Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?
If you're an Android fan, you probably made your choice in mobile operating systems based on the insane level of customization options that Google's software offers. Don't like your home screen app? Simply replace it. Not a fan of a particular app's sharing system? No big deal, just share through a third-party app.

In general, we never really put much thought into fonts, but they comprise a huge portion of our online experience. A whimsical mood can easily be set by using something like Segoe Script, but switch it up to Sentinel and you've got a more sophisticated feel all of a sudden.

Maps is great for making sure you always get to your destination, until you miss that critical turn because you couldn't hear the turn-by-turn directions.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.
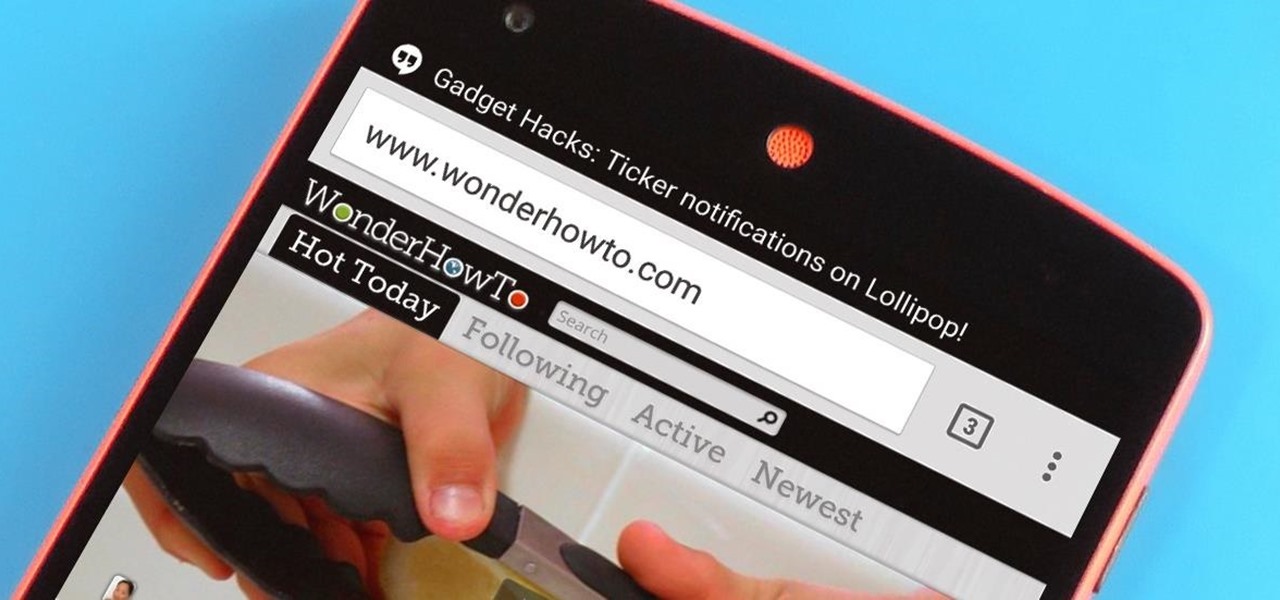
With Android 5.0, Google introduced a new "Heads Up" notification system for incoming calls and messages. While the new incoming call interface seems to be a rousing success, the rest of the Heads Up system has been met with much less enthusiasm from users.

