
How To: The Hardware Hacker's Introduction to Microcontrollers, Part Two: How Does Arduino Think?
In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!


In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.
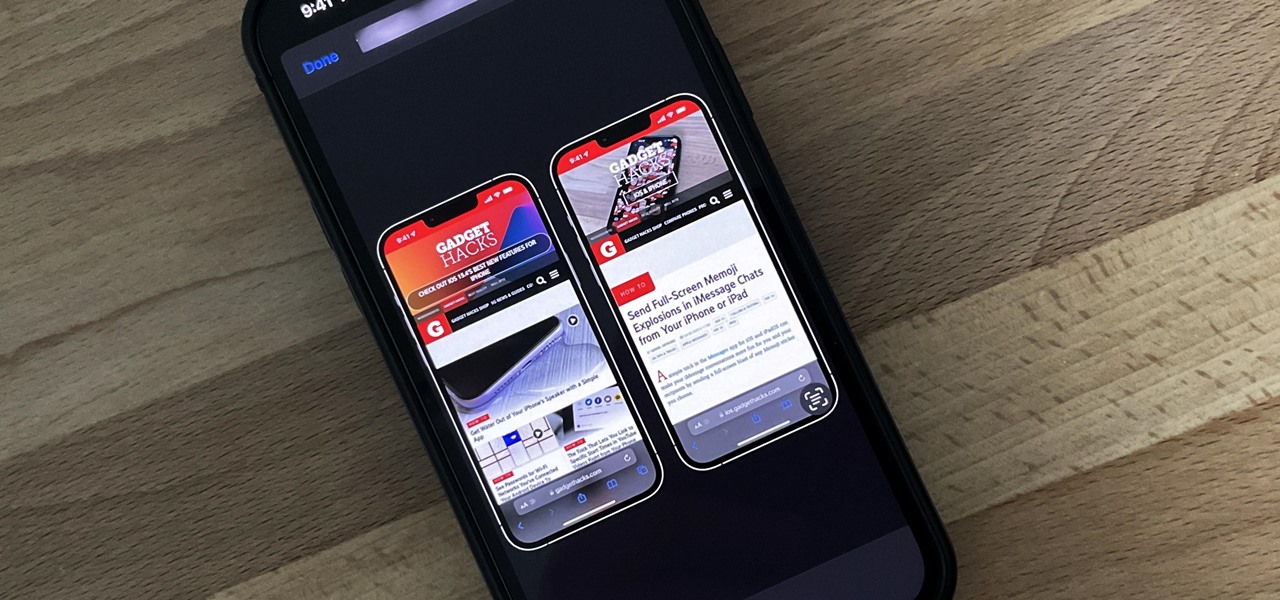
Have you ever seen an image on social media, somebody's blog, or a news website that shows an iPhone or iPad screenshot with an actual iPhone or iPad model framed around it? You can do that too, and it's really easy to accomplish with a third-party app — but you can do the same thing with a shortcut that won't bug you to pay or subscribe.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Python is commonly touted as one of the best programming languages for beginners to learn, and its straightforward syntax and functionality makes that hard to argue with. But a lot of tutorials still use Python 2, which is outdated now. Python 3 introduces many new features, and it's important to be aware of them going forward, as well as the key differences between Python 3 and its predecessor.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?
