In this video we learn how to say "I love you" in Mandarin and Cantonese Chinese. To say "I love you" in Mandarin, you would say "Wo ai ni". To say this in Cantonese, you would say "ngo ngoi ney". Say each part of these words slowly and practice them to make them sound perfect. There are different dialects you need for each of the types of Chinese, so take your time when researching and practicing. Once you get these down, you will be able to learn more basic phrases and be on the way to lear...

In this tutorial, we learn how to kiss a guy. First, make sure he's into you before you kiss him. Guys will be more willing to kiss someone, but it will be better if you both like each other. Then, make it apparent that you want to kiss him by flirting and having a lot of physical contact with him. If he doesn't try to kiss you, show him with body language that you are into him. Touch his arm or his shoulder and joke around with him to show him you want him. After this, look into his eyes and...

Meeting new people can be hard for some people, especially if they're using a different language, like French. This video will teach you how to say "what is your name" and "my name is" in French. To ask someone their name, a stranger or someone older than you, ask, "Comment vous appelez-vous?". When asking someone your own age, it's "Comment tu t'appelles?" To answer, say "Je m'appelle" + Your Name. Example: "Je m'appelle David."

Don't let the fact that the text in this tutorial is in a different language. Aside from that, everything still remains the same on what you need to do in order to unlock the Bridge Limbo achievement in Just Cause 2. All you need to do is fly an airplane under 30 unique bridges in Panau and you'll have 20 gamer points for you to take home. This may take some time to complete and it can be a bit tricky. So good luck and enjoy!

The iPhone pc suite is an application that allows you to connect easily to your phone. This video will show you how to download this application, reset your phone and then use your audio and video on your iPod. This is a helpful application and is not too difficult to set up. Some of the possible functions include:

This video will show you an interesting trick which you can use to access Facebook or other web pages on a school server or other place where Facebook is normally blocked with the help of Google. You will need to first go to the Google homepage and find the button at the top of the toolbar which says "more" and go to the pull-down option of "even more" options. This will open up a new web page. You should then go down to the "translate a webpage" option on the right hand column of results and...

What's a good way to learn the English language? Scrabble! What's a fun and irresistible word board game the whole family can enjoy? Scrabble! What's the best way to show off your smarts to your friends? Scrabble!

Watch these Japanese language videos and learn to how to ask for permission to do things. You will learn to use the phrase "May I look at this?".

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

With iOS 18, you get better note-taking capabilities in the revamped Notes app, advanced features like conversions and results history in the more powerful Calculator, and interactive Math Notes, a feature in both apps that's a game changer for students and professionals dealing with complex equations. But Apple didn't forget about Reminders, which has become more than a simple to-do-list app.

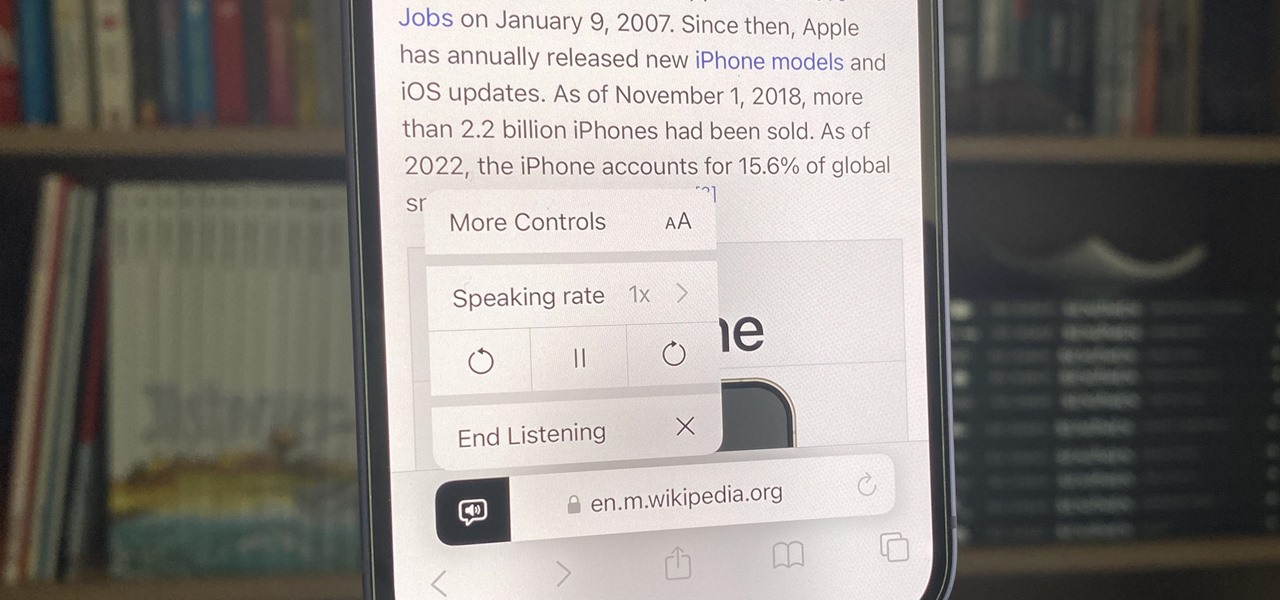
Speech-to-text technology can be seen on your iPhone in various places, from the Dictation tool to Apple's new behind-the-scenes, auto-created transcripts for podcast episodes. Your iPhone also has some pretty impressive text-to-speech capabilities. With them, your iPhone can read webpages, documents, or whatever text is on the screen out loud to you — only some of these tools aren't easy to find.