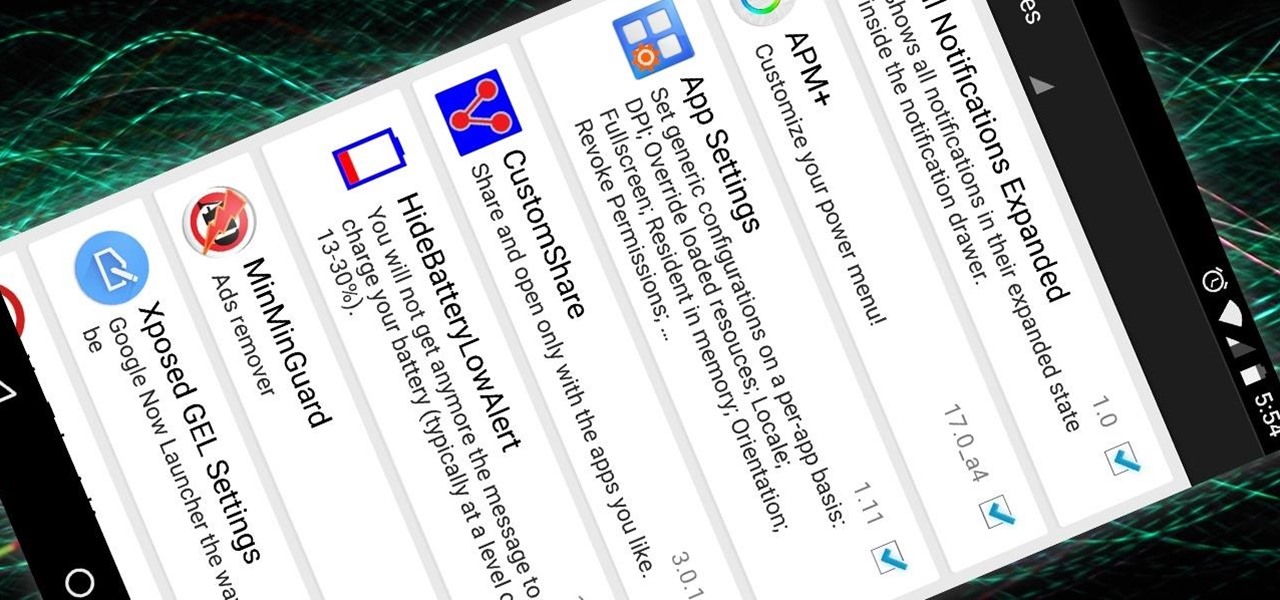
Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

Most custom ROMs are built from the freely-available source code of AOSP, so they share a lot of common ground with stock Android. The difference, though, is the fact that Google adds many minor tweaks and finishing touches to AOSP while creating the version of Android that ultimately comes pre-installed on Nexus devices.

During a power outage at my apartment this year, I watched movies on my MacBook Pro instead of on my television. While I had no complaints about the screen size, I did have an issue with how low the audio coming from my speakers was. External speakers would help, but I don't want to buy them or lug them around every time I want to watch a movie.

Almost all modern Android devices have a gesture that will take you directly to Google Now. For most phones and tablets, it's a simple swipe up from the home button. With a Samsung or an older Android device, it's only a matter pressing and holding the home button.

The volume is maxed out, but that doesn't stop me from hitting the volume key on my Nexus 7 in hopes that it will magically get louder. This happens to me everyday as I watch videos or play music. The simple fact is that a Nexus 7 tablet just doesn't get very loud. At least, not loud enough for me.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Practically every kid in the '80s would rush home after school to put in some time on the first-gen Nintendo before their parents got home. Games like Super Mario Bros. and Super Smash Bros. were synonymous with fun times, and to this day, call up a wave of nostalgia amongst Generation-Xers.

