Still got stock? Many factory installed exhaust systems not only sound anemic, they actually are because they scrub power. The designers who are given the task of producing these pipes are often handcuffed by several different requirements that add up to one big compromise. Exhaust engineers are required to build systems that are quiet and that meet certain types of emission standards, but not all of the design concerns are driven by government regulations. Some are based on a perception of w...

Check out this instructional climbing video that demonstrates how to set up the ascent system for crevasse self rescue. Hooking up the prussik is the subject of this video and stops at the second ascender required for upward mobility. Watch all the crevasse self rescue series and you may get the hang of this. It is best to practice this somewhere dry and safe before the real thing happens. When you are in the hole things get tougher.

Big Tony the plumber introduces you to the process of installing a residential lawn sprinkler system.

Perform cable management to improve cooling and system layout.

Understanding the Binary Numbering System and how to decode binary numbers.

While Elon Musk is in Los Angeles showing off the future of personal transport via the Cybertruck, another, unaffiliated group is taking one of his most popular ideas to market, with augmented reality as a key part of the plan.

It looks like Magic Leap is getting its ducks in a row to launch its Magic Leap One: Creator Edition as the company's name is once again showing up in US Patent and Trademark Office (USPTO) filings.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

Augmented reality developer Blippar has created a new visual positioning service based on computer vision that is two times more accurate than GPS in urban locales.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

When your clutch pedal is dropping down and not coming up again, the cause is most probable one of the cylinders in the hydraulic clutch system. The video will give you a step-by-step tutorial on how to replace both, the master and the slave cylinder. In addition, it is a good idea to also replace the pressure hose in-between the cylinders.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

If you need a dolly for your movie masterpiece, you don't need to go with a professional dolly system. You can save that money for your expensive actors and actresses by building your own DIY camera dolly on the cheap. You'll need some nuts and bolts, PVC pipes, scrap wood, drill bits and a drill, inline wheels and a hammer. This homemade camera dolly will cost you around 65 bucks.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

Learn how to use Audacity, a free audio editing application that can be used to record music, podcasts, and more. You will learn how to install the LAME Encoder, set your preferences, save the project, record, preview your recordings, edit content, remove noise, adjust volume, time shift, and exporting. Each of these is an important part of the podcast creation process and you will learn to do it all in this Audacity video series.

Build a mineral oil computer aquarium. It cools the system while giving you something to look at.

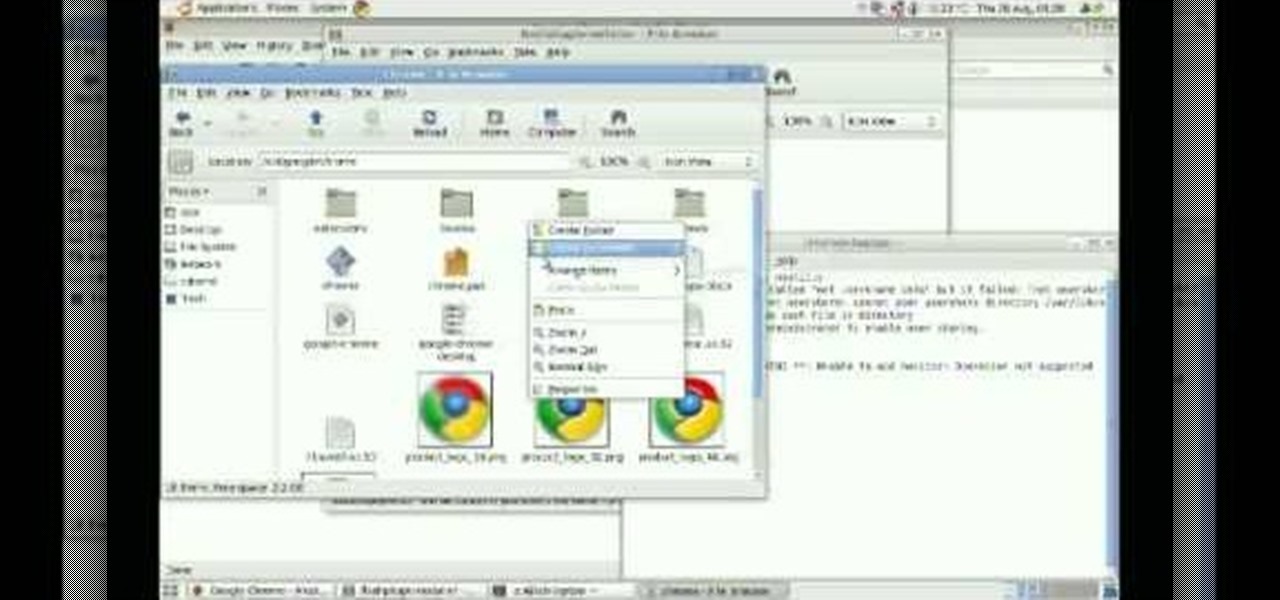
This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.

If you want to run multiple windows operating systems at the same time you first need a Windows computer, the installation disk for the operating system you want to run, and Windows Virtual PC 2007. To install this, first type in Virtual PC 2007 to Google, go to the Microsoft link and download and install the program. Now, open the Virtual PC and click next on the wizard. Name your hard disk and click next until you choose where you want this at. Now your virtual hard drive is created. Now, p...

In this how to video, you will learn how get VMWare Fusion on your Mac. This will allow you to install Windows and run them on the same computer. First, go to the mediafire page and download the files. Next, download and install Unarchiver to join the files together and extract the file. Mount this file on to your computer. Run the file and click install. Once that is finished, open it. You will see your Windows partition if you already have one installed. To install a new one, click new and ...

