
How To: Spot a player
Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.


Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Uploading certain pictures to Instagram can be problematic, especially when the dimensions of your picture exceed the dimensions of the square crop that's forced upon you. Why should I be forced to hack up my awesome fisheye picture inside of a lame square? I get the whole square thing, and I love it, but there's just some times when you can't be bound by the rules.
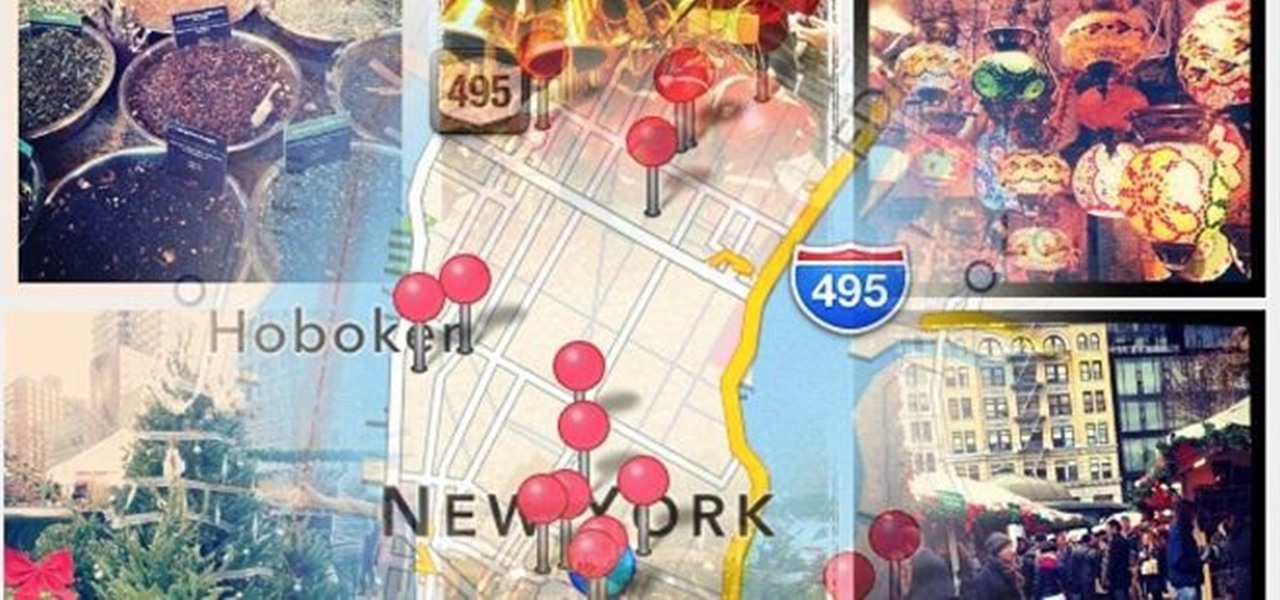
The only thing worse than not having any plans is not even knowing where to begin making them. Sure, you can check Yelp or one of countless other review sites to find a great spot, but there's no way of knowing what the vibe is like before you get there. Is it crowded? Are people having fun, or does it look pretty lame?

Being lost sucks. There really is nothing worse than going to a huge event with a bunch of friends or family and then getting separated. Instead of partying with the bros, you get stuck next to this lame couple who keeps seriously making out every ten seconds. SMH.

There's nothing worst than throwing a party without any music. That's like having watching the Super Bowl without any chips or beers...lame.

Small containers are useful for many things. They're good for storing snacks if you have children, as well as holding coins or odds and ends. But those regular store-bought containers are lame—who wants to keep their stuff in a Tupperware dish or old butter container?

