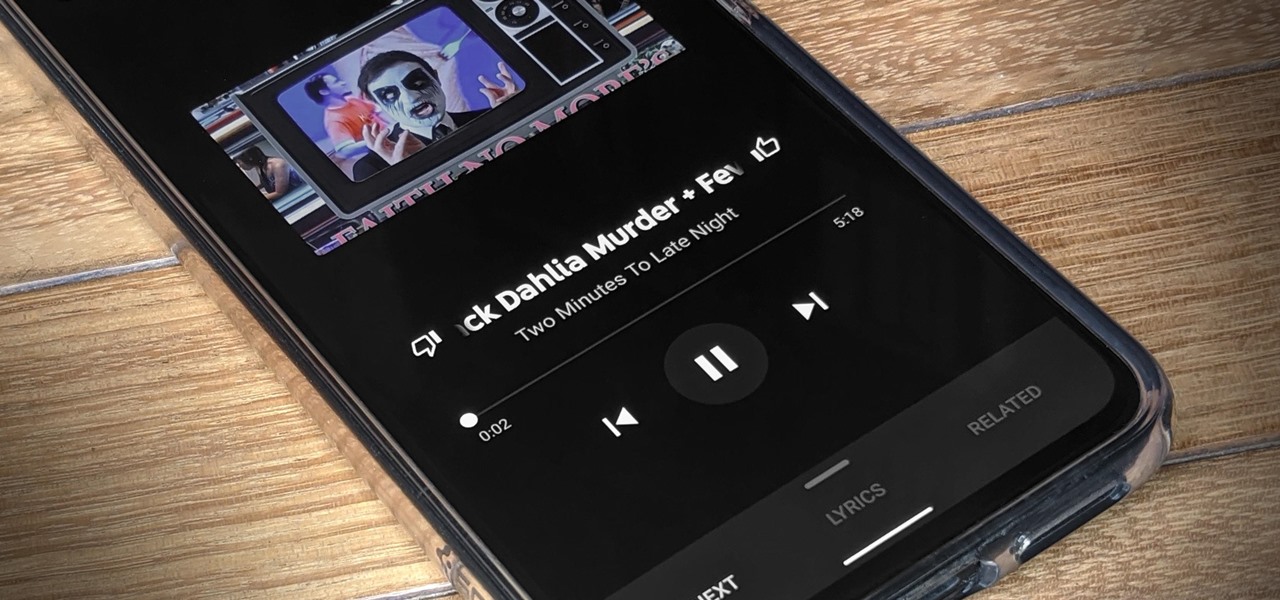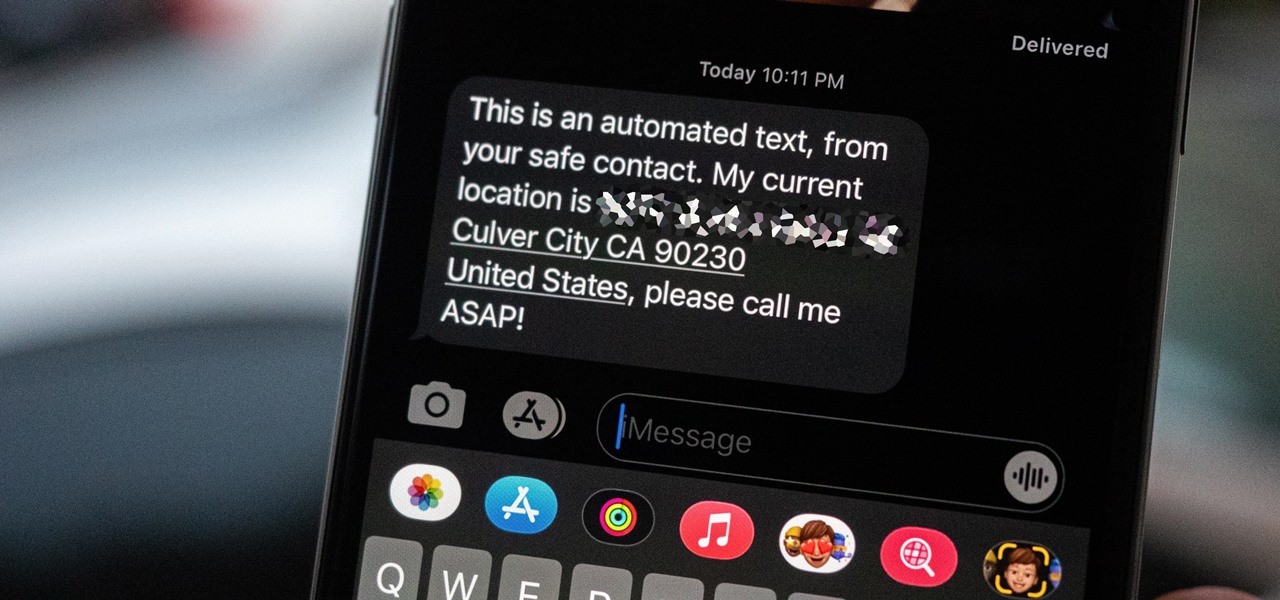
Strange or uncomfortable encounters can be difficult to get away from sometimes if you're overly polite and don't want to hurt anybody's feelings. Thankfully, your iPhone can help save the day, providing you with a plausible excuse to exit the scene without having to conjure up some last-minute reason on the spot.
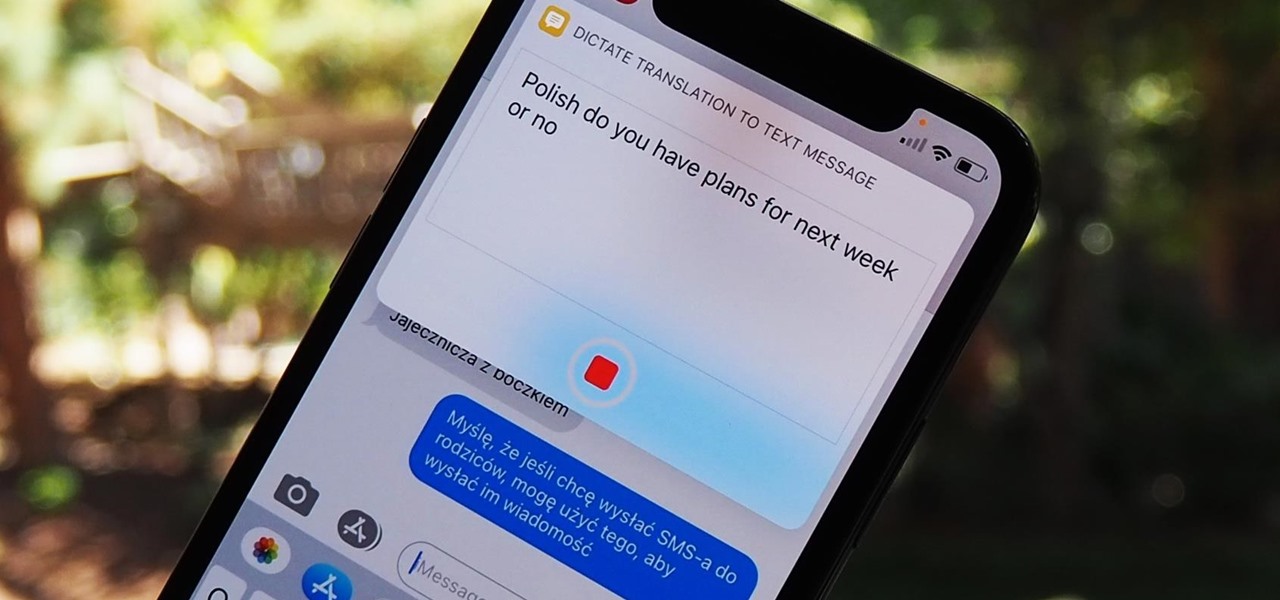
When iOS 14 came out, Apple released Translate, an app for translating voice and text between several languages (even within Safari). Unfortunately, it's not as comprehensive