This video tutorial is going to show you how to steady your shots with a homemade fig rig. The camera is mounted right in the middle of the top bar and it uses the iron as the balancing mechanism. The official fig rig is about $300. But, the one shown in the video will cost you around $10. Cut a PVC pipe about 2 feet in length and glue on two T joints on either end parallel to each other. Now fix the two feet into the T joints as shown in the video. The larger the camera, the longer will be t...

This video illustrates the transfer of paper patterns on woodworking projects with Lowe's. If you have a pattern in a piece of paper for the woodworking project. Draw the grid for the pattern in a piece of paper. Even though, the piece of wood is six times larger than the pattern in paper. Draw the grid in the wood with One and half inches by the use of ruler. Then check out each and every box of grid in a pattern, trace the shape of each boxes in the wood. After finishing all the grid boxes ...

This video instructs you on how to draw angles in geometry. The instructor begins by showing you 4 example angles you can create. He then draws a straight line that can be linked to any of the other four angles. The first example of an angle shown is 180 degrees. He draws a line at 50 degrees and then he continues to draw a 90 degree angle. The instructor varies whether he uses the left or right side of the protractor. He ended by noting some angles will be larger than the protractor.

A great and easy to do trick. You can cut out a small hole and by bending the paper just right you can fit a much larger coin through it. This "large coin, small hole" bar trick is a great way to win money, beer or even just to impress the best.

This video shows you how to make your very own water filter. 1. 20mm PVC pipe for upper section larger debris.

First, draw a medium sized circle. Then, draw a triangle on top of the circle, with the top of the circle acting as the bottom of the triangle. Next, draw two half circles on the sides of the triangle. After that, draw two small shaded circles inside the medium sized circle. Then, draw two lines above the shaded circles. Next, draw a line at the top of the triangle. After that, make two short lines with triangles on top of them. Then, draw a square touching the underside of the medium sized c...

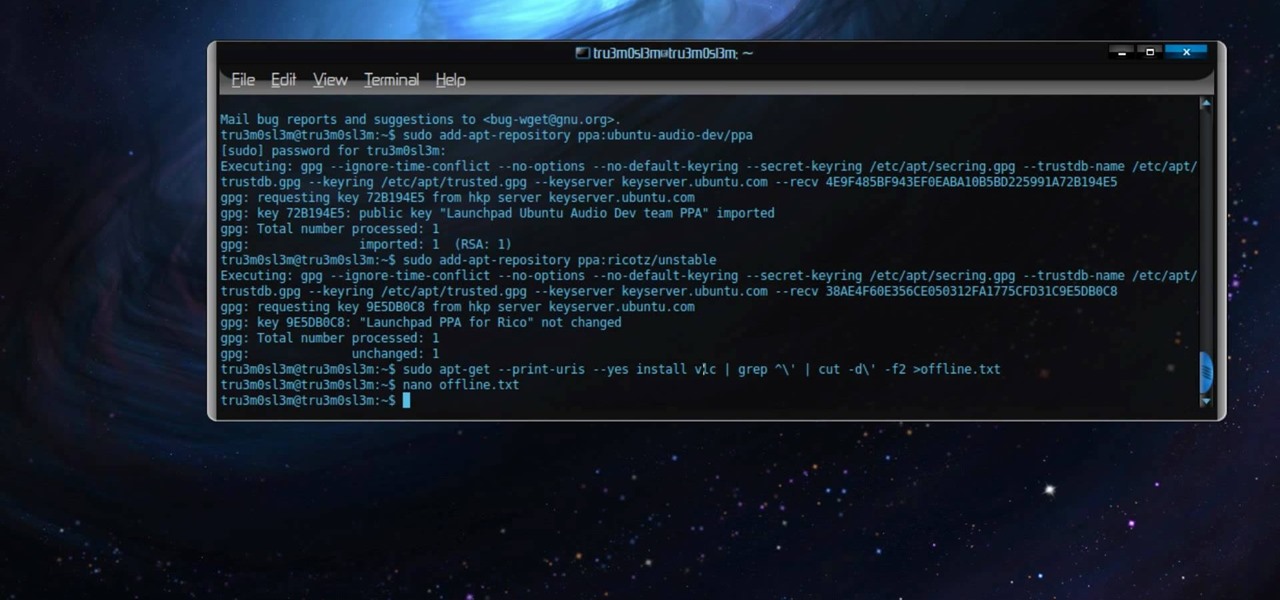
Permanent access to the internet might not always be possible for you and your Linux system, and this computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to offline package install and update on Ubuntu Linux.

