
How To: Build a Man-in-the-Middle Tool with Scapy and Python
Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.


Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

Why did I write this when they're tons of scanning tools available.
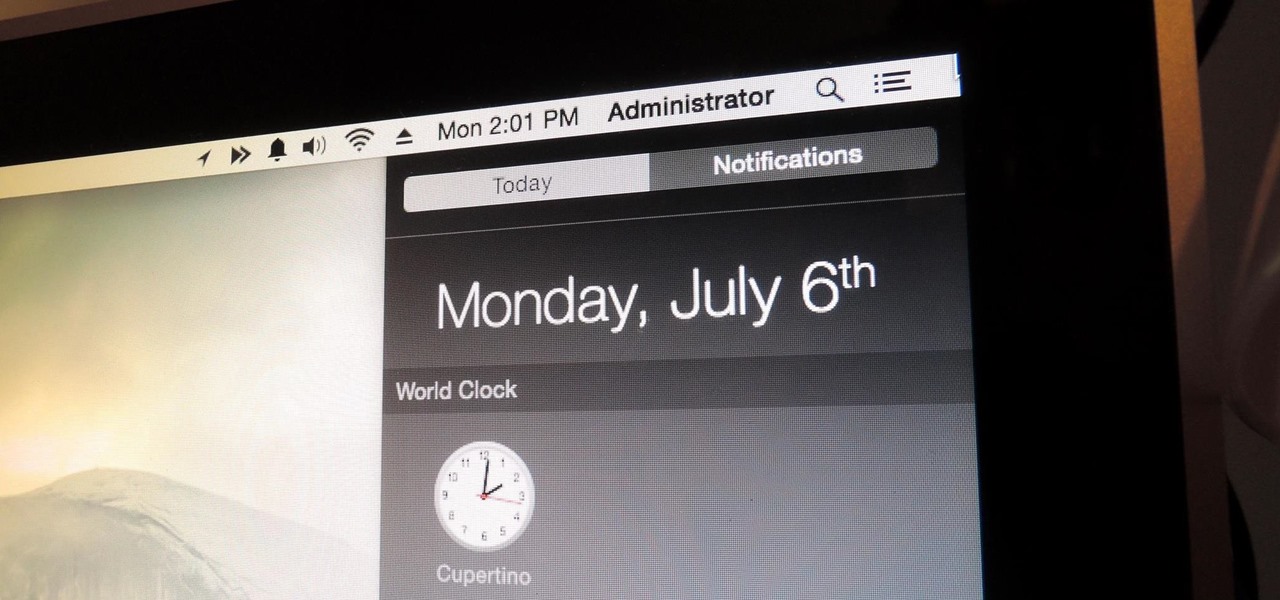
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

As Android owners, we ultimately have to look at our device and ask the difficult question: "Where the hell did all these applications come from?"

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.
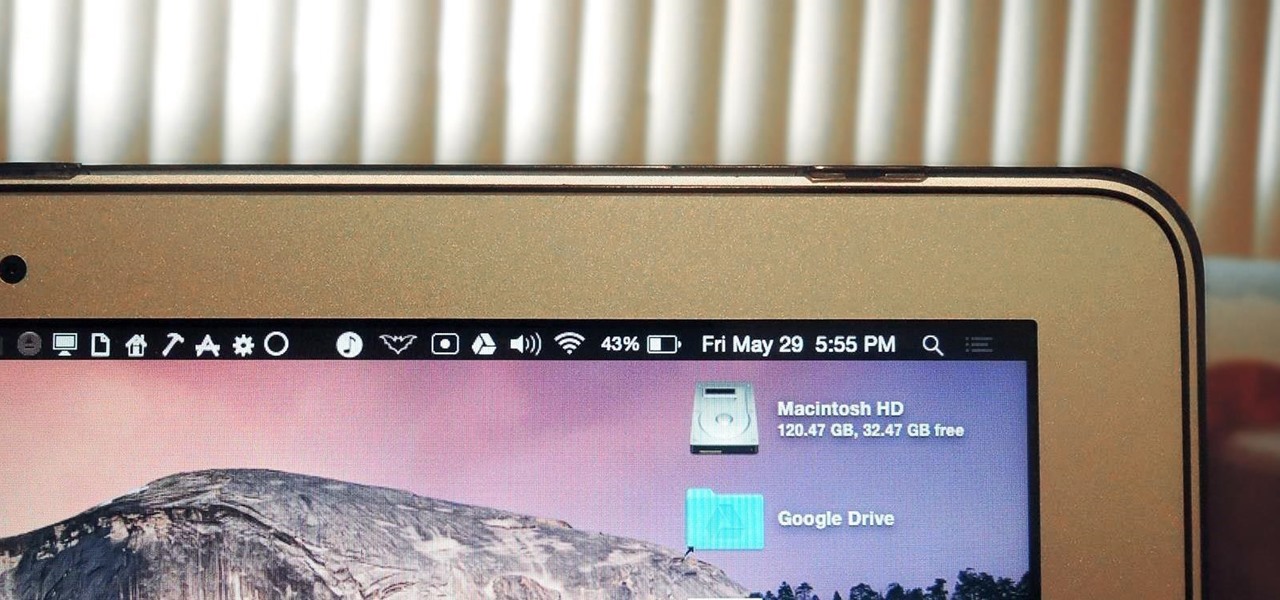
The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

