Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.
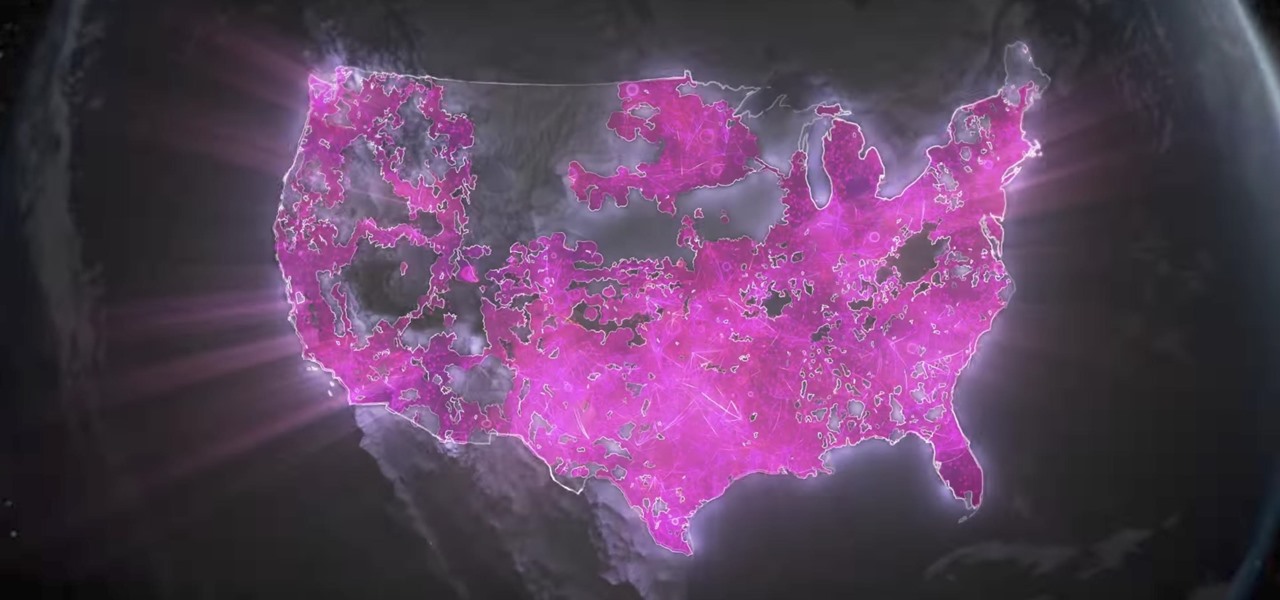
Last month, AT&T made headlines with its disastrous launch of its 5G Evolution network (spoiler alert: it wasn't actually 5G). T-Mobile responded to the embarrassing news by saying the company would be working on its own 5G network, and would take its time rolling it out. Well, T-Mobile may have just pulled an AT&T — T-Mobile is launching LTE-U in the US, and things seem pretty similar to the 5G Evolution's introduction.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.
The widget system on iOS leaves a lot to be desired when compared to Android's offering, but that's not really Apple's fault. The system is there, we just need some good widgets to really get the most out of it, so it's up to developers to create some awesome apps that work with the home screen and lock screen widget panels on iPhone, iPad, and iPod touch.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

This easy "recipe" requires just two ingredients: popcorn and caramel bits. Caramel bits are made for melting, and they take all the work out of making caramel-based anything. If you've ever made caramel before, the result is delicious, but it's often hot and sticky work—in most cases.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

As one of the most frequently used and popular applications available, Facebook is now attempting to be a little more considerate for those Android users that don't have a bleeding-edge device or fast data connections.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