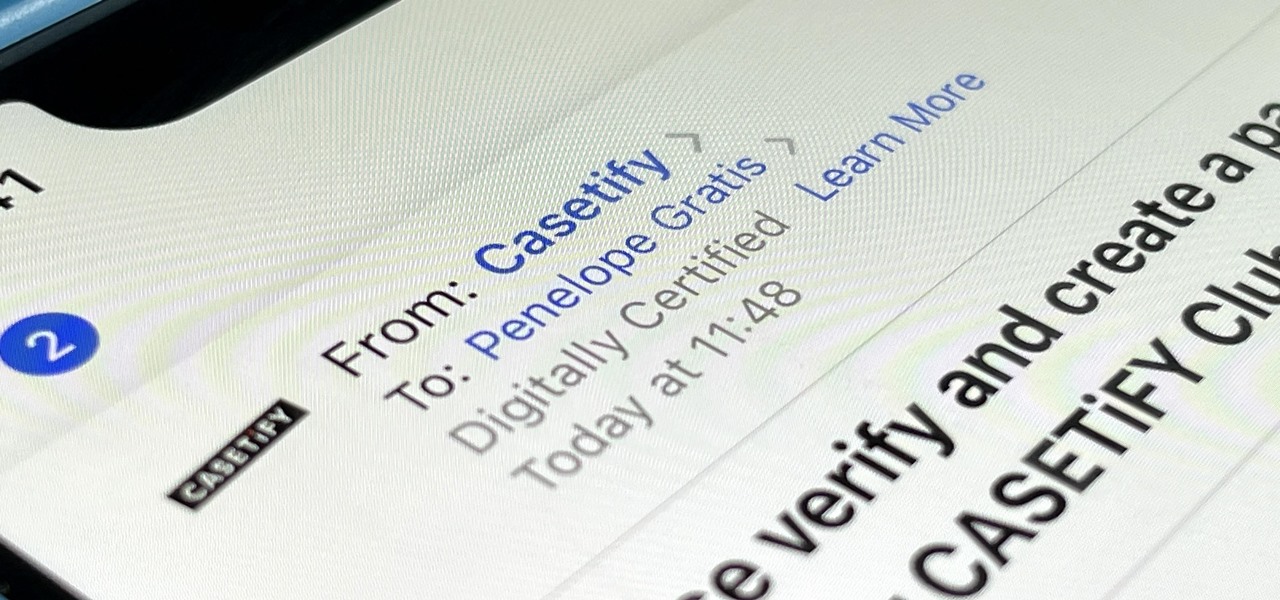
If you use Apple's Mail app on your iPhone for iCloud and third-party email accounts, install the new iOS update ASAP if you haven't already. While there's not a colossal number of new features, the latest tools and improvements are powerful enough to make the update feel like Mail's biggest ever — and there are features we've been waiting for for years!

Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.
In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

One of the coolest aesthetic features of iMessage is its animated message effects. If you're like many users, you might even have discovered them by accident, where wishing your friend a "Happy Birthday!" or congratulating them on a promotion unexpectedly flooded your screen with balloons or confetti.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.
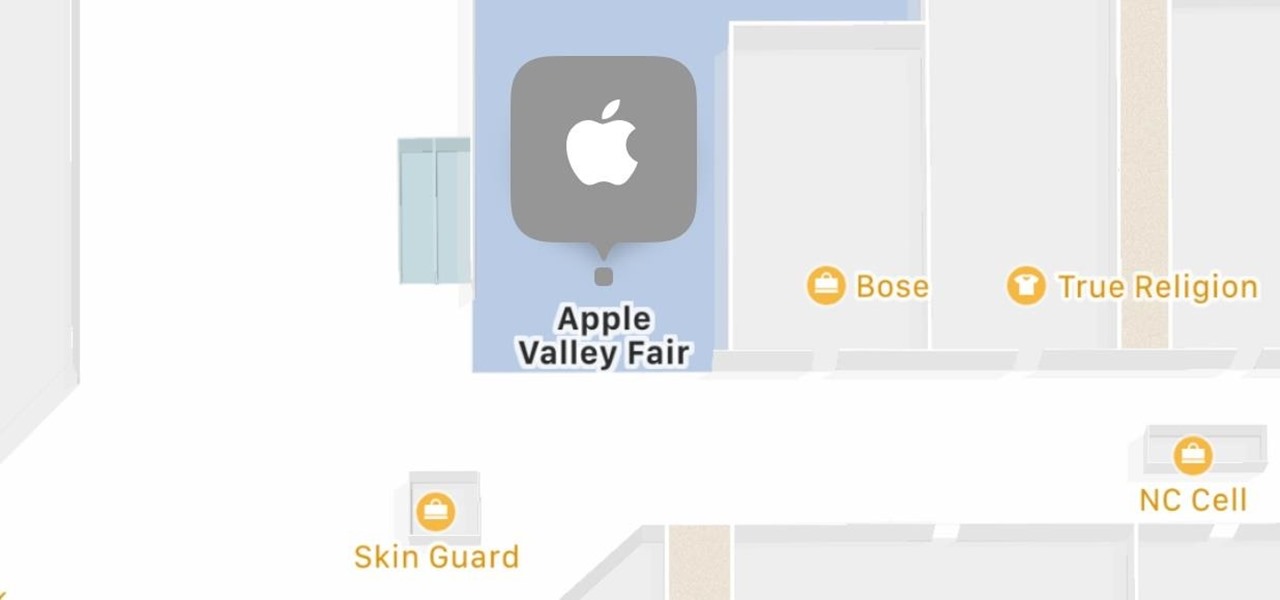
Apple has some great features aimed at making the lives of globetrotters and mall aficionados significantly easier, such as having detailed floor plans for airports and shopping centers in its native Maps app. With this feature available in Apple Maps, you no longer need to rely on publicly posted maps and directions that are often hard to understand.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Greetings my fellow aspiring hackers,

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.