as some third-party apps or even Siri. That's why Apple uses Microsoft's translation services within Shortcuts. It may sound surprising, but we're not complaining since you can do some pretty awesome things with it.
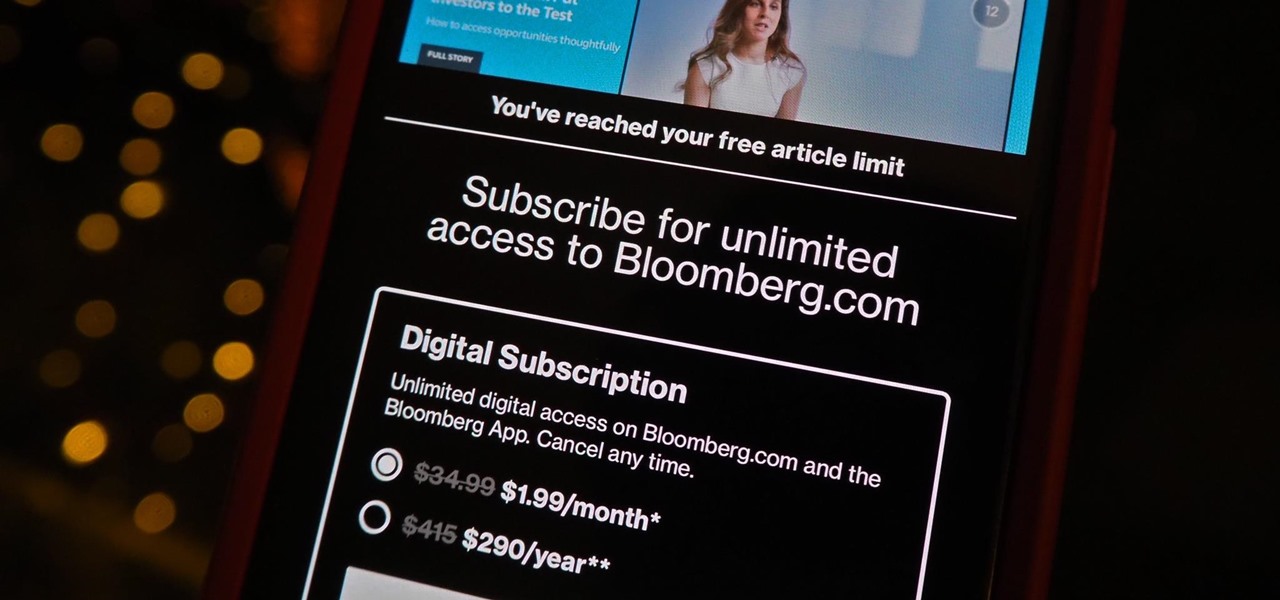
One of the most aggravating things that can happen on Facebook, Twitter, and other social media apps is when a friend shares an exciting story, and a paywall prevents you from reading any of it. You could pay for a subscription to unlock it, but there are so many news sites that it can be both confusing and expensive to spend money on all of them.

