Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

There was big news today from Google, Apple, Volvo, and Nvidia regarding their self-driving efforts.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Anticipation is building for the release of the Essential Phone. Andy Rubin's newest creation is expected to be loaded with features like a rear fingerprint reader, attachable 360-degree camera, and an edge-to-edge display. However, a news release from Sprint has just revealed that it may take more than $700 to get your hands on the Essential Phone. The release revealed that the Essential Phone will be exclusively carried by Sprint, so it might be time to switch your wireless carrier.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

The Samsung Galaxy S8+ isn't yet available for consumers to buy, but that isn't stopping tech reviewers from discovering what the phone is capable of. Turns out, the S8+ has a good battery—just not as good as the iPhone 7 Plus.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

Bats are an important part of the US economy. They devour metric tons of bugs every night that would otherwise ravage crops and also be generally disgusting-looking and make you itchy. But they're in danger from a nasty fungal infection called white-nose syndrome, which has just popped up in Texas and has been spreading across the country.

Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

Most augmented/mixed reality hardware still exists in the development stage, whether that's one of the more robust headsets or a high-powered smartphone. Most everything else isn't widely used or monetized. Snapchat, however, snuck in under the radar and created the foundation for the first social network to focus on augmented reality.

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

When it comes time to buy a new smartphone, the sheer amount of options on the market can make you feel overwhelmed. There are Android devices of all shapes and sizes with different functionalities and price points, and now, even Apple has three unique iPhone models to fit various budgets.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Hello again, ***UPDATE: Adding links to the other Two articles****

Back in August, Google unveiled a new YouTube Gaming service meant to compete with e-sports streaming sites like Twitch. At its launch, the service was capable of broadcasting desktop PC gameplay, but when it came to the mobile segment, users were only capable of viewing streams hosted by others.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

The horizontal dotted icon in your iPhone's status bar serves as an indicator of your device's network strength. And while it does help provide an approximation of how strong your signal is, swapping it out to display an actual numeric value is a lot more precise and can change up the look of your iPhone (or at least the status bar). The process is quick, painless, and you don't even need to jailbreak your phone.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Do you have a major mosquito problem? Well, here's a solution used by the military to drastically cut down their numbers.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

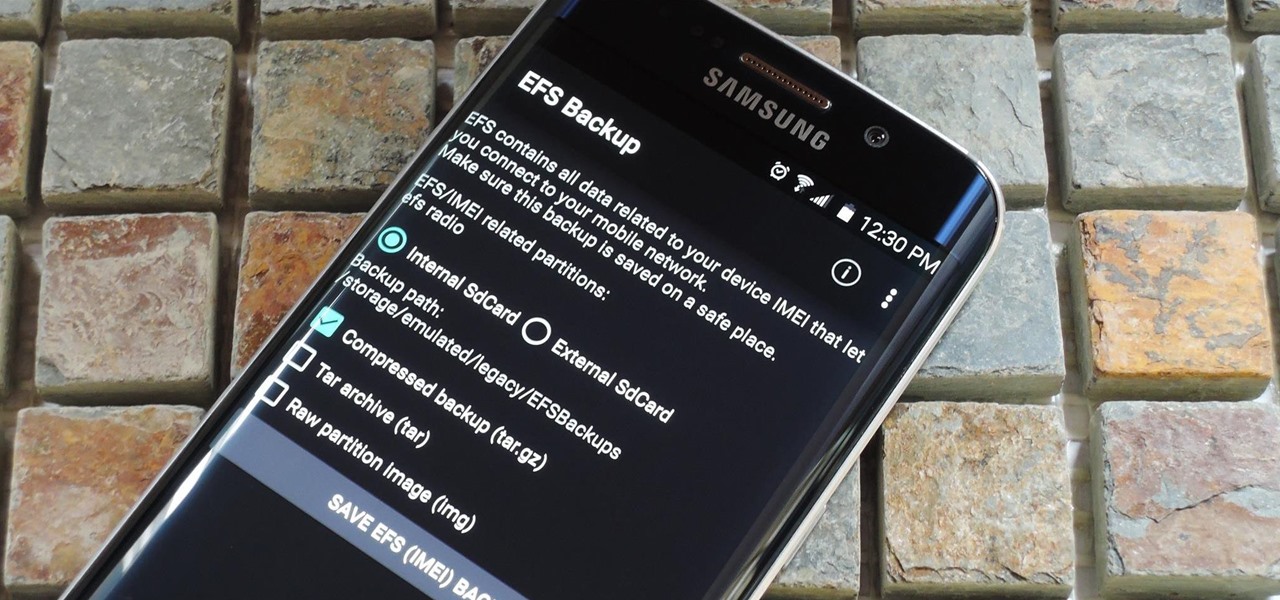
The EFS partition on modern Android phones houses the unique IMEI for your device, which is essentially an identification number that lets you connect to mobile networks. But sometimes, when you're flashing ROMs or restoring backups in custom recovery, the EFS partition can become corrupted, which will prevent your phone from connecting to any type of mobile network.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

When Apple released their plus-sized iPhone 6 and 6 Plus models, it only made sense that they would include a one-handed feature to accommodate the larger displays. That particular feature is called Reachability, and with just a quick double-tap of the Home button, the screen shifts to the bottom half of the device for easier use with one hand.

Those of us with girlfriends understand that in order for the relationship to run smoothly, you have to keep your woman happy and let her know that you're thinking of her—even when you're not.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

So you've decided to transform your drab backyard into a Japanese Zen garden. You've made the right choice. Yes, tire swings and crab grass can slowly kill the soul. That being said, a bit of planning lies ahead. This article offers a list of How To tips, culled from the Landscape Network and other professional Japanese style landscapers, for planning an effective Japanese style landscape in your home. Step 1: Research.