Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

The new rail system might be a small (Read: BIG) problem for those who like using rail systems. See for your self! Check out BebopVox's video:

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Much like the built-in screen recording tool on Android 4.4 KitKat, hidden features like the new battery Status bar icon must be manually unlocked on your Nexus 7 tablet. This is both exciting and annoying.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

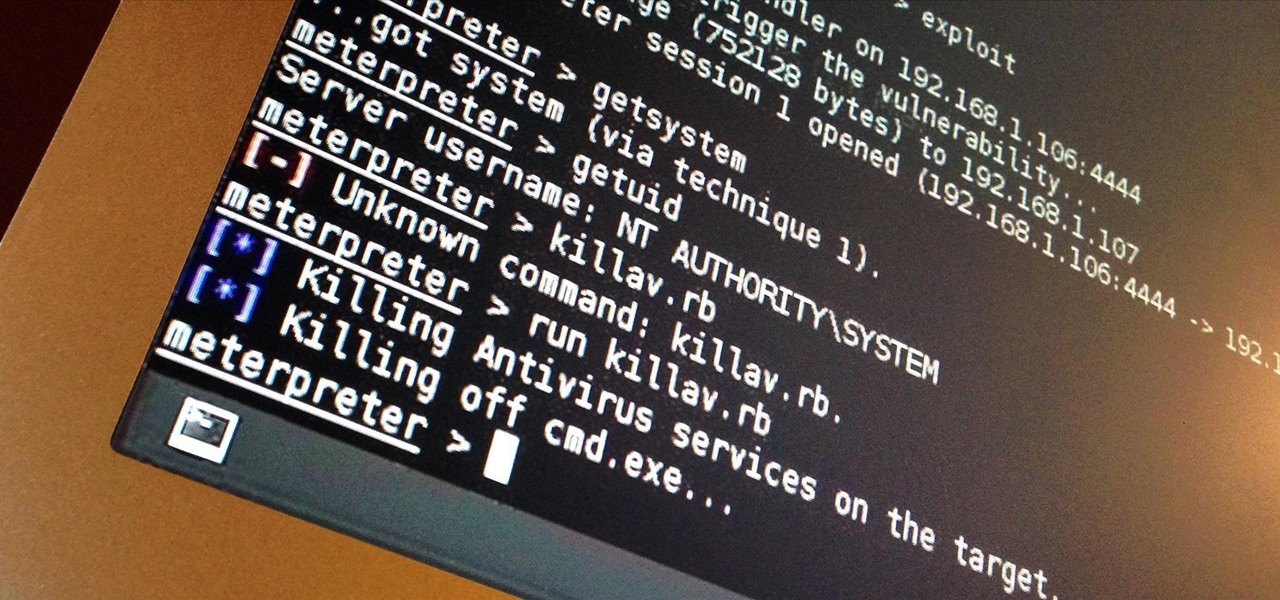
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear Store.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

