Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Your smartphone has a ton of ringtone options built in, but ringtones haven't really changed much in the past decade, and it's definitely not cool to hear someone in the supermarket with the same lame ringer. While replacing the stock sounds with a song of your choosing is the best way to keep your phone personalized, why not go a step further using a video?
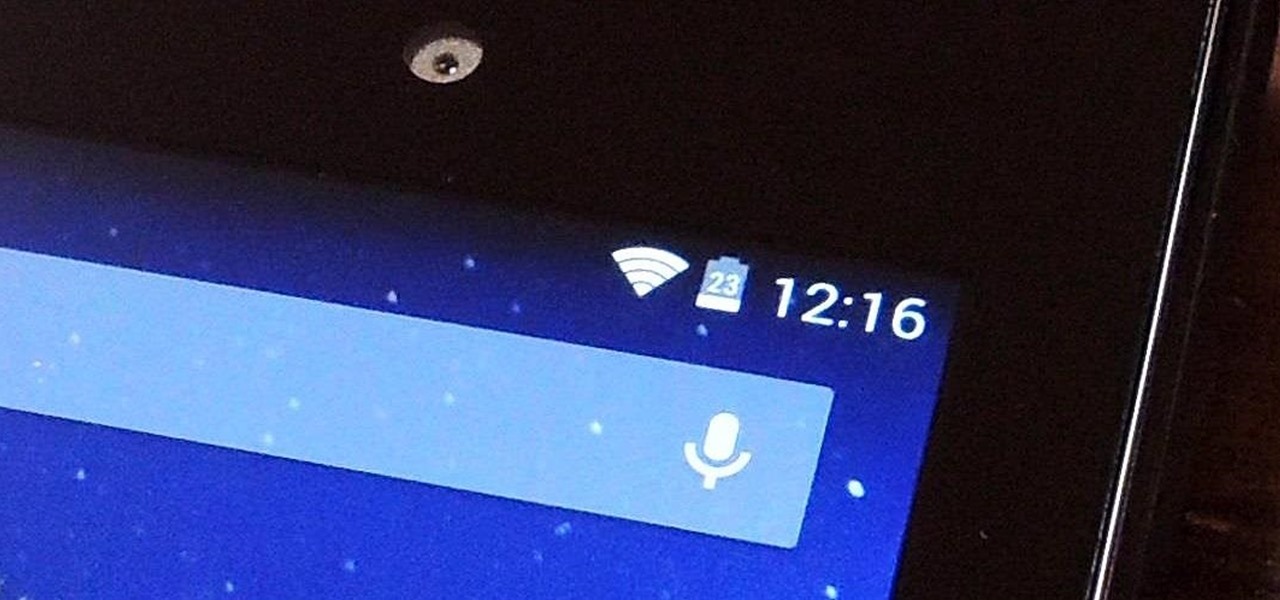
Much like the built-in screen recording tool on Android 4.4 KitKat, hidden features like the new battery Status bar icon must be manually unlocked on your Nexus 7 tablet. This is both exciting and annoying.
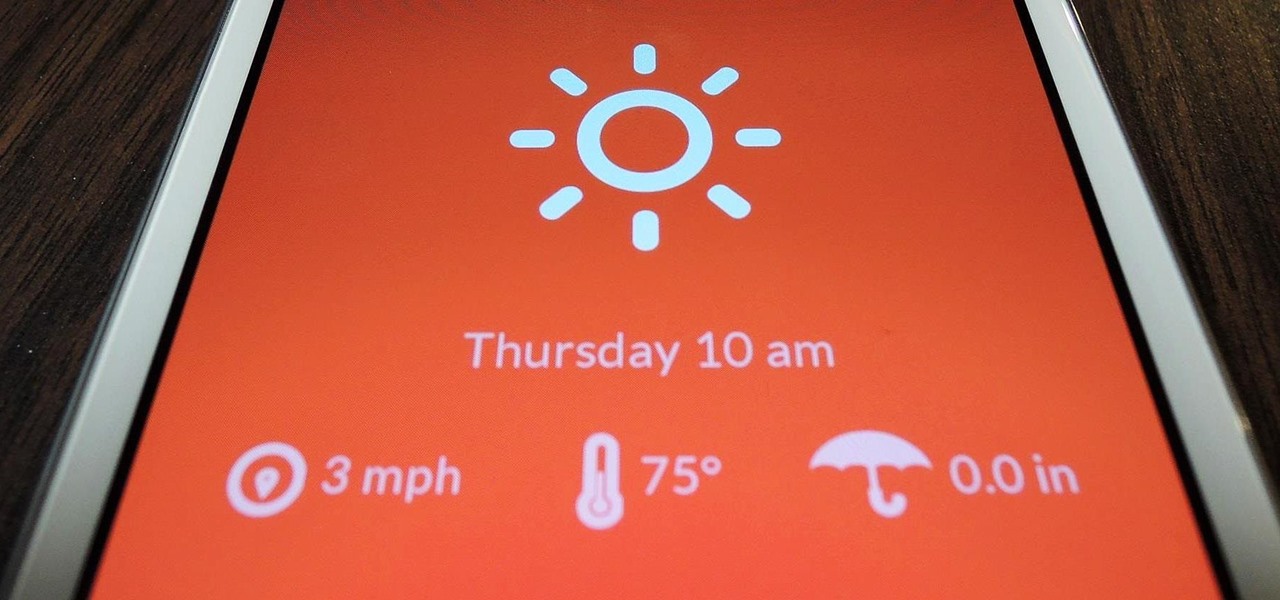
70 degrees, 8 mph winds, and sunny clear skies. That's the current forecast here in Los Angeles and I can't really complain. However, if you don't live in Southern California, checking the weather may be the difference between getting stuck in a snowstorm or remembering to bring an umbrella.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Sometimes the hardest part about getting your minecart rolling is the beginning takeoff. Have you ever started a minecart on a hill, and then tried to jump into it as it started moving, only to fail and watch it slowly dwindle into the distance?