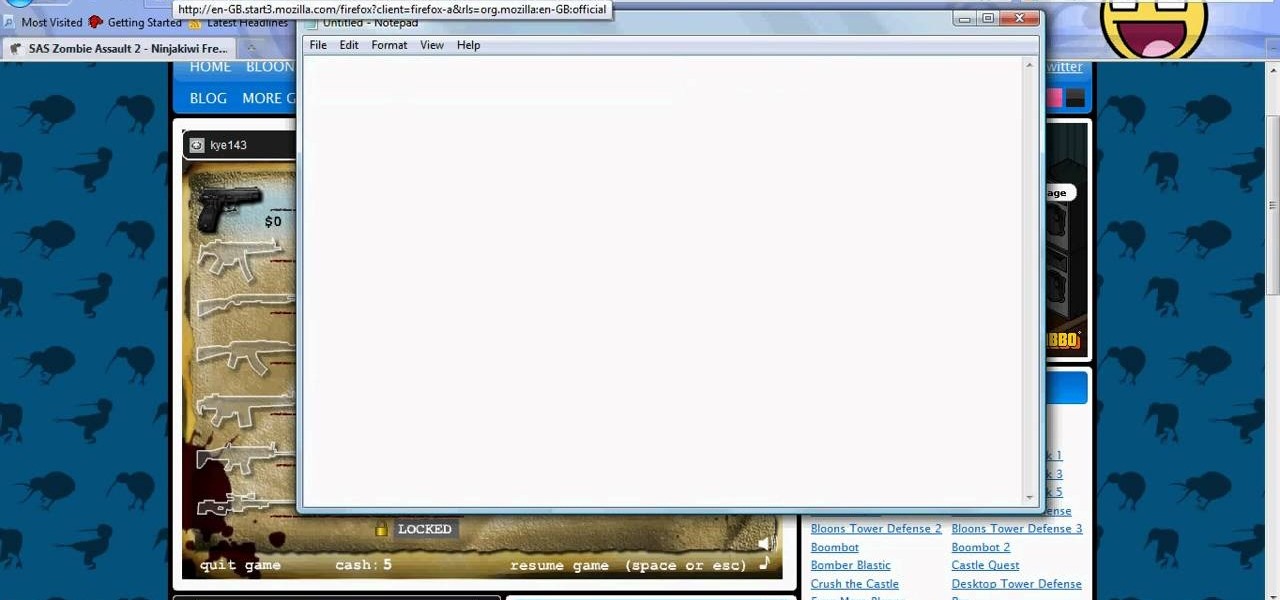
SAS: Zombie Assault 2 is flash game from Ninja Kiwi. Learn how to hack Zombie Assault 2 with tricks and cheats. Watch this video tutorial to learn how to hack Zombie Assault 2 with Cheat Engine (09/13/09).

Need a way to convert your scanned documents back into text files? Check out this video tutorial on how to convert scanned documents (JPG, PDF) to text.

