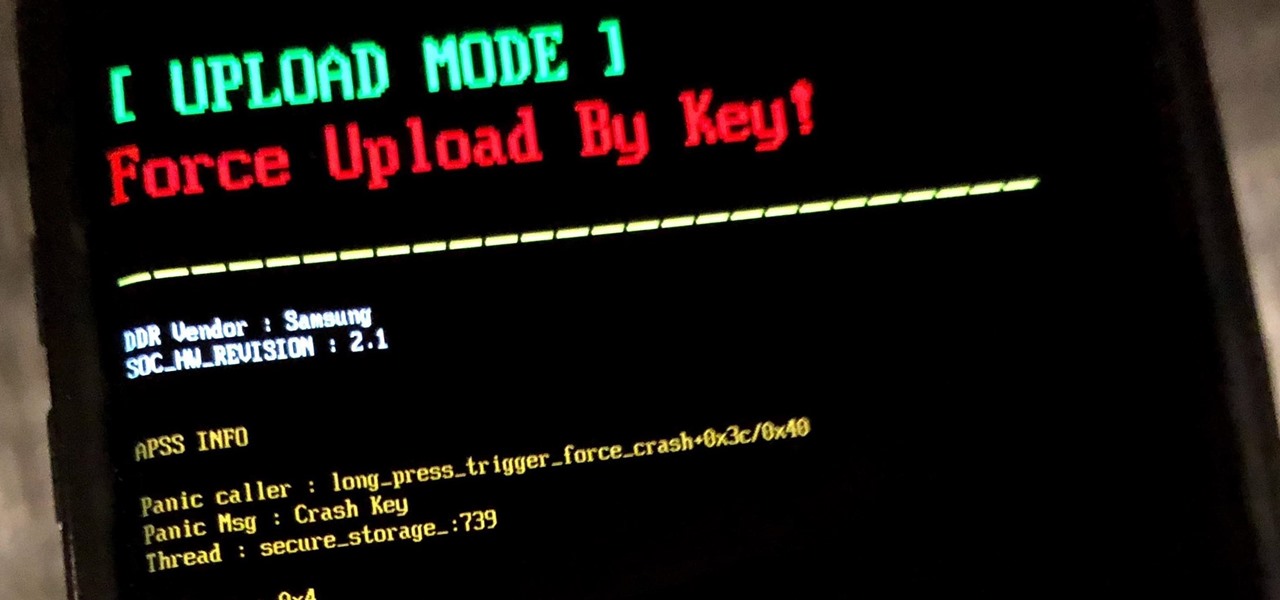
If you own a Samsung phone and enjoy rooting or modding your device, flashing official firmware can be very useful. Odin is Samsung's own internal program for loading such updates for testing purposes, and it's quite easy to use for your own custom modification needs.

The augmented reality industry made great strides in 2017, but its apex is not even in sight. In terms of software, augmented reality is approaching meaningful mainstream awareness, thanks mostly to Apple and ARKit. Meanwhile, on the hardware side, AR is very much in its infancy, with headsets mostly limited to enterprise customers or developer kits and the majority of smartphones lacking the sensors necessary to achieve much more than parlor tricks.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Google's Pixel phones claimed the top spot in our ranking of the best phones for rooting, but they do have one drawback from a modder's perspective: Because of their A/B partition layout for seamless updates, the devices don't have official support for Magisk. Thankfully, though, developer goodwin has stepped in with a fix, so we can now get Magisk working on the Pixel and Pixel XL.

Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

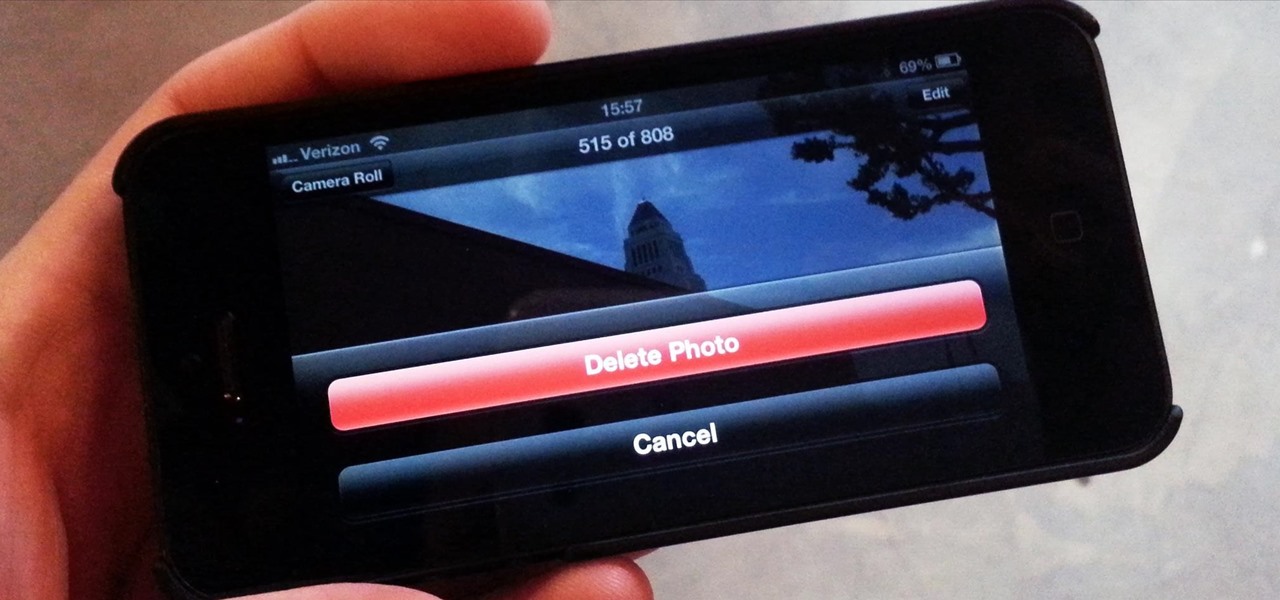
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

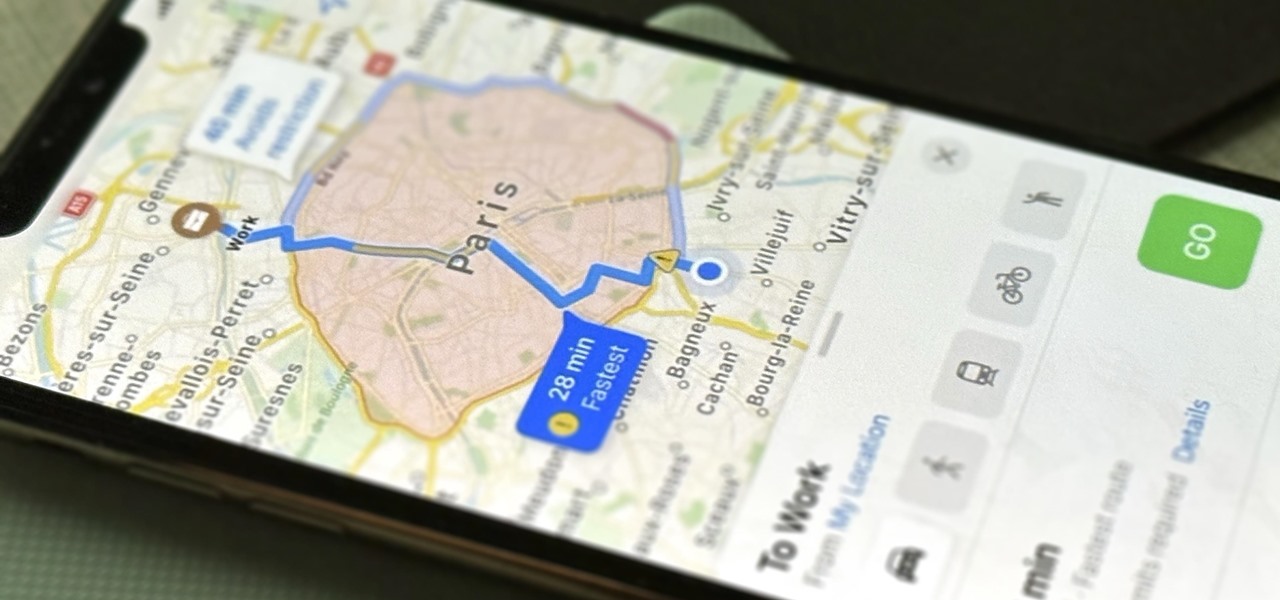
Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But what's worse than your electronics just giving up on you?