At the opening of its virtual Lens Fest, taking place Dec. 8-10 and open to the public, Snap is furthering its facilitation of AR development with new tools for Lens Studio version 3.3 and a planned investment into its AR creator community.

One of iCloud Photo's biggest perks is its ability to store large video files taken with your iPhone, so you can fill up your iPhone's storage with other items. That said, when you play back those videos, you may not be watching the footage in its original quality. Instead, they may be low-res versions. To view the high-quality originals — or to make sure that's what you see — just follow this trick.

Apple does not provide a native way to lock apps on your iPhone behind Face ID, Touch ID, or your passcode. For a long time, we've wanted that option for improved privacy and security, but Apple does allow developers to use its authentication protocols. Apps like Messenger, Outlook, and WhatsApp give the option to lock them down, but for the apps that don't, you can force it with a little time and effort.

Why pay for a movie when you can get it for free? Thanks to Movies Anywhere, you can claim and download a video for your digital film collection right now at no cost. And getting your freebie flick couldn't be any easier.

When it comes to washing clothes, the laundry symbols on your tags might as well be hieroglyphics. They're difficult to interpret, easy to forget, and even easier to ignore. But if you don't want to ruin expensive designer clothes, blankets, and other fiber-based materials, you need to figure out the meaning behind those tiny icons. Thankfully, your iPhone can help out.

