Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!
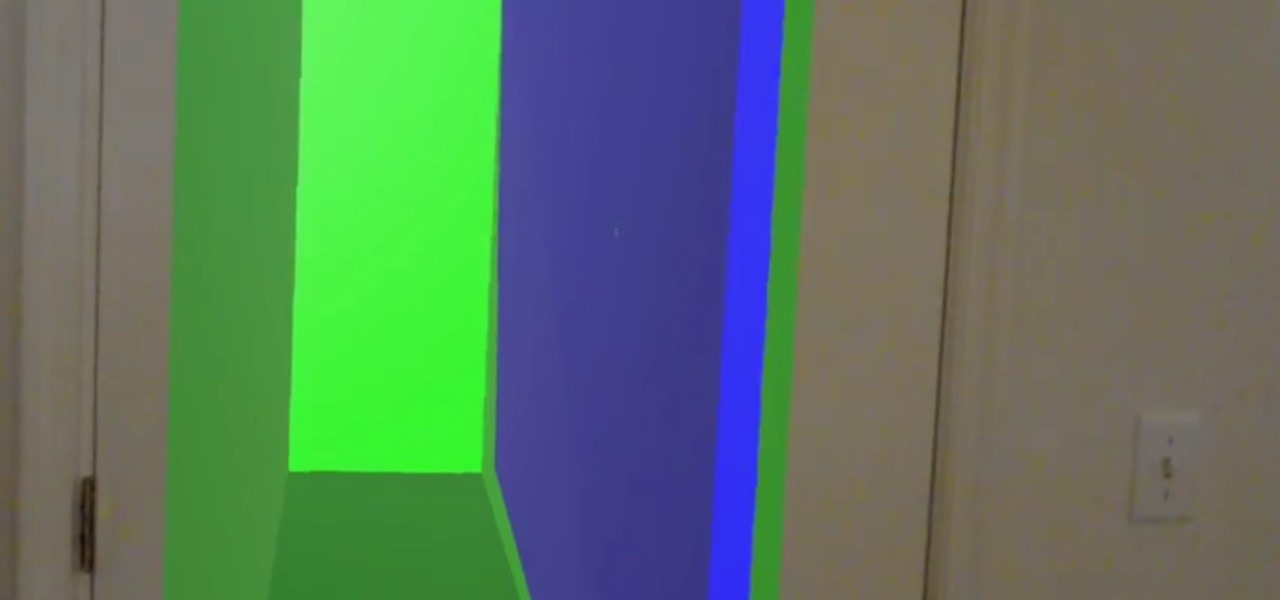
Once mixed reality technology is more widely available and realistically priced for consumers, using the tech to create the illusion of a larger space, will likely be a favorite use for mixed reality in places where real-estate is expensive, people tend to live in smaller homes and work in tighter offices.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

