
How To: Graft Lophophora peyote onto the scion plant
How to graft Lophophora The materials to be used:-


How to graft Lophophora The materials to be used:-

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

This is how my version of an origami Christmas tree turned out based on the instructions I posted awhile back. Cory also made a version from white glossy paper, which looks great. I opted for the green and brown look, but it wasn't easy.

Connecting your Nokia N900 smartphone to a wireless hotspot or your home wifi network is just a few quick taps away! Take a look at this tech support video from Nokia that will tell you exactly where to find the available internet connections on the phone and select the one you wish to connect to.

Fring is a free app available from the Apple store which will allow you to use video chat, Skype or AIM on your iPhone 4 over a 3G network. This tutorial demonstrates how to use the app with your iPhone to make video calls.

In this how to video, you will learn how to use the Nerf Gun Long Shot. First, you will need to know about the magazine. These can hold 8 shots and are spring loaded. Do not load 8 shots, as it will jam. Instead, load 6 shots to prevent this. The shots can be used in other guns, but the Long Shot magazine can only use this shots. The holes in the shots make a whistling sound. If you get shot, you will feel it regardless of distance. The gun has a trigger, a mount, a quick grab design, a hidde...

Family Fun Video demonstrates how to make a leprechaun craft project. To make the leprechaun, you'll need a small paintbrush, a ruler, green craft foam, green paint, pink paint and a skin tone acrylic paint, a black permanent marker, tacky glue, a toilet paper glue, a decorative button and four brown pipe cleaners. Trace a circle onto craft foam with the toilet paper tube and make a larger circle for the hat brim. Cut them out and set them aside. Paint the tube green and then add face, hands,...

You don't need a fancy panini press to make a good panini! Check out this video for tips on how to make yummy grilled sandwiches using items you already have in your kitchen. Save time and money with this method!

You've had pumpkin bags and you've had ghost bags, now you can have a Halloween colored duct tape bag to collect candy in this year. This bag is fun to use and just as much fun to make. Plus, by adding some reflective tape your bag will help keep you safe.

Take a pumpkin that is round and not oblong, to make the arrangement look its best. Cut the pumpkin strait across at the top, below the stem but far enough down so you have a wide opening. Clean all the seeds out and guts in pumpkin so that the pumpkin will not decompose. Cut your floral foam piece to fit snugly inside the pumpkin so it won't move. Take it out, and soak it for a few minutes in water so it will absorb lots of water. Choose fresh flowers that would look nicely in pumpkin arrang...
Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

Iknitwithcatfur teaches viewers how to knit perfect garter eyelets. Choose worsted, double-knit (DK) or sport weight yarn. A cotton or wool blend without fancy textures is the easiest to work with for this pattern. Use slightly larger needles to show off the pattern's open work. Size nine to 11, depending on the yarn weight you've chosen, is ideal. Cast on 25 stitches for a good-sized swatch. The garter eyelet pattern requires an odd number across and you work it over six rows. Knit the first...

Learn to make sodium metal with this great video tutorial. Be sure to use latex gloves in the process, as the chemicals can be hazardous. This should not be performed by an inexperienced chemist.

Want to supply your head with a little extra jazz factor? Why not tie a scarf around it? You have only one head, but any number of ways to decorate it with a scarf.

Looking to spruce up your living room or bedroom? Learn to combine a vivid imagination with good paint sense to choose the right colors for your walls and feel good about your surroundings.

Are you the one scraping sticky marshmallowed yams and congealed gravy off the dishes every Thanksgiving? Shame someone else into doing it this year. Avoid doing the Thanksgiving dishes.

The Department of Biological Sciences at the University of Alberta brings you this video tutorial specifically relevant to your student laboratory courses, specifically microbiology. If you're a student at any school of biology, this information will be helpful for learning how to perform agarose gel electrophoresis in the lab.

