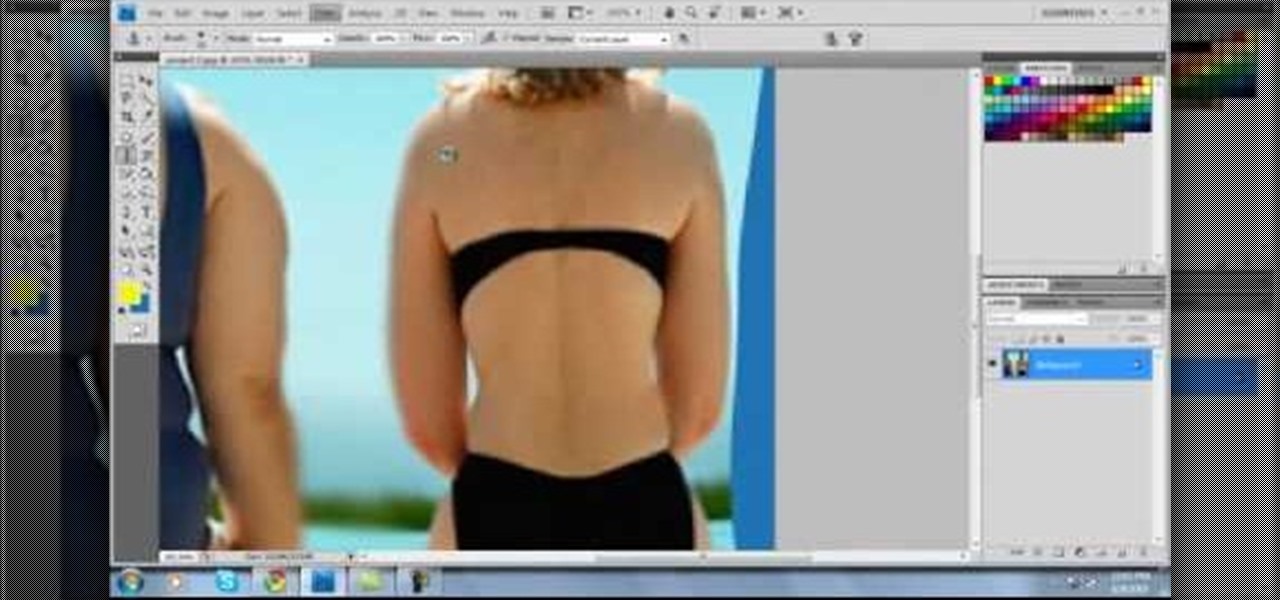
If you have a photo subject that is a tad larger than you would like, check out this tutorial. Change even the chunkiest body into a slim and svelte physique with a few clicks of your mouse in Photoshop. After watching this clip, you will certainly understand why you can never take a photo in a magazine seriously - its so easy to change someone's entire body!

Using specific measurements and settings, this video details how to use a Canon 5D Mark II with a Steadicam Merlin. The Steadicam Merlin is a great, low-budget alternative to larger, more cumbersome Steadicam rigs, but it still gives you a steady, smooth image. Paired with the 5D and you've got a slick, professional looking video.