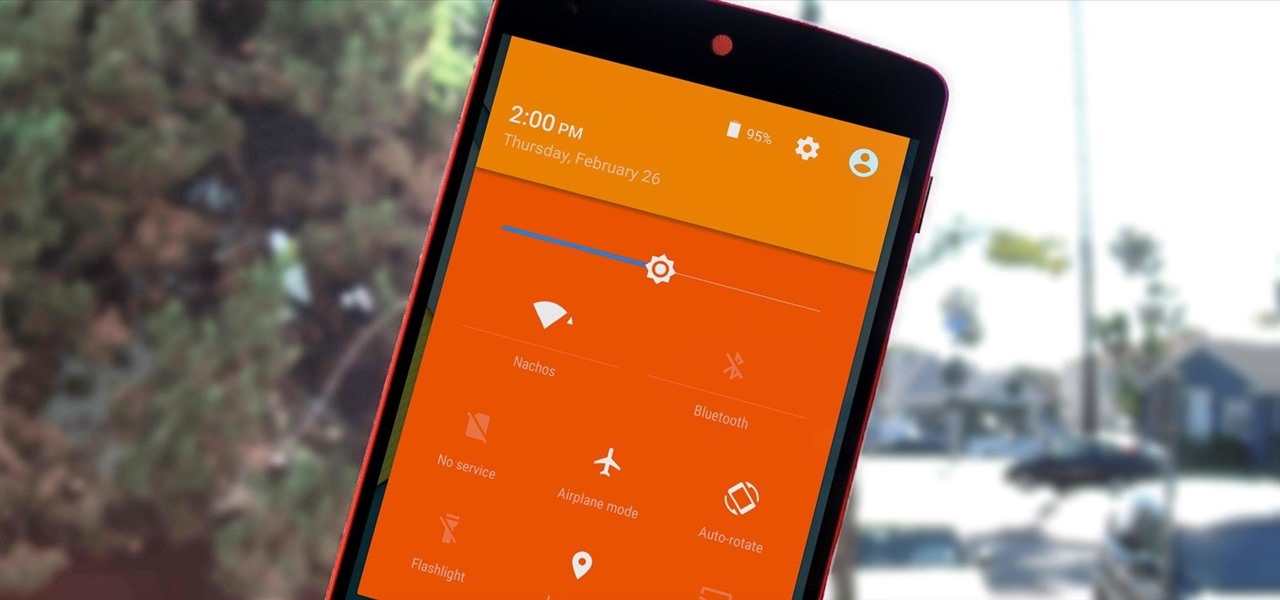
We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Since the release of the Galaxy S5 back in April, the process of converting older models, like the Galaxy S4, to replicate the look and feel of the newest S-family member was inevitable. Galaxy users didn't want to be left out, and for good reason. The revamped interface of the S5 introduced a new color palette that was a definite improvement from the flat boring colors on older models.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

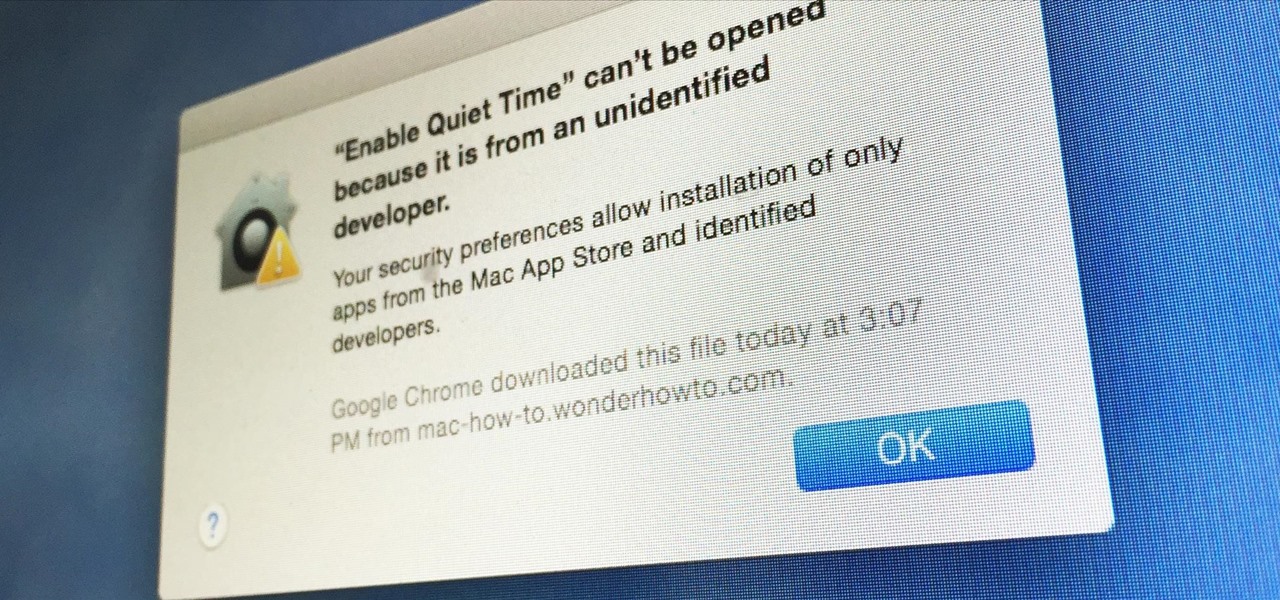
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

With all of the top-notch specs that the Galaxy S5 sports, the only minor quibble users have had with its hardware is the speaker situation. A front-facing earpiece is used for phone calls, but all other media is restricted to a single rear-firing speaker.

