Sure the Nintendo DS Lite can play games, but it makes a great travel alarm clock, too. Watch this Nintendo DS tutorial video to learn how to use your DS Lite as an alarm clock instead of just a game system.
Check out this Blender video tutorial all you wannabe digital animators out there to see how to use paths and dupliframes in your 3D modeling.

Installing a home security system can be expensive, but it doesn't have to be. This how to video shows you some easy practices that keep your home well protected. All you need is a few inexpensive items such as flood lights, signs, and light timers.

Your home security systems may not work for you if you don't turn it on. To top it off some of your bad habits can invite thieves in to your home. This how to video reviews some common sense steps to protect your home from burglars.

The throttle body forms part of the air intake system that controls the amount of air flowing into the car's engine. Watch this how to video to learn how to remove the "air pedal" or throttle body from your vehicle.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

A walk through on installing a flash player on an Ubuntu system. Also, a tutorial on downloading and installing the Opera browsing software.

An instructional video on how to repair a leaky bladder on Ozone new Instinct Sport, which has the one pump system.

The two main types of swings for a horse drawn carriage are the solid bar swivelling on a central pin and the flexible rope type that moves on a system of pulleys.

This video addresses the consonants of Hindi from velars to retroflexes, including the writing system (devanagari script). It is concluded by part 4 (b). Please watch the videos on Hindi phonetics before this part.

The move order 1.d4 d5 2.e3 Nf6 3.Bd3 e6 4.Nd2 c5 5.c3 Bd6 is very annoying because it discourages the key move f2-f4. Instead, White should play a different opening. He can enter a reversed Meran Defense with 6.dxc5, or a Colle System with 6.Ngf3.

This video demonstrate a system against the King's Indian Attack. Enjoy! And don't get too good, because if we ever play, I don't want to lose.

Yoga butterfly breathing is a great way to start you day or any work out. It gets you well oxygenated, helps you eliminate toxins, gets your cardiovascular system revved up and bumps up your metabolism. Watch this how to video and start using this butterfly breathing technique.

Olympic Gold Medal winner Sheila Taormina demonstrates the high elbow catch (HEC) swim stroke using the Halo Swim Training system and as explained by Craig Askins. The high elbow catch is considered a key component in the success of todays best swimmers.

How to use Crystalxp.net to get new skins for Microsoft Windows XP and change the appearance of the operating system.

Why does a DJ use a monitor system? To avoid secondhand sound from the speakers that the crowd listens to. Uses a mixer and amplifiers connected to smaller speakers.

R4DS is a cartridge-based system that fits right into SLOT-! on a NIntedo DS. Here's how to install R4DS and be able to support ROMS, multimedia files, and homebrew games on your Nintendo DS.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

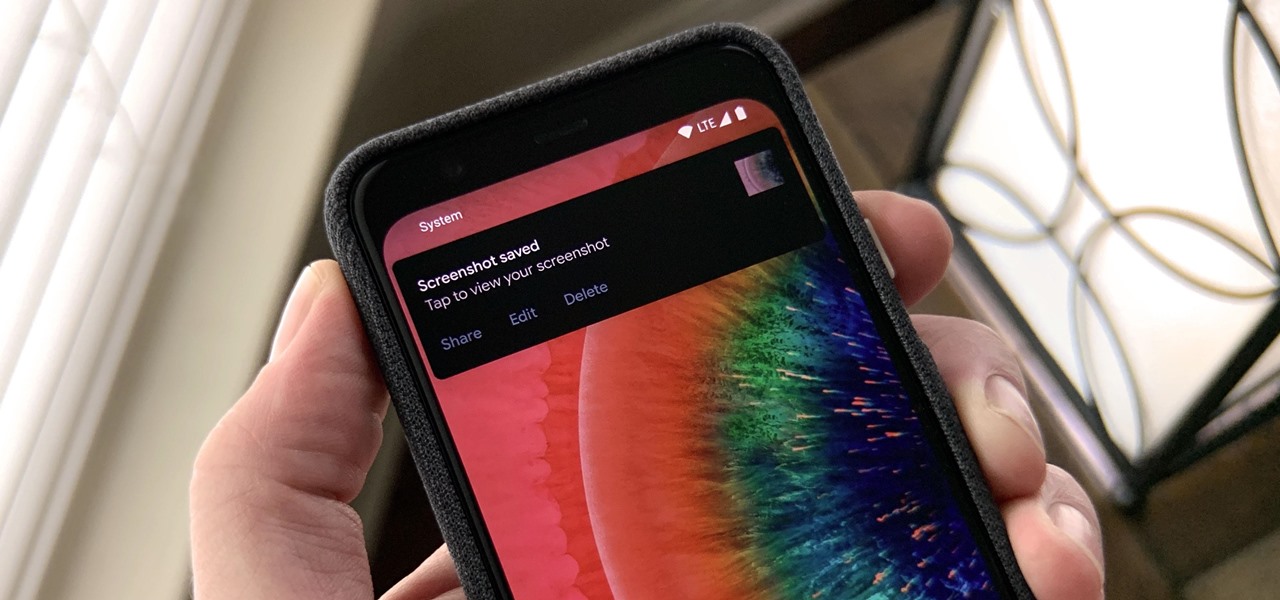
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Until Star Wars-style 3D hologram projection technology becomes commonplace, the near future of certain kinds of remote work is in robotics. Now, a new dynamic is using augmented reality to give this kind of telepresence a kind of superpower.