If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer.

Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help from travel accessories.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Many users have reported Android's speech-to-text feature adding an 'Oh' before each comma. How annoying is that? Fortunately, Reddit user Jay-jay1 has found a solution to this pesky problem. This quick-fix should make your 'Oh' so annoying problem disappear.

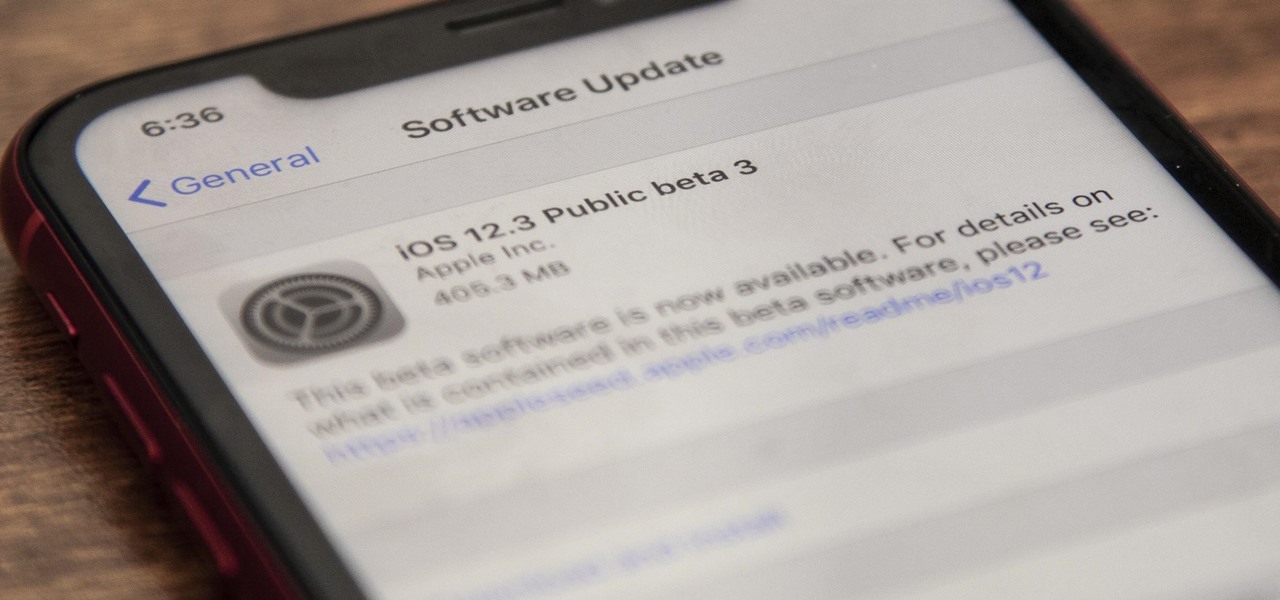
Apple quietly pushed out iOS 12.3 public beta 3 on Tuesday, April 23, just over a day after developer beta 3 was released. Just like with the developer version, there aren't any major features or changes to get excited about, but if you were experiencing any minor bugs with the previous betas on your iPhone, this update could squash some of them.