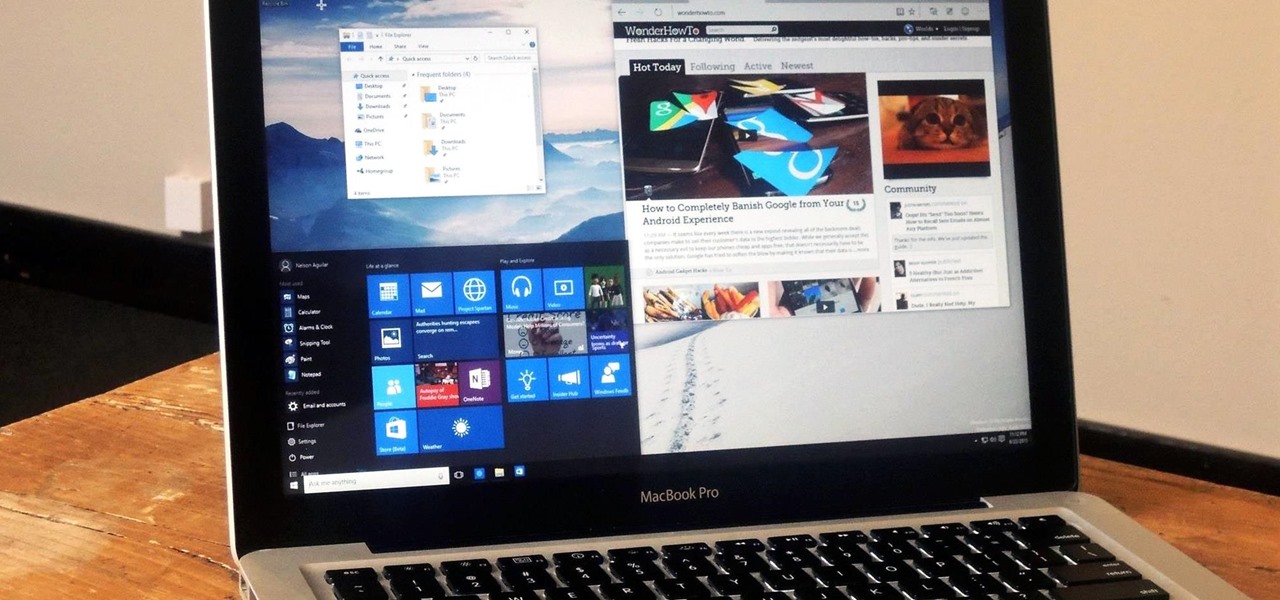
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

Apple's Siri is well-versed in the spells of the Wizarding World of Harry Potter, but it's not like Android users are Muggles. Google Assistant, Android's virtual concierge, can cast a few spells out of the box, and it can learn the spells it doesn't know quicker than a year of studying at Hogwarts.