You may think your iPhone has all the features you could ever need or want, but that may change once you discover the features and services you're missing out on by residing in the United States.

From time to time, you may need to locate the version and build number for a particular app on your iPhone or iPad, but it's not at all obvious where you can find the information. Well, there's more than one place to look on iOS 18 and iPadOS 18, but none are perfect solutions. Knowing each method will ensure you can always find any app's real version number.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

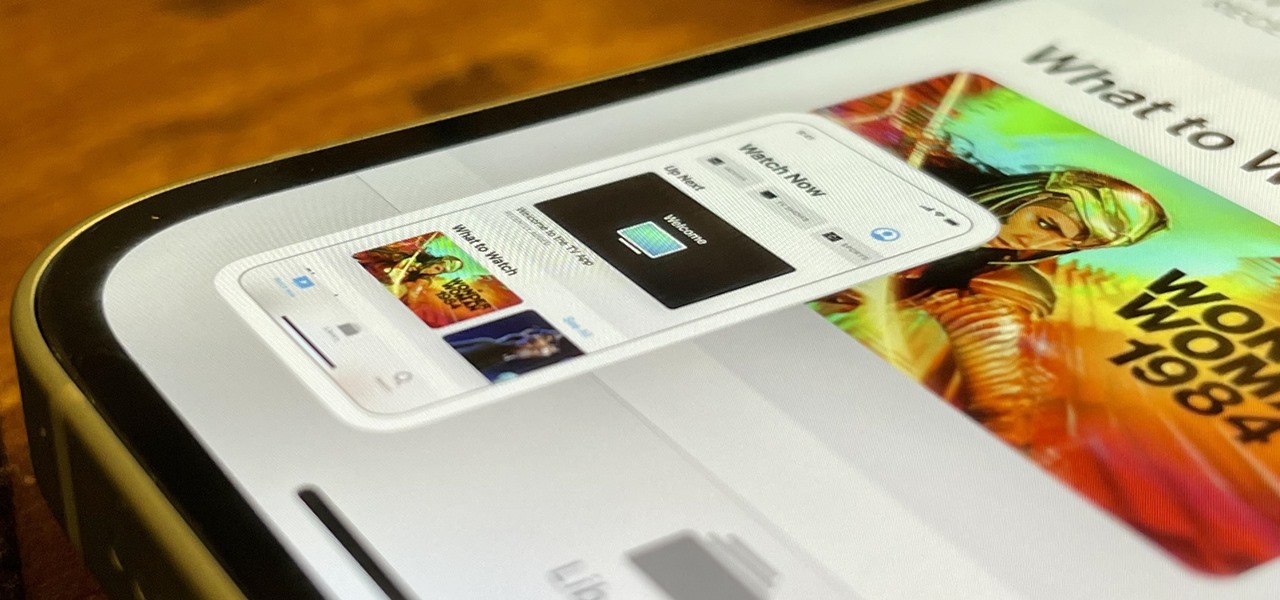
Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

While Touch ID has been a part of the iPhone's legacy since 2013, Apple waited until 2016 to add biometrics to its MacBook lineup, and it's not as impressive. An iPhone with Touch ID can register up to five fingerprints, but Macs can only register a maximum of three per account. If that seems unfair, there's an easy trick to doubling that number, meaning six of your fingerprints could unlock your laptop!

The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar sizes and features to 2020's offerings. If you want to know what makes the 2021 iPhones so different, we've got answers.

If you just got an iPhone 12, 12 Pro, 12 Pro Max, or 12 mini, and you've never owned an iPhone before, some of the most basic tasks can be baffling. Shutting it down, force-restarting it, quitting apps, and even viewing the percentage of battery remaining sound simple but aren't very intuitive for new iPhone owners. Another big question mark is screenshots, and there are several ways to take them.