Developers, get excited. The new iOS 12.3 dev beta 3 just dropped. While this beta doesn't introduce any major features or changes, it means Apple is continuing to address unseen bugs and potential vulnerabilities from the previous versions.

Apple just released the second public beta for iOS 12.3 today, Tuesday, April 9, one day after the release of the iOS 12.3 developer beta 2. This update introduces new Japanese "Date & Time" updates as well as changes to Wallet transactions. Overall, iOS 12.3 includes Apple TV Channels, premium monthly subscriptions with content available directly in the TV app across the Apple ecosystem.

Apple just released iOS 12.3 dev beta 2 today, Monday, April 8, which follows the first iOS 12.3 beta by twelve days. This update introduces new Japanese Date & Time features as well as updates to Wallet transactions. As a whole, iOS 12.3 introduces Apple's previously announced Apple TV Channels, premium monthly subscriptions with content you can watch right in the TV app across Apple products.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my greenhorn hackers!

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

The autocorrect feature in Apple's default iOS keyboard is anything but perfect. Sometimes it can't autocorrect things on your iPhone to want you want, while other times there's a software bug that just flat out gets it wrong. These autocorrect issues can get even worse thanks to Apple's predictive text feature, QuickType, and the inability to edit your custom dictionary.

This video will show you how to target your audience for Facebook post. You could set country, language, age group, qualification, etc. for watching your post. Watch the video and follow all the steps. Employ the technique in your Facebook account.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

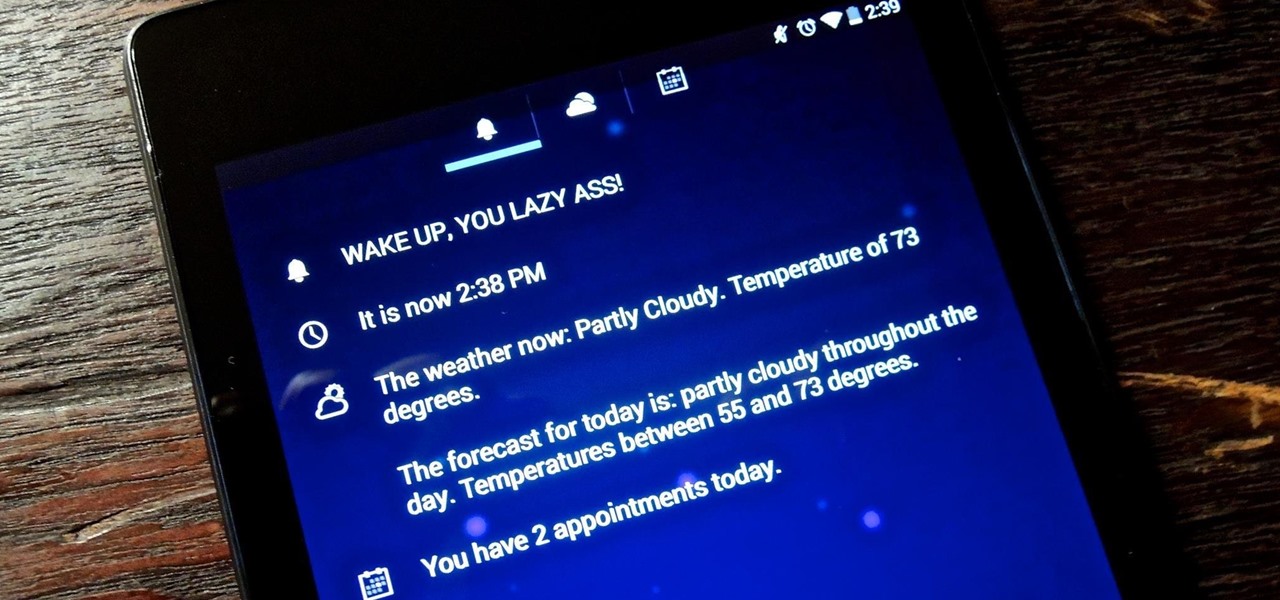
I regularly use my Nexus 7 to wake up in the mornings (well, sometimes afternoons), but it's pretty minimal in what it does. I shouldn't have to open multiple apps when I wake up to figure out my schedule for the day or what the weather is going to be like.

"Enter your email address. Confirm your email address." I absolutely hate seeing those two sentences when I'm signing up for something online, especially on my Samsung Galaxy S3. The less keyboard work I have to do on my mobile the better. Luckily, there is a way to enter your email address without having to type it all out, and I'm going to show you how it's done.

