With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...
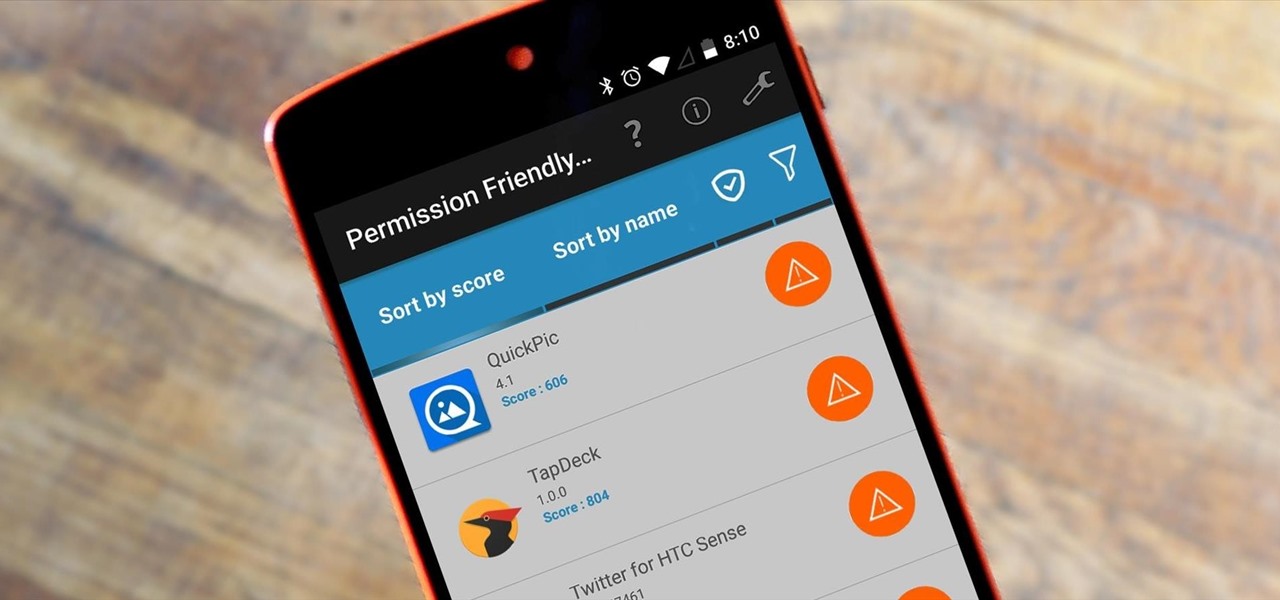
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.
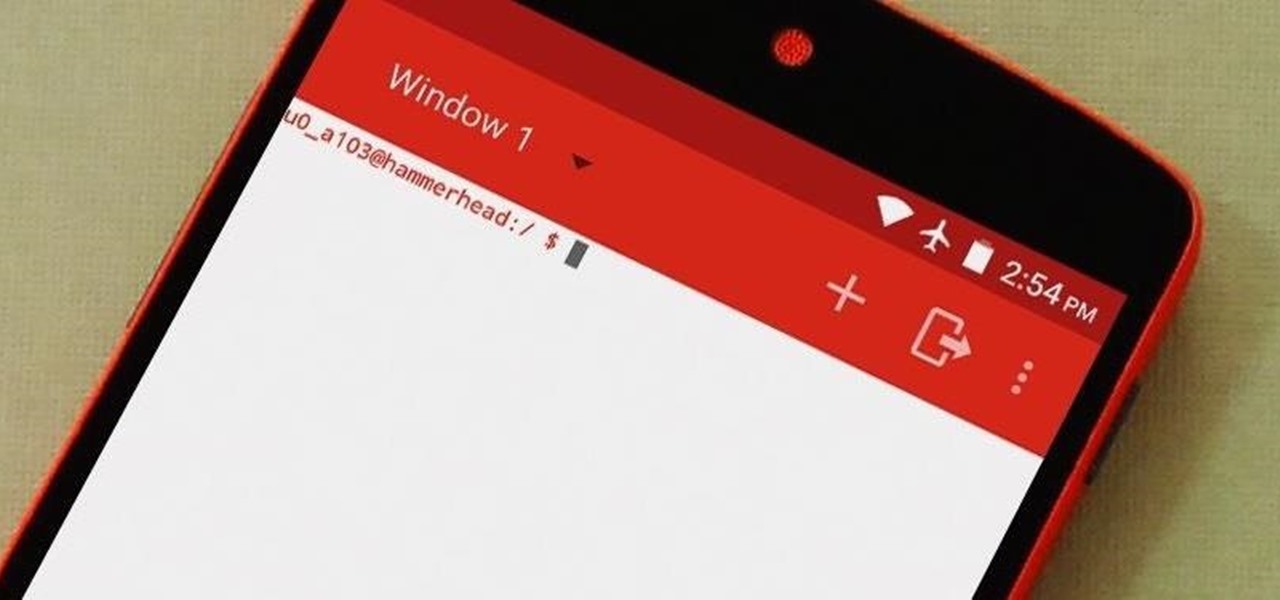
Deep down, Android is a fork of Linux, which is a desktop operating system that started out as entirely command prompt-based. For that reason, many system-level tasks can still be executed within a terminal emulator app.