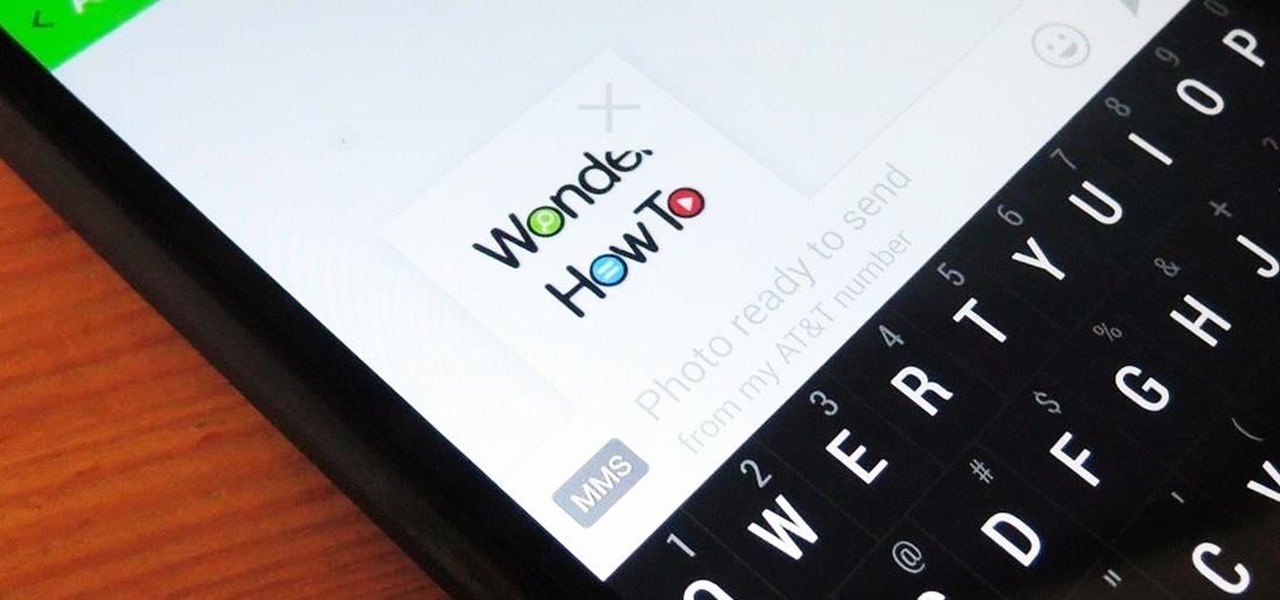
Whenever a picture is sent via MMS, a certain amount of compression needs to be done in order for a carrier's network to send it. That compression is meant to ease strain on the network, but in the end it leads to heavy downsizing and increased graininess in pictures.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

If you ever wanted to communicate with friends without having to deal with those pesky essentials like words and phrases, have no fear, Emoj.li is here!

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

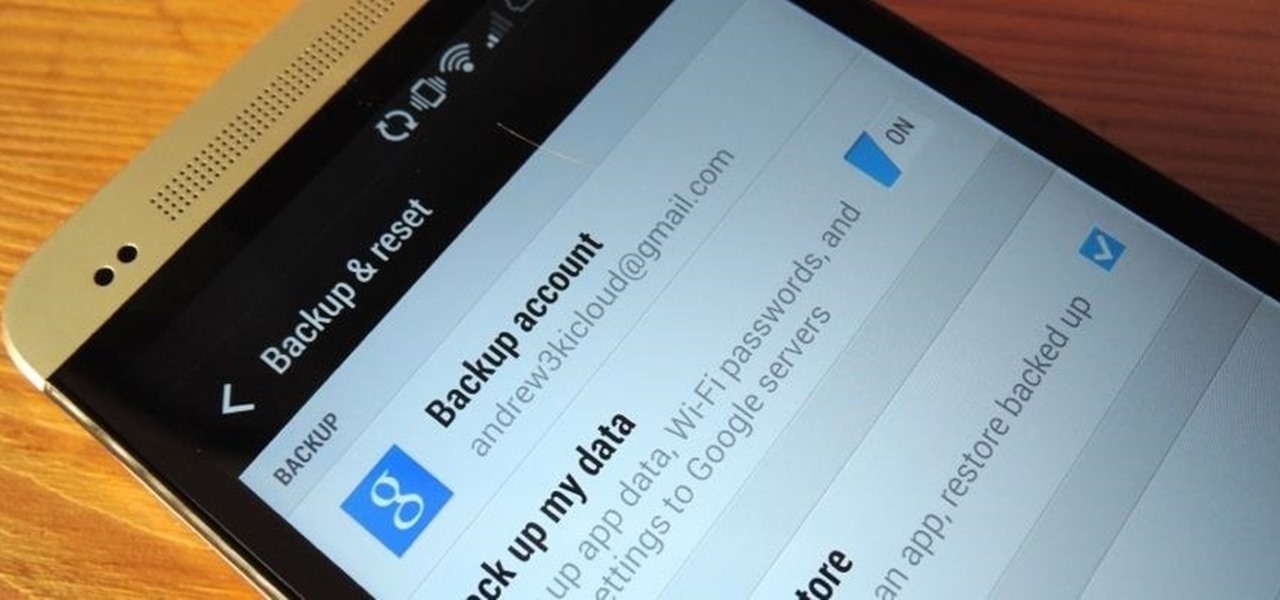
If you are using the the AT&T variant of the HTC One, you are well aware that the carrier opted not have the HTC Backup app pre-installed on the device. Luckily for us, HTC said "screw it" and put the app on Google Play, allowing anyone with an HTC One, regardless of carrier, to be able to download and use the app—if you're an AT&T customer, grab the app and let's take a quick walkthrough (again, the rest of us on other carriers should have the app already).

