
How To: Crochet the cluster stitch
Improve you crocheting skills by learning the basics. This how to video is a crocheting tutorial that will show you how to do a crochet cluster. Crochet several cluster stitches to create larger yarn projects.


Improve you crocheting skills by learning the basics. This how to video is a crocheting tutorial that will show you how to do a crochet cluster. Crochet several cluster stitches to create larger yarn projects.

The Pattern Stamp Tool in Photoshop is great for filling larger areas with a repeating pattern. This tutorial will show you how.

Watch this video to learn some of the fundamentals of crocheting. It will show you how to crochet increases. This technique is useful for tapering projects to a larger size.
Another NewDarkRoom.com Video tutorial. This tutorial will show you how to get more room out of your photo booth by hiding all the unwanted parts past your seamless paper. As usual you will be able to find a more detailed larger video at our website.

PDFs are the industry standard for document sharing. However, sometimes PDFs generated by non-Adobe apps can tend to be larger than they need to be. In this video you’ll learn how to make your PDF files smaller even if they were not generated by an Adobe product.

If you use After Effects you have become familiar with the Work Area, a range of time that allows you to focus on a specific range of time. You can work exclusively in this area, or work in the larger time of the composition, only to preview or render that area of time when you go out to final. In CINEMA 4D, users can achieve similar results using the Preview Range. This tutorial will show you how.
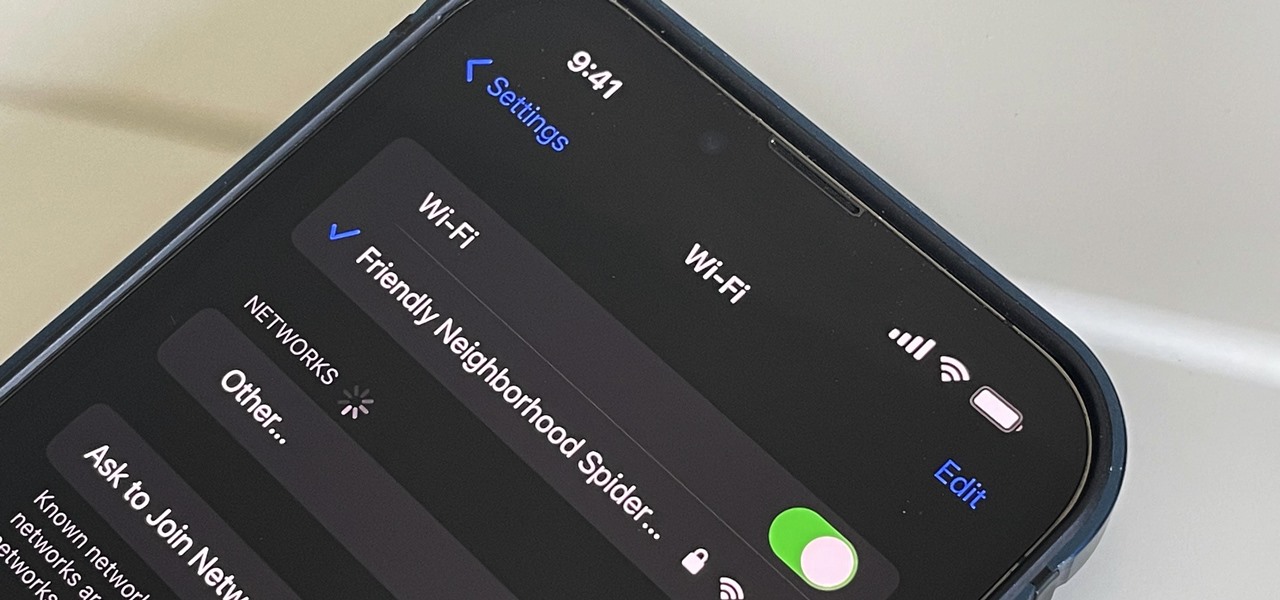
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Can you be too lazy for video games? That's how I feel sometimes. I want to play the latest PlayStation has to offer, but I can't be bothered to get out of bed. As if Sony read the minds of lethargic gamers everywhere, the company has released an amazing thing — PS4 Remote Play allows you to play your PS4 on your iPhone, no TV required. The best part? It's 100% free.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.
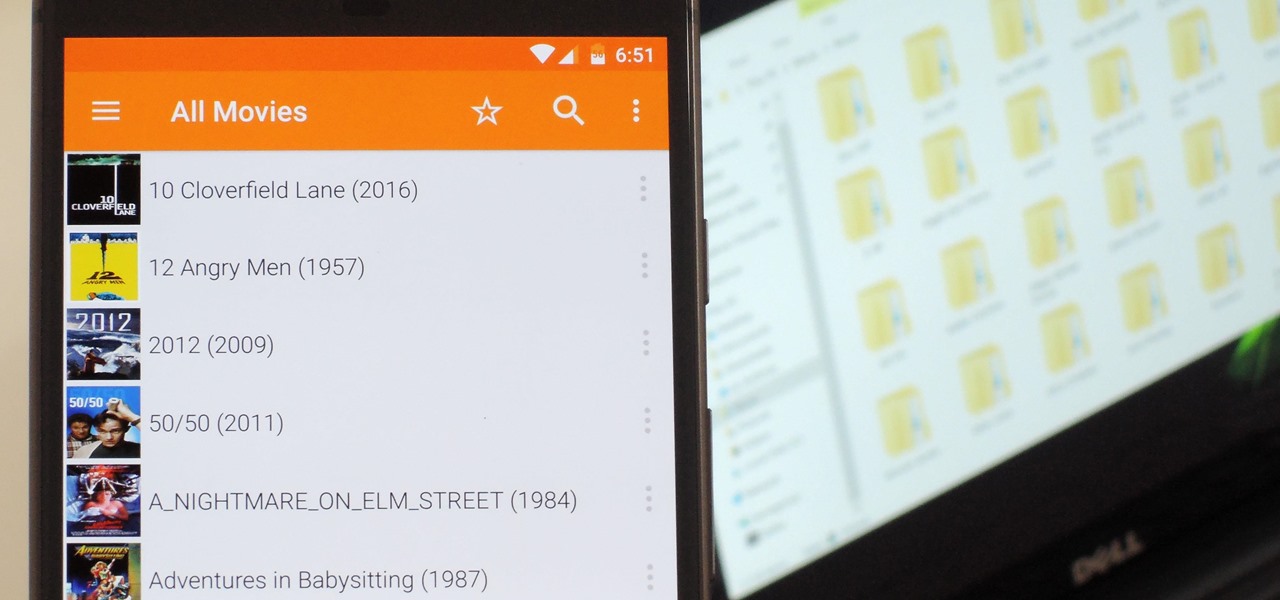
Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.
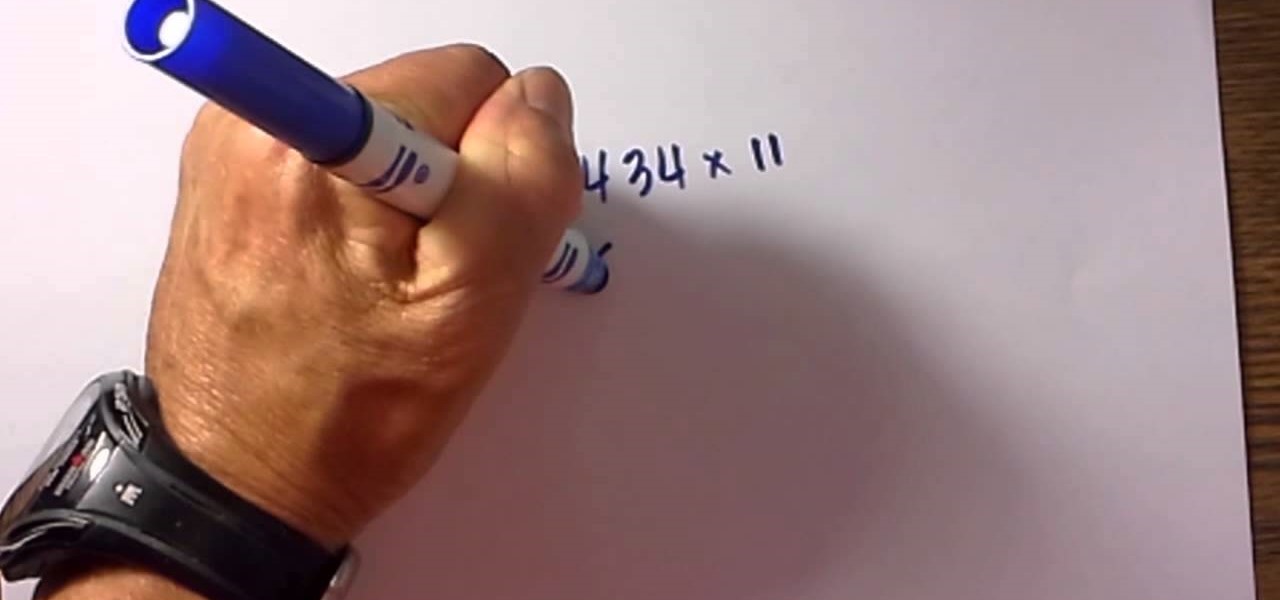
Yes, with this simple technique you can multiply 2 digit numbers in your head. The video also reviews a really easy method for multiplying larger numbers by 11 in a simple fashion.