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!
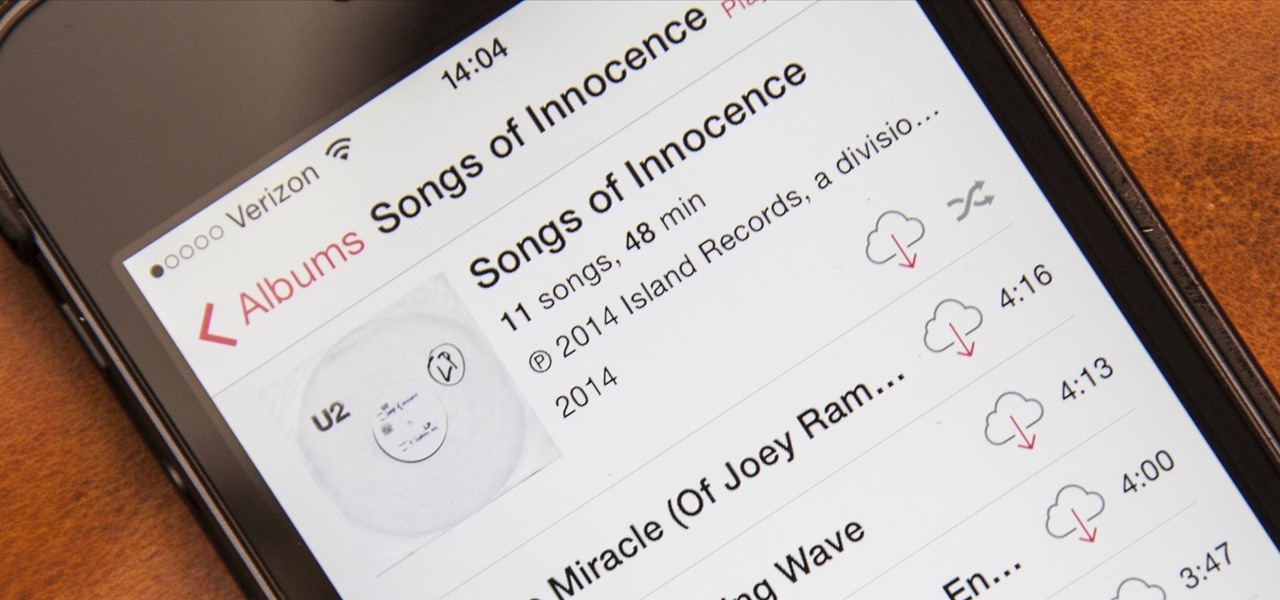
From my experiences, there are only two types of U2 people: those that love them and those that hate them. I'm the latter, so it's pretty damn annoying that Apple just added U2's new album, "Songs of Innocence," to my iCloud. If you find it creepy that U2 is appearing on your iPhone or in iTunes, don't worry—I've found a few ways to deal with it. UPDATE: How to Delete U2 Forever & Ever

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

The iPhone X is sure to be a hot seller this holiday season. You probably know someone with the $1,000 iPhone on their wishlist, and with a price tag that high, Black Friday is probably the best chance of them getting one. But there's only one store we've found so far that's even offering a real holiday deal for the iPhone X.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

If you relate in any way to having the need to carry your iPhone and your vaporizer in one hand, then keep on reading.