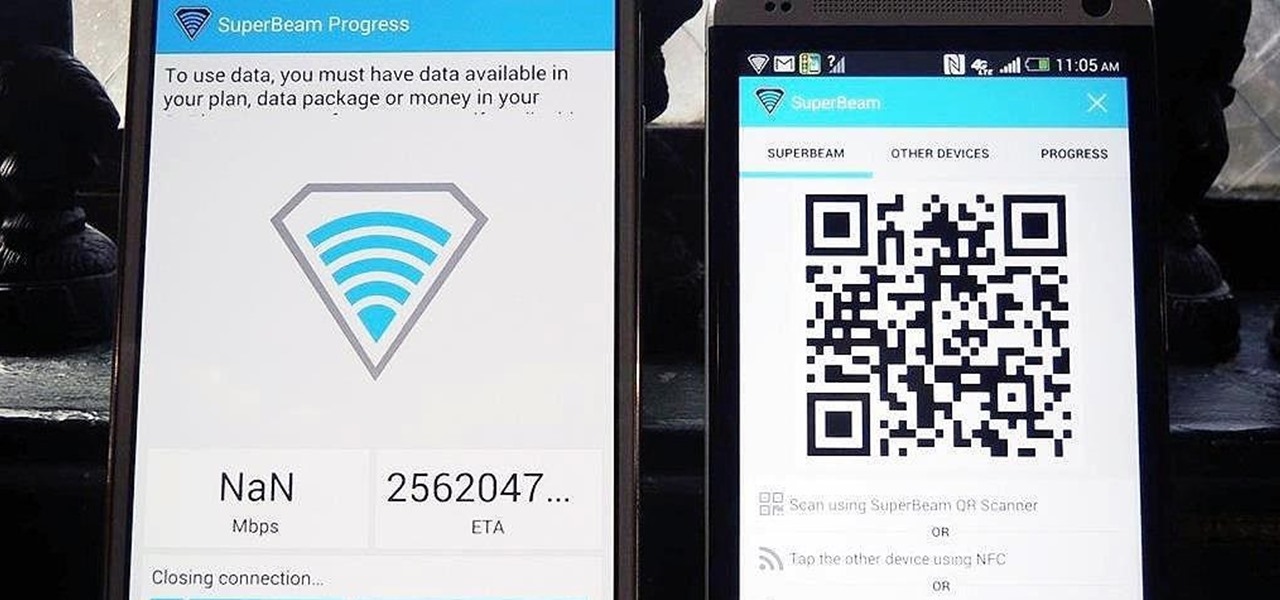
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

If you're like me, then you were a little disappointed after updating your Nexus 7 to KitKat and realizing that not much has changed. The old Jelly Bean look still occupied your home screen, and there wasn't really anything noticeably new overall. All of that waiting and anticipation only to be left high and dry.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Drilling holes in wall tiles is a fairly easy skill to master once you know how. Follow these simple steps on how to drill a hole in a tiled wall for a hassle free experience.

It doesn't really matter what kind of cell phone you have—battery life is one of the most important features for any electronic device. We've written tons of articles on how to get better battery life from your Android, iPhone, Kindle, and more, but we've never really covered Windows Phones before—until now. The Nokia Lumia 920 and other devices running Windows Phone 8 suffer from battery problems just like any other mobile device. So, if you've got one in your hands that can't seem to make i...