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

After the Galaxy Note 3 firmware updated to NF4, Samsung decided to remove the option to hide apps in the app drawer, replacing it with an uninstall/disable feature instead. Before, with the hide feature, you could simply hide third-party apps that were barely used or that you didn't want others to see. Now, you can only completely get rid of them.

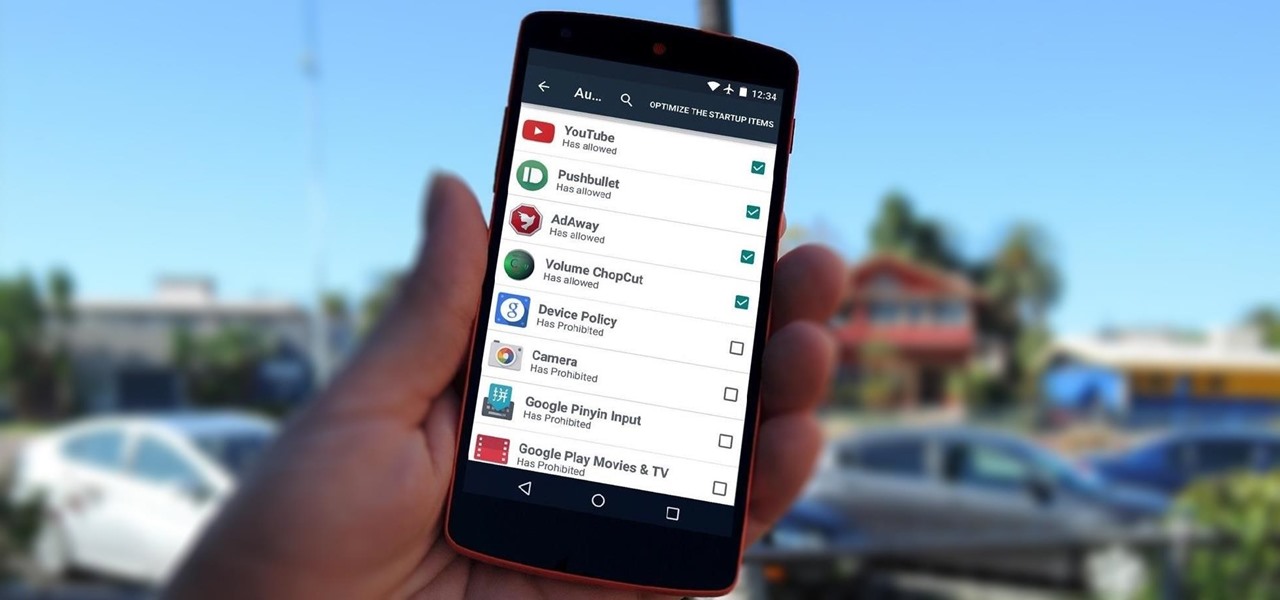
By default, any app that requests a certain permission can run automatically as soon as you start your device. Since Android doesn't offer a granular permission control system like iOS, this gets lumped in with all of the other permissions that you have to accept when you're installing an app from the Google Play Store, and you effectively have no choice in the matter.