If you enjoy watching music videos, live concert recordings, or bedroom cover songs on YouTube, then YouTube Music is worth your consideration. In fact, YouTube will show a "Switch to YouTube Music" button on some music videos that opens the song in the YouTube Music app — but not always.

Google Maps Live View is already one of the more useful examples of augmented reality on smartphones that is available to the average consumer today.

One of the biggest bummers about Netflix is the inability to create different lists for your favorite movies and TV shows. Instead, you're only able to lump titles into the single default "My List," and that can be impossible to browse. It doesn't separate titles into categories or genres, and titles are arranged for you automatically, so there's not much room for customization.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

It's not so difficult to stay at home during the coronavirus lockdown when there's so much free entertainment to take advantage of. That seems to be the M.O. for many studios and streaming services, as they've made so many shows and movies available to the public for free. That said, they aren't running charities here. These deals won't last forever, so make sure to jump on board before it's too late.

While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

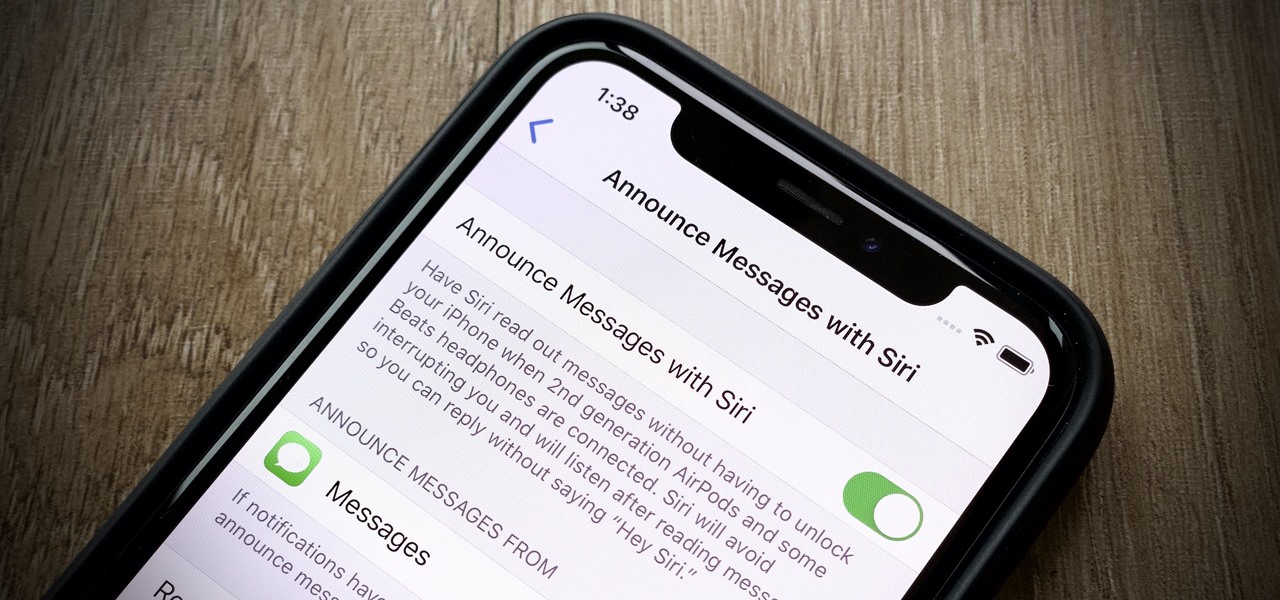
Apple's iOS 13 has been quite the disrupter. The initial update featured over 200 new features and changes, while its successor, iOS 13.1, brought another 22 to the mix. With the company's latest update, iOS 13.2, you'll see an extra 22 amendments on your iPhone, including new emojis, Deep Fusion on iPhone 11, 11 Pro, and 11 Pro Max, and Announce Messages with Siri, just to name a few.

While iOS 13 introduces over 200 new features for your iPhone, one of the biggest focuses this year is Photos and Camera. The update completely overhauls the Photos app, creating a more organized and natural way to interact with your pictures and videos. You'll also find a few new tricks in the Camera app. In all, Apple has added over 30 new features to your shooting, editing, and viewing experience.