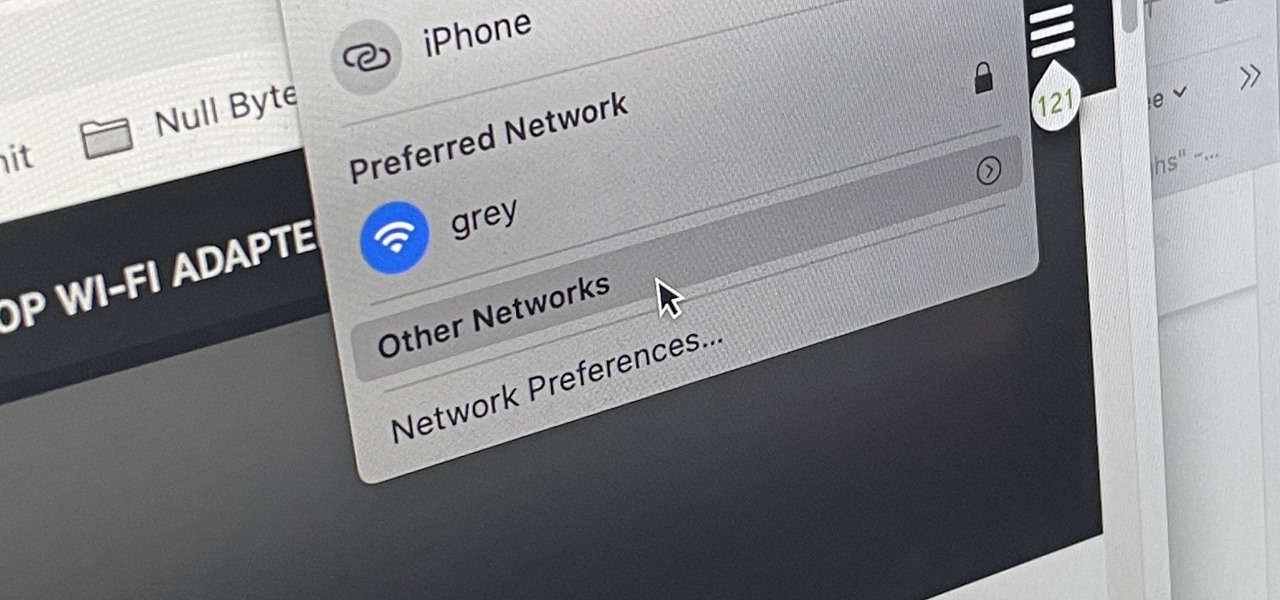
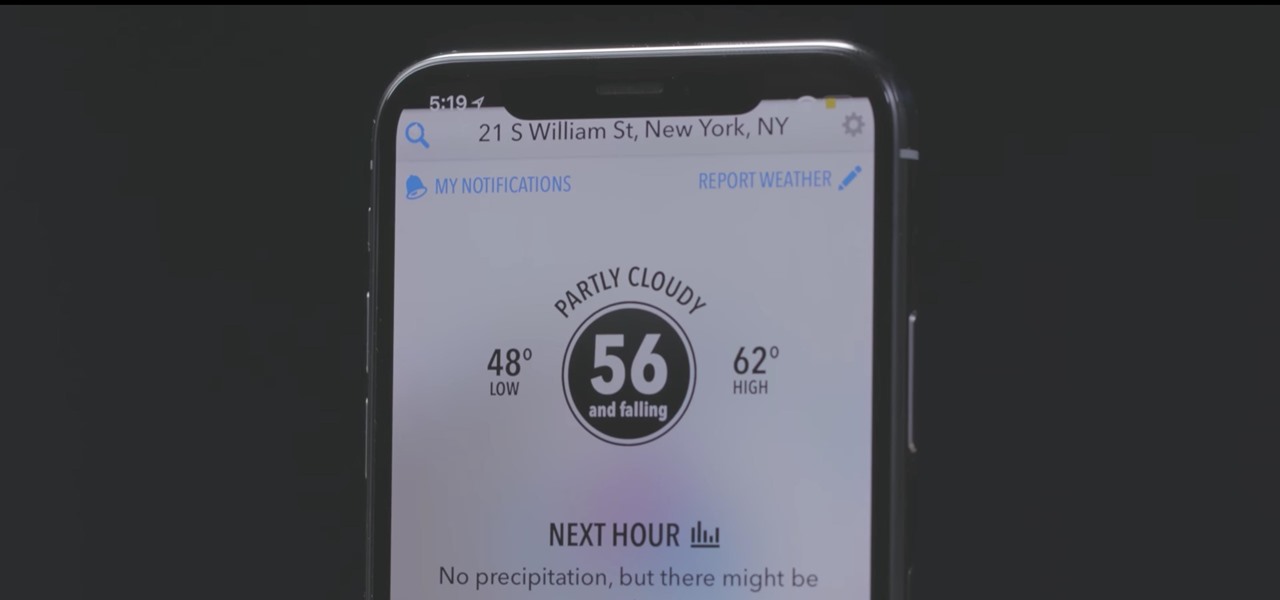
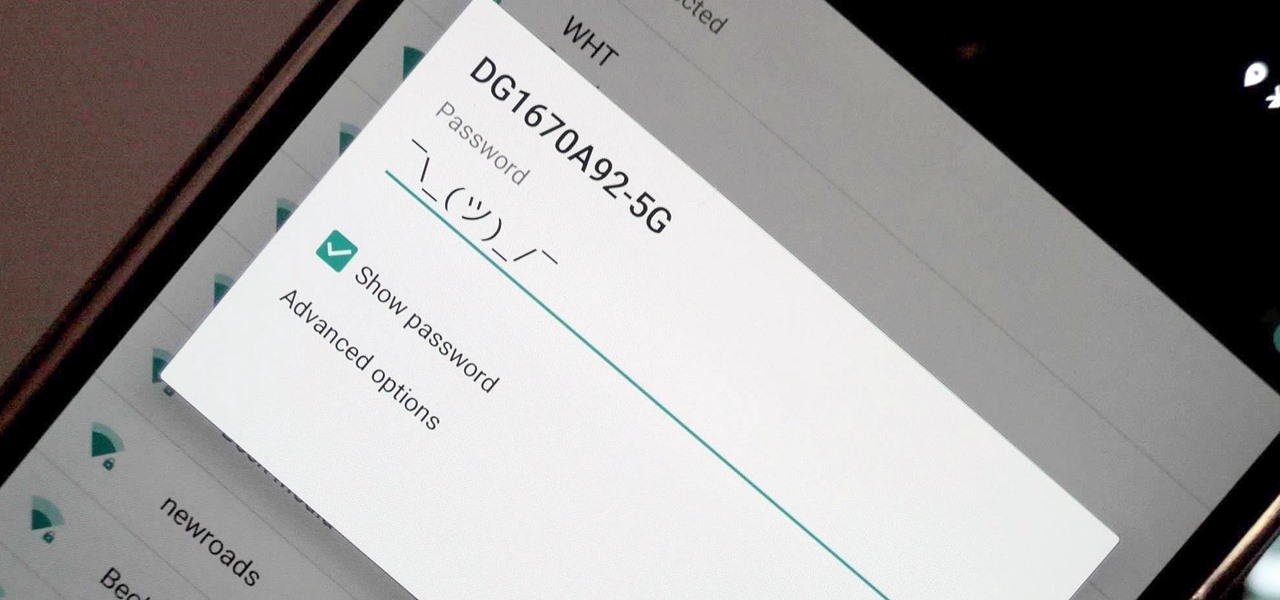
In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.