If you watched Samsung's Unpacked 2013 live last month, where they announced the new Galaxy S4, you probably sat through this awkward skit: This was Samsung's way of introducing their new translation software, dubbed S Translator. In the skit, the backbacking American traveler in Shanghai typed his question in English, and the phone spoke it aloud in Chinese. The other man replied in Chinese, and the app translated the message back into English. Live conversation translation aside, the app ca...

The man with the epic moustache is back. That's right, Mike the Greek is giving you yet another instalment of his Oscar Picks for 2013. In this episode, he talks Best Costume Design, Best Original Screenplay, Best Adapted Screenplay, Best Foreign Language Film! Get your little pencils ready.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

The best way to win friends over in a foreign country is by breaking the ice and showing your enthusiasm with your best effort at their language. Practice your Gaelic for travel or just for fun with friends.

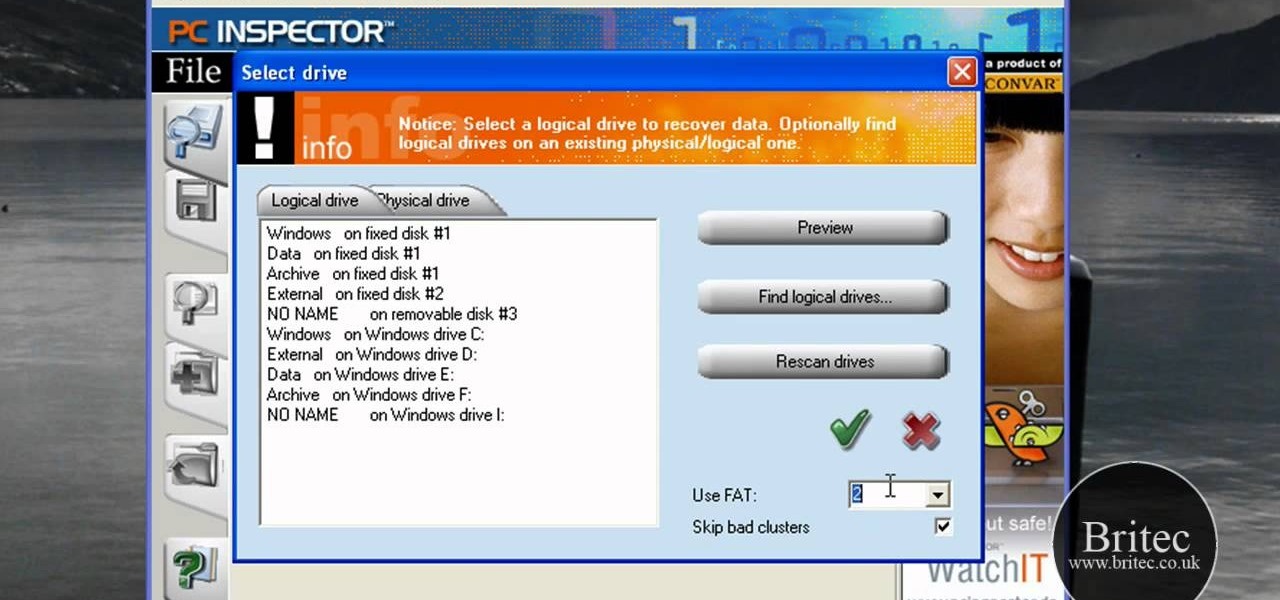
In this data recovery tutorial the instructor shows how to recover deleted files and lost data using a free software called PC Inspector. On your computer you may loose data sometimes due to a corrupted hard drive, or because you deleted it accidentally or some other reason. Now some times you will need to recover that important data and it will cost you hundreds of dollars to get it done outside by the professionals. Now you can avoid this and use a free software called PC inspector and reco...

Body language is one way to tell if a guy likes you. He will lean towards you or look at you a lot. If he likes you, both feet will be pointed towards you. If he doesn't like you, one foot will be pointed at the door. Eye contact is another way to tell if he likes you. If he is shy, he will turn his head quickly when you catch him looking at you. He may try to catch your gaze and hold it, which could be uncomfortable to you if you don't like him as much. Guys will try to make themselves seem ...

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

Whether you subscribe to Apple TV+ or not, the TV app on your iPhone is a great place to watch movies and TV shows. On the surface, it looks like a pretty straightforward app, but hidden features are lurking in the shadows that can enhance how you use it.