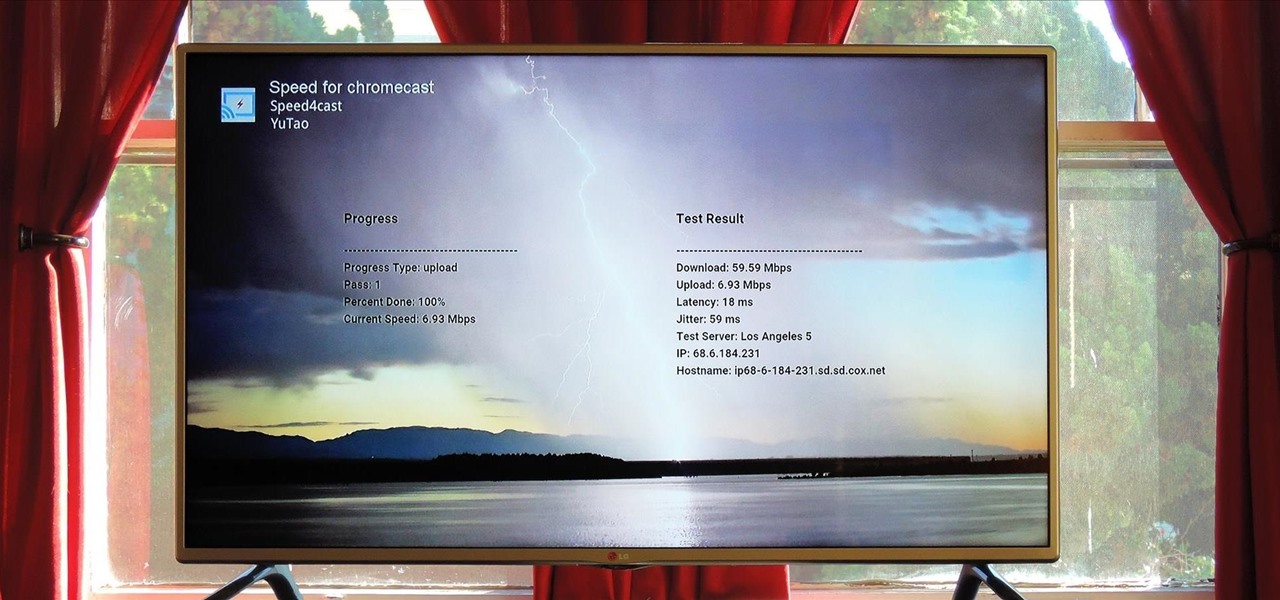
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Google recently changed the way we search online, and from what I can tell, I'm not the only person online just a little bit irritated with the new design.

ThreadBanger's Corinne visits with Luca of Lolibomb to learn how to make winter-inspired vegan beauty products in a DIY fashion. Way to save some money on gifts! In just fifteen minutes and a few easy steps, make an animal-friendly body butter for your best buds with these ingredients: cocoa butter, hazelnut oil, emulsifying wax, stearic acid, liquid glycerin, distilled water, and a vitamin E preservative of your choice. Add the body butter to a decorative jar and you have a great gift that m...

Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about capturing digital photos with the Meade Deep Sky Imager. The universe is out there, and you can take a picture of it.

The Nokia Booklet 3G netbook is capable of utilizing GPS when the 3G network connection is active. If you want to find your location and see a map of the area around you, try out the Maps gadget available as part of the Ovi Suite.

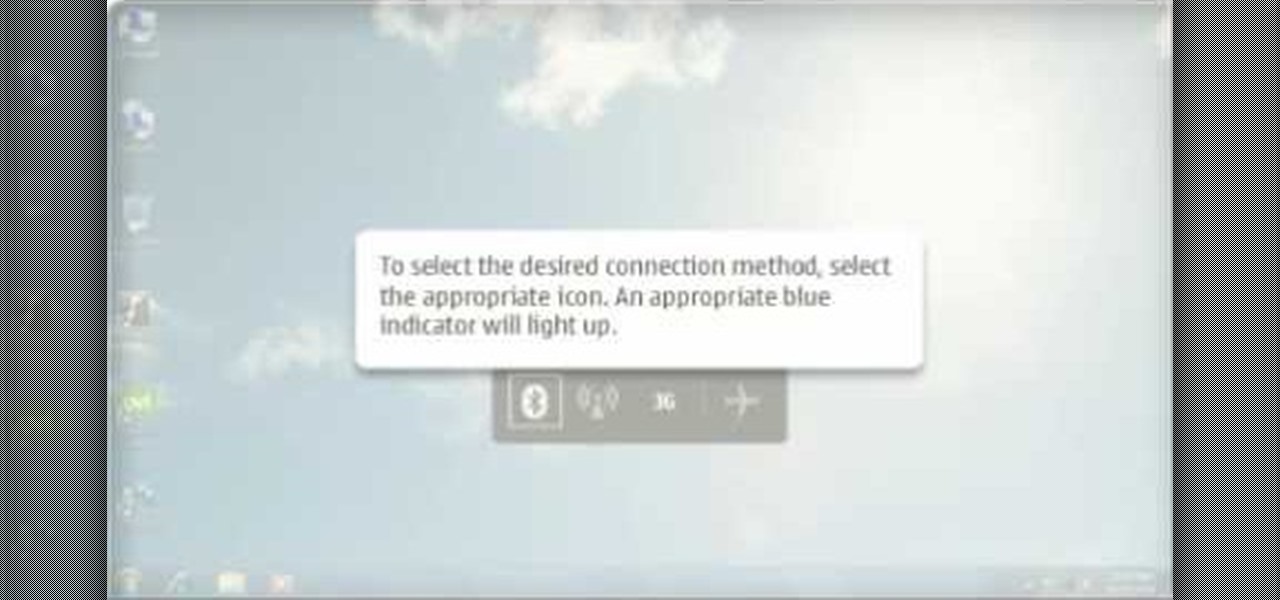
If you hit the FN + F10 keys on your Nokia Booklet 3G, you'll see the available internet connections methods for your netbook including Bluetooth, wifi, and 3G.