There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

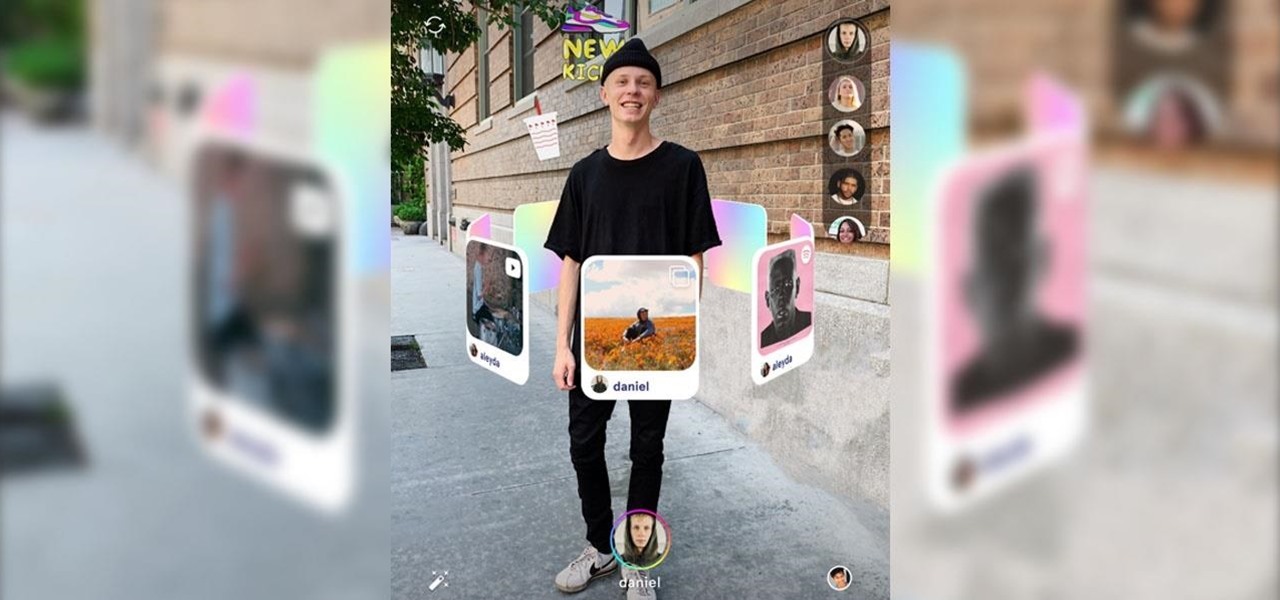
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