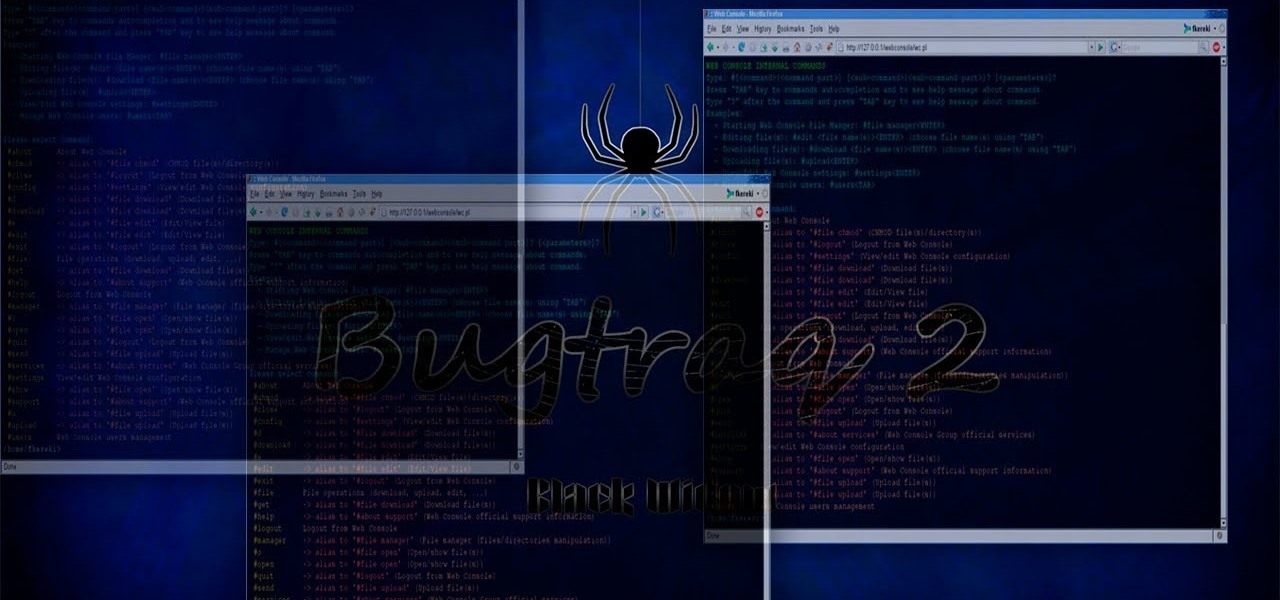
In this "HOW TO" I will show you how to install and mange yourself in bugtraq. You will jave to folllow a couple of videos and then you will know everything that you need on how to install and configure bugtraq.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

The Jelly Bean update brought a lot of cool features to the Samsung Galaxy S3, but one nasty bug remained. Something was causing "Android System" usage to be consistently high. Of course, the percentage of this process that is used is dependent on what you're doing at any given time, but it shouldn't be anywhere near this level with "standard" use (calls, texts, emails, light browsing, etc.).

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Imagine two stakes in your backyard. Now draw an east-west, north-south coordinate system on your lawn. Measure the east-west distance between the stakes and also the north-south distance. Take the square root of the sum of the squares of the two measurements and, voilà, you end up with the "distance" between the two stakes.

Keys are on the way out. They're clunky, take up precious space, and slow you down when you have tons of identical-looking gold ones on your keyring. Everything we can open with keys can now also be opened with wireless technology in just a click—so why use keys anymore? Sure, you can pay hundreds of dollars for an automated lock system on your house—but why do that when you can build it yourself!

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install KDE 4.3 Plasma on [k] Ubuntu Linux.

With iOS 5 coming out, the folks behind RedSnOw were able to jailbreak the operating system so that you can install Cydia on it. This walkthrough / tutorial will show you how to jailbreak your iOS 5 iPad, iPhone, or iPod touch.

