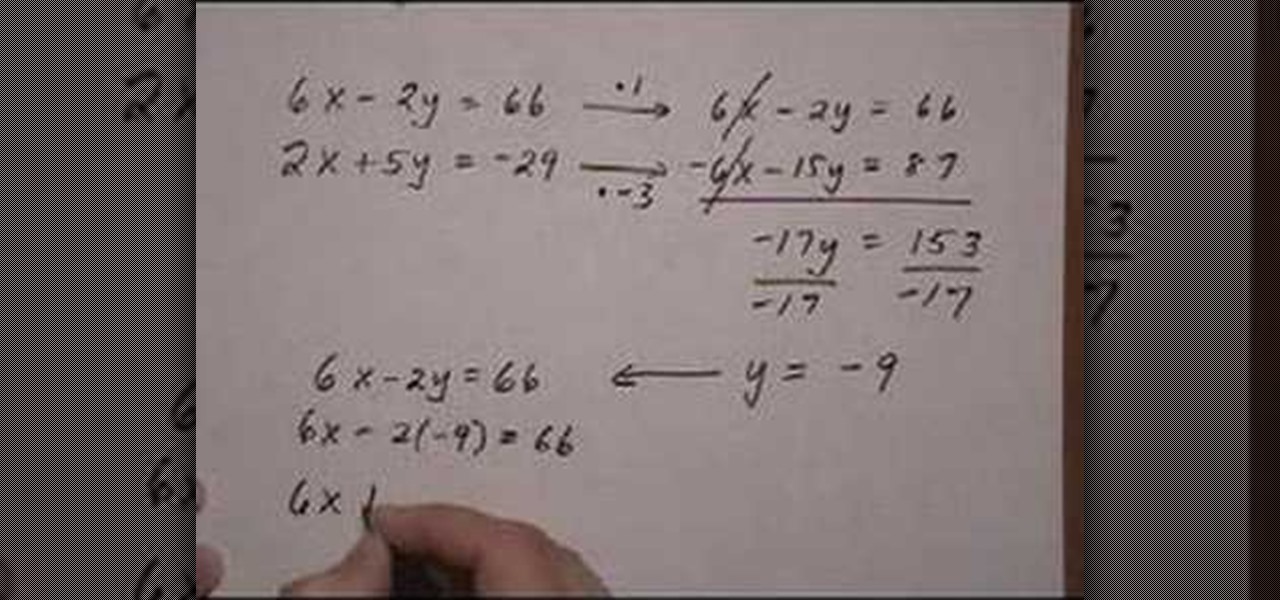Who better to demonstrate bar tricks than a cute girl bartender? Sexy Francesca teaches a trick to help pick up a chick in a bar. Brush up on your bar tricks so you can impress the ladies (or con your fellow barflies out of a dollar or two). Break presents bar tricks by Francesca. Pick up a chick with this trick.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Dirty Jersey has a house full of guests & they demand good alcoholic drinks! In this video beverage-making tutorial, learn how to mix up a pineapple daiquiri cocktail for the ladies in the house. All it takes is rum, sweet and sour mix, and pineapple.

Now, rolled-up bangs may not be a good choice for going clubbing (at least not if you're trying to catch a cutie's eye in a positive way) or for work, but work great for Halloween if you're dressing up as a movie star or teeny bopper.

Goldiestarling presents you this video where she does a make-up inspired by late Bette Davis was a Hollywood actress. She says that Bette Davis is her all time favorite actress and she loved her from her high school days. She says the Bette was a very strong lady even in her real life and if you Google on her or watch her movies, you too will like her. This make-up she has done she says is based on Bette's character in the movie called 'Of Human Bondage' in which she plays a waitress and late...

This video is about using the elimination method to solve a linear system. The lady presenting this video says that elimination method means that one of the two variables has to be eliminated while adding up the two linear equations. She then explains the example equations 6x-2y=66 and 5y=-29-2x. She asks you to first line up x and y. So the second equation is rewritten as 2x+5y=-29. Then she says that, to eliminate a variable, we should have their variables equal in value but of opposite sig...