Augmented reality gaming startup Tilt Five is ready to reinvent old school Dungeons & Dragons-style games for the modern age with its augmented reality headset and tabletop game system.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

We've all been there — using Google Maps for navigation and waiting for the app to find our location. As we drive around, we keep hoping it will get a lock in time to make the next turn. Well in the US, we finally have a solution to this problem, and it's the OnePlus 7 Pro.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With every new Android update, hidden features are lurking under the surface. Google hides these options to prevent unnecessary tinkering by average users, leaving them in place for power users to discover. These secrets range from silly to really useful, with the latter opening up new ways to manage your phone.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

The price tag for the Microsoft HoloLens might be out of range for the average consumer's budget, but for enterprises, like BAE Systems, adopting the AR headset is yielding a return on the investment. And for those with even slimmer wallets, Best Buy just made the Lenovo Mirage, part of the Star Wars: Jedi Challenges package, more affordable.

If it had come out just a week earlier, around April 1, no one would have believed it. But it's true, Leap Motion has developed its own prototype augmented reality headset, and it looks pretty wild.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

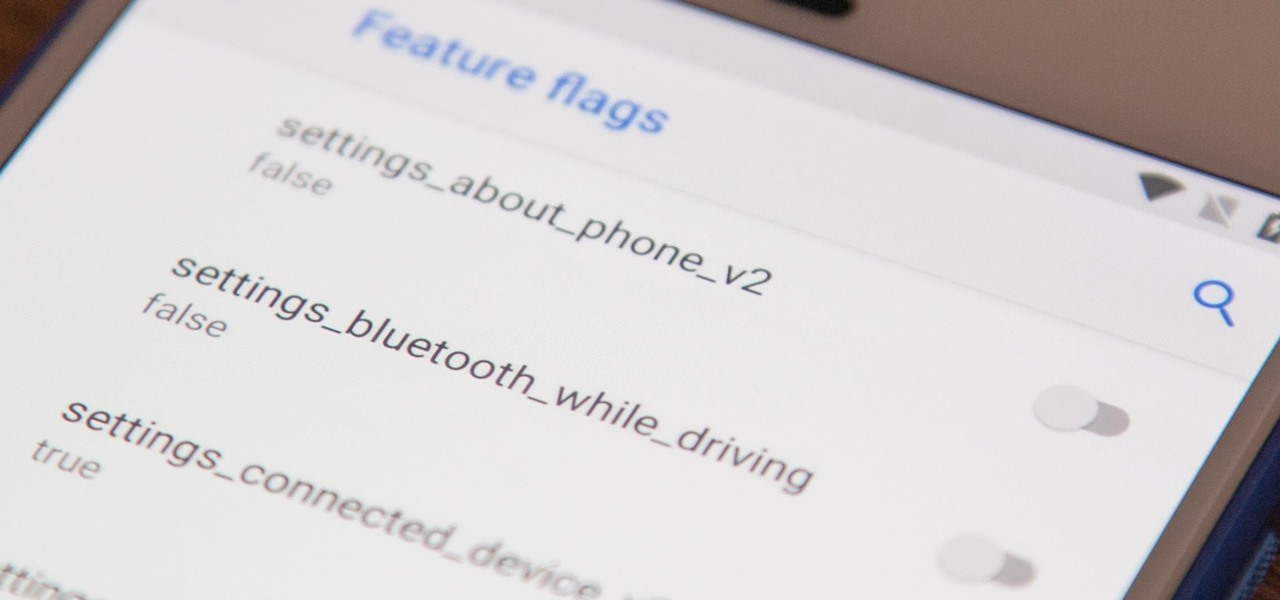
There's a new secret settings menu hiding in Android 9.0 Pie that offers Chrome-style "flags" to the overall operating system. Since it's currently the first Developer Preview and Public Beta versions, it's possible that this menu could disappear entirely when the stable version finally gets released, but it could also persist in its current hidden state where you have to unlock it.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.