Before you head to class, work, or sleep, you're probably doing the same thing over and over again—toggling off system settings like Wi-Fi, sound, data, or brightness, depending on the circumstances. Schedules and routines can help increase efficiency, so while you abide to a particular schedule, so should your Android.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

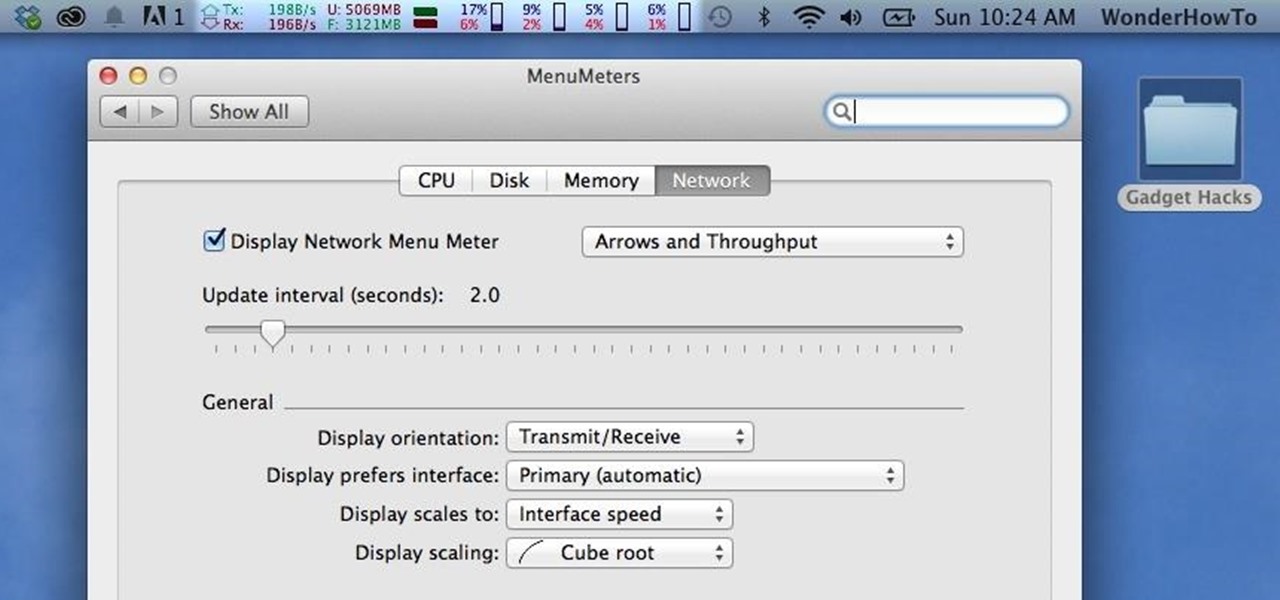
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

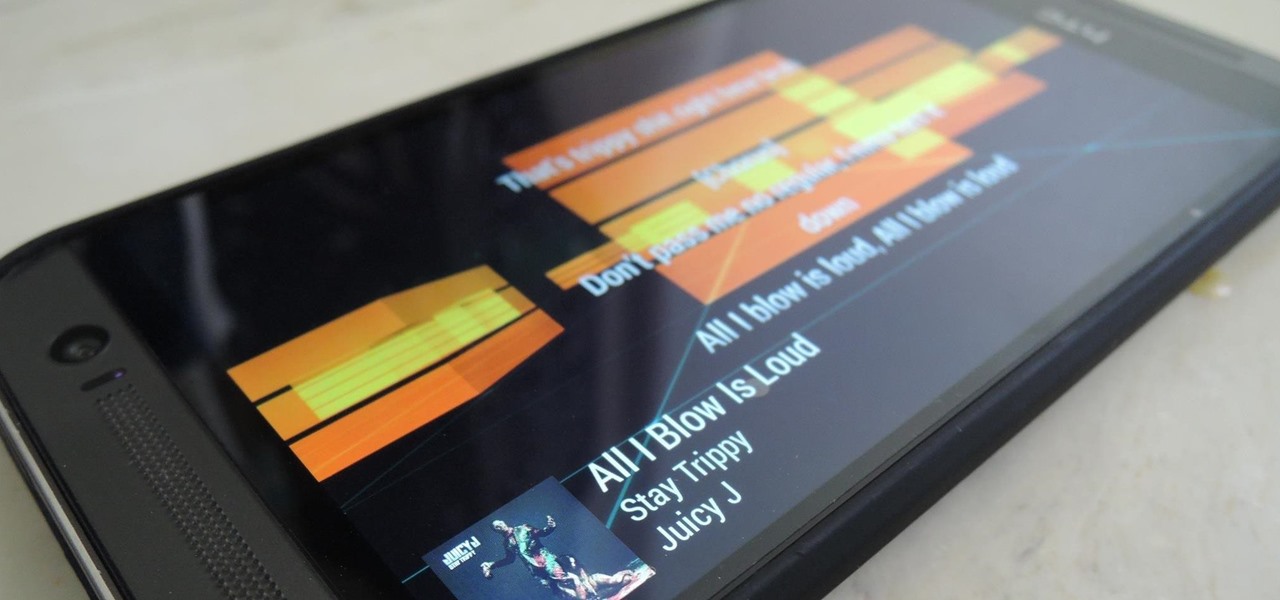
The HTC One has proven to be the industry standard in mobile audio performance. With BoomSound and Harman/Kardon technology backing its front-facing speakers, there is no doubt that every other flagship out there pales in comparison. Despite this, HTC didn't include a decent equalizer on the One. The M7 had Beats but the M8 doesn't have anything.