The basics of how to pack personal gear for a canoe trip. This video doesn't cover food or larger gear like tents and canoes, but the rest is covered. Enjoy!

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Xara Website Designer Tutorial learn how to test website compatibility. This website design tutorial emphasizes the importance of compatibility for end users. If your website design does not work in certain web browsers its important to address the issues before your website begins to grow larger.
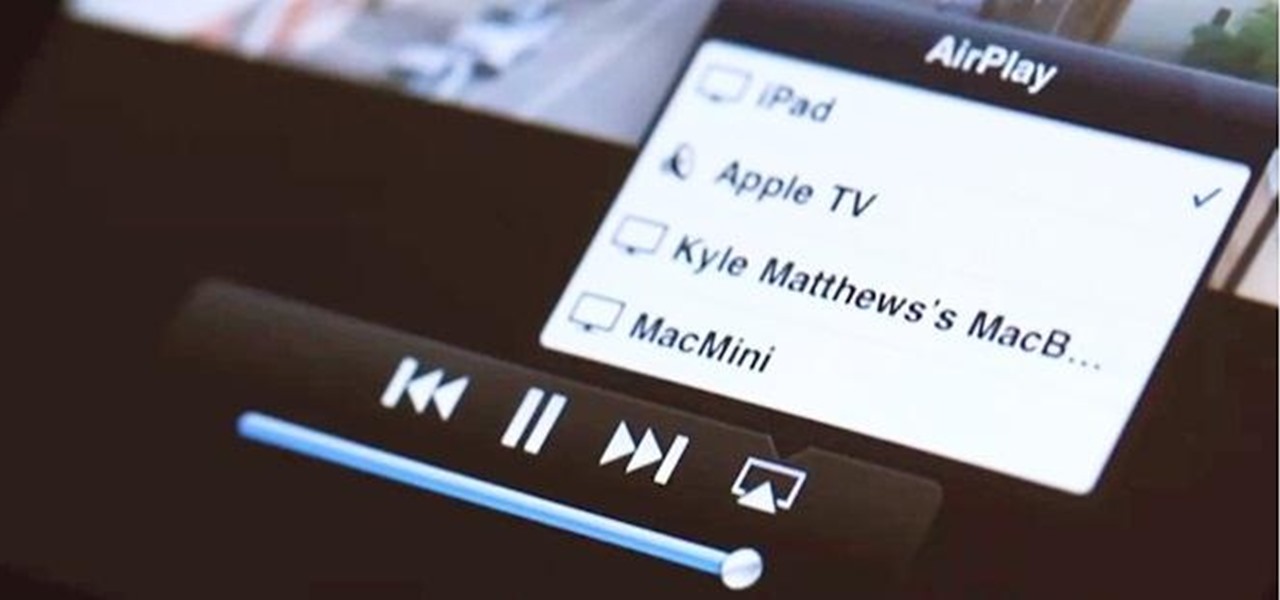
AirPlay is probably one of the most underutilized features in Apple products. It allows users to wirelessly stream photos, music, or video directly from their iPad, iPhone, iPod touch or Mac to their Apple TV or AirPlay-supported speakers. The Apple support page has a complete list of all the supported and needed devices. Mirroring is also available, but only for the iPhone 4S, iPhone 5, and iPad 2, all of which need to be running iOS 5 or later.

Some locks are easier to drill through than to try and pick, especially if you need to get through them in a hurry! You will need one large power drill and an assortment of drill bits to be able to use this method. First, drill a 1/8 inch pilot hole just above the keyhole. Then follow through with a 1/4 inch or larger drill. After just a minute or so of drilling, you should be able to get through the lock!

