
How To: Make a Prank Popup Message in Windows That's Hard to Get Rid Of
This is a very simple, but very funny prank to play on your friends using Windows. Creating the file


This is a very simple, but very funny prank to play on your friends using Windows. Creating the file

Get Google Chrome Download and install Google Chrome.

If you ever consider modding your Galaxy Note 20 or Note 20 Ultra, you'll need to know about recovery mode and download mode. Even if that isn't your thing, knowing how to how to boot into these modes can help save your phone from a soft brick.

One of the things you've likely gotten used to if you have a rooted Android phone is not installing OTA system updates in a typical fashion. Depending on your version of Android, you might not actually be able to swipe away that nagging update notification at all. Thankfully, there's a way to prevent your system from automatically checking for OTA updates.
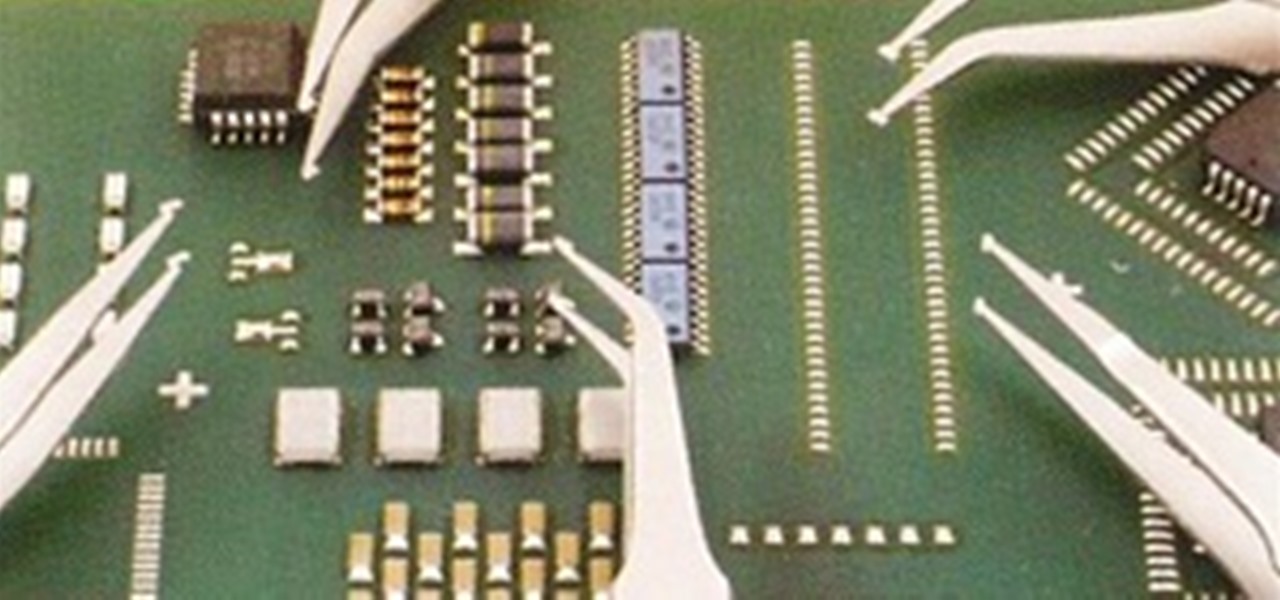
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get those last microns, we have surface-mount components for SMDs (surface-mount devices). These are all of those teeny, tiny things you see when you crack open your digital camera or laptop case.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

Pygame! And what you can accomplish with it. Another python article... (Blame Alex for getting me hooked on yet another coding language...)

Filter effects aren't a new thing. But when Instagram hit the market, everybody began using them because it was simple. Take a picture, add an effect. It wasn't only easy, it was fun. It started a craze among smartphone users everywhere, prompting a slew of retro photo filter apps to pop up for Android and iPhone. One app that stands out from the crowd is FX Photo Studio.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.
At GDC 2011 this past March, three of the world's best game designers participated in a contest called Game Design Challenge. Each presented their vision for a game that fit the prompt "Bigger than Jesus: games as religion" before an audience, with applause to determine the winner. Jenova Chen, John Romero, and Jason Rohrer all spoke, and Rohrer won in a landslide with his revolutionary game called Chain World.

This week, Apple announced the beta version of its new wireless, cloud-based service, iCloud. I wrote a summary of it here. The iCloud service includes some new features in the latest version of the iTunes Store, which allows you to access all your iTunes songs, mobile apps, and eBooks purchased in their respective iTunes stores and download that media to up to 10 of your devices—your iTunes supported Macs and PCs and mobile devices. This downloading can all be done wirelessly without you hav...

I love my laptop. It goes wherever I go. Unfortunately, that means that it also gets pretty grubby after a while. The screen gets dusty. The frame gets smudgy. The spaces between the keys fill up with crumbs of questionable origins. And my desktop? That thing is a dust bunny magnet.