Curious about Google's new social network, Google+? Get the rundown by watching this video and learn the ins and outs of Google plus, including the circles feature, the chat feature, photos and more. This is your video guide to Google+.

Check out this video for an introduction to the new Google+ app for iOS. You can use Google plus from any of your iDevices, including iPhone, iPod Touch and iPad. Make the most of Google's new social network with this app.

Looking to get online with your Nintendo 3DS so you can play your favorite DS games with your friends? Watch this video to learn how to set up a Nintendo 3DS on a wireless network so that you can enjoy handheld online gaming.

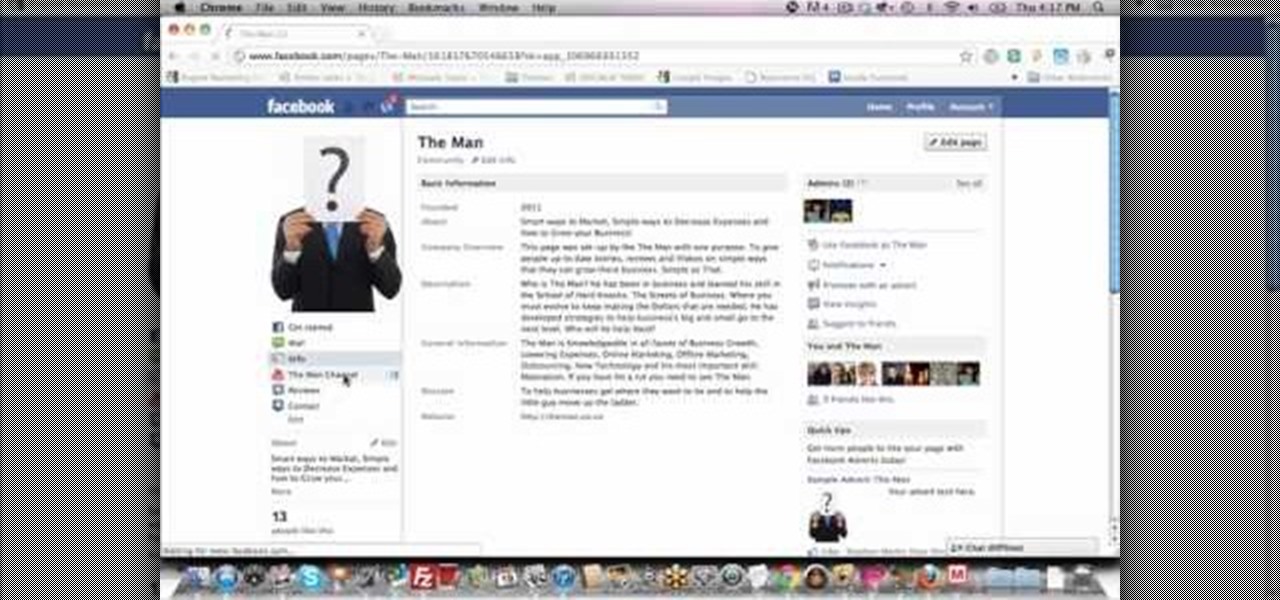
Facebook is a great tool for businesses. Watch these videos to learn how to maximize the effectiveness of your business' Facebook page. Reach out to your customers with social media and networking with the methods demonstrated in these how to videos.