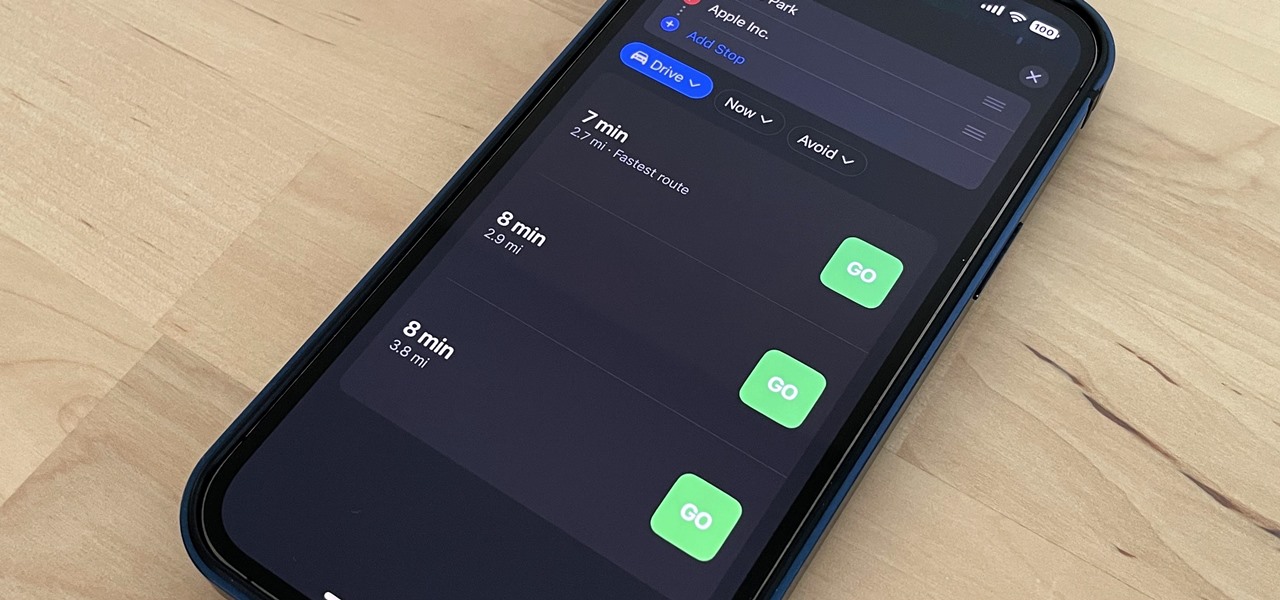
Apple removed the option to quickly change between miles and kilometers when using Apple Maps on iOS 16, but it's not entirely gone — it's just not as easy to find.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

Null Byte readers are no strangers to the powers and benefits that come from learning how to code. By knowing only a handful of programming languages and platforms, an intrepid developer can create everything from best-selling apps to spyware in the comfort of his or her own home.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

We all know how volatile the stock market is, especially during times of crisis. That does not mean that the market is impossible to gauge, however. Day traders are trained to read charts in order to recognize market trends and price patterns, giving them the insight they need to make their trades as profitable as possible.