In this culinary video tutorial from Guy Fieri's Big Bite, you'll learn how to prepare smoky grilled, tender lamb chops, simply seasoned and served with a fragrant, spicy Morroccan charmoula sauce, a delicious herb and onion mixture that will take your grilled meat to the next level.
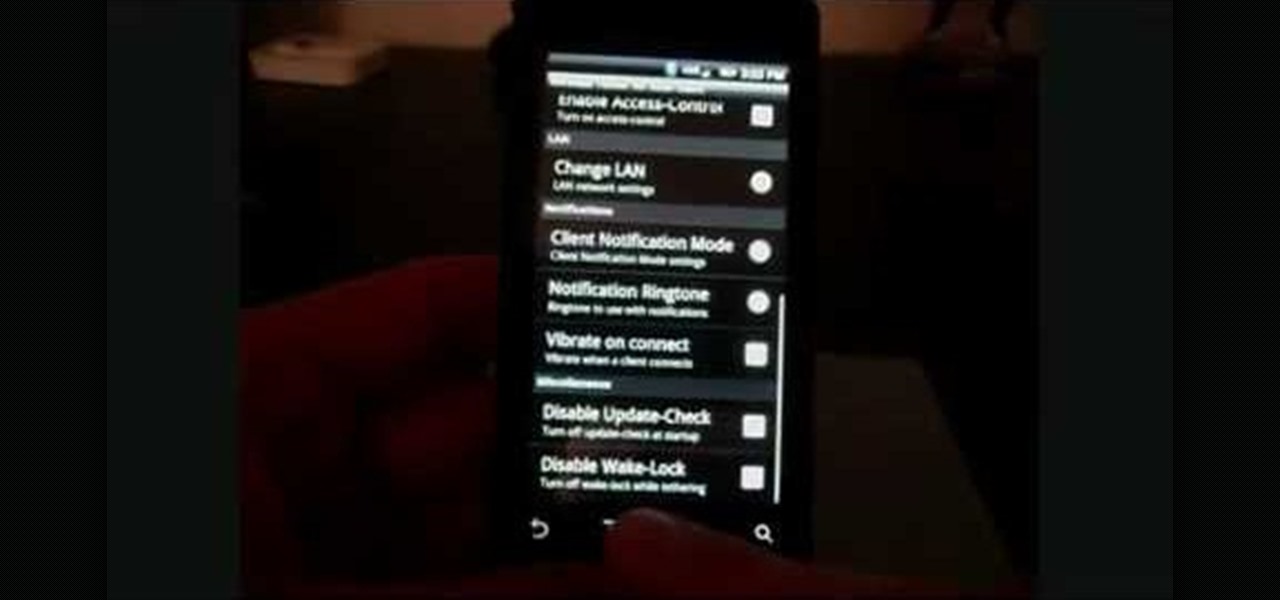
Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...

Use whole saws or drill bits larger than the necks of the glue bottle and about a ten inch 2x4 piece of wood. Drill holes for the amount of bottles you want to have. You can add feet to your rack if the necks on the bottles are too long for the rack by gluing a couple of small wood blocks underneath on both ends.
Using a simple workaround, one can change the font settings on the iPhone or iPod Touch to an easier to read, slightly larger size. And the best part? No jailbreaking required!

Learn how to make stuffed pizza pockets for your kids. A delicious snack or meal. A larger version of this Italian recipe is often called a calzone. Vary the fillings to your families liking and you will win raves at the table.

In this video, "Miki Falls" manga cartoonist Mark Crilley shows how to draw body proportions for manga comics. Characters in manga proportions are often proportioned differently than characters in American comics, with larger heads and more childlike bodies. This video show you how to get manga bodies right.

Don't let your roast flop about untied. Tie a chicken properly so that it roasts to perfection. This skill is very useful to start with and transition to larger birds like the Thanksgiving turkey.

Watch this instructional ceramics video to learn how to throw a wide bowl with Simon Leach. As a preliminary step, one should throw a flat piece of clay onto the pad to assure easy lifting off of the bat. Centering is quite difficult with a larger piece of clay. Leach's visual guide allows one to view the delicate steps required to throw a wide ceramic bowl without letting it collapse.

Improve you crocheting skills by creating fun shapes. This how to video is a crocheting tutorial that will show you how to create a small star with five points. Crochet several of them, bind them together and create larger handmade projects.

Trying to learn the English language? Then it's vital to start with the basics: the alphabet. Learning larger words won't be difficult once you understand how each letter of the alphabet is pronounced.

This knot is identical to the "Four-in-hand", apart from the addition of another pass of the wide blade across the knot before ending. This gives a slightly larger knot.