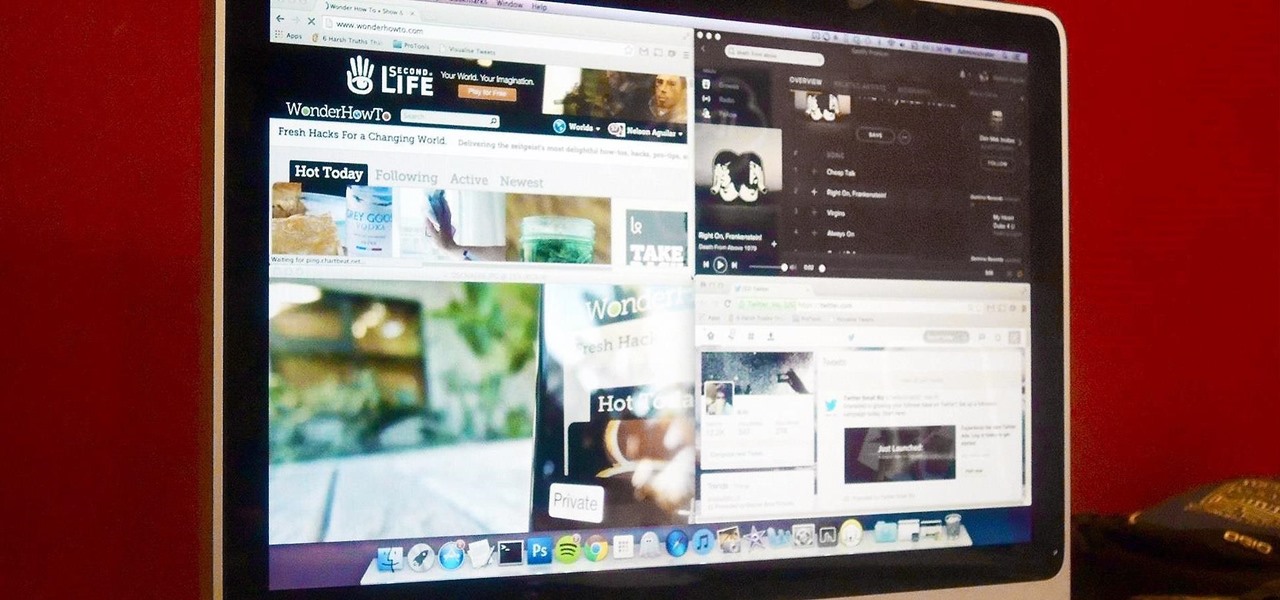
Mac OS X has finally added a way to use two apps side by side in full screen mode, à la Microsoft's Windows Snap. But since it's only available in 10.11 El Capitan right now, those of us with older systems will have to wait until the El Capitan Public Preview or final build is released later this year.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

Though they share the same name, the HTC One and OnePlus One have completely different sound quality. HTC had put a lot of time and effort into fine-tuning their BoomSound technology, while OnePlus is still fairly new to the game, with brand recognition being a much greater objective than awesome speakers.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Google's upcoming Android release hasn't even received a name or version number yet, but the third-party development community is already having its way with the firmware.

Yes, I know. Nexus owners aren't exactly the biggest Apple fans out there. That "Pure Android" experience was one of the main reasons we bought our Nexus devices. But give the other side some credit—the iPhone's operating system has come along way, and is still the champ when it comes to aesthetic design (at least until Material Design dethrones it this fall).

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

If you thought iOS 7 was a drastic change from previous iterations, iOS 8 will certainly continue to rock the boat. From a revamped Control Center to enhanced "Continuity" to ephemeral messaging, Apple's newest mobile operating system will have many of you relearning the "basics."

