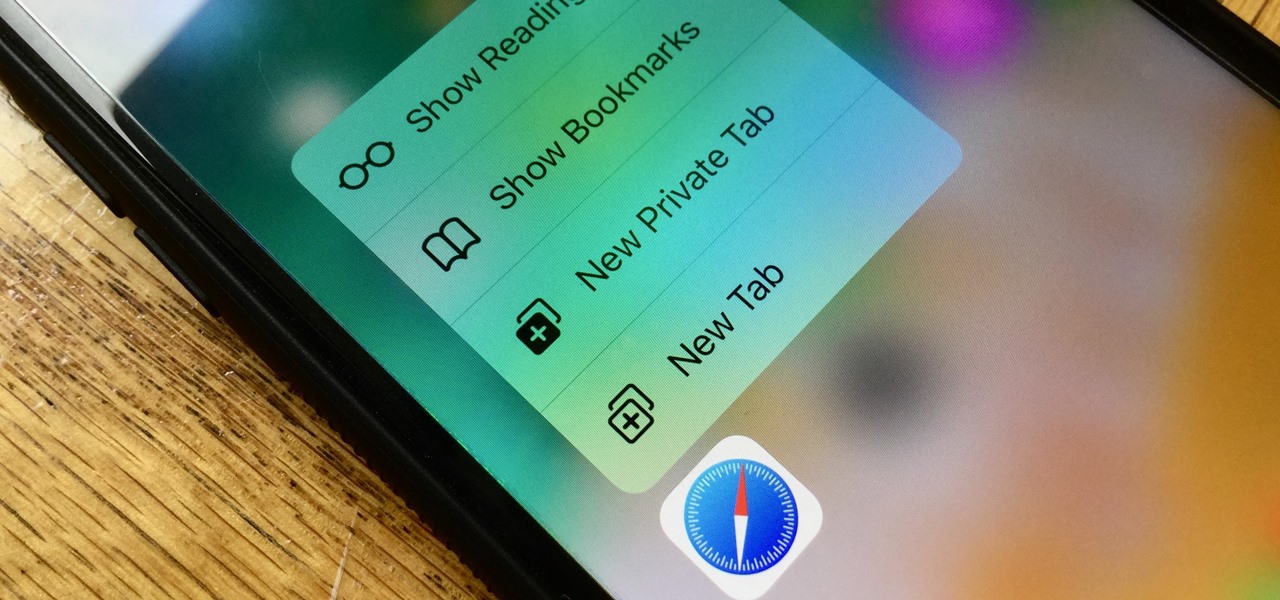
Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

The big day is nearly here... Super Bowl 50 kicks off this Sunday, February 7, at 3:30 p.m. PST (6:30 p.m. EST). And whether you're having a giant party or watching the game on your big-screen TV by yourself, there's one thing you probably won't be doing: cooking food in your kitchen.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.
Welcome back Hackers\Newbies!

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.