If you've just brought home a brand new Android smart phone, or you've installed a new ROM, you probably don't want to have to go through the configuration process on the 3G network. You can skip the "Touch the Android to Begin" screen and get straight to the good stuff.

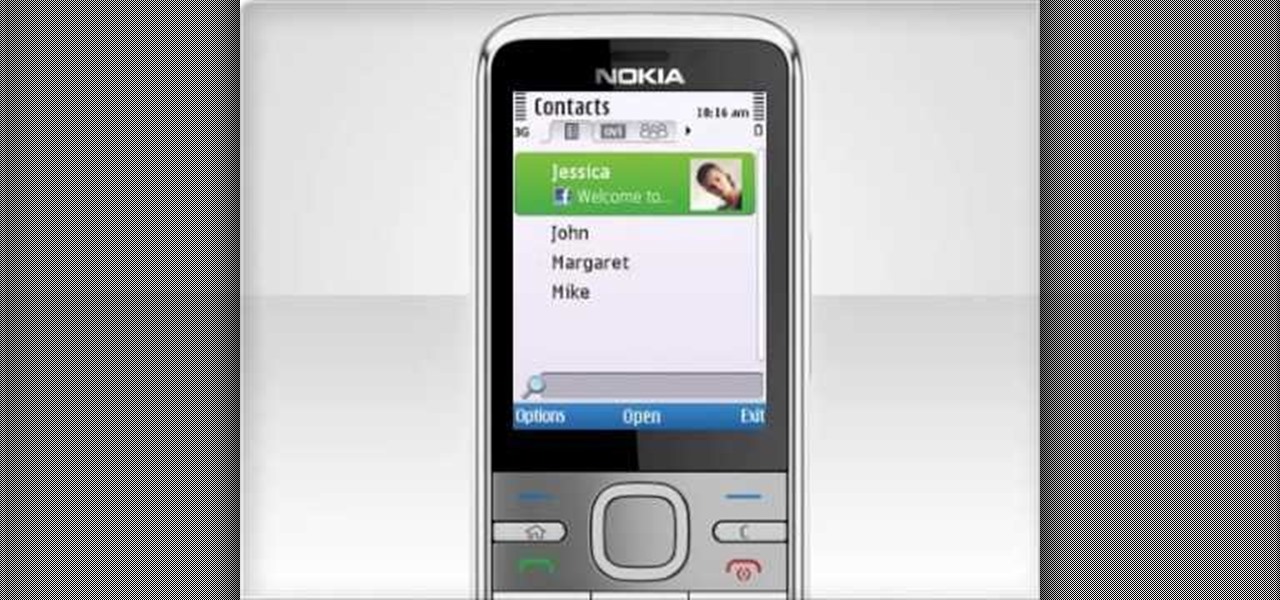
Learn how to upload pictures to social networking services. It's easy and this clip will teach you everything you need to know. For all of the details, including complete, step-by-step instructions, watch this brief, official C6-01 owner's guide from the folks at Nokia!