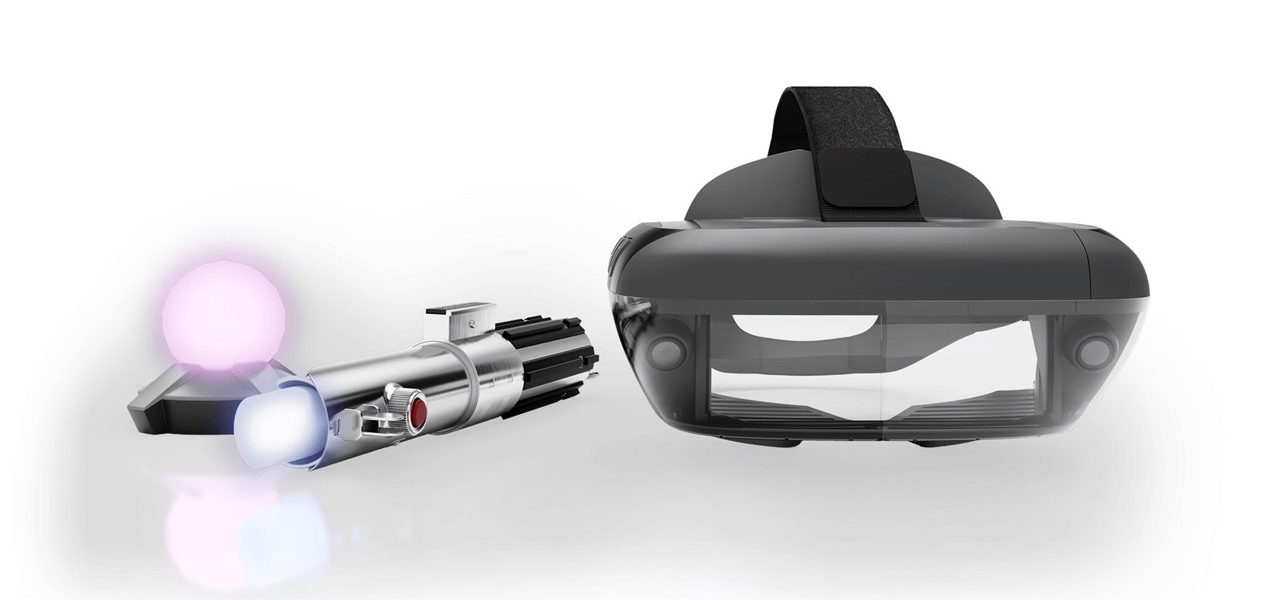
While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

News junkies who own the Magic Leap One received some good news on Thursday, as CNN has published an app for the headset to display the network's news coverage in augmented reality.