PICC stands for a peripherally inserted central catheter, and is usually inserted somewhere in your patient's uppper arm, giving access to the larger veins in the chest region. PICC lines are often desirable because they are the least risky way of giving central access to the veins near the heart, especially when your patient will need to have one for an extended period of time. This tutorial shows you everything you'll need to know about how to properly and safely insert a PICC line into you...

A compact survival kit is a great piece of gear to bring with you into the wilderness even if you have a larger pack as well, to serve as a backup. This video features a Brazilian wilderness survival expert detailing the contents of his compact survival pouch, a homemade canvas model.

In this tutorial, we learn how to make a serving tray from a picture frame. First, grab a picture frame in a larger size that comes with glass on it and a backing. From here, you will grab some scrapbooking paper or another type of paper and cut it to size to fit on the background of your paper. Then, find two handles that you have and screw these onto the sides of the picture frame. After this, glue your favorite pictures onto the paper and then let it dry. When finished, stick this under th...

In this tutorial, we learn how to make a flat circle using double crochet. To start, you will begin with twelve double crochets in a ring shape. For the second round, you will increase in every double crochet until you have twenty-four. Next, you will increase every other double crochet until you have thirty-six double crochets. For round four, you will make two double crochets between increases until you have fourty-eight double crochets. For the last round, you will make three double croche...

In this video, we learn how to make a flat circle using single crochet. Start out by crocheting six single crochets into a ring for round one. For round two, you will increase in every single crochets so you have twelve of them. For round three, you will increase with every other single crochet doing one single crochet in between the creases. do this for a total of eighteen. Then, make two single crochets between the increases and you will have twenty-four. On the last row, you will make thre...