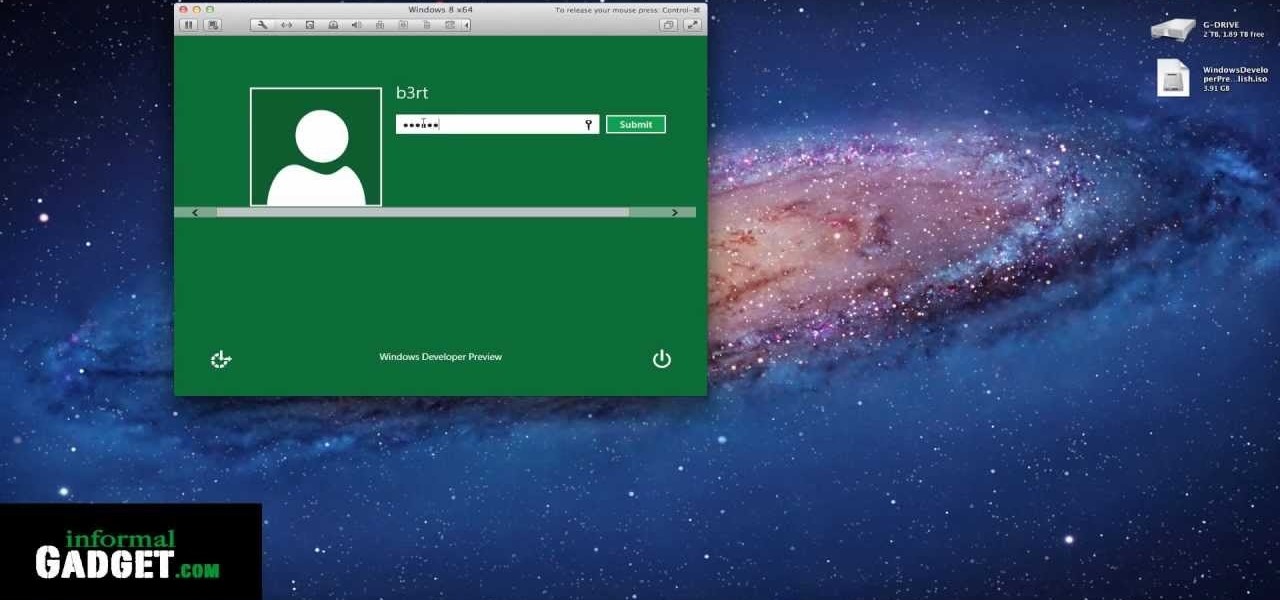
You can give the Windows 8 Developer Preview a spin on your Mac laptop or desktop by installing and running it with VMWare Fusion 4. VMWare Fusion 4 allows you to run Windows from within OSX so that you can have access to both programs and operating systems at the same time.

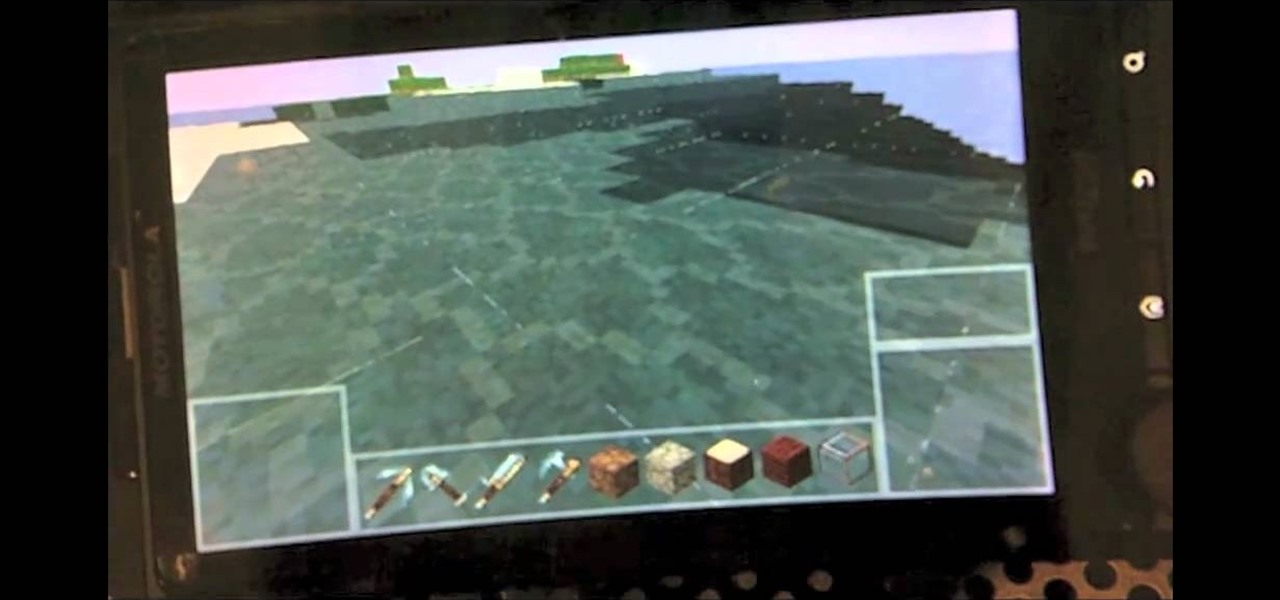
The low system requirements of Minecraft make it ideal for playing on an Android smartphone. If you're looking to find out how to download, install, and play Minedroid, a version of Minecraft designed for your Android phone, take a look at this walkthrough and check out the download options below.