At last, what you all finally waited for! Hi! Fire Crackers,

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.
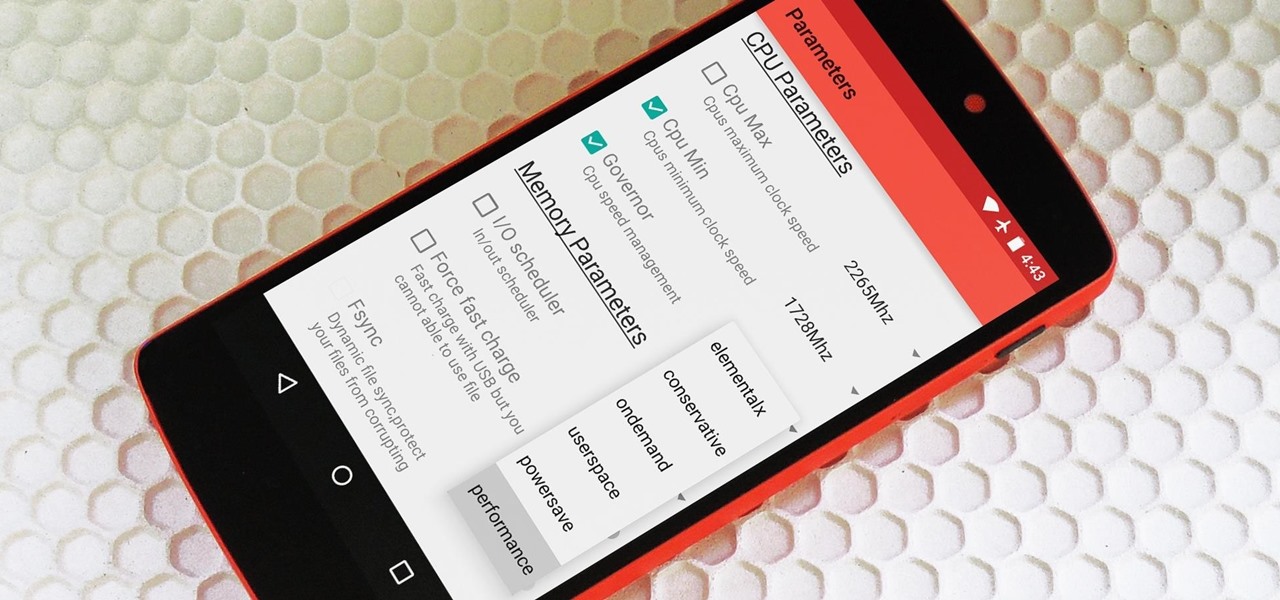
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

iTunes 12 was released alongside Yosemite this year, but it didn't pack quite the punch that the operating system did. Instead, iTunes received a minor facelift, with few new features and somehow lacking the intuitive feel of its predecessor. If you're not thrilled with iTunes 12, we've got a few tips to help you feel like you've got iTunes 11 back on your computer!