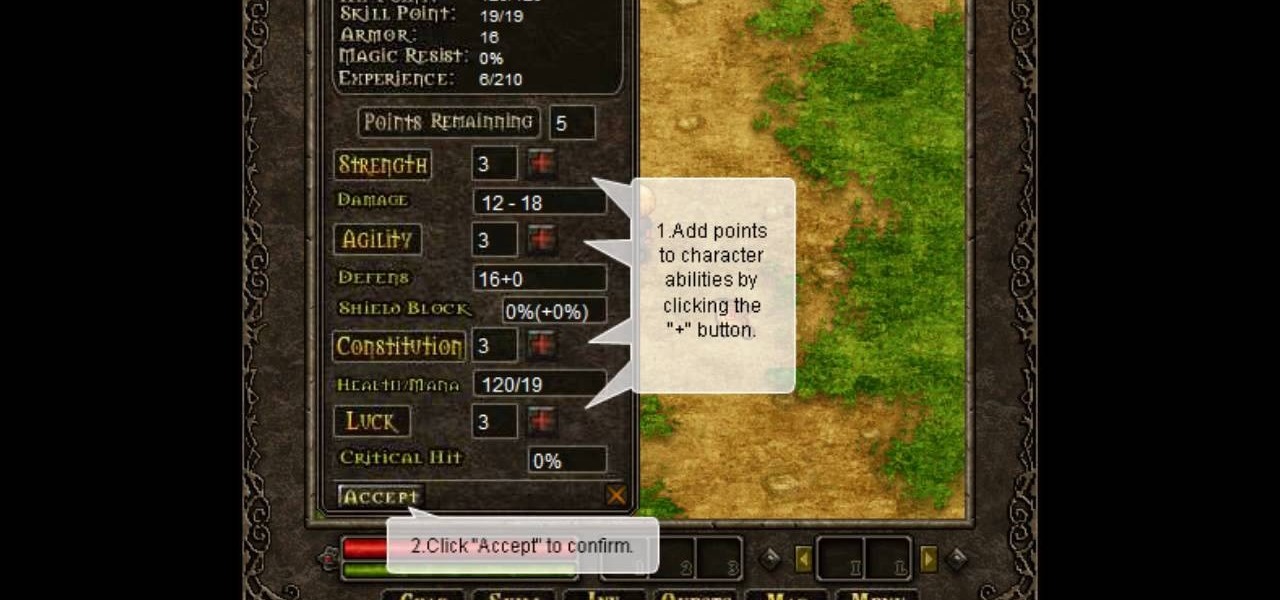
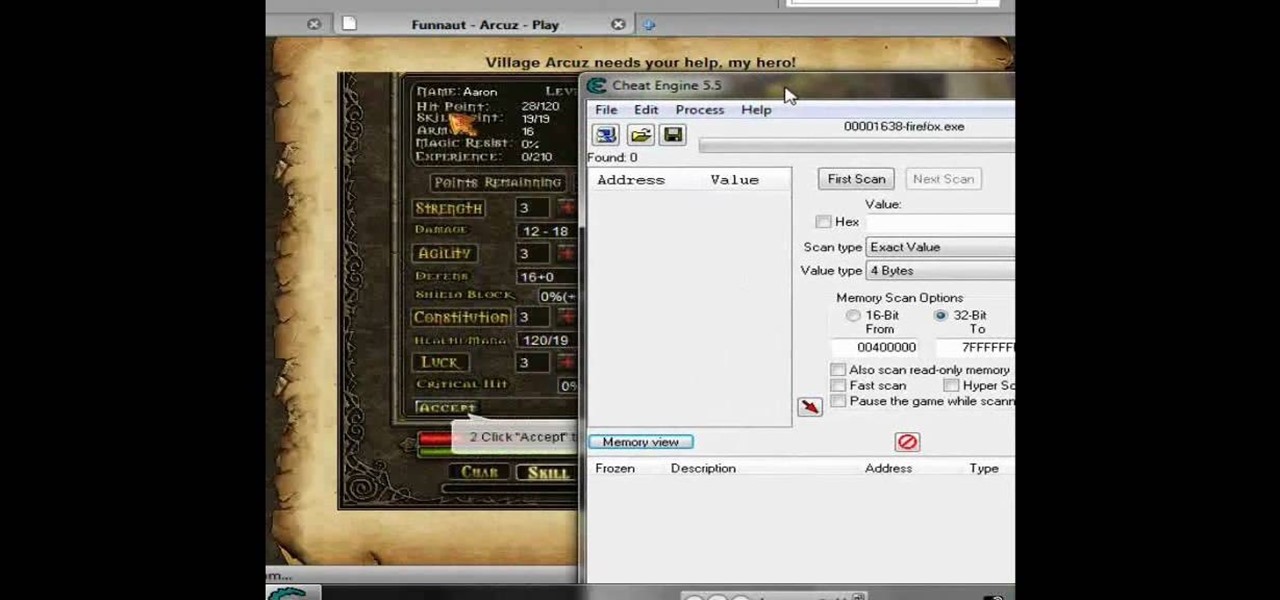
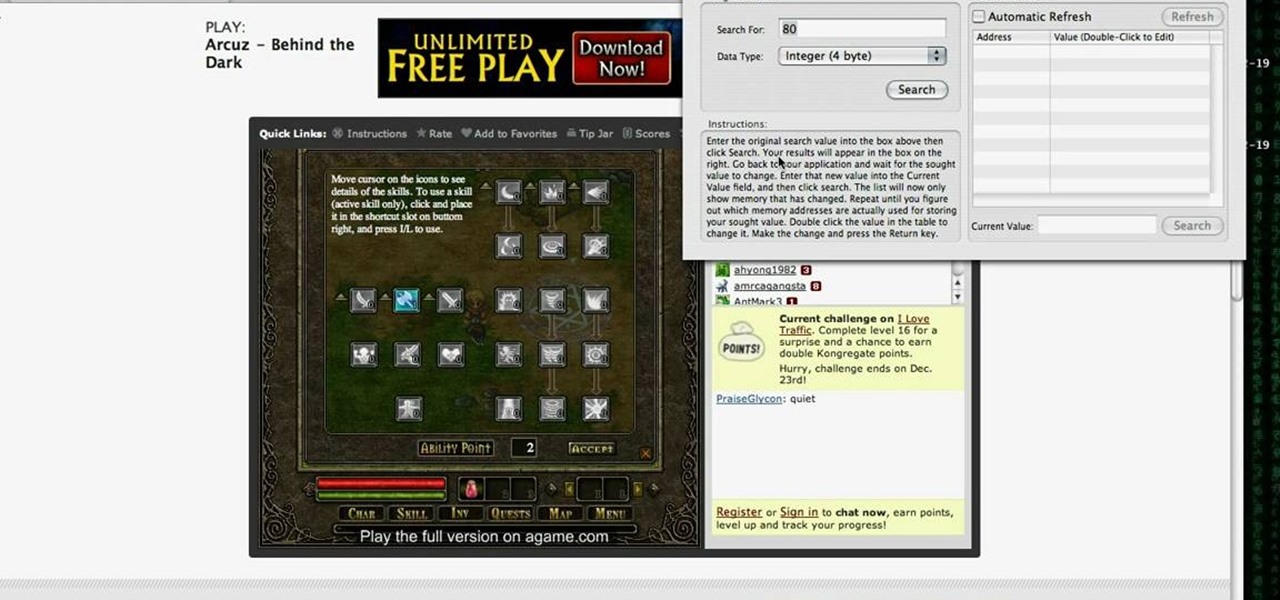
Want more gold? How about more skill points? You may need them in the game Acruz. But how do you get more, more, more? Well, with Cheat Engine, you can get more gold and skill points, with no real hassle.