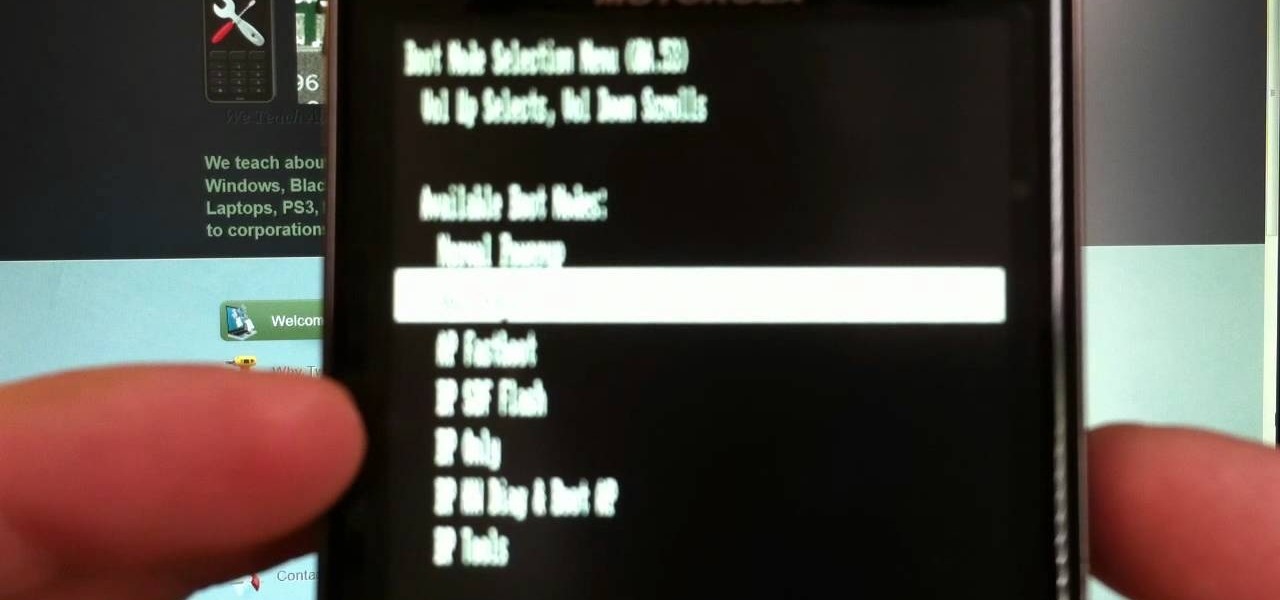
If your phone won't boot or you need to dig deeper into the Android operating system on your Motorola Droid Bionic, this tutorial on booting the Bionic into recovery mode should help you out. Just be careful, because a factory reset on the Verizon Wireless smartphone will cause you to lose all of your data.

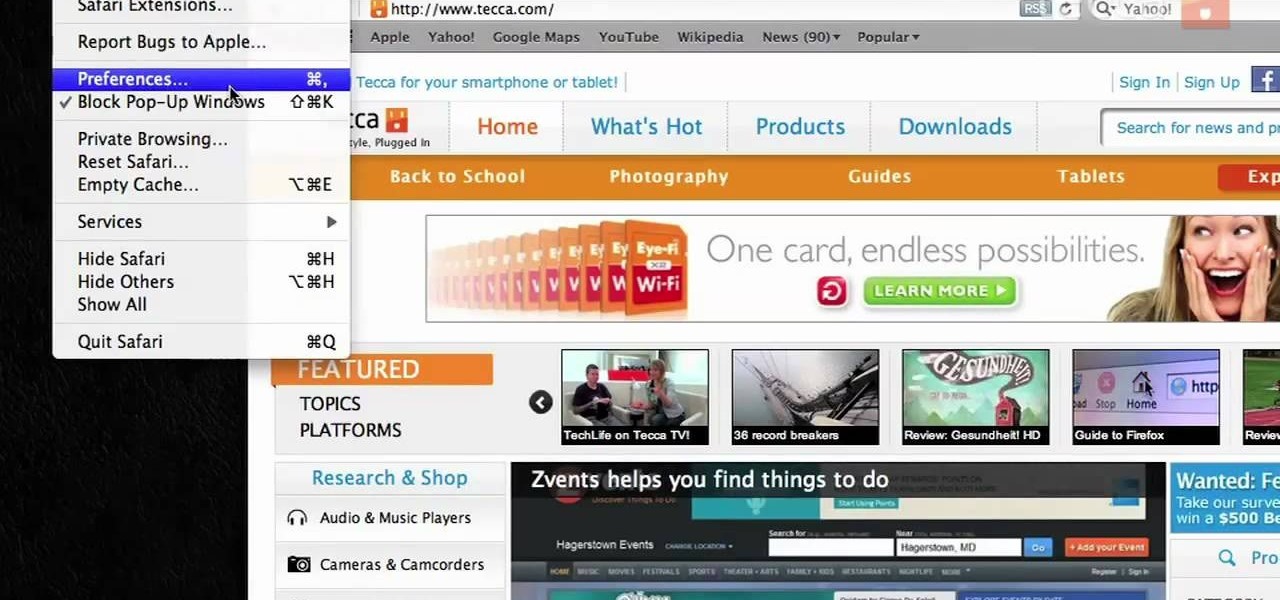
If you want to permanently set the default browser on your Mac notebook or desktop, take a look at this walkthrough. You can set any browser to open up by default when you click a link or try to access webpages in OS X.

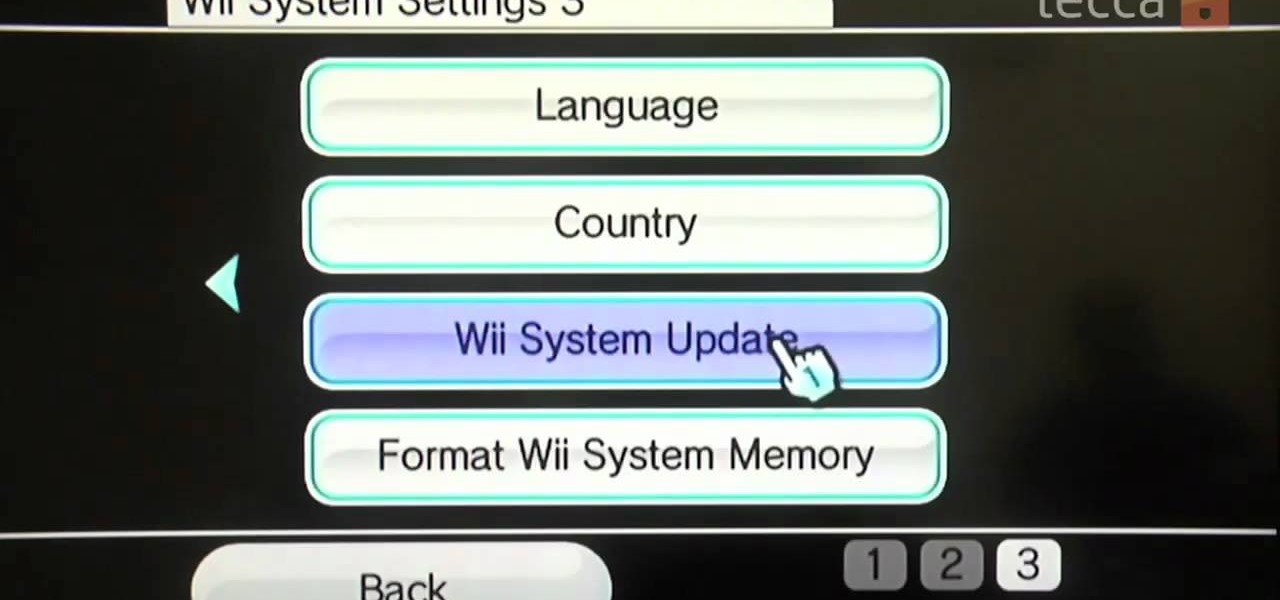
Using the Wii Options menu, it is possible to upgrade your Wii software to the latest version released from Nintendo for the gaming console. You will need to have an active internet connection to download the update first, so make sure that the Wii is connected to your home network. Be sure to check for upgrades every so often so that you have the latest features!