Got moves? Than show them off! School dances can be pretty lame, but you could pump up the volume and make it one of the best nights of the school year… along with impressing all of your classmates (or maybe completely embarrassing yourself). Be creative with your sources to impress your classmates at your next school dance.

In this series of easy-to-follow diy videos, our Flash expert explains the intricacies of importing Photoshop layers of text and graphics, as well as import entire files into the Flash program. Once imported, these files can be turned into buttons for your interface, images and movies for your website or simply moving pictures to show your friends and family. Our expert also show you how to retain the links of the files you are importing and how to use the Flash video encoder. He also demonst...

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

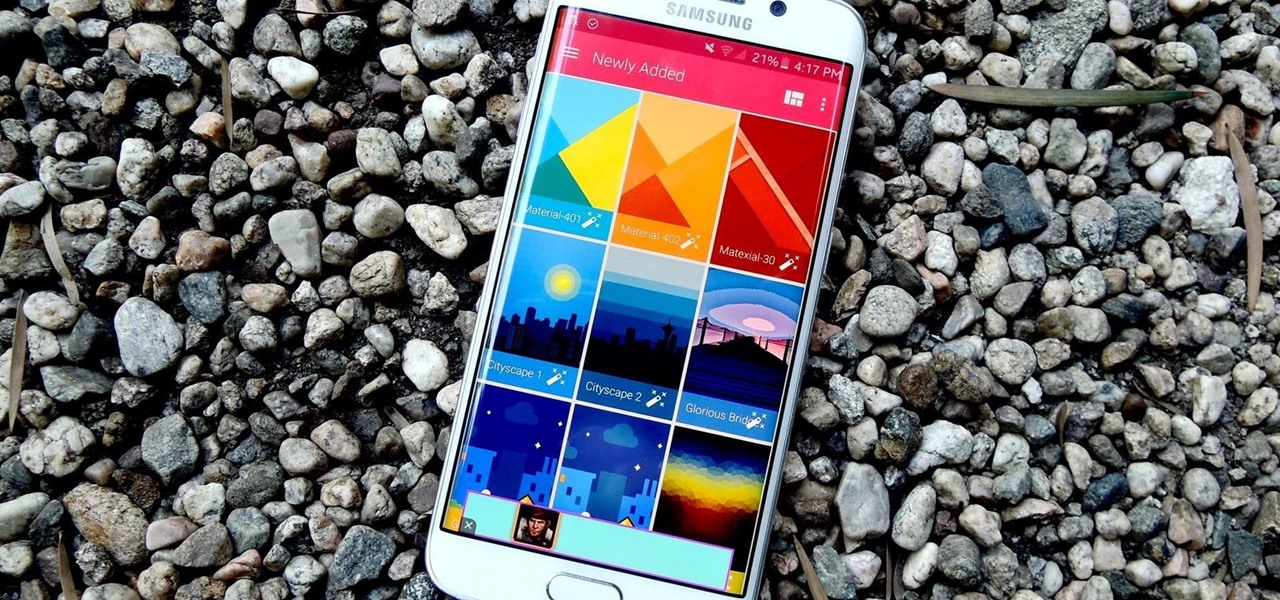
Out of all the questions that we receive from our readers and viewers here at Gadget Hacks, the most frequently asked one is "What wallpaper is that?" On occasion, our wallpapers may be personal or images from the web, but for the most part, they come from dedicated wallpaper apps.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