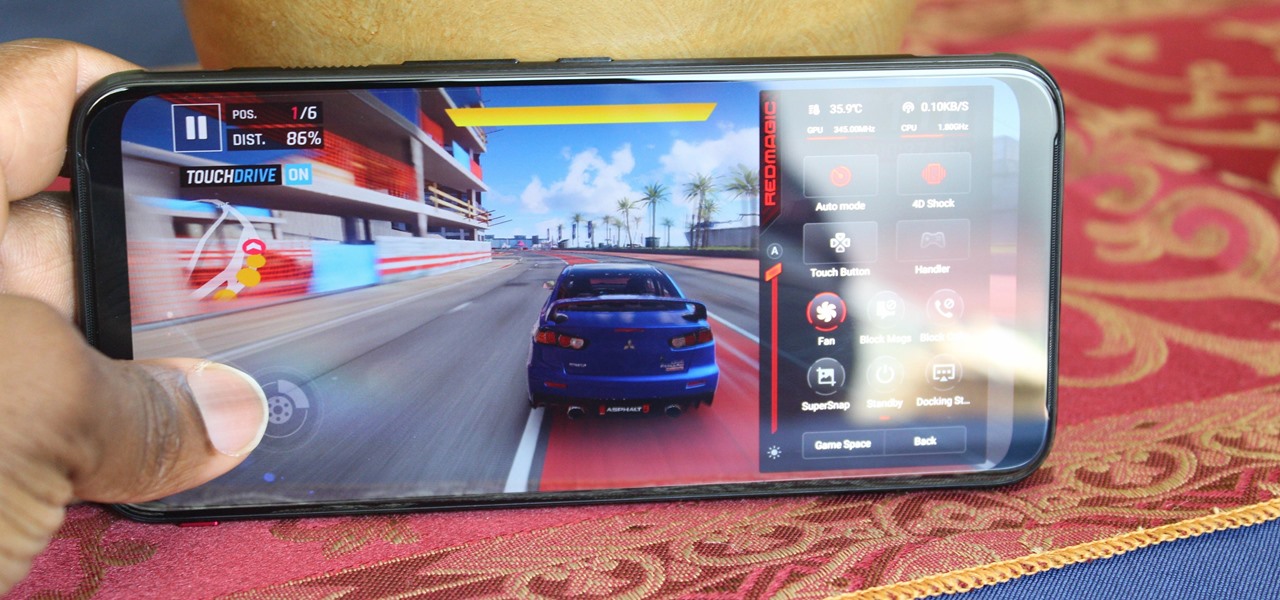
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

September is nearly here, which means new iPhones are, too. We're looking forward to iPhone 11 Pro and 11 Pro Max, as well as the more affordable iPhone 11R. All three iPhones will run iOS 13, so Apple's entrusting beta testers to ensure its new OS is ready. The latest update, developer beta 8, is now here for us to test.