Copying a file's path on your Mac isn't always an easy task. Thankfully, this cool little OSX utility called Copy Path Finder helps solve this problem and lets you copy the path of a file in your file system to the clipboard so that you can paste it into a text editor later.

Marvel vs. Capcom 3 is a frenetic modern fighting game, and learning how the combo system works and being able to apply that knowledge on the fly is the key to arcade success in the game. This video will teach you how the combo mechanics in MvC3 work and how you can use them to come up with new combos on the fly and beat any character, as any character, any time.

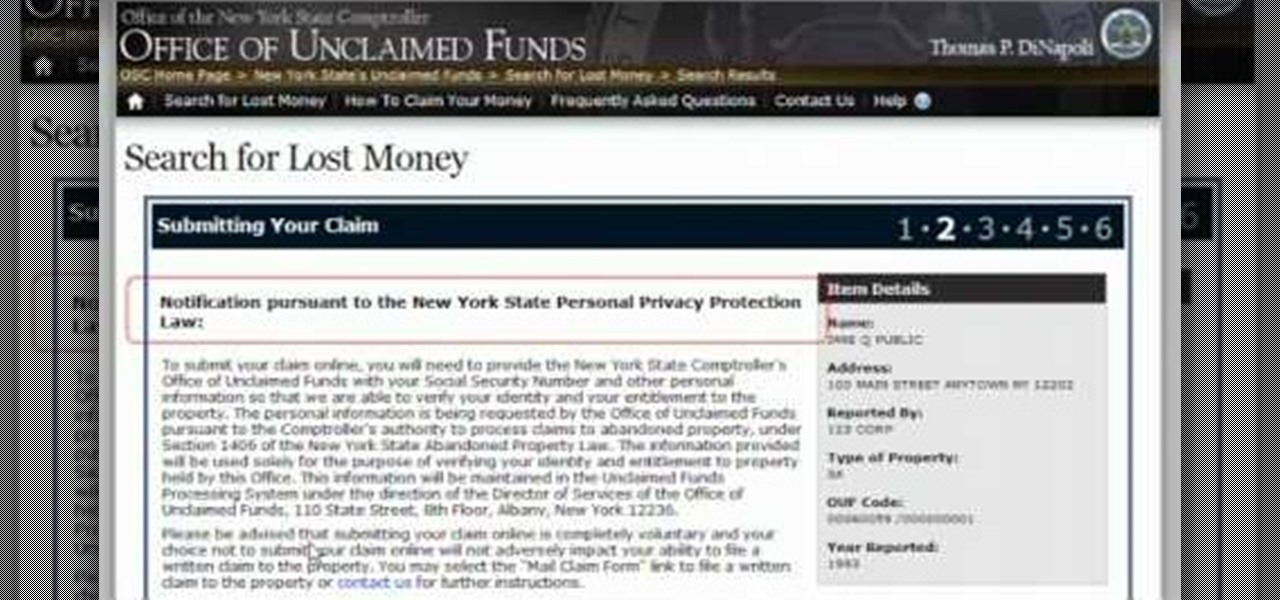
Unclaimed money, or money that has gotten lost in the financial system but is owed to you, is all over America. If you think there might be money that belongs to you in the state of New York, check out this video made by State Comptroller Mike DiNapoli outlining how to check whether you are owed unclaimed money and how to claim it.