MySpace is an excellent resource for up and coming musicians. If you just can't do without that hot new jam, then it's time to rip your favorite song using Audacity media player. This video tutorial demonstrates the process of ripping MySpace songs in a few easy to follow steps:

For the dedicated prankster, April Fool's Day is no joke. Nothing will stop them from coming up with the cleverest, most elaborate prank the world has ever seen. Or at least—their victim.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

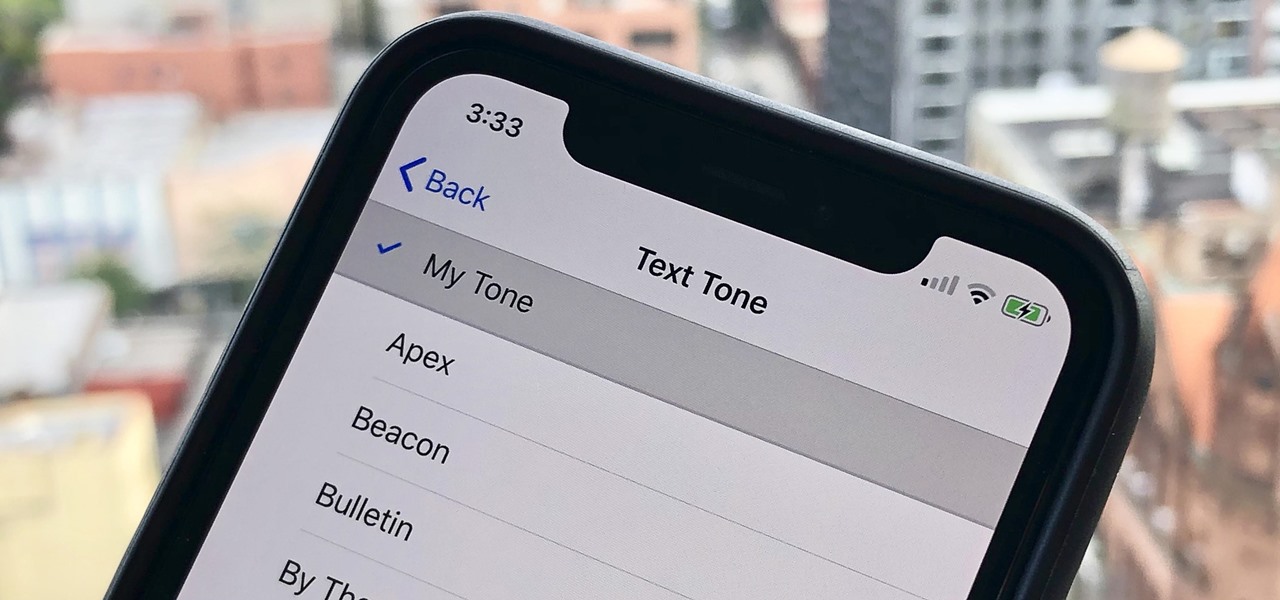
Your iPhone comes packed with a long list of excellent text tones to choose from. Bamboo anyone? Of course, for some of us, stock sounds from 2013 don't cut it anymore. We want customizability, something that's found more on Android than iOS. However, you can add your very own text tones to your iPhone right now, so long as you have a sound file in mind and a computer running iTunes.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call. Apple doesn't let us pick a song from our music libraries, but there is still a way to use our favorite tunes as tones.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