There's a lot you can access from the Notification tray on your Galaxy S4. Quick settings toggles, brightness controls, and of course, notifications. However, despite the power this simple pull-down gives you, you're still left with a boring, black background for the shade.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

CyanogenMod is one of, if not the most popular, third-party operating system for Android devices. It's so popular in fact, that it is the standard, out-of-the-box operating system on the recently released OnePlus One. CM is a lightweight ROM built on top of AOSP (Android Open Source Project), which is the base for all Android builds.

There are two types of bricks ("brick" as in "bricking your phone")—soft and hard. Soft bricks are recoverable—something has probably gone wrong with some critical system partition, causing a bootloop or inability to boot in some way. Fine. Re-flashing everything should fix that instantly. Hard bricks are not recoverable—if you manage to hard-brick your Nexus, you are in trouble.

When we look back on it, 2014 may be remembered as the Summer of Android Wear. With two new flagship smartwatches due out soon, Google's been readying its mobile OS for the wearables sector.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

HTC pulled out all the stops when designing the HTC One M8. From it's sleek body, to it's incredible sound quality, this thing just oozes sophistication. While all of these add-ons are great, they can be incredibly taxing on the CPU, in turn causing some serious lag.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

Changing an app's name on your home screen is not something you can do on stock Android or TouchWiz, but it should be. If you think of it merely from a customization angle, sure, it's not a big deal, but having the ability to alter an app shortcut's name can do wonders for cleanliness and being able to distinguish from similar icons.

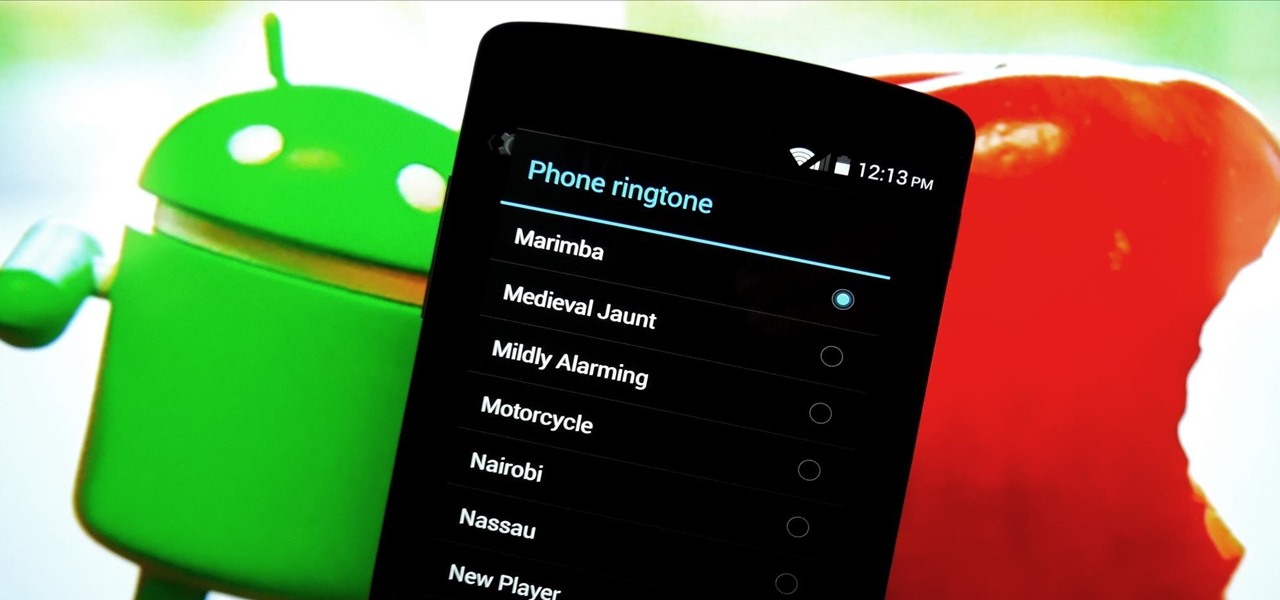
As Nexus owners, we love our device's operating system, and it's probably the reason we went for a pure Google experience in the first place. But that doesn't mean there's not room for improvement in Android, especially when the OS has so many freely available softMods to tinker with.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.