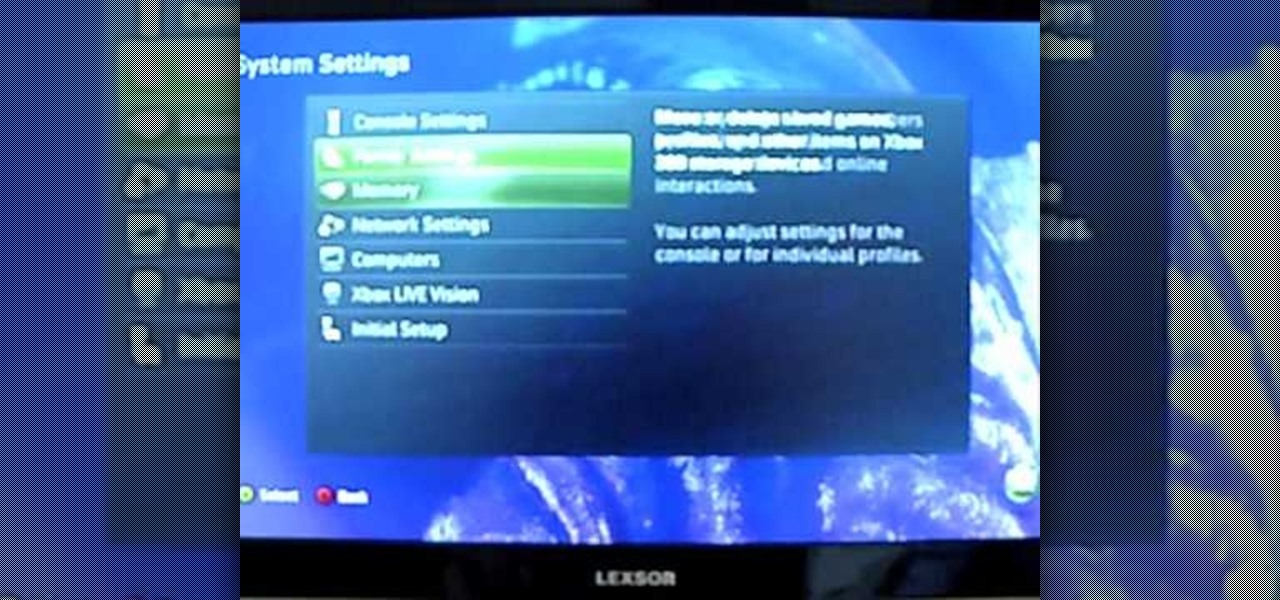
If you're looking to expand the storage capacity of your Xbox 360, you should look no further than a USB memory stick. And, this video will show you how to do it. You can store games, profiles, basically anything that's stored on your Xbox 360 game system. Microsoft recently added a patch to the game system to make this process really simple and easy to do. So, get a memory stick and start bulking up today! Oh, all that video game glory!

The Nintendo DS Lite is the best portable gaming system ever, and you want to make sure yours works forever. If you find that your unit won't charge or turn on and plugging it in makes the charge light flash, watch this video for a guide to taking the DS Lite apart and jumping the fuses with a conductive pen like a CircuitWriter so it will power on once again.

This video will show you how to play PlayStation 1 games on your PlayStation 3 without modding the system. Note, this how-to does require you open up your machine, so if you're still under warranty you may wan to think twice!

This video shows you how to set up a mini wireless spy cam. Where you put it is up to you. Who you spy on is up to you. If you're wanting to keep an extra set of eyes on someone, watch and learn. So whether you're looking to put a camera in your bathroom or garage, go for it.

