While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

After joining Google and Huawei in underwriting the UW Reality Lab at the University of Washington in January, it appears Facebook is already seeing a return on its donation.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

After weeks of teasing what many hoped might be a live, on-device demo of Magic Leap software to go along with the hardware glimpse we got last month, it turns out that all we got was a bit of new demonstration video footage.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

For every cool new thing Android Oreo brought to the table, Android 8.1 adds a bit of polish. After a brief but successful beta period, Google started rolling out the official 8.1 update to its Pixel and Nexus devices today, and it's everything Android 8.0 should have been.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

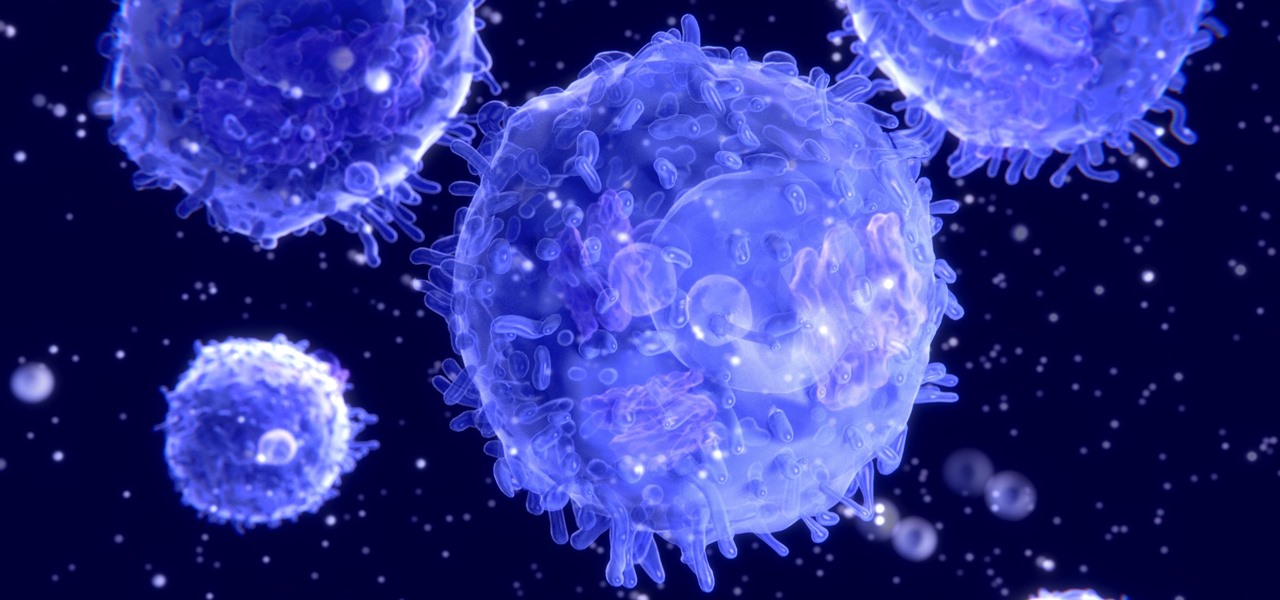
As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

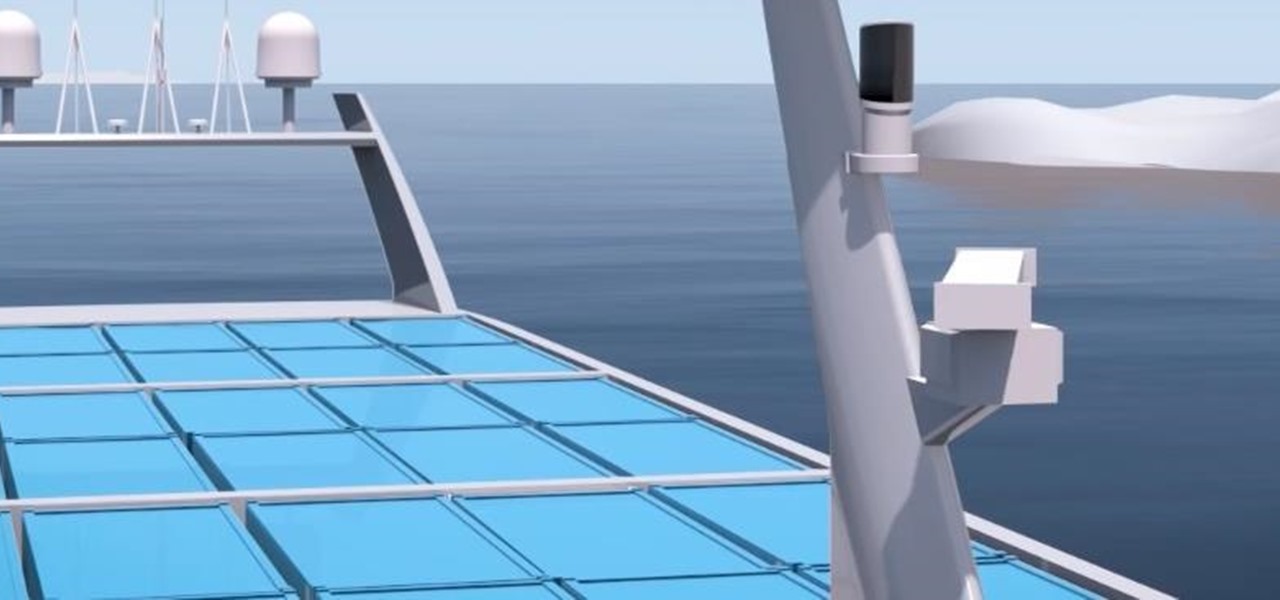
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