ThreadBanger's Corinne visits with Luca of Lolibomb to learn how to make winter-inspired vegan beauty products in a DIY fashion. Way to save some money on gifts! In just fifteen minutes and a few easy steps, make an animal-friendly body butter for your best buds with these ingredients: cocoa butter, hazelnut oil, emulsifying wax, stearic acid, liquid glycerin, distilled water, and a vitamin E preservative of your choice. Add the body butter to a decorative jar and you have a great gift that m...

Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop the App Store on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Learn how to play "Single" by New Kids On The Block Ft. NeYo, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

The V-Cube 6 puzzle is a uniquely designed and constructed skill game. V-Cube 6 is a multi-colored, multiple-layered cube, rotating smoothly on based axes. The player is required to discover a strategy to achieve uniform color sides on her or his V-Cube, but in this process, the Rubik's Cube-like puzzle may break, especially if you're in the process of speedsolving.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

I used to brag that I could make a swan out of an apple, but chicks don't dig swans—they dig roses. So now I'm going to brag about making apple roses, because you would, too, if you could get them to look like this: Now that's an apple tart that will win the ladies over. (And definitely 100% tastier than the usual bouquet of roses, and 100% less greasy than a bouquet of bacon.)

Your closet is an area that holds important things such as keys, glasses, clothes and shoes. However, for some reason, it's always messy. Why is this? I know my closet is messy because I don’t have a lot of time to sit down and organize every little thing in there. I have never really even given much thought into organizing it.

If you discover that your Guitar Hero guitar is having some difficulties, check out this video for instructions on how to rectify the problem! This is especially useful if you discover that your keys stop working, or something of the like.

In this video tutorial series, DJ James Zabiela shows how to use effects to enhance your DJ set, utilize a feedback loop, and discover new music. In the second half of the series he shows how to alter live vocals, incorporate a few of his signature moves, and edit digital scratches into your DJ set.