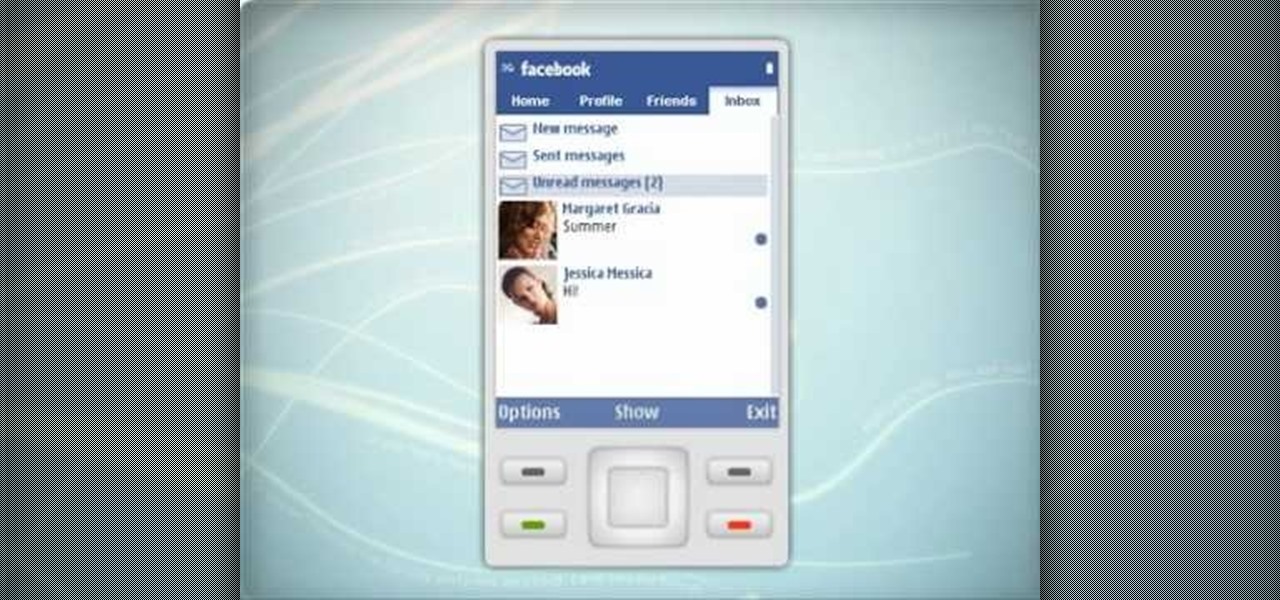
In this video, we learn how to use the Nokia C5's social networking features to read, open and respond to Facebook messages. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

In this clip, we learn how to use the Nokia C5's social networking feature. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

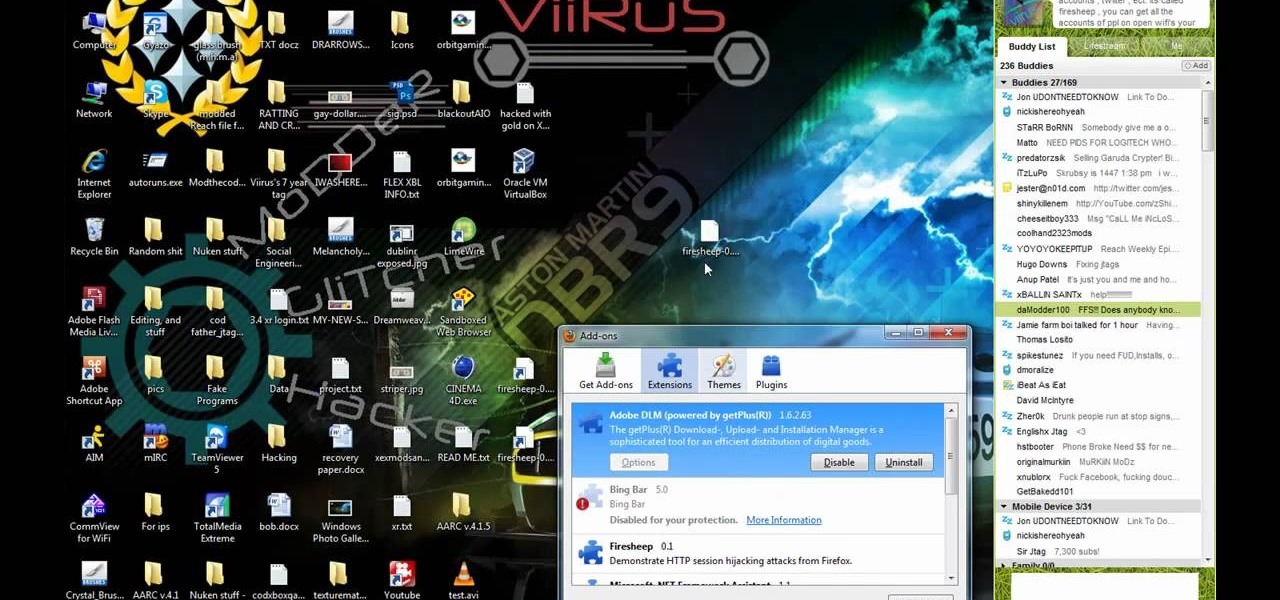
Ever wanted to hack your friends' Facebook accounts? With the Firesheep Mozilla Firefox browser add-on, it's easier than ever. Before you can use Firesheep to sniff account cookies, however, you'll need to download and install it. This clip will teach you everything you'll need to know.