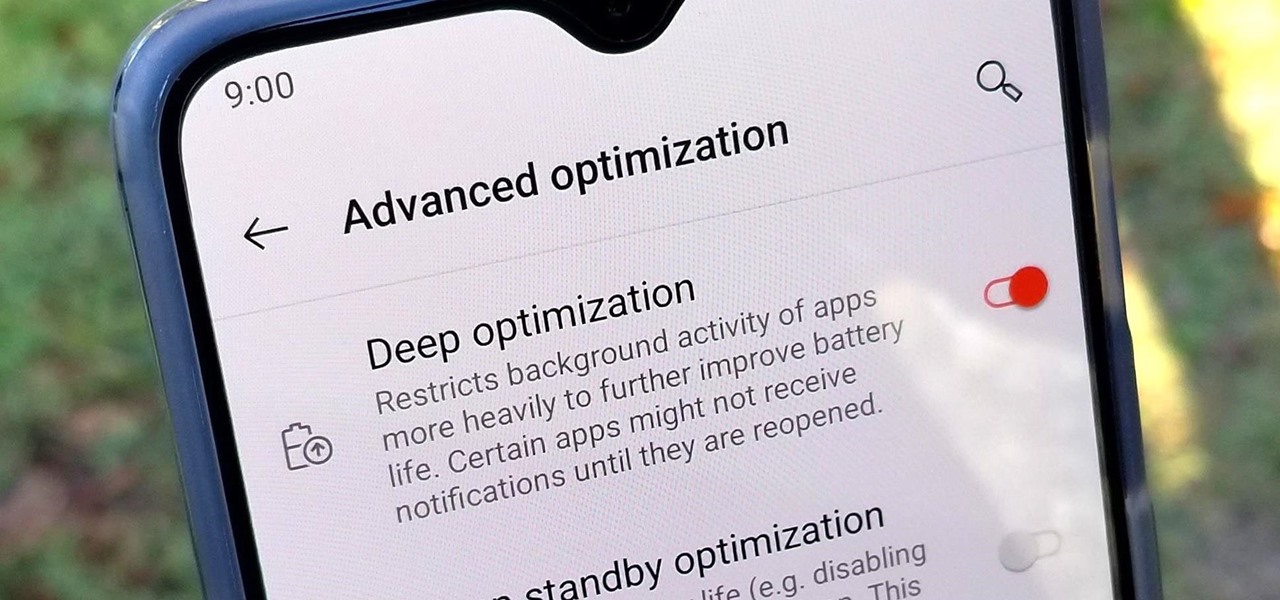
OnePlus is known for pushing the boundaries of what we thought was possible for a mid-range price. One of the best things about OnePlus phones is that their battery life is fantastic in general, but to achieve this, Oxygen OS will disable or delay notifications by default once your phone goes into deep sleep mode. You will not be notified until you wake the phone up — this could be an issue for some.

If you've gone anywhere near a television in the US in the last 48 hours, you've probably seen some of the reports of Hurricane Florence and its devastating wind and rain making its way toward the Carolina coast.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

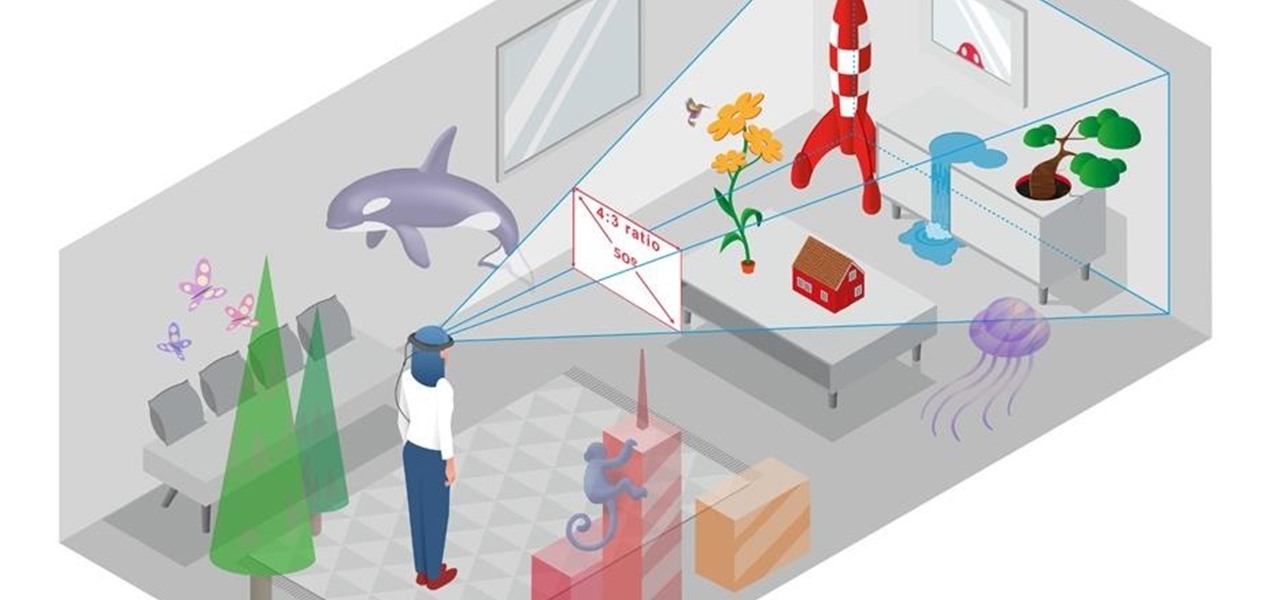
In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