The video starts with the presenter explaining that he will be talking about harmonic oscillators, not the harmony of anything in sound, but something that moves back and forth in roughly the same speed back and forth.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

1. Before applying eye makeup, eliminate under-eye swelling by applying cold compresses to your eyes for ten minutes. Any fluid retention around your eyes will cause eyes to look smaller.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

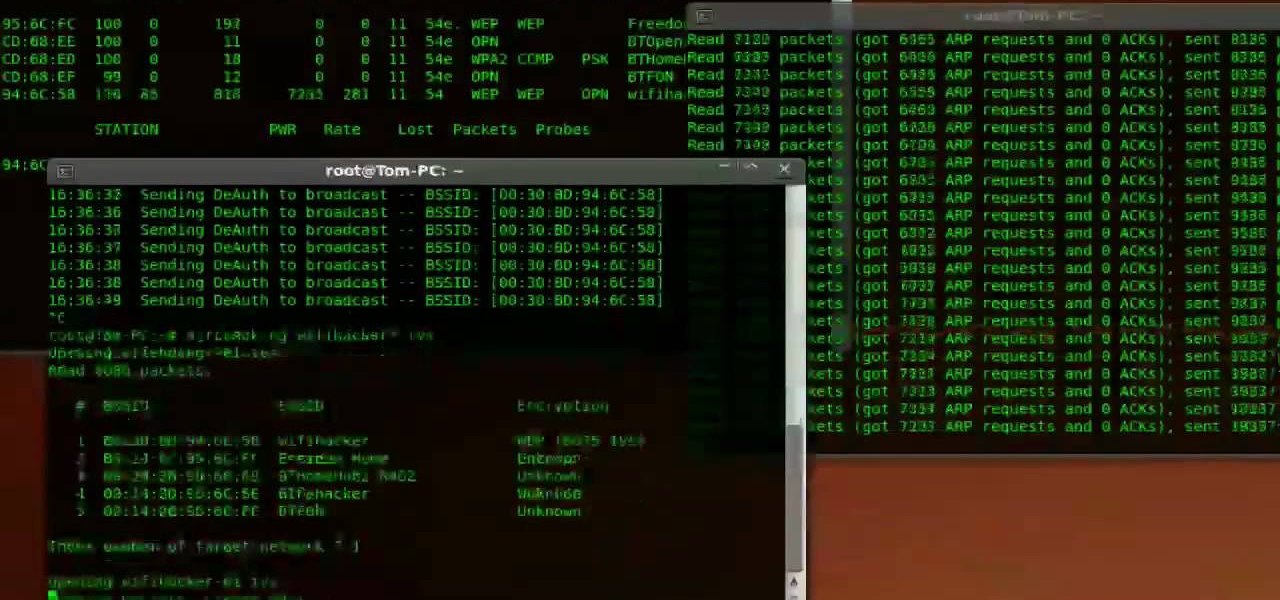
This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

With the economy as terrible as it is these days, obtaining any sort of job, from receptionist to screen writer, requires thorough networking.

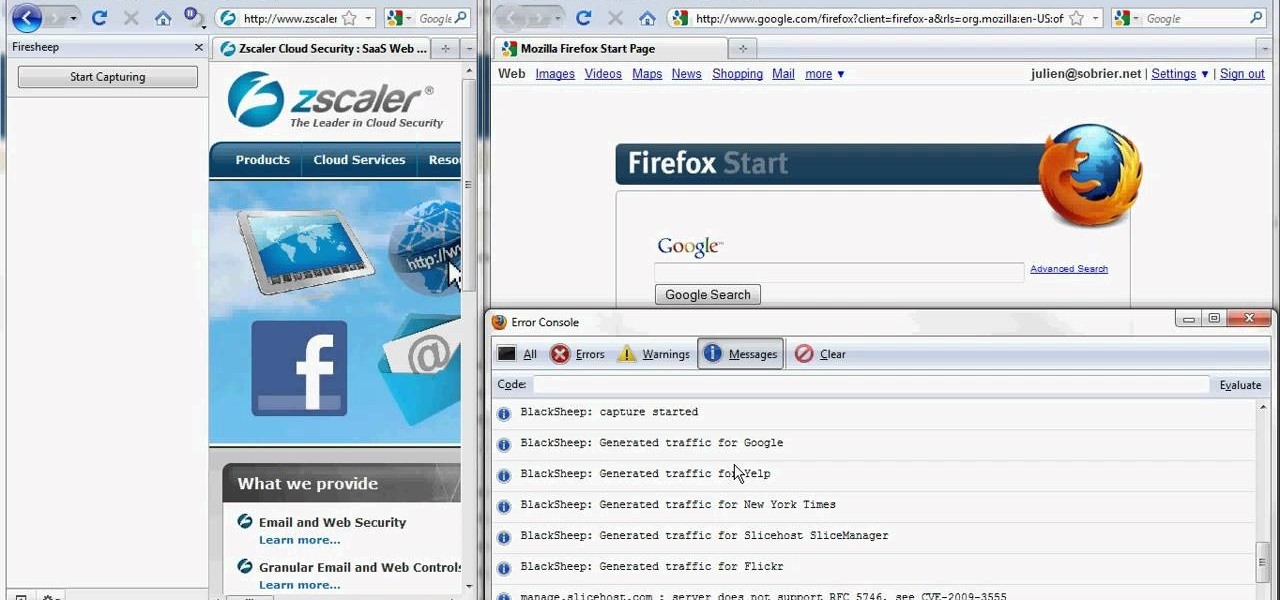
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.