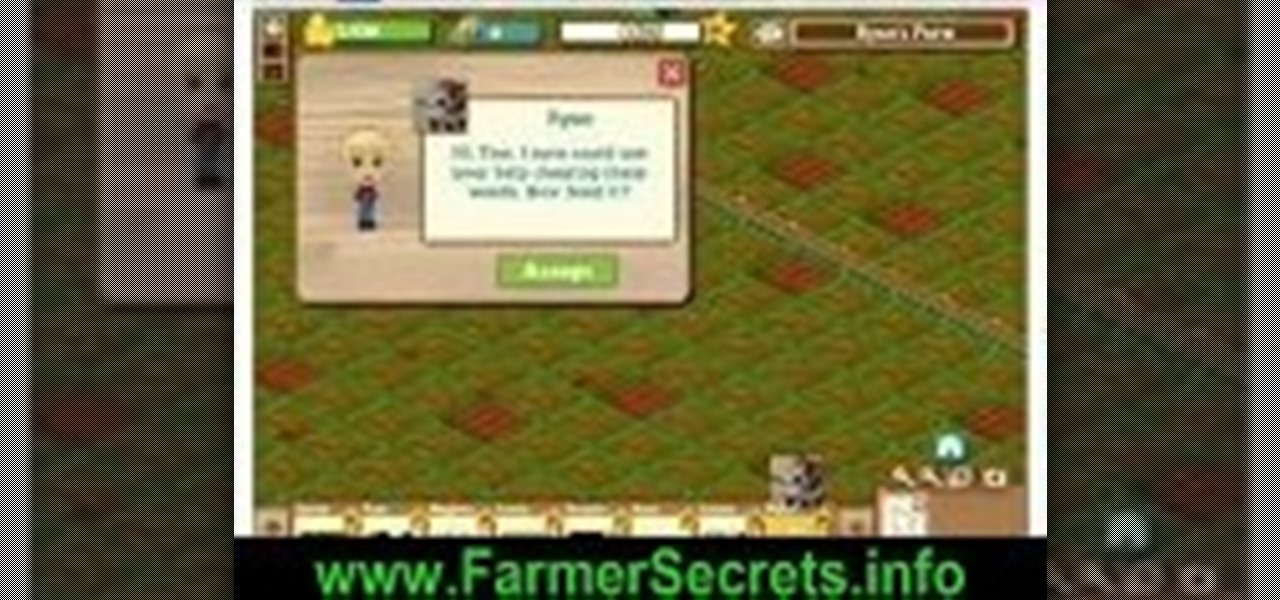
Are you a Farmville fan? Looking to get ahead without all the time and hard work? This how-to shows you how to level up quickly and beat the system. This cheat is easy to use and will let you plant your corrupt seeds quickly.

The achievement system and hard drives of modern video game consoles present an as-yet-underutilized potential for crossover content between games. Microsoft has finally taken advantage, and recent Xbox 360 releases World of Keflings, Ilomilo, and Raskulls contain some really awesome crossover content. Watch this video for a guide to accessing and using all of this awesome and visionary content.

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

Learn how to multitask when running iOS 4.2 or 4.2.1! The 4.2 release of Apple's iOS 4 mobile operating system for the iPhone, iPad and iPod Touch brings with it a host of new features. While that's certainly a cause for celebration, there's also, believe it or not, a downside: learning how to take advantage of them. Happily, the web is awash in helpful video tutorials like this one which make the process a pleasure (and a simple one at that).

The Sanctuary menu system in Fable 3 has spawned some controversy, but it's pretty novel when you consider that there are a hidden Gold Chest and Gold Key right there in your pause menu! Watch this video to learn how to unlock and find the Gold Key and then the Gold Chest in your sanctuary.

In this tutorial, we learn how to count cards in Blackjack. The basic principle in counting cards is that high cards are better for the player and the low cards are better for the dealers. There's a high concentration of Aces and 10's which gives you a higher chance of blackjack. 10's will increase the chances the dealer loses and you win. It's not hard to count cards, it's a simple system of adding and subtracting by 1. It is very simple where you learn how the high and low system works. Onc...