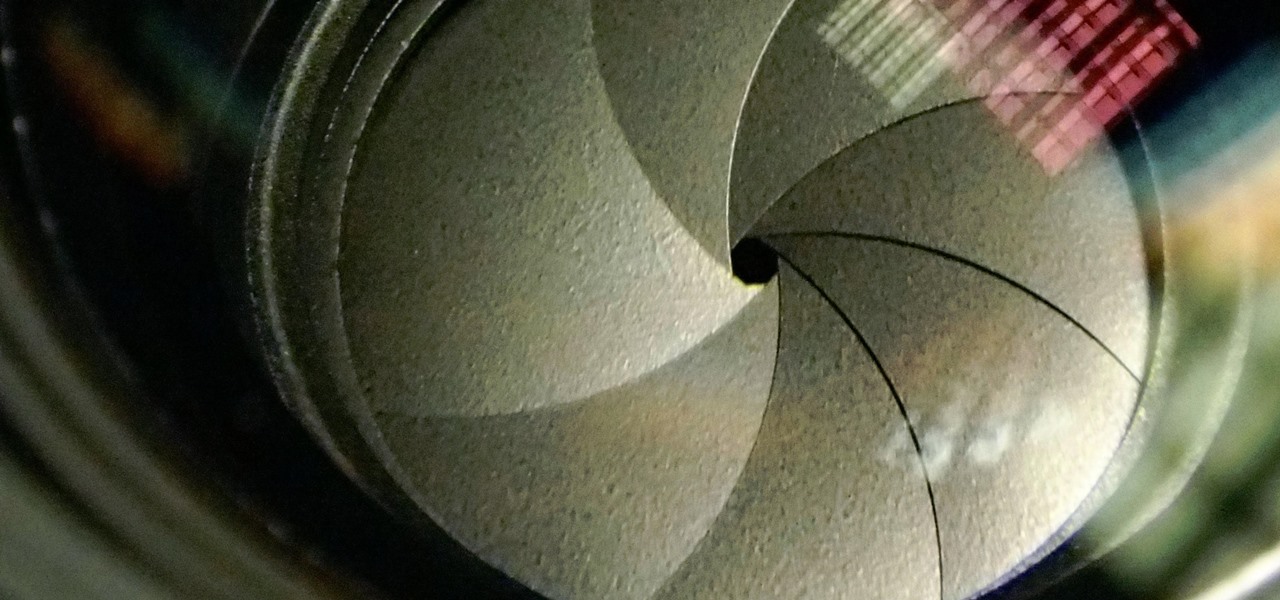
The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.

The iPhone X's "notch" is now possibly as notorious as Apple's decision to cut ties with the headphone jack. With that said, a cautious consensus can be made from first impressions of the X that the notch isn't all that bad. Still, one problem has shown up in reviews again and again — apps are not optimized to fit the notch.