It's that time of year again, folks. Each fall, Google debuts a new device alongside the latest iteration of its mobile operating system—but this year marked the release of three new Nexus gadgets.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Getting a new phone is exciting, but having access to its exclusive apps ahead of its release is what we're all about here on Gadget Hacks.
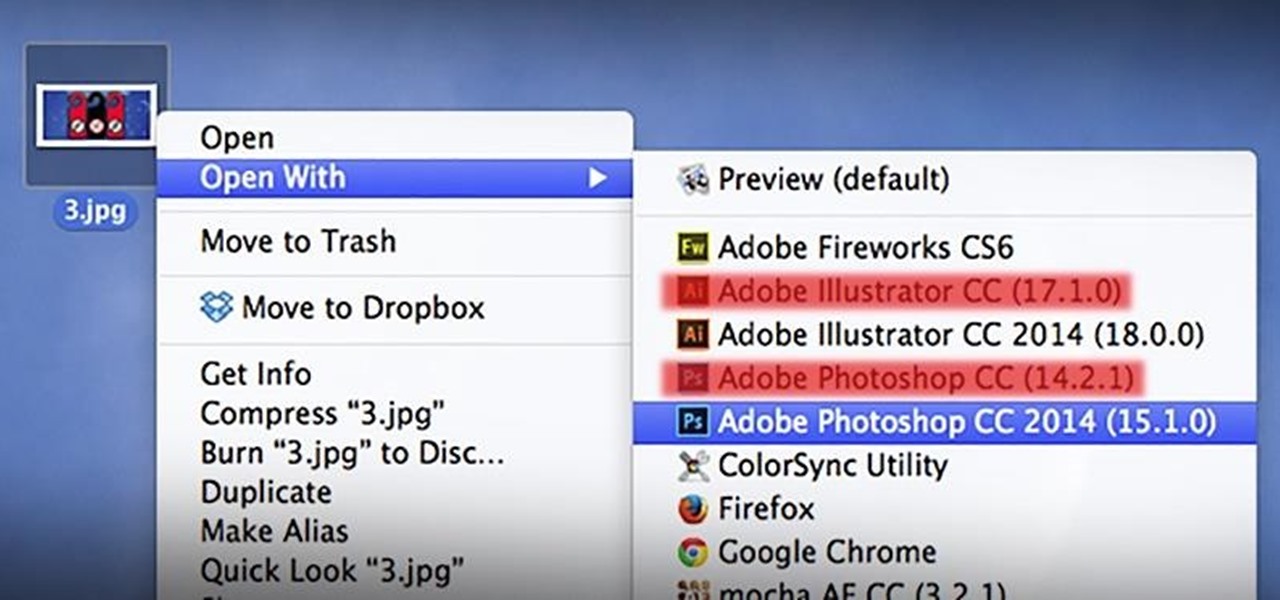
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?
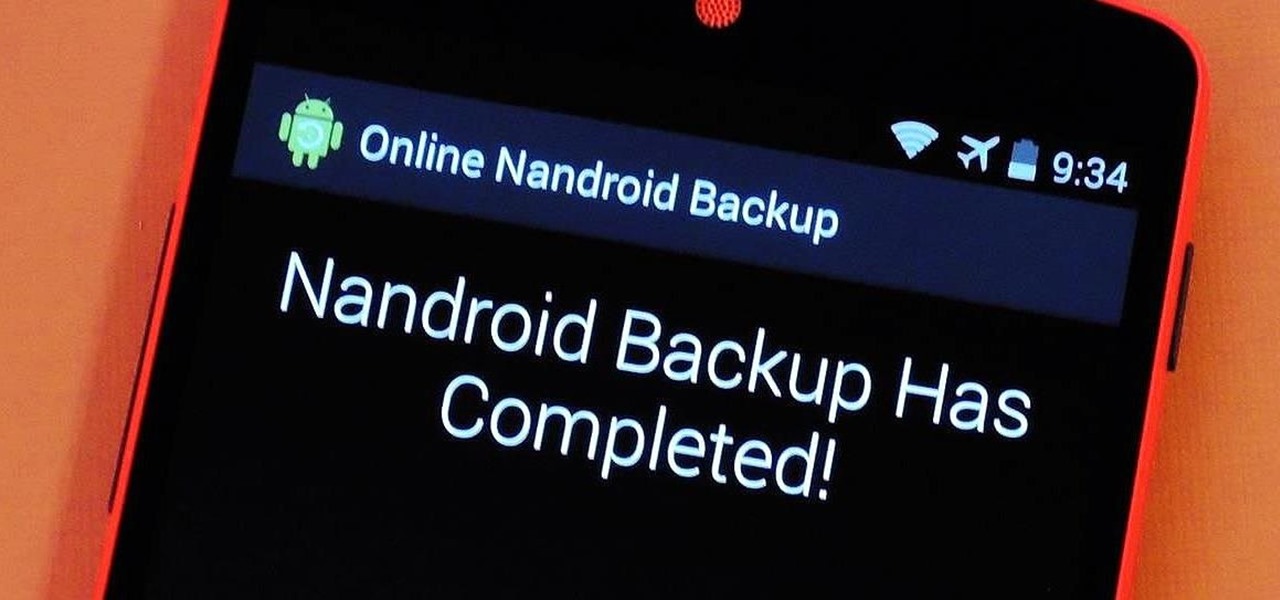
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.
When the Samsung Galaxy S5 launched a few months ago, I was pretty envious of the new UI elements Samsung included on it, as I'm sure you were. The flatter interface provided for a more polished and less cartoony feel, bringing the device more in line with Google's design elements.
It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

Multitasking has always been one of Android's strengths relative to other mobile operating systems. As the first cell phone OS with "true" multitasking, Android's been ahead of the game in this department for quite some time.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

I dabble in video editing, and when working on even the shortest of motion graphics clips, the exported files take up quite a bit of space. For all of you heavy Mac users out there, I'm sure you know my pain.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

If you're one of the lucky people who received the gift of terrible eyesight from your parents at a young age, chances are you ate an awful lot of carrots growing up. Though carrots are one of the top vision-boosting foods, they don't offer fast results.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Flashing ROMs can be a tricky process, and sometimes you can end up leaving yourself without a ROM at all, often referred to as a soft brick. If you accidentally wiped your internal memory before a flash or forgot to download the ROM before wiping your system partition, don't worry, there is always a way to get your phone back up and running.
In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.