Play Acruz online and hack it, too! With this handy hack, you can cheat your stat points, levels, and money. You just need Cheat Engine.

If you want more money, character points, and skill points on Arcuz online, then this video should solve your dilemma. Just use Cheat Engine.

Looking to give a personalized gift for a birthday or for the holidays? How about a personalized bar of soap, specific to your friend or family's style? In this episode of ThreadBangers's Decor It Yourself, Meg visits Bobbie Thomas, an editor for the "Today Show" and learns how to make your own soap, and how to customize it to be just about any color, shape, or size!

Ever desired your very own masquerade mask? ThreadBanger takes us through the fun, multiple steps to acquire your very own custom-fit plaster mask! Materials needed include plaster wrap cloth, water, scissors, petroleum jelly, spray paint (in your color choice), sand paper, paint sealer spray, and decorative additions to personalize your mask! This project will need to dry overnight, so be sure to leave enough time before your party or event.

Ready to get into custom hat-making? Be your own milliner, with the tips from this video fashion lesson. In this video episode, Rob and Corinne hook up with Hat make Victor Osborne for a super DIY lesson on how to make Hat Molds on the cheap.

The Newport Harbor Lawn Bowling Club would like to help you learn how to lawn bowl. Just watch this great video introduction to the much under-appreciated game of lawn bowling.

Music producer Mark Ronson, fresh off his Oscar win for Best Original Song as a co-writer of "Shallow," the song by Lady Gaga and Bradley Cooper for the movie A Star Is Born, has now added augmented reality to his varied repertoire.

Ever since Facebook announced Spark AR at the 2017 F8 Developer's Conference, the social media giant has been looking for ways to implement its mobile augmented reality camera platform in the lives of everyday users.

Many native New Yorkers, like myself, get a chance to visit the famed Statue of Liberty during school trips when they're a child in grade school. And if you're not lucky enough to be born in the city, you have to make a special trip to the monument as a tourist.

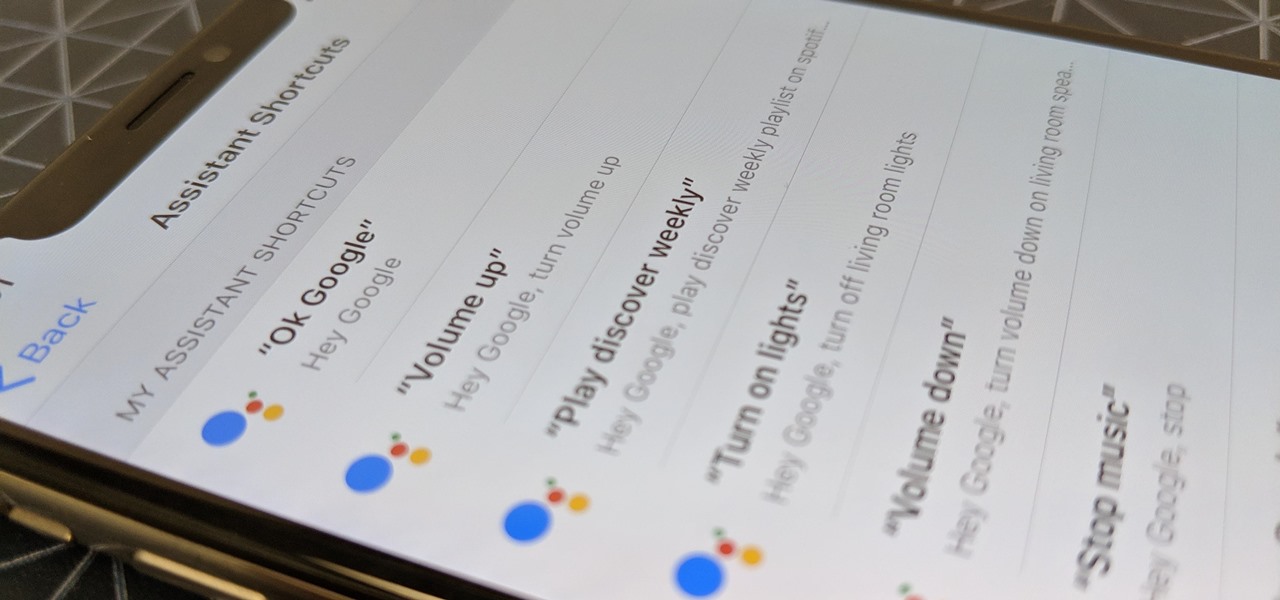
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.

Well-regarded men from the history of the United States tend to grace the country's currency, but what if equally deserving women were honored in the same fashion?

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.