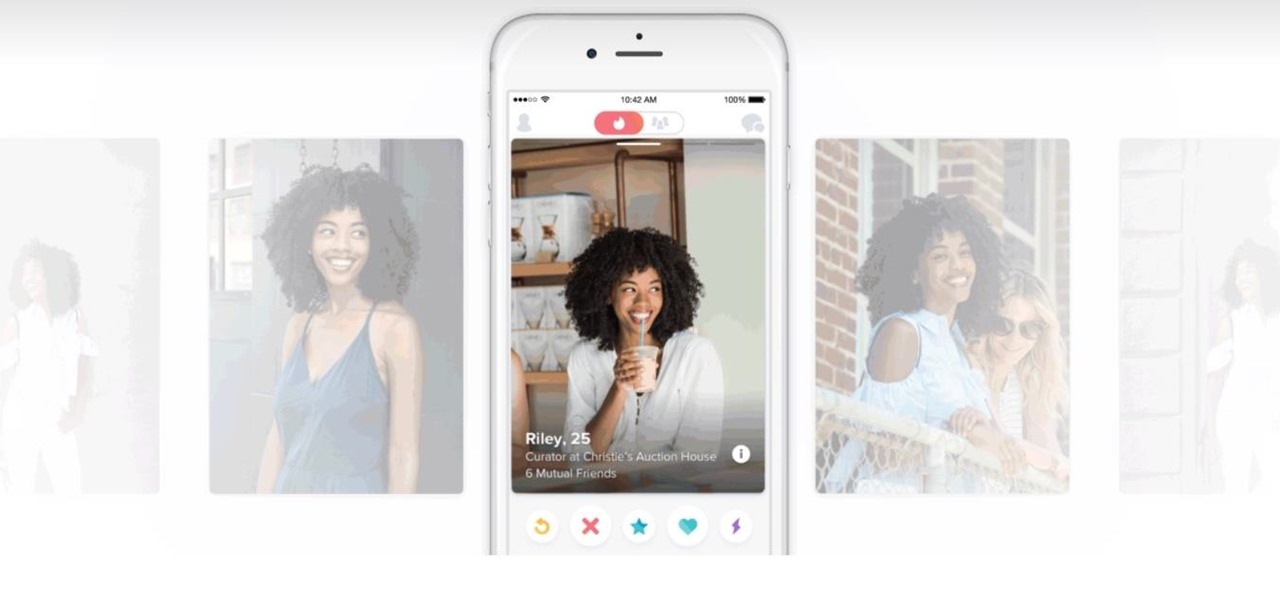
If we're being honest, very few people go on Tinder to fall in love with someone's personality. Oftentimes, the only reason they'll look at your bio is to make sure there are no red flags.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Imagine if you combined Tasker with your favorite live wallpaper—that's roughly the gist of a new app from developer feedK. With this one installed, your home screen background will finally be aware of its surroundings.

One of the biggest causes of smartphone battery drain is the mobile data connection—particularly if you live in an area with poor reception. But, chances are, you don't actually need this connection most of the time, because you're probably connected to Wi-Fi for a good chunk of the day, which uses far less battery life.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

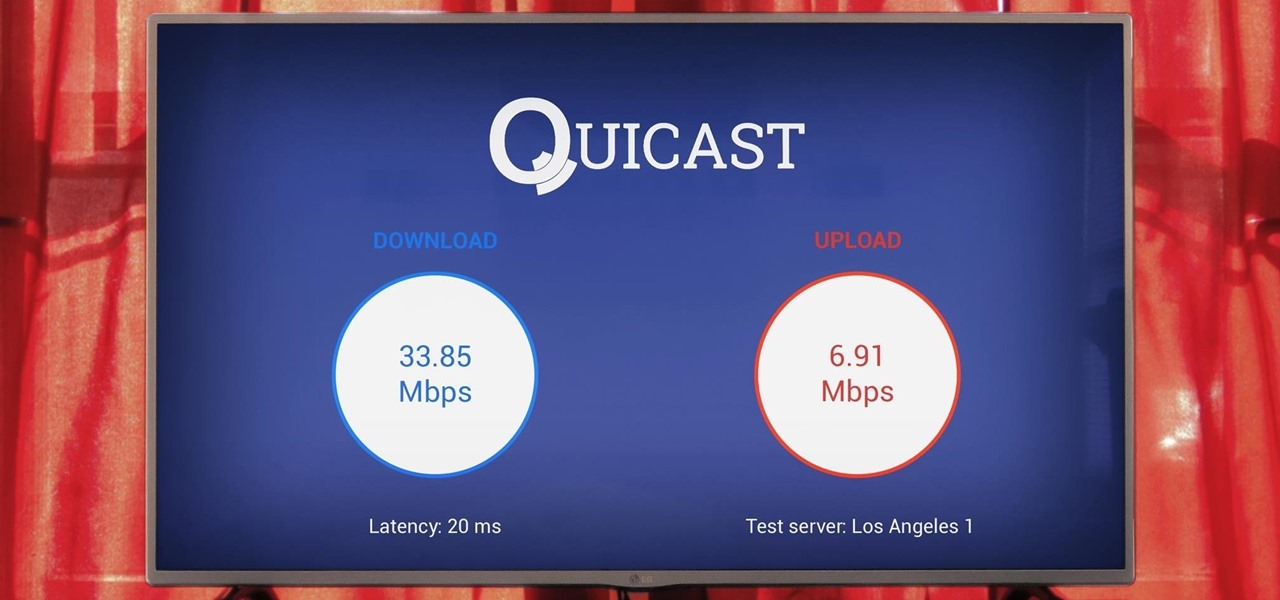
The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.