In Bhopal, India, a place nestled in between the royally pink city of Jaipur and the dry (i.e., alcohol forbidden) state of Gujarat, is a team of developers determined to make a fully driverless car suitable to the complexities of Indian traffic. An algorithm elaborate enough has yet to be made by any other company, but is the fundamental key to handling the intuitive habits of Indian drivers, the often intense and gridlocked traffic, and the country's vast expanse of jarring roads.
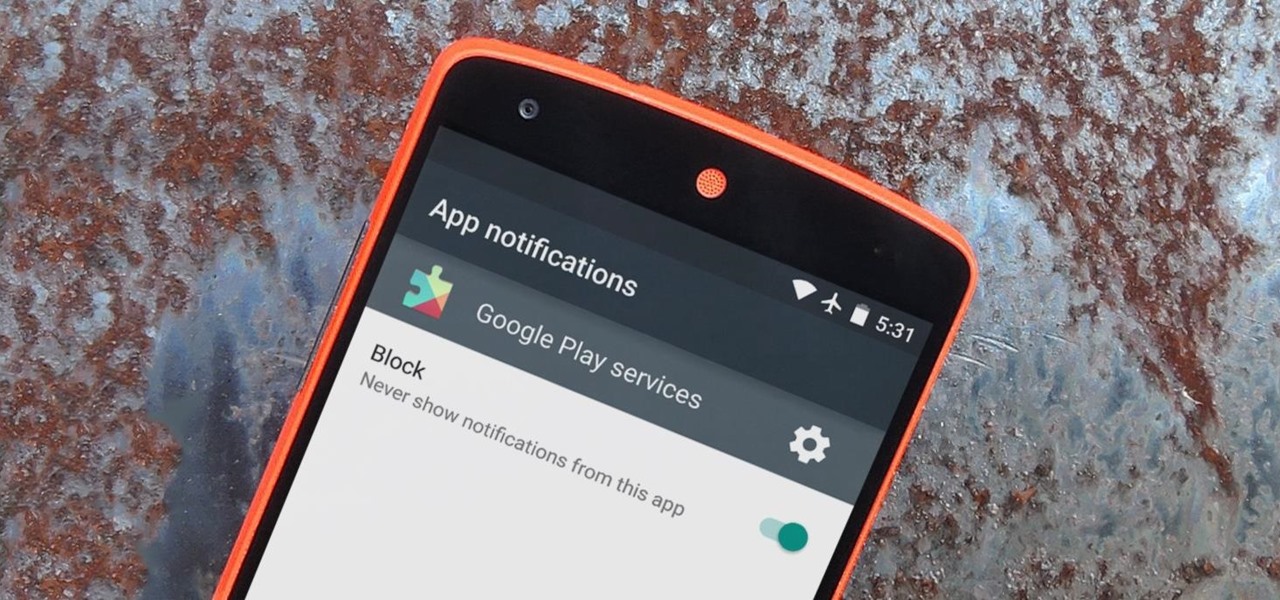
Have you ever had one of your Android games post a notification in a lame attempt to remind you to play? This is becoming a common practice these days, and to me, it's about as annoying as a Best Buy blue shirt when I'm just trying to check out the latest TVs.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements
In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

With over 2 million uploaded videos and over 28 million people who had talked about it online by the end of August, the ALS Ice Bucket Challenge was the most viral social media event of 2014. Its popularity provided the ALS Association with $115 million in donations to date, with everyone from students to veterans to celebrities contributing.
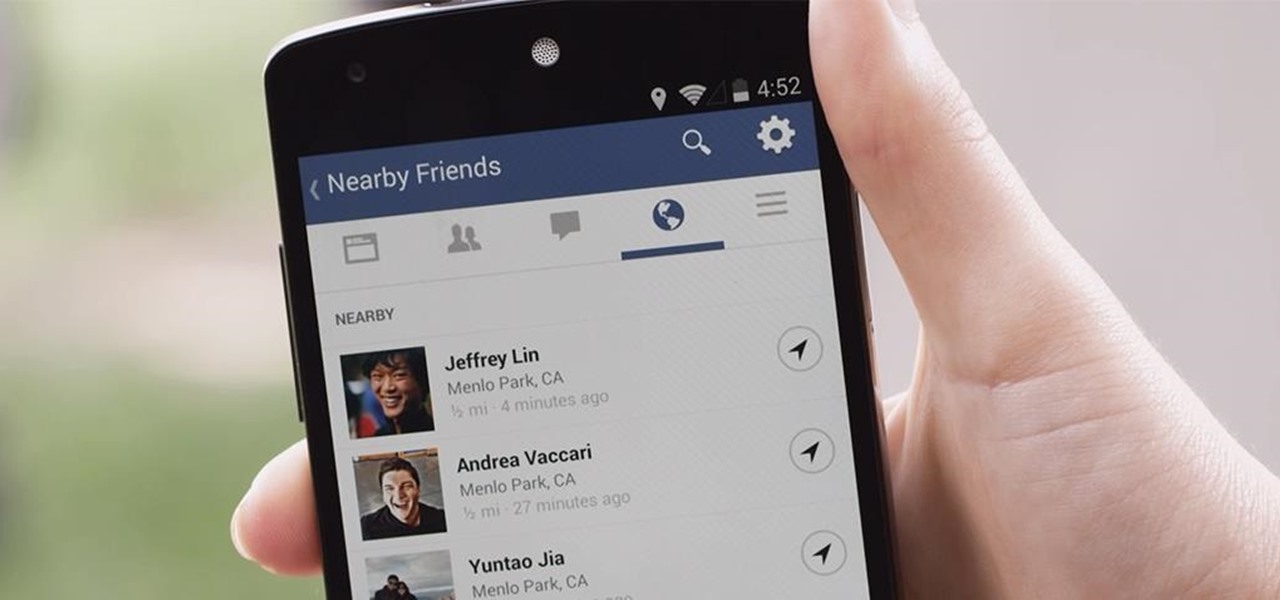
Facebook today has unleashed a new way to creep...er...keep in touch with "friends" using the official Facebook apps on Android and iOS.