It's the end of an era. Facebook's WhatsApp just announced that older Android devices equipped with the Gingerbread operating system will no longer be able to use the messaging app as of February 1, 2020.

A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.

Apple's iOS is a great operating system, but it's not without its faults. Minor quirks have plagued the Apple community for years, such as a general lack of customization, a poor notification system, and some interesting UI choices like the intrusive volume popup. With iOS 11, Apple's tackling many of these pain points, not the least of which is being able to select multiple home screen icons at once.

Google's Pixel phones claimed the top spot in our ranking of the best phones for rooting, but they do have one drawback from a modder's perspective: Because of their A/B partition layout for seamless updates, the devices don't have official support for Magisk. Thankfully, though, developer goodwin has stepped in with a fix, so we can now get Magisk working on the Pixel and Pixel XL.

Google's working on a new mobile operating system called Fuchsia, and while we don't know much about how they intend to use it, we're now getting a glimpse at what the main interface will look like.

Everyone loves emojis, but some folks aren't quite happy with the way the little yellow guys look on their particular phone. In order to replace them, however, your device needs to be rooted, and you'll usually need to perform some complicated procedure that ends up making your phone hard to update since it modified a ton of files on your system partition.

While the technology continues to mature, businesses from various industries continue to adopt augmented reality to improve the efficiency of business processes. In this edition of Brief Reality, as conference season continues, we see examples of augmented reality applied to logistics processes and marketing of industrial supplies, as well as the topic of discussion at another trade show.

HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

Emoji, emojis, smilies, or smileys—whatever you want to call them, those little yellow icons have firmly implanted themselves in the human lexicon. However, just like with localized languages and dialects, emoji can be very different from one another depending on the device or operating system you're using.

DAQRI, a company mostly known for its odd but fun-looking industrial Smart Helmet, unveiled their new Smart Glasses product at CES 2017. Their smartglasses look like a strange attempt to answer the Microsoft HoloLens, and the price tag of $4,995 for the developer's edition reinforces that notion.

Augmented reality software developer Maxst has made the move into hardware with Revelio, their new untethered AR smartglasses. These stereoscopic glasses feature an Octa-core processor, 2 GB of memory, a 40-degree field of view, and a 720p display, and they do not require being connected to a phone or computer.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

If you're an Apple user and want an untethered virtual reality system, you're currently stuck with Google Cardboard, which doesn't hold a candle to the room scale VR provided by the HTC Vive (a headset not compatible with Macs, by the way). But spatial computing company Occipital just figured out how to use their Structure Core 3D Sensor to provide room scale VR to any smartphone headset—whether it's for an iPhone or Android.

When Google released the first Developer Preview build of Android 7.0 Nougat, users were happy to see that a new "Night Mode" was included among the changes. The feature would cancel out any blue light emitted from your screen to help you get to sleep a bit earlier, quite similar to f.lux for desktop computers, or Apple's Night Shift for iPhones. It could be set to turn on automatically based on time of day, or you could manually enable Night Mode with a Quick Settings toggle.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Microsoft did a wonderful thing in 2015: for the first time, it was offering a free upgrade to Windows 10 for all current Windows 7 and 8.1 users. And, if you were lucky, the upgrade process was relatively simple and painless. There were, however, some questions after the everything was said and done.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...

Windows has always been pretty customizable, and there are a ton of ways to change up the way your PC looks—though, it hasn't always been easy. In the past, changing anything other than wallpapers, titlebars, and fonts involved long hours of switching out system files with modified versions and changing icons to no end, but that's not the case with SkinPacks.