Home improvement expert Danny Lipford talks about a caulk tube extender. Check out this video tip to see how to get everything out of your caulk tube.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.
It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.
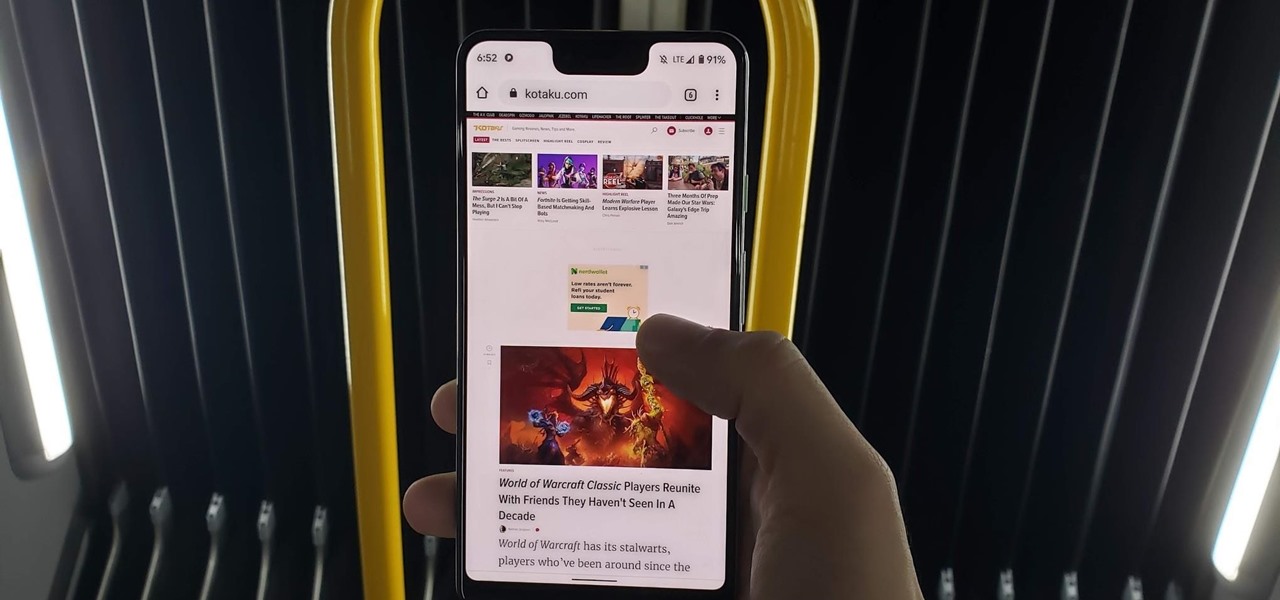
It's now standard for websites to have a mobile version. Conveniently, we can browse the web with a mostly mobile-optimized experience. But what if you want the desktop experience on mobile? If you want, you can browse the mobile web and see only the desktop version of websites on Android devices.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mobile data anywhere in the world.
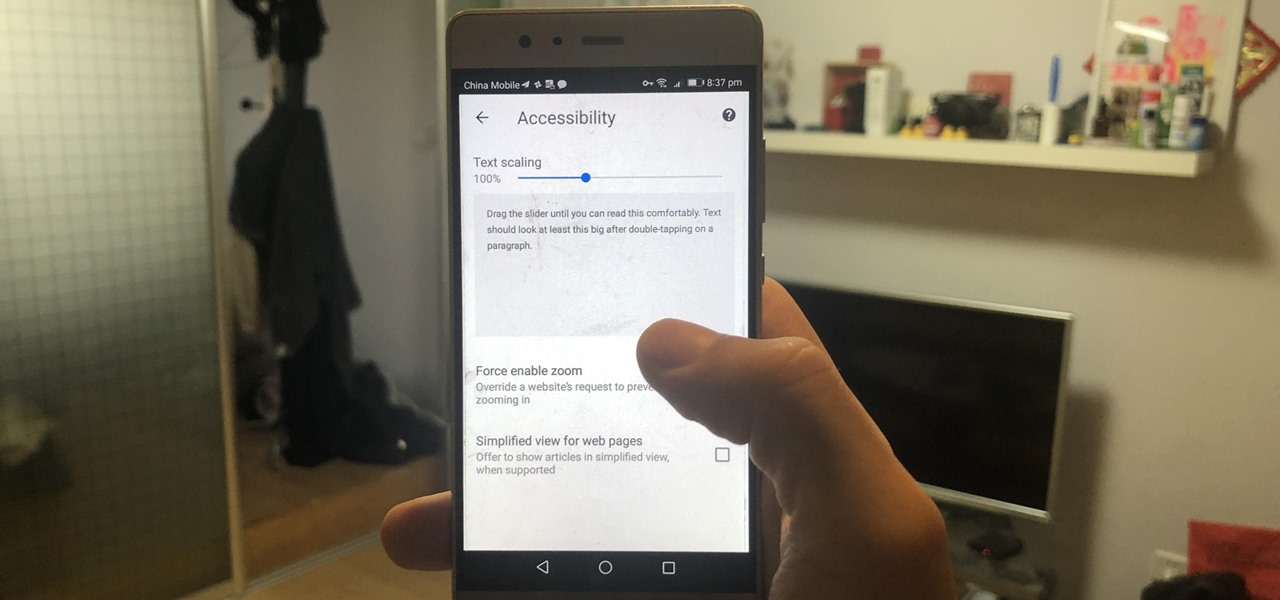
There are many reasons you might want to increase your text size in Google Chrome. The browser's accessibility options have a few tools to help the readability of text on websites. Changing the text scale, enabling zooming, and toggling the simplified view can customize Google Chrome to be perfect for you.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Samsung isn't set to reveal its latest and greatest — the Galaxy S10 line — until February 20, but that hasn't stopped leaks from giving us an early taste. While we already know what the rumored devices will probably look like, we now have access to their wallpapers as well. Apple fans don't need to be left out of the fun — someone has already cropped these images to fit your iPhone's display.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Waveguide manufacturer DigiLens has closed a $25 million Series C round of funding from automotive technology company Continental, which uses the technology in its heads up displays.

With numerous insider reports, patent awards, acquisitions, and hires over the past few years, augmented reality smartglasses from Apple appear to be an inevitability.