QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Rumors are swirling today that NASA's Jet Propulsion Laboratory (JPL) may have shown us the first public glimpse of the next-generation HoloLens. Are they real? Or just a prototype? We've been digging in all day to find the answers.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

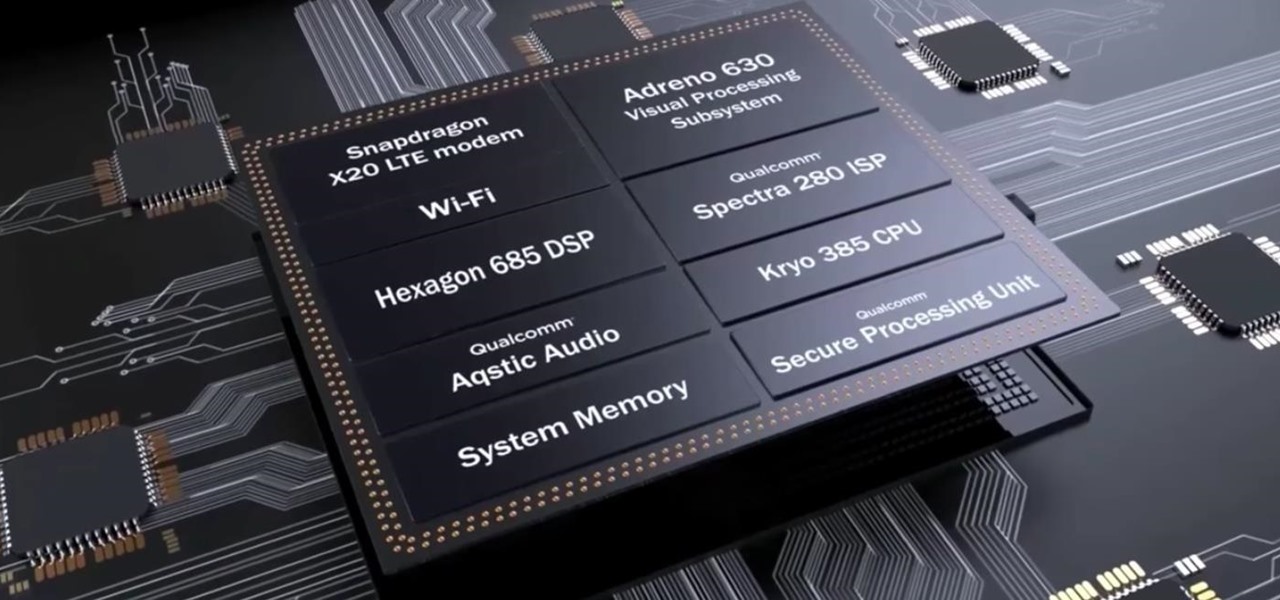
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Innovation Congress starts tomorrow, but its creator, Jason Keath, spoke to Next Reality today about the future of augmented reality.

Chromecast comes to mind when "casting" video from a smartphone to a big screen television, but it's not the only way to "cast" streaming content. This is especially true for Netflix, where you can cast movies and TV shows to not only a Chromecast-enabled TV, but to smart TVs, video game consoles, and other streaming media players so that you have complete control right from your smartphone.

Waymo revealed more clues about its future business model after it said yesterday it plans to kill its Firefly pod-like car project and focus more closely on offering driverless systems for commercially available car and truck models.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

The internet was blowing up recently over this mind-blowing, mouth-watering video of a woman making a cake decoration out of… wait for it… chocolate bubble wrap. Yes, that's right: she turned the ubiquitous packing material into the mold for an absolutely gorgeous cake embellishment that, deservedly, went viral. You can watch the video below.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...
Welcome back Hackers\Newbies!

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

Portrait drawings are difficult for most artists, but one thing's for sure— drawing nerds is as easy as they come. Nerds are easier to draw because you can stray from the formality of portraits, putting your own spin on it, over-compensating the details, exaggerating the dorky features. It's a drawing class in its own, and Merrill shows you how to draw his version of the NERD!

In this video from TheCurrentCustom she teaches how to enhance your breasts. First she says you need to measure your breasts to figure out the right kind of bra for you. Take the measuring tape below your bust, and wrap around back, and then measure right above your bust. Round down to the nearest even number if you get an odd number. Then measure your bust size by wrapping the tape measure around the largest part of your bust, typically where your nipples are. Then subtract the bust size fro...

Okay, so you're fishing and you forget the basic essentials… you're fishing pole and your bobber. How are you going to catch a fish with just some fishing line? The answer? Plastic straw.

If you prefer glow sticks over candles during a power outage, then this how-to is for you! Although glow sticks are used as temporary light sources, there are other applications for them. Divers use them for night diving, fisherman use them to catch swordfish, and the military uses them for light markers, along with infrared versions used in conjunction with night vision devices. But with all these handy uses for glow sticks, the most popular is — recreational use, like dancing at raves, some...