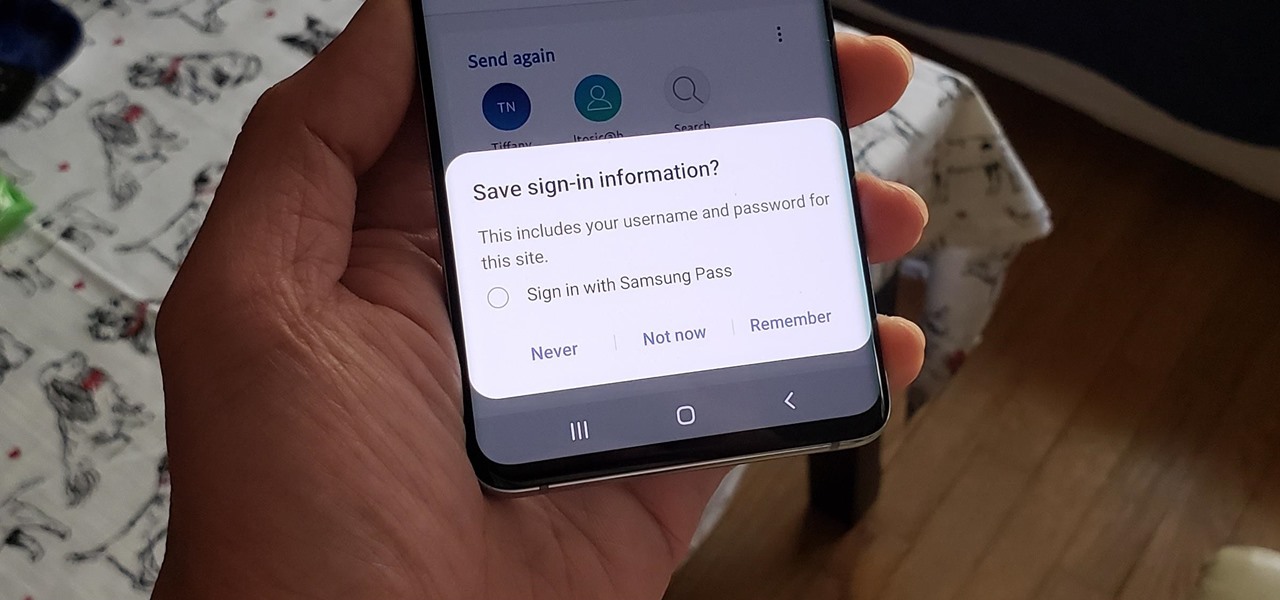
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.
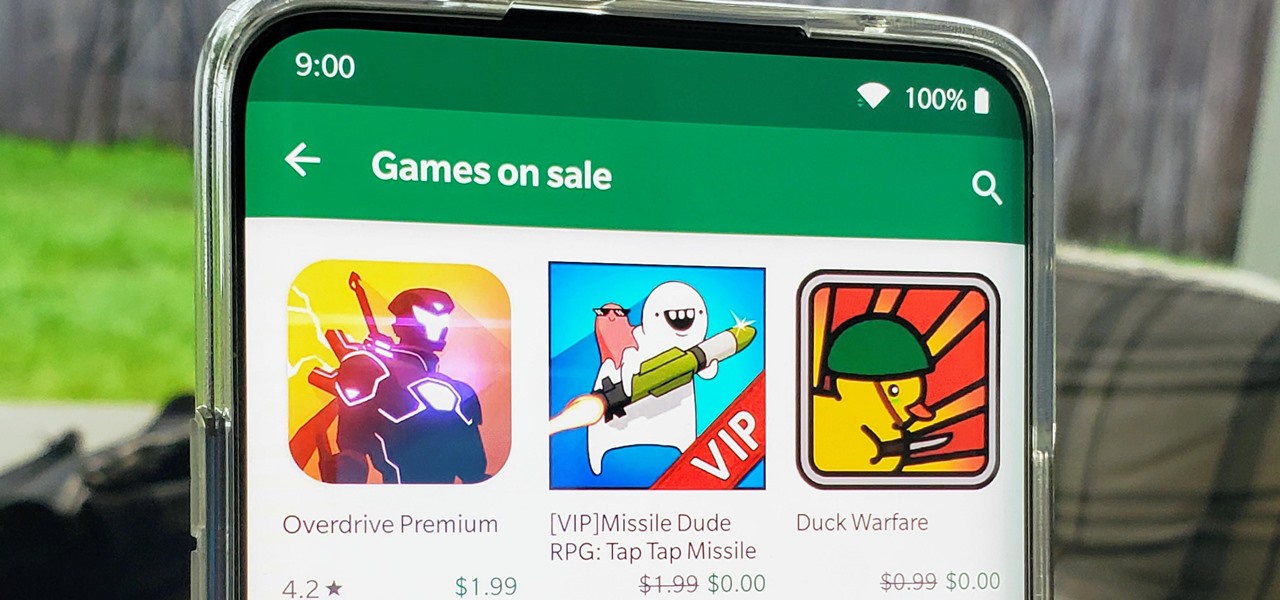
I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.