I know all of you softModders love these little modifications, like enabling the hidden battery percentage on the Nexus 7 or getting the exclusive Google Launcher on your Nexus, so here's an easy one that lets you hide the soft-keys from your tablet, which will actually expand your screen to look a little bit longer.

You told yourself you wouldn't be one of those lame people who throws on a mask and shows up at costume parties, but here we are a day before Halloween and you still have nothing. Unless you want to endure endless ridicule, you can't skip dressing up altogether, but if you don't want to buy a pre-made costume your options are pretty limited.

#FOMO. If it bugs the living hell out of you that you don't know what that means, you're presently FOMO, as in you've got a Fear of Missing Out.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

In this video series, watch as Mike Purdy teaches you how to build and host online radio stations. Learn how to get the components and players for online radio stations, how to install the encoder and and streamer, how to get the rights to songs, and how to promote the online radio stations.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

What's the best part of the holidays, other than gorging yourself on food until you're physically able to hibernate? Imbibing delicious, hot drinks that are spiked to the gills with liquor.
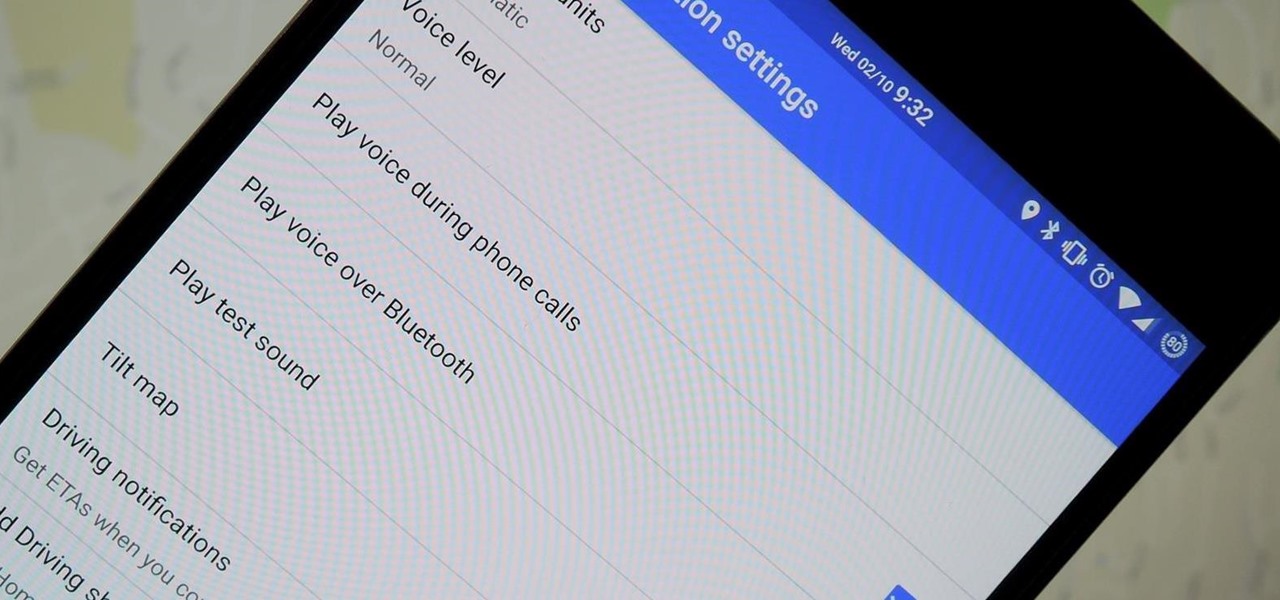
We've all been there. You're driving along with Google Maps pointing the way when you get a call from your friend asking you how much longer it'll be until you show up. You try to offer some lame excuse about how something came up last-minute, but you're interrupted, quite rudely, by Maps's voice guidance. The voice butts in again, and again, and again, to the point that you consider having Maps navigate you to the nearest cliff so that you can drive off it.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.