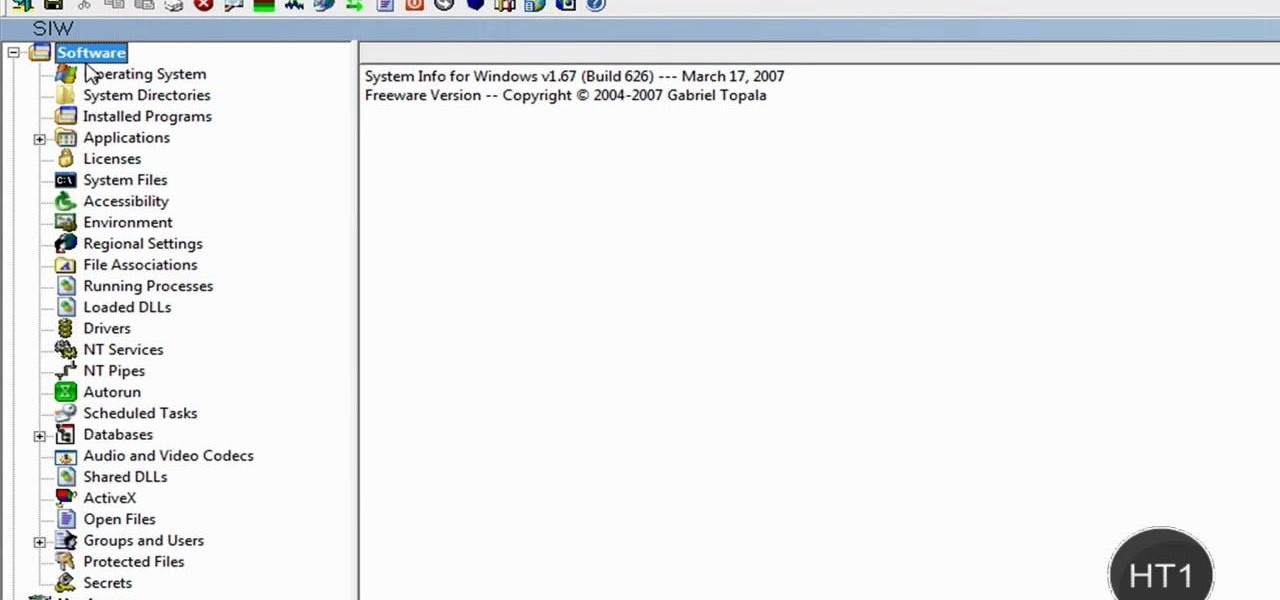
How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

On 4Runners equipped with the automatic climate control system, the left and right hand knobs control the temperature settings for the driver's side and passenger's side. To use it, switch on auto mode by pressing the ‘auto’ switch on the left hand knob so the amber light is illuminated. Then press ‘dual’ on the right hand knob so its amber light is illuminated. Rotate the left hand and right hand knobs to set your temperatures. The system will maintain those temperatures. If you want the who...

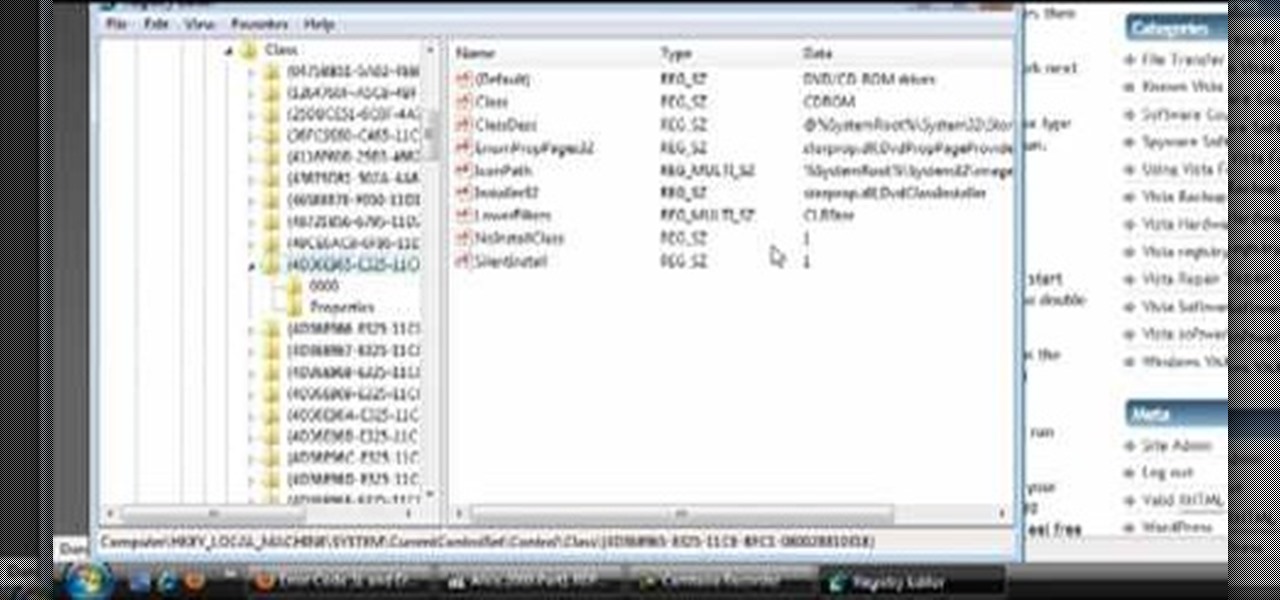
This how-to video explains how to fix DVD/CD player related issues with error code 31,32 or 19 in the computer that is having either Windows Vista or Windows 7 as their operating system.

Warts can be embarrassing – as well as contagious. Help minimize the chance you'll spread them to other parts of your body, or other people.