Firesheep! It's a good reason to be cautious when using public Wi-Fi. But is it reason to stay off of open networks altogether? Certainly not! There are, in fact, a few simple steps you can take that will make you invulnerable to the malicious Firesheep Firefox addon. Learn how to protect yourself against Firesheep with this video guide.

You can view Flash content on your iPad without having to jailbreak it by using a VNC (virtual network computing) app. You can't zoom, and there is no audio capability, but you can otherwise view Flash content on the web through your iPad.

Send a text message to a landline? You can! If you're on a Verizon or Sprint network, you can write the text message and include the landline number. This will convert your text to a voicemail, and ask for approval before sending.

Make a custom background for your Facebook, MySpace or YouTube profile using the Fireworks software! This tutorial, using the YouTube layout, shows you how to create a little extra personalization for your profile. Keep screen size and your file limitations in mind as you create your image!

Business cards are one of the most effective ways of networking with professionals, and making good ones without breaking the bank is hard to figure. This video will show you how to make your own professional looking business cards at home and use them to improve your career.

Did you know you can connect to your computer from wherever you are? This video teaches you how to set up a remote access network, whether you're using Microsoft Windows on a PC or Mac OS on an Apple. Now you can do your work from anywhere, no matter how far away!

Want to get involved with the information superhighway? E-mail is the best technology to stay connected with friends and family. Use these tips to create your own email account in Gmail, MSN or Yahoo! mail. Keep track of addresses, improve your networking and learn the basics of instant messaging.

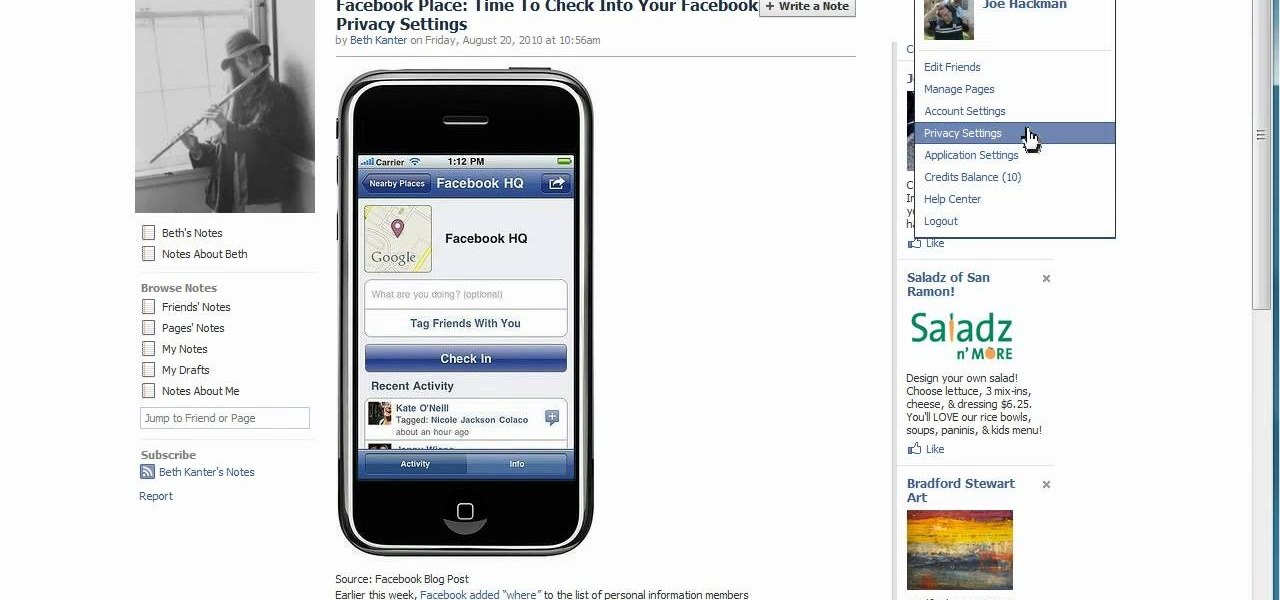
Underwhelmed by Facebook's new Places geo-tracking feature? Disable it. It's easy. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to deal with the Places feature, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