Try your hands at duck eggs instead of chicken eggs. Duck eggs are practically the same, a little bit larger than chicken eggs, but the yolks contains a lot more fat (making them richer) and the whites contain a lot more protein. They're perfect for baking because they make desserts light and fluffy! But forget about dessert— we're talking pizza here.
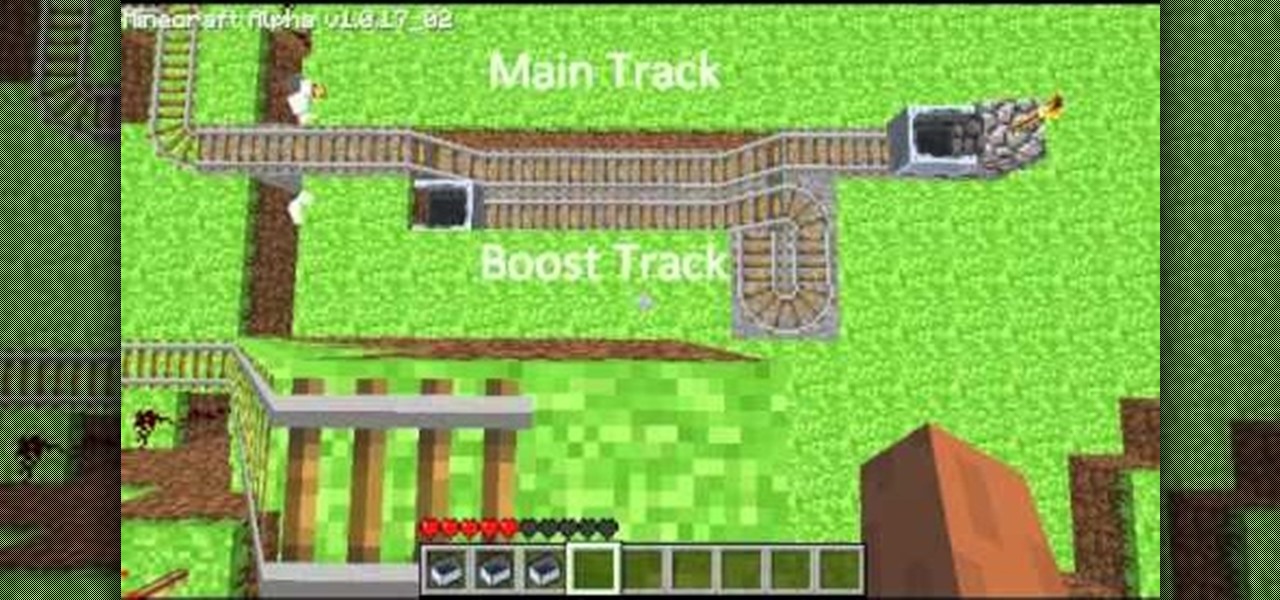
In Minecraft, one cool way of getting around those larger fortresses and bases is to set up a minecart. If you're looking for fun or efficient new ways of setting up your minecart station, adding booster carts to make it faster, and adding floor tile switches, check out this video series! There's a plethora of information in here that'll give you the inspiration to have more fun with your base building!
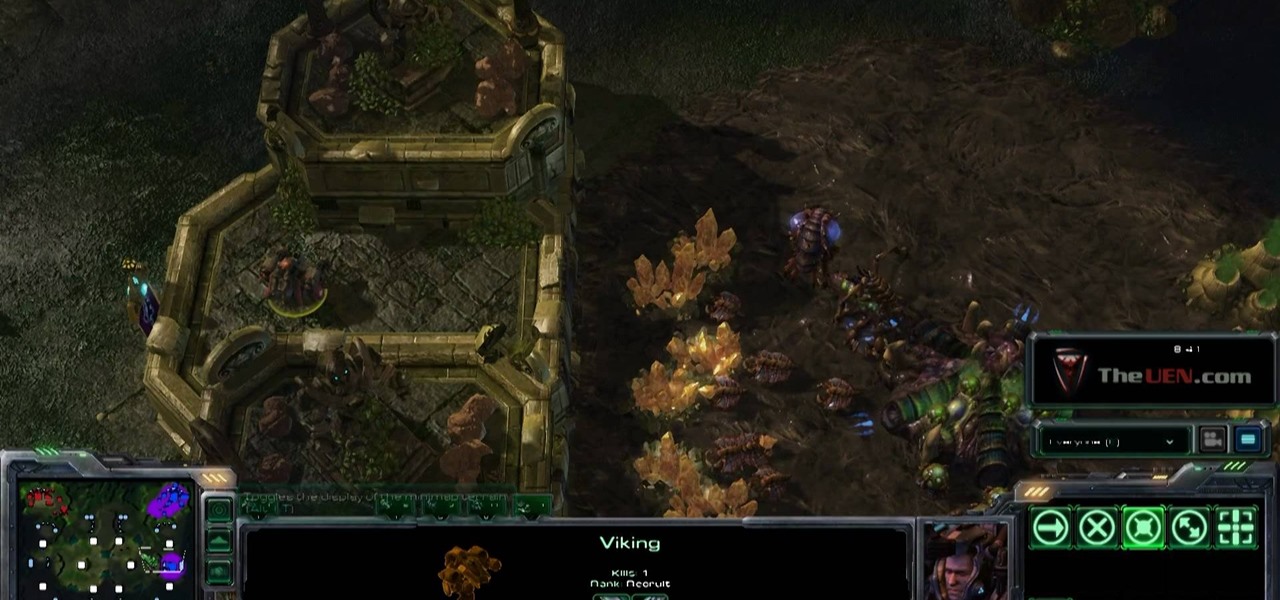
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to take advantage of ledges on the map to make your Terran Viking un...

If you still own and use an original XBox console, good for you! You've got a little piece of history right there that most people just tossed or sold to a game store for $10. This video will show you how to replace the paltry 8gb hard drive that the console came with with a big honking 120gb drive. This will allow you to store more data, and since hacking the original XBox is the best reason to keep it around at this point, you should probably make sure that you can do that.

If you are unfortunate enough to own one of the XBox 360's that shipped with a 20gb hard drive, then you've realized that that is way to little storage for everything that you want to have on your XBox. If you've decided to buy a larger drive from Microsoft, this video will show you how to transfer your precious saves and other files from the old hard drive to the new one using a transfer kit. Now you can buy as many downloadable games as you want or even install your disc games on the hard d...

Microsoft has behaved pretty douchily as far as managing the hard disc drive (HDD) sizes it made available for the XBox 360. The 20GB drive included in most models of the system is woefully inadequate, and many have been convinced to give Microsoft even more money to get a larger one. That's not necessary. This video will teach you how to upgrade the XBox 360's hard drive yourself, putting in any large-capacity SATA drive you wish and massively increasing the storage capacity of your XBox 360...

Know your knots! With this free video tutorial, you'll learn how to tie a twisted leader knot. When tying a twisted leader fishing knot, you'll probably use a small amount of filament and attach it to a larger braided fishing line. The knot is easy to tie provided, of course, you know how to go about making it. For an easy-to-follow, step-by-step overview of how to tie this useful fisherman's knot in a minute's time or less, watch this free video knot tyer's guide.