Sense 6 came with a ton of new features for the HTC One, but for some reason, HTC decided to keep one of them hidden to all non-Harman Kardon editions.

Thanks to a recent back-end update to Google's Search app, every KitKat-running device can use "Okay, Google" from within any app—even the lock screen. However, the default settings for the OnePlus One's mic leave it unable to detect your voice unless you have it right up to your face. That isn't a good look for anyone, but thankfully there is an easy fix to get this working correctly.

Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream.

Greetings, my friend. Welcome to Null Byte. I am Dr. Crashdump. Linux will be talked about a lot in Null Byte. It's used in most tutorials on this site, actually. You should learn how to use Linux as soon as possible, but where do you start? No worries. Let's figure that out.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Puff and Po and the Empress's Treasures, is an inspiring indie game that stays fateful to the arcade single screen plat-former style and game-play.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

The iOS 7 release brought with it many new aesthetic upgrades, from new flat, vibrant icons to a sleeker text messaging interface. Another small, yet noticeable, difference is the minimal and clean lock screen, which removed the overbearing "Slide to Unlock" background bar in lieu of just the text.

There are thousands of fonts you can download online. Some are free, some you have to pay for, but they all have something in common—if you can get them, so can everyone else. If you want a truly unique font that no one else is using, you have to make your own, and what's more unique than your own handwriting?

There have been hundreds of reports of users hearing a grinding noise when they place a disc into their brand new Xbox One video game consoles. To prove it, here is an awesomely sad compilation of Xbox One owners having the issue.

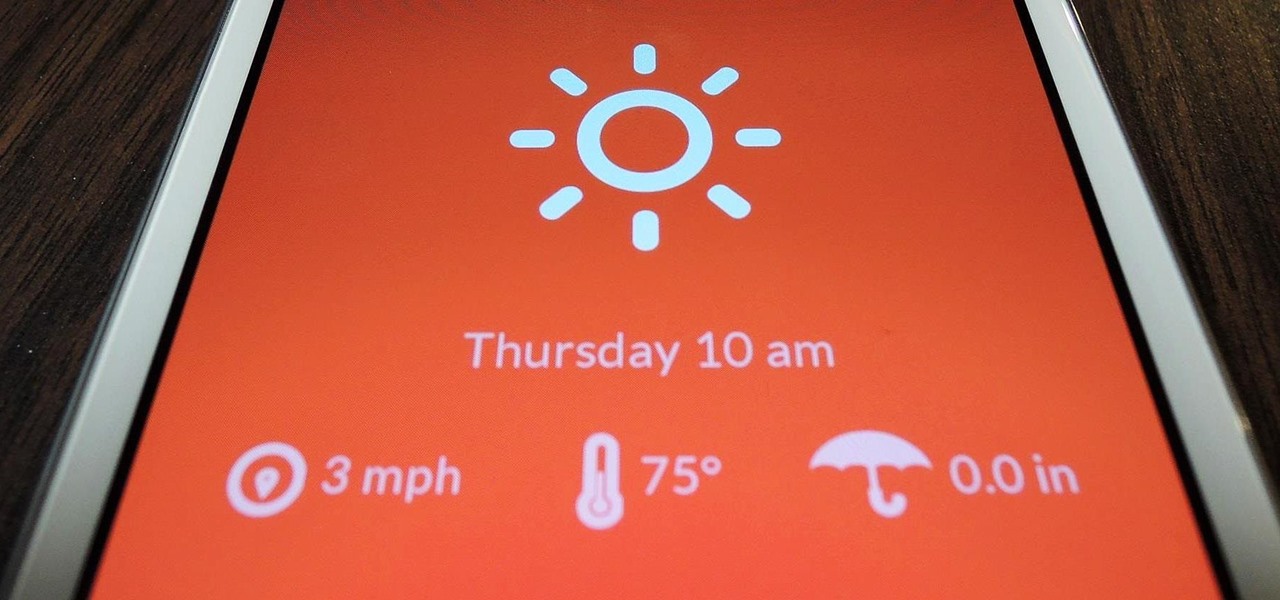
70 degrees, 8 mph winds, and sunny clear skies. That's the current forecast here in Los Angeles and I can't really complain. However, if you don't live in Southern California, checking the weather may be the difference between getting stuck in a snowstorm or remembering to bring an umbrella.

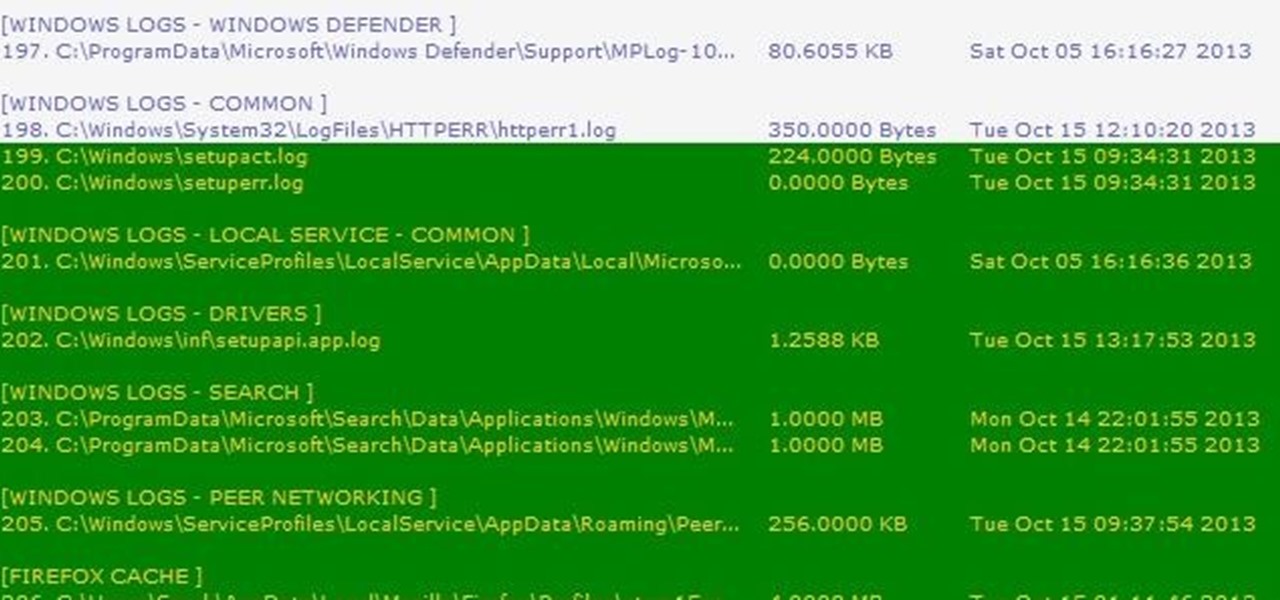
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

Uploading certain pictures to Instagram can be problematic, especially when the dimensions of your picture exceed the dimensions of the square crop that's forced upon you. Why should I be forced to hack up my awesome fisheye picture inside of a lame square? I get the whole square thing, and I love it, but there's just some times when you can't be bound by the rules.