In this quick clip, you'll learn how to disable Facebook's location-tracking "feature," Places. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to deal with the Places feature, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll see how to change your privacy settings to turn Facebook's geo-tracking feature, Places, either on or off. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to deal with the Places feature, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

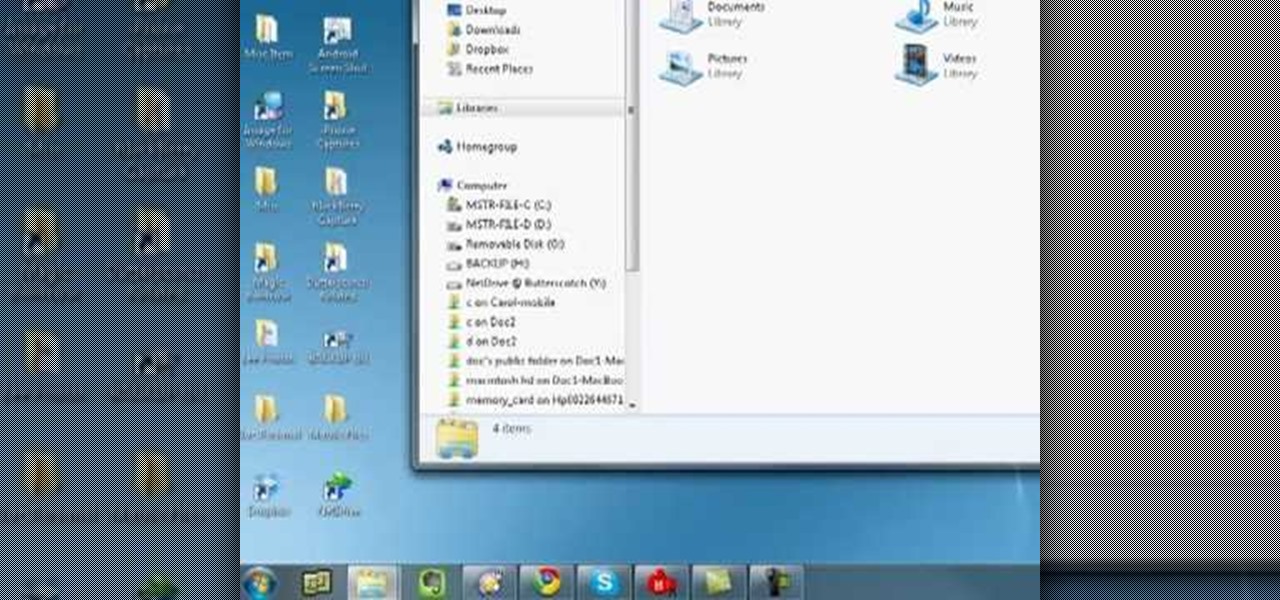
In this clip, you'll learn how to use the Home Group networking feature of Microsoft Windows 7 to easily share files and folders between two or more computers. This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started sharing files across your own Home Group, take a look.