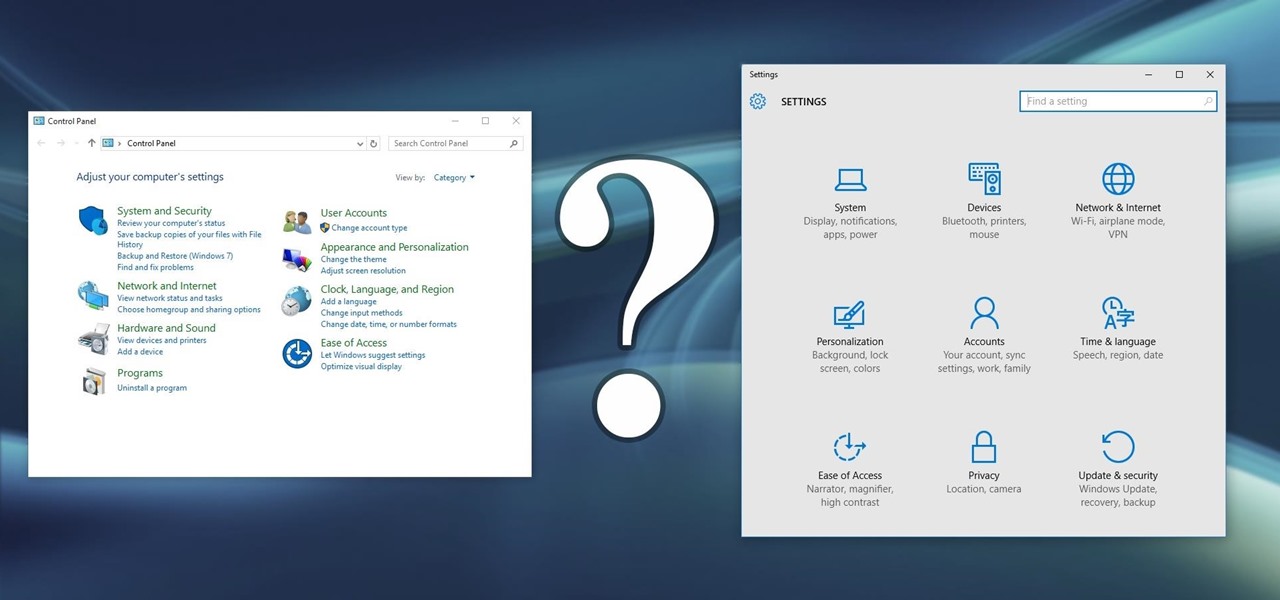
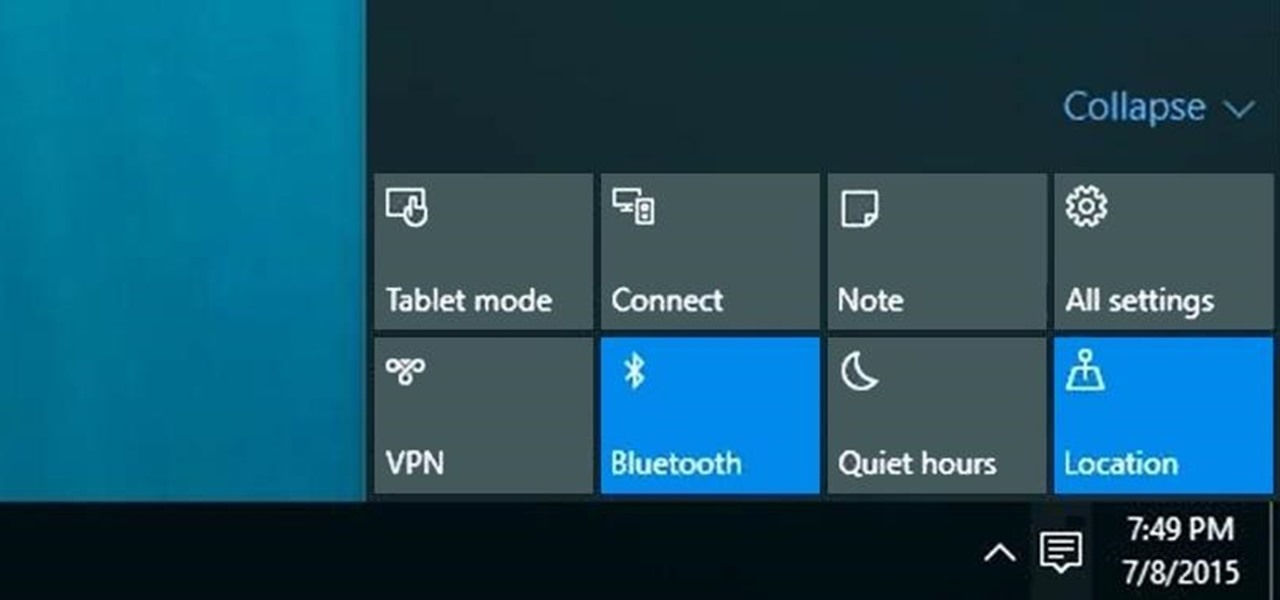
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.