I've been a Sprint customer for a long time. Normally, Sprint (flagship) phones come with some useful apps, such as Sprint TV, Sprint Zone (for payments, updating PRLs, and account information), and NBA Game Time. In other words, relatively free of bloat.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.

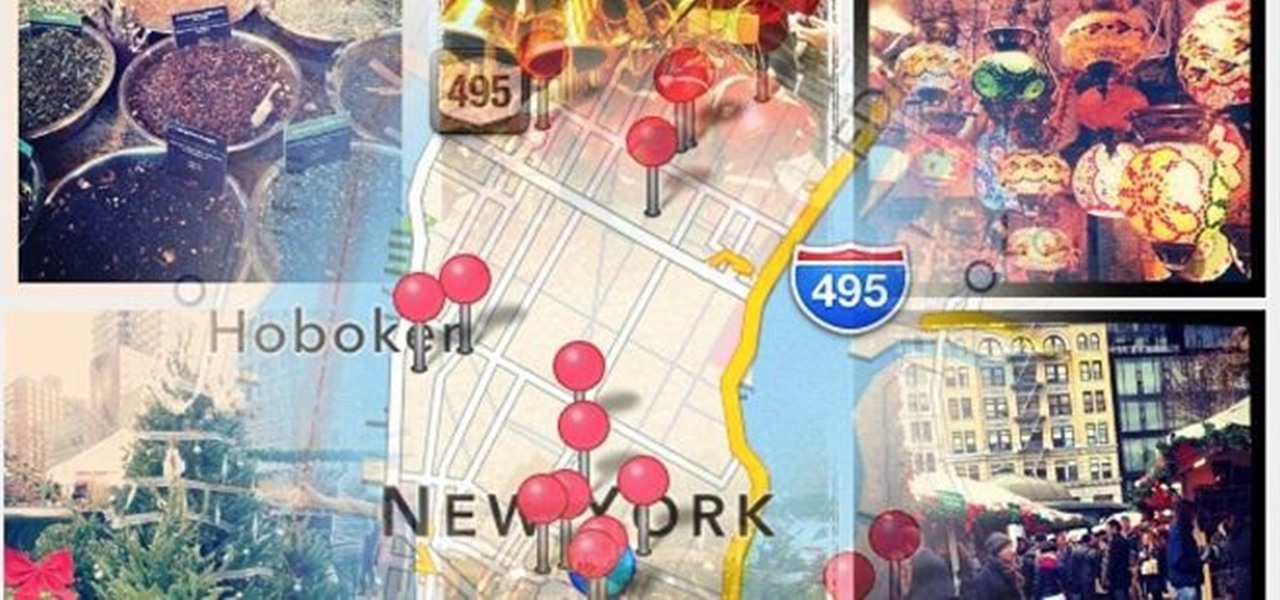
The only thing worse than not having any plans is not even knowing where to begin making them. Sure, you can check Yelp or one of countless other review sites to find a great spot, but there's no way of knowing what the vibe is like before you get there. Is it crowded? Are people having fun, or does it look pretty lame?

Being lost sucks. There really is nothing worse than going to a huge event with a bunch of friends or family and then getting separated. Instead of partying with the bros, you get stuck next to this lame couple who keeps seriously making out every ten seconds. SMH.

I love my Mac to pieces, but there have been times, so many times, that I wanted to silence that classic Apple start-up chime. I mean, the only thing the sound does is notify everyone around you that you have a Mac, and that you have turned said Mac on, right? Well it's not so vain.

As a multitasker, I've embraced the hustle and bustle that has filled my life. I'm constantly doing several things at a time, while looking for shortcuts to finish all of these things quicker than before. I brush my teeth with my cell phone in hand and drive to work with breakfast in mouth—I spare no time. Well, now there's an application for the Mac users among us that can help take some of the stress out of doing a thousand things at once.