Many folks seem to treat their computers as a sort of mysterious alien technology that only the shamans of the IT Department can comprehend. You might have gotten it into your head that you're just not good at computers and will never understand them. On the contrary, getting a basic grasp on all the amazing stuff inside your computer doesn't require you to be a technological genius. Most people will never have a need or desire to open up their computer and poke around. But it's your machine....

The Google Nexus S smartphone is finally here! Well… almost.

Google's much anticipated eBook Store has finally opened. As of today, the digital bookselling enterprise is awaiting your needs, with over 3 million eBooks to read directly on the web or on other platforms, like Android, iPhone, iPad, Sony and Nook devices.

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Yesterday was the biggest shopping event of the year— Black Friday— the day after Thanksgiving. Most waiting in huge lines, getting swallowed up by commercialism on its biggest profit-turning day, and there's still tons of shopping to be had on Saturday and Sunday, with many stores continuing their sales across the weekend. But if you're not interested in bouncing heads with a rush of angry holiday shoppers, you can still get the same deals online, from the comfort and safety of your own home.

These days, eReaders are everywhere. For die-hard book nerds, eReaders offer the convenience of a full library without having to sacrifice shelf space. Sure, there are the paper buffs who swear that you just can't take an eReader with you into the bathtub, but when's the last time anyone actually did that? Face it, eReaders are convenient and here to stay. But there's a dizzying array of information out there, so what should you look for in an eReader?

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

It may not be your number one spot for finding cool apps for your Android device, but the Amazon Appstore for Android is running a new promotion this week called "Geek Week," where eight of the most popular productivity and utility apps are now on sale for 48 percent off or more.

Culinary collective Studiofeast is known for thinking outside the box, especially when it comes to food. They've hosted inventive and spectacular events like the L Train Lunch, where a high-end meal was served to guests on a moving train, and the Datalicious Last Supper, where results from a survey of people's desired "last meals" informed the menu.

Hangouts are one of the most fun features in Google+. As long as you have a webcam and a microphone, you can "hangout" with up to 10 of your buddies on Google+ and do just about anything. Of course, sometimes it can get kind of awkward when you are hanging out and you don't really have anything to say. This problem can be mitigated if you host hangouts with a plan.
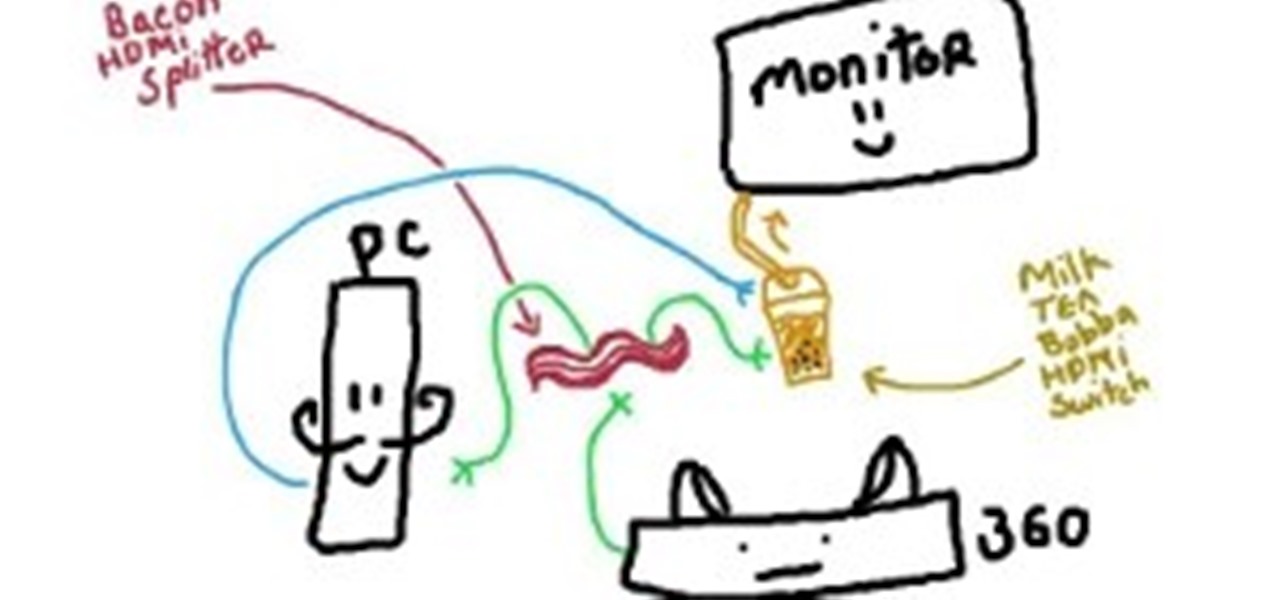
Video capture... how does it work? Apparently, I have no idea. What I thought would be a simple undertaking turned out to be a slow and annoying pain. I just wanted to capture video in high definition and to lessen the time it takes to setup, record, and upload the video.

Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet another edited version. Soon you're drowning in a desktop folder full of mismatched documents, all with the same name.

Are you tired of counting your hair while waiting for your computer or laptop to respond? Then, these easy steps are perfectly fit for you, especially if you're a Windows 7 user.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!

I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible.