It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.
Android 9.0 Pie has finally arrived for Galaxy devices like the Note 9, S9, and S8, in the form of One UI. Of course, we've had a good idea as to what Samsung had up its sleeve for some time, thanks in large part to beta versions of the firmware that leaked out well before its official debut. Nevertheless, it's still exciting to experience the new features the software has to offer — with all its kinks ironed out.

With HoloLens and its enterprise-focused software offerings, Microsoft continues to make an impression on companies looking to adopt augmented reality, with Toyota Motor Corporation among the latest.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

This year marks the first for Apple to exclude the Home button from any new iPhones. If you're going from a Home-button iPhone to a new XS, XS Max, or XR, you might be a bit stumped when trying to perform basic tasks, such as activating Siri. While you can't hold down the Home button any longer, there's a new method that's just as quick.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

Google's ARCore team is staying busy, as evidenced by yet another update of its augmented reality toolkit.

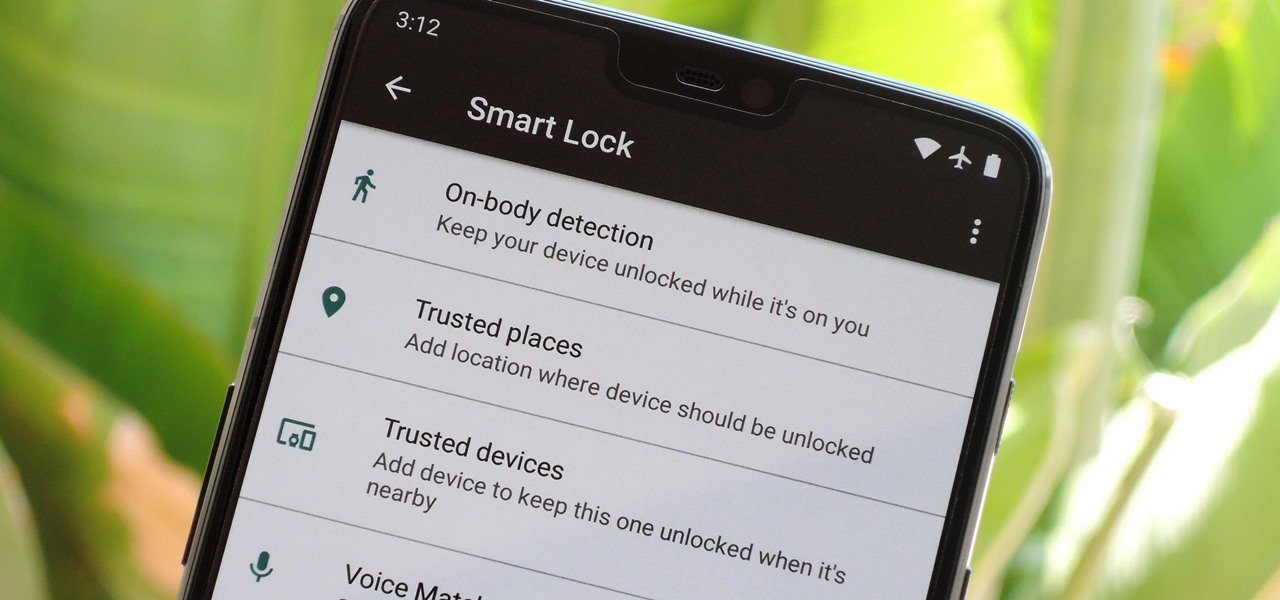
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.

A newly-filed patent application from Disney Enterprises, Inc. teases more augmented reality lightsaber duels, either for at-home gaming or for the media behemoth's forthcoming Star Wars theme park.

Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

Part of the Star Wars: Jedi Challenges experience that was once exclusive to users of Lenovo's Mirage AR headset is now available to anyone with an ARKit-compatible iOS device.

The Android version of Google Chrome only shows a home button on some devices. Unfortunately, this feature isn't available to all Android phones due to several factors. But thanks to a simple workaround, you can now enable this button and set a home page regardless of what device you have.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

It looks like Google's feud with Amazon won't end anytime soon. A war has been brewing ever since Amazon pulled Chromecast, Apple TV, and other competing devices from their store in 2015, but the latest exchange is a huge blow to people using Amazon Fire tablets and streaming TV sticks.

The Galaxy S9 is a great phone powered by the Android ecosystem. This includes Google's family of apps — many of which overlap with Samsung's in functionality. This can lead to redundant apps that siphon resources from your phone, but fortunately, there's a way to dull some of the noise and disable built-in apps.

Most Android phones don't even have an Oreo beta yet, but that's not stopping Google from releasing the preview to their next big update. Android Pie is here for developers to test, and with it, one of the more controversial additions in the Android world today — the notch.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.

Eventually, even the most private company has to file its patents and unveil its tightly-held secrets, and Magic Leap is no exception.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

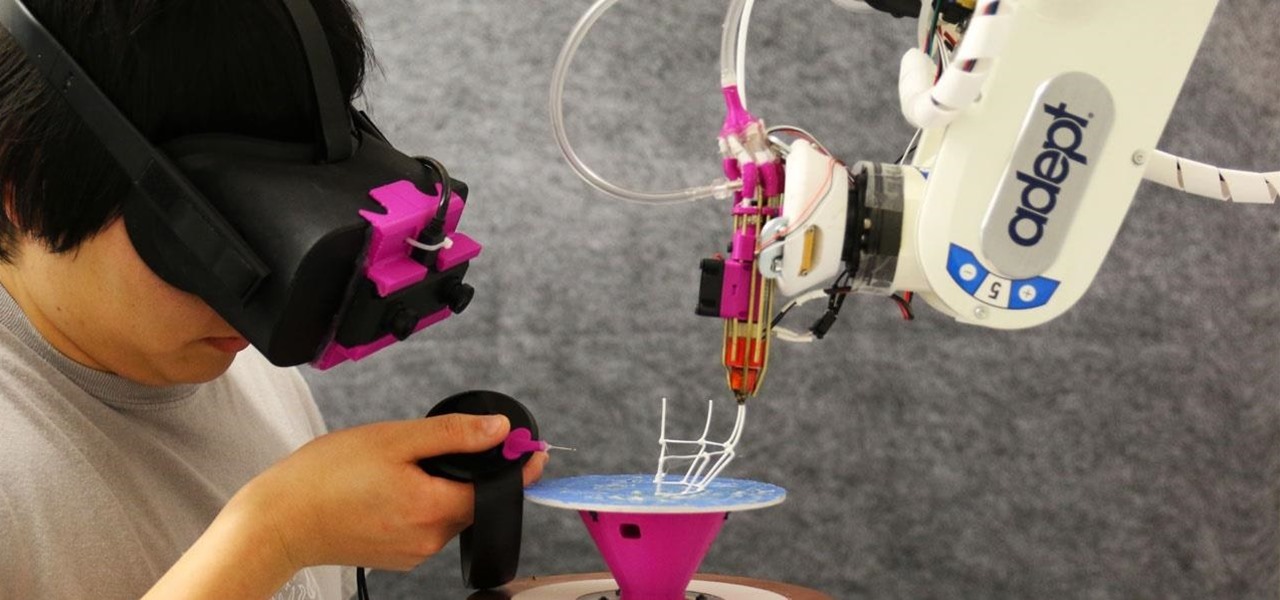
We've seen a number of unique mashups of augmented reality with other bleeding edge technologies, but somehow it took until 2018 for someone to come up with a now obvious complement to AR: 3D printing.

Among the revelations uncovered during the December unveiling of the Magic Leap One: Creator Edition was the fact that the Lightwear augmented reality headset would be tethered to a wearable computer called the Lightpack.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

Samsung's Galaxy S8 and S8+ are excellent smartphones that wowed critics and consumers alike. So, it's only natural that Samsung's followup, the Galaxy S9 and S9+, would garner significant anticipation. While we don't know everything about these devices quite yet, we do have guesses to some key points of interest, including when the device will be announced and even released.

Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

Google caught a lot of flak for the Pixel 2 XL's POLED display issues, regardless of whether the problems were real or perceived. It's too late to contract another screen manufacturer at this point, but Google is doing the next-best thing: Fixing as many user complaints as possible with software updates.

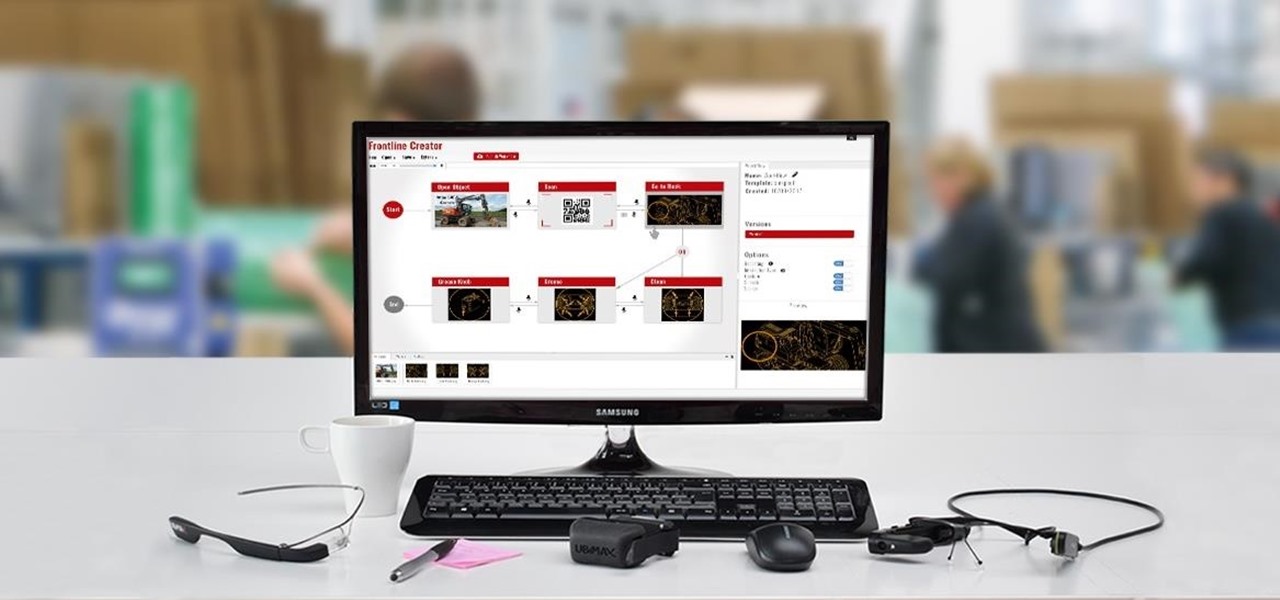
Augmented reality software provider Ubimax unveiled their graphical authoring and publishing tool for their Frontline enterprise platform to attendees at Augmented World Expo Europe today.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Avegant Corporation has begun shipping display development kits based on its light field technology that other companies can use in their augmented and mixed reality devices.