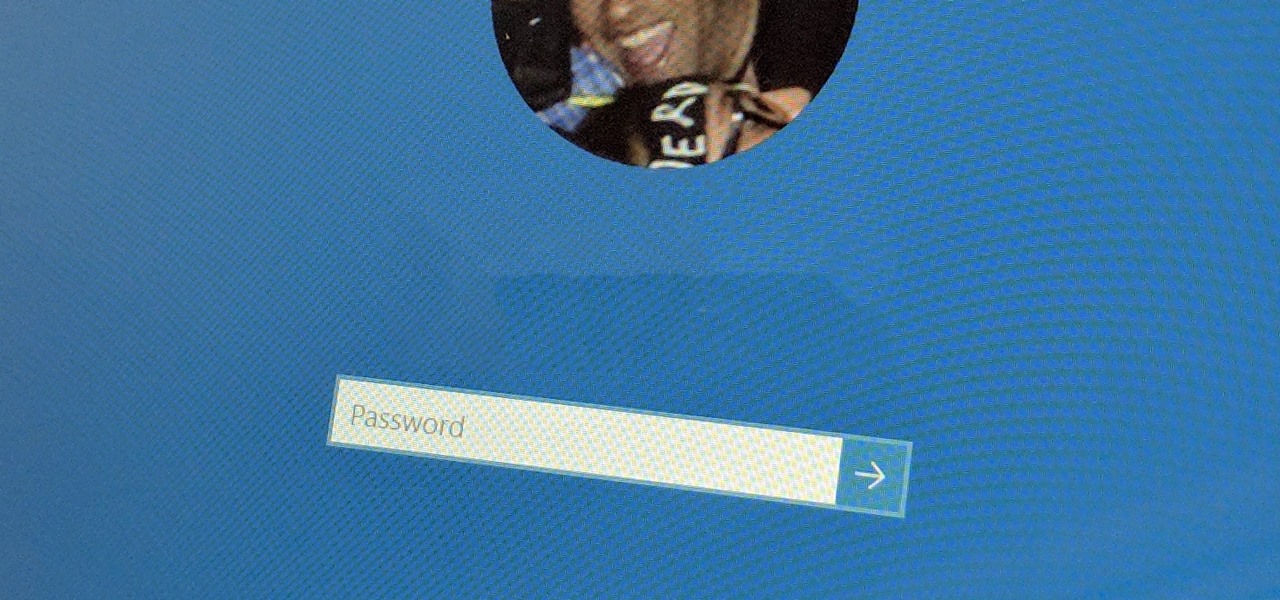
It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