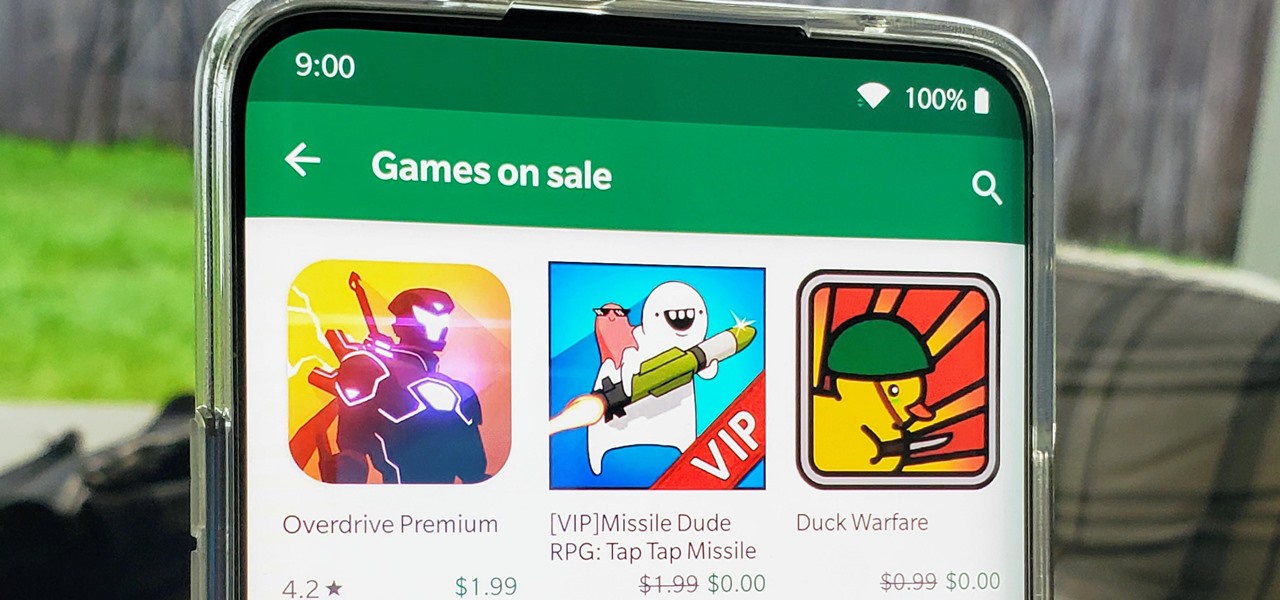
I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

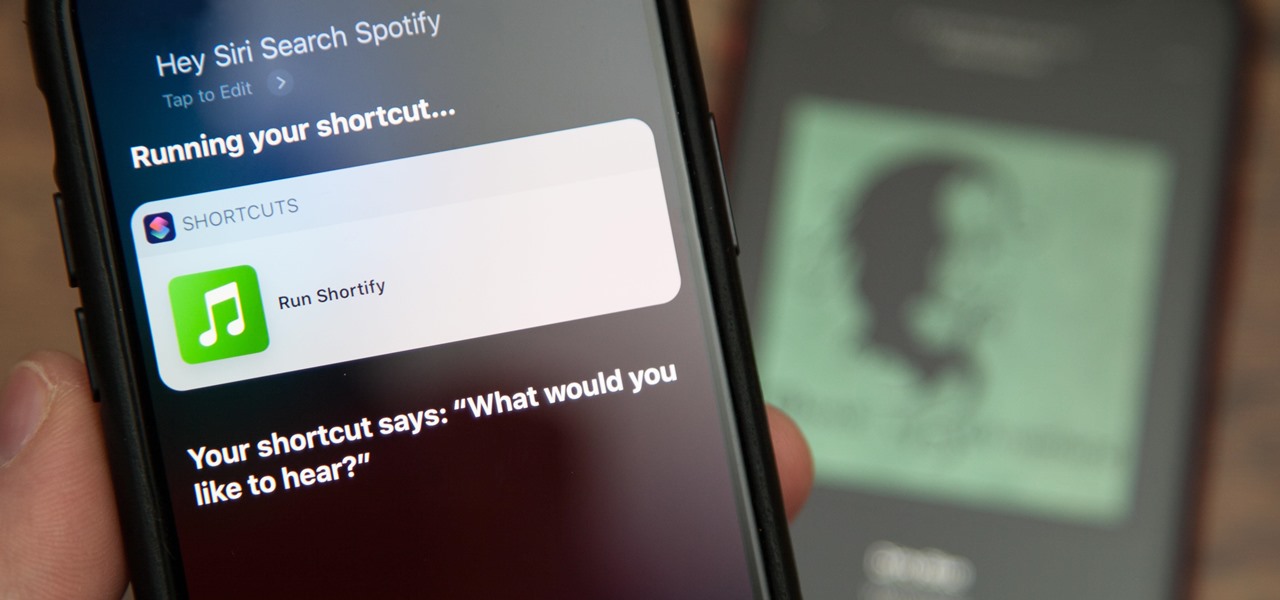
In iOS 13 and later, Spotify supports Siri commands, something we've wanted ever since Siri and Spotify were things. But if you're on iOS 12 still, you're missing out. All you can do is open the Spotify app, then pause and skip tracks with Siri after you start playing a song manually. There is a workaround, however.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.