While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.
I've struggled for a long time trying to set up a virtual network between my KVM virtual machines. I tried several forums and tutorials on the web, but still on my system it just wouldn't work. I eventually got it owrking, so I've decided to make some notes of my own. Hopefully it will be helpful to you as a reader as well.

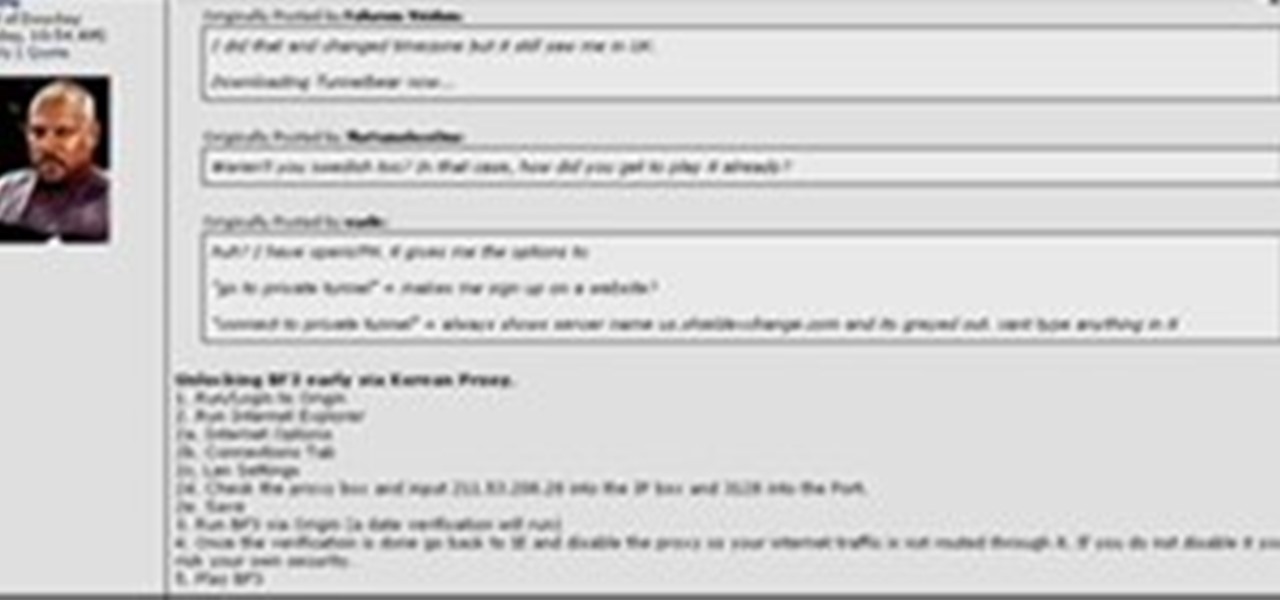
Battlefield 3 officially comes out tomorrow but people have figured out a way to play it today if you have it downloaded (digital pre-install). All you have to do is fake an ip to make it look like your timezone is ready to play. I'll try this when I get home, in the meantime:

As if air travel wasn't filled with enough fees and baggage levies, we've got our prized quiver. Why Renting Boards Sucks

How to set up a Counter-Strike LAN server. You'll need a router. Start a server on Counter-Strike.

What is DansGuardian? Schools, offices and universities often tend to use a software like DansGuardian to prevent people from accessing certain websites - websites like Youtube, Facebook, Myspace, and so on. However, if you ever find yourself in a situation where you need to access a blocked website... it's possible! As a matter of fact, it's quite easy.

make a box to skate on and put 2 holes in the box and cover it with paper thats the same color as the would so its not noticable and under the box have fircracker or a flower bomb and as soon as whom ever lans on the box and gets halfway across set of the fircrackers

There are a lot of fantastic video games out there. Indie Games Ichiban's bread and butter is making sure that you steer clear of the bad ones and embrace the good. But really, the biggest goal here is to help everyone have more fun. To that end, today a game is not recommended, but an event. If you like games—not just video games—but tabletop, board and even hopscotch, then PAX Prime is one of the best events you could possibly go to.

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/