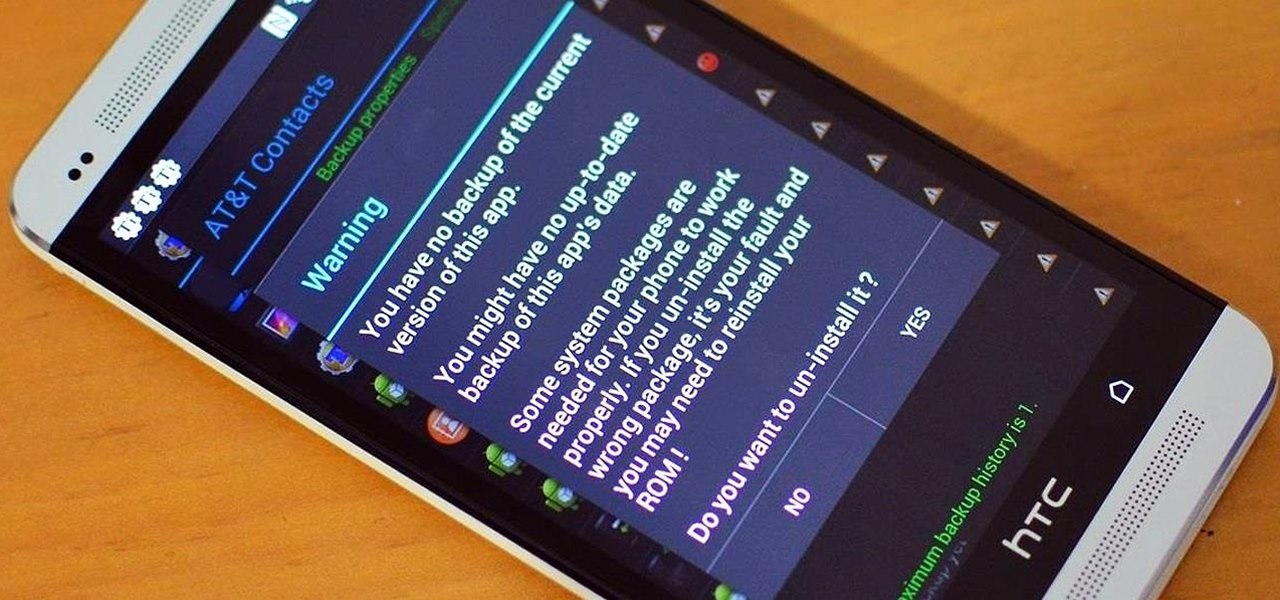
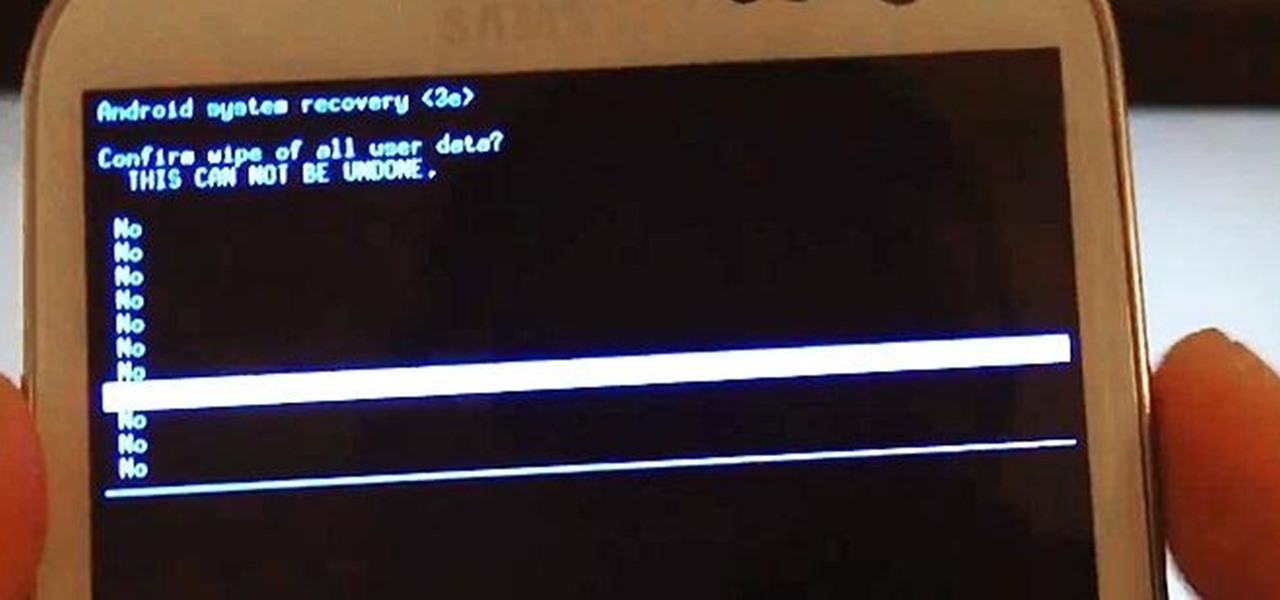
Erasing everything off of your phone and starting anew is a pretty drastic step to take for a little glitch. For most people, system restoring is a last resort option, but there are a few reasons to want or need to restore your device to factory settings.

While the PlayStation and Xbox models may rule the current world of gaming, there are still those who love to keep it old school. The grittiness, toughness and nostalgia that is laced throughout old gaming consoles appeals to many people. Every time I play Donkey Kong 64 (with the expansion pack of course!), I revert back to the days of Sunday morning cartoons and only worrying about homework.

One of the more innovative features about the new Windows 8 operating system is the ability to unlock the screen via a picture password. This new feature allows the user to select any photo they would like and use taps, circles or straight lines to unlock the device. The video below shows the picture unlock in action.

You can take some absolutely gorgeous photos using the natural reflection that appears in people's and animals' eyes. With the right angle and lighting, you can even see a detailed picture of what the subject was looking at when the photo was taken. Photo by Martin Cathrae

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

If you are like me and you have a old iPhone and you don't want to buy a new one, you can fake your ios version by fallowing this tutorial. Just to be safe i am not responsible for what you do with this or if you mess up and wreck your phone. Plus ios and iPhone all belong to their rightful owners.