Greetings my fellow hackers.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a day and age where smack cam is the new level of pranking, so it's time to step your game up, novices.

While many of the features in the iPhone 16 and 16 Pro series build on what we've seen in previous iPhone models, Apple has packed the 2024 lineup with iOS 18 and plenty of fresh upgrades worth considering.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Adobe Media Encoder CS4 takes the place of several tools that users had to rely on for processing and compression. The Adobe Media Encoder CS4 converts to several different formats, including formats for web and mobile devices. There are also speech transcription option and batch processing. See how to use the Adobe Media Encoder CS4 in Premiere Pro CS4 for Flash video encoding and exporting from Premiere Pro CS4 in this tutorial. Use the Adobe Media Encoder CS4 in Premiere Pro CS4.

Creating your own video tutorials. Over the last few years we have created a whole database of short video tutorials at helpvids.com - showing you how to use different programs.

Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to export audio to multimedia formats such as Blu-ray and YouTube as well as how to launch the Adobe Media Encoder and render vide. Export a project from Premiere Pro CS4.

This Adobe CS4 software suite tutorial shows you how to create FLV and F4V files in After Effects CS4. You will also learn how to create and optimize FLV files in Adobe Media Encoder, Premiere Pro and After Effects CS4. Create FLV and F4V files in After Effects CS4.

Check out this report ONLY available at http://www.sunsetsurf.com/

So the singing is kind of lame, but we love the lyrics.

Got a spare plunger lying around? Why not take a dump in it, plunge it onto your best buddies car windshield. Smashed doodoo butter lying in wait under a seemingly lame prank of a plunger on the windshield.

Picture frames with images of your loved ones can be pretty lame gifts, but not when they're made out of chocolate! This video will show you how to make a homemade picture frame made entirely of chocolate. Surprise (and we mean surprise!) someone you love with this message of pure chocolate-love! Emily Jones, chocolate sculptor, shows how it's done. The most important step is the tempering of chocolate, which you'll find in the recipe. Make an edible picture frame made entirely of chocolate.

I'm pretty sure every villain Batman has put away over the years makes an appearance in Batman: Arkham City. If that fact weren't so awesome, it'd be freaking ridiculous. To get the 'Sandstorm' achievement, you have to defeat Ra's al Ghul in some sort of magical sand land.

Here's a nice challenge for you completionists out there. In Assassin's Creed: Revelations, after you collect all 10 of the memoir pages, load up Sequence 5 - Memory 3 and head over to the Hagia Sofia. Once you're inside, I hope you're wearing your platforming hat, because you will need to jump, climb, slide and glide your way to the very end of the challenge course.

I found this old video I made for a class project about staying in a hostel. It's corny as hell and it's the first time I've ever narrated, but it was for school, cut me some slack.