In this tutorial, learn how to save yourself the money you'd pay someone to unlock your Google G1 phone from T-Mobile and do it yourself in just a few quick minutes. This is actually a very easy process and this clip will walk you through the process step by step so you can freely use your phone on any network and not be limited to T-Mobile. This is also helpful if you wish to give away or sell your phone to someone on a new network.

In this clip, learn how to tether your rooted Droid to a WiFi network and use it as a modem for your other Wireless devices. This process is pretty easy and only requires a network and that your phone be rooted.

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

As far as HBO is concerned, it's not augmented reality — it's Snapchat. The premium cable network is leaning hard on Snapchat's AR magic tricks to promote yet another series, this time for the adaptation of Philip Pullman's His Dark Materials series of novels.

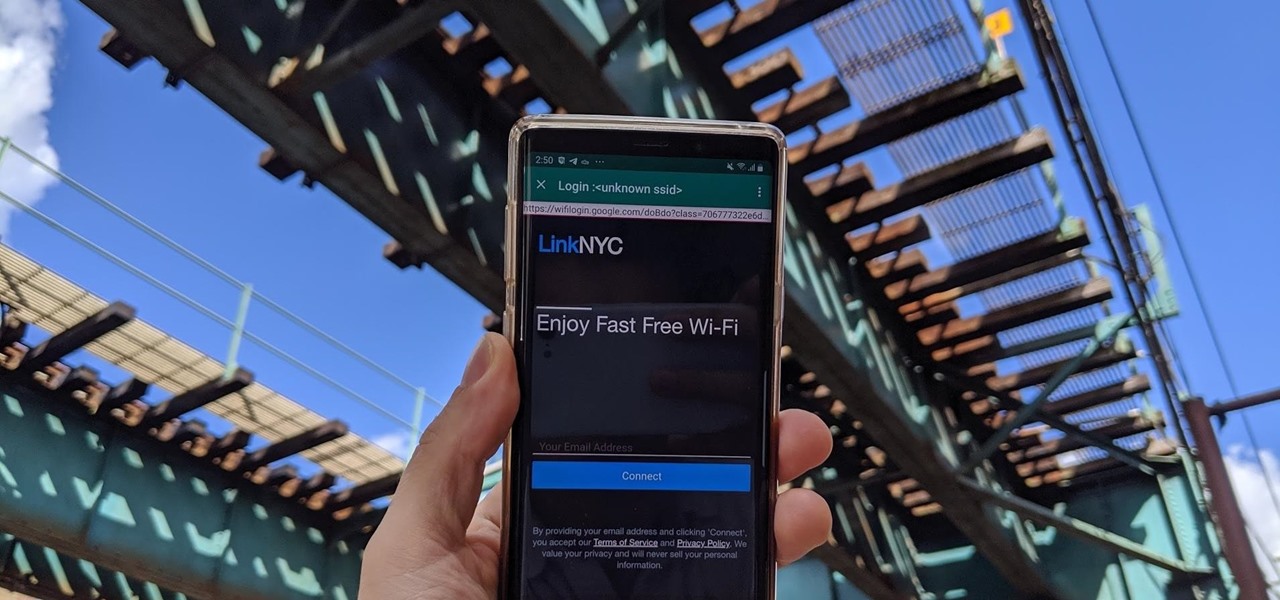
Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.