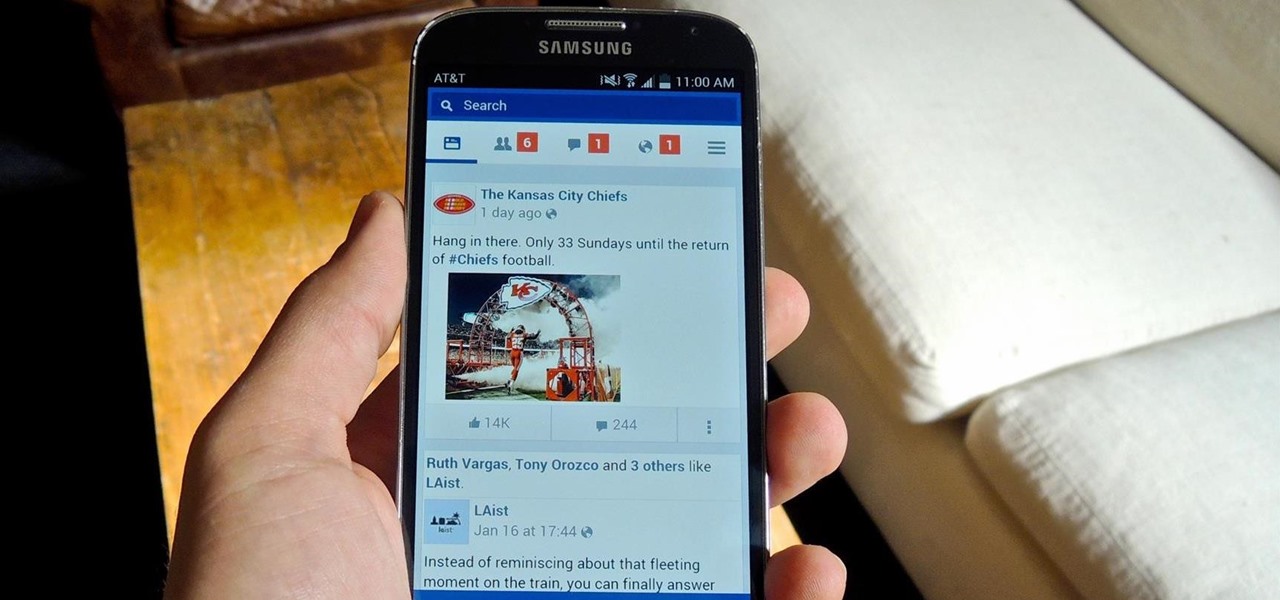
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

There are plenty of ways to speed up your wireless network at home, some as simple as changing the placement of your router. While you can always buy equipment to boost your signal, there are plenty of cheap or free DIY solutions you can try as well.

Android devices are known for their USB and Wi-Fi tethering abilities—rooted or unrooted—which comes in handy for those that travel and need internet on their laptops in areas that don't have any Wi-Fi networks available, but have a strong cellular signal.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

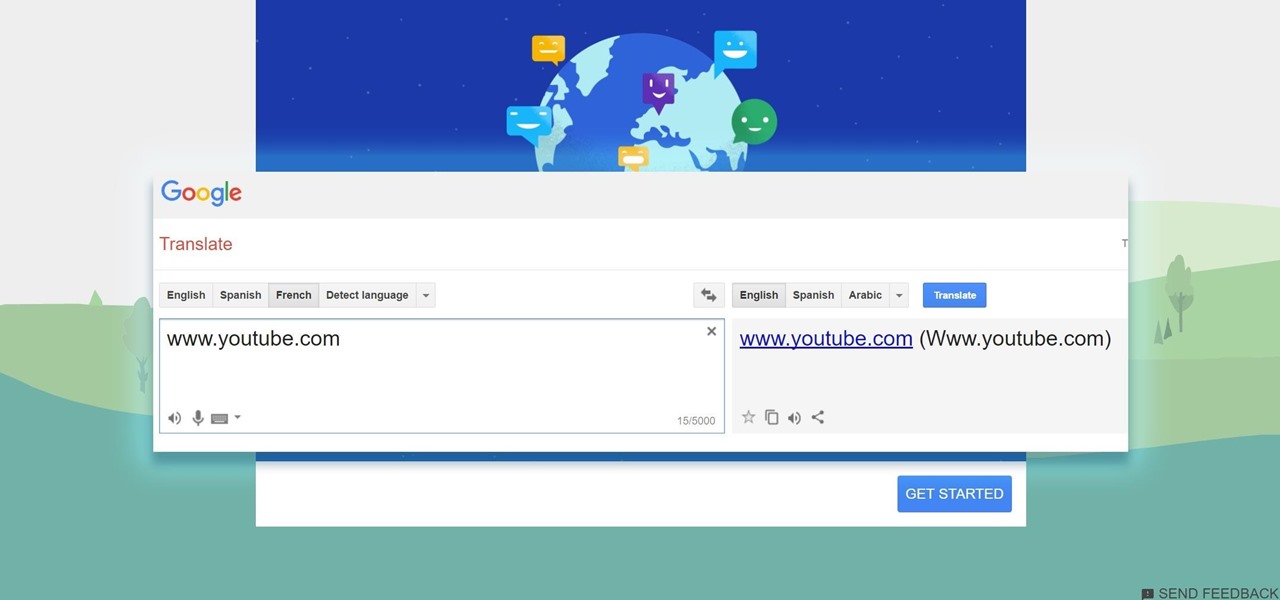
Need to break out of the restrictions your school or workplace have on internet browsing? Maybe you want to waste some time on YouTube, check out some gaming action on Twitch, or simply just browse Facebook or Twitter.