The holiday season is here! Whether you're gift shopping for the iPhone owners in your life or just trying to save some money on your own purchases, Black Friday can deal out the discounts. This year, you'll find great prices on iPhone accessories of all kinds — all Thanksgiving week long — whether you're buying gear for an iPhone 12, X, or 7, there's something here for everyone.

Apple has four iPhone models for the remaining months of 2020, but the most impressive ones are the iPhone 12 Pro and iPhone 12 Pro Max. While the iPhone 12 and iPhone 12 mini are great smartphones, the "Pro" models offer more advanced features, especially for photographers and augmented reality enthusiasts.

Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed on countless other TVs and set-top boxes.

Last year, many were caught off guard when Google released a midrange Pixel device. It was quickly crowned the best value-buy phone on the market, as it brought most of the camera tech people loved in the flagship Pixel for almost half the cost. Google's 2020 entry in this series has finally made its long-awaited debut.

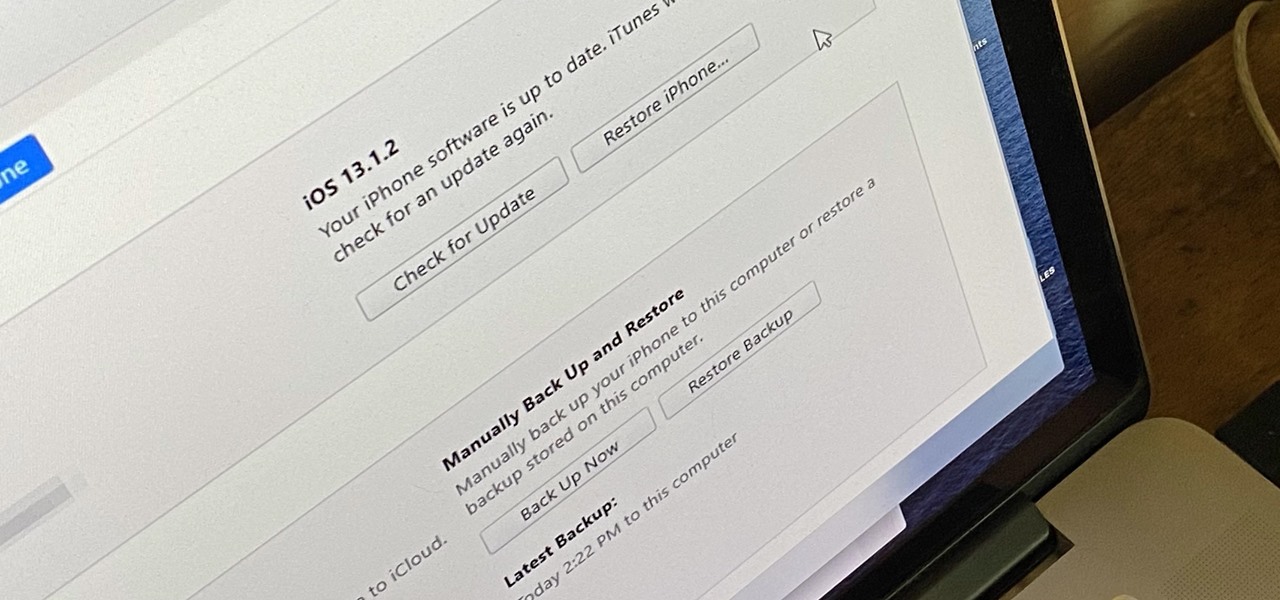
Whenever something goes wrong with your iPhone, or whenever you want to downgrade from an iOS beta back to the regular iOS release, you can restore your iPhone to your last saved state. Restoring to an iCloud backup is great but won't work in all situations. Plus, if you saved a backup on your computer, that may be the best route to take to get back all of your data.

Despite making great phones for years, Sony continues to struggle to penetrate the US market. Sales volume has fallen year after year, with 2019 limited to only 5 million units sold globally. To help alleviate this drop, last year, Sony released the Xperia 5, the return to compact smartphones. This year, rumors indicate a sequel is first on their agenda.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.