Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

I love making beeps and bloops with the Arduino pitches library, but sometimes archaic 8-bit tunes just don't cut it. Whether you want your robot to terrify your enemies with a demonic synthetic voice, you just need a pocket boom box on the go, or you want to a miniature guitar amp, a simple LM386 amplifier can crank up those signals loud enough to play through any speaker.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

It wasn't Christmas, but for Amazon Prime members, it was darn close: Amazon Prime Day, one of the biggest shopping days of the year, came and went earlier this week. Unfortunately, there weren't many Prime Day-specific deals to be had for augmented reality fans, but that doesn't mean AR-loving Amazon Prime members were completely left out.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

Could your fever, body aches, cough, and sore throat be the flu? Soon, finding out may not involve a trip to the doctor.

If you're a developer in the augmented and mixed reality space, there's a high probability that you're intimately familiar with the 3D application and game engine Unity. In May, at VisionSummit 2017, Microsoft announced that 91% of all HoloLens applications have been made with the software. But there's a section of Unity that you may not be familiar with, which has become very important to augmented, mixed, and virtual reality (known collectively as XR, for "extended reality") — Unity Labs.

The sun-drenched people of Phoenix can now sign up to ride in an automated car, for free, courtesy of Waymo. The Alphabet affiliate announced its "early ride program," which will (hopefully) demonstrate how self-driving cars will fit into people's everyday lives. Highlighting a challenge Nissan CEO Carlos Ghosn has spoken about that faces the driverless industry.

If you ever imagined turning the surface of your desk into one large augmented computer, well the future might not be far off, my friends. Lampix, the company that transforms any surface into a smart surface, is currently working on a portable and quite fashionable lamp to project an augmented computer onto any surface that you can interact with using your hands.

Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

While visiting the Made by Google pop-up shop in New York City this morning, I had a chance to try out the new Daydream View virtual reality headset. First impressions are important, and Google's new mobile VR product makes a good one. The headset is made of a soft fabric that most evokes a beloved old college sweater that's well worn but properly cared for. The demo only featured the Slate (darker gray) model, though customers will ultimately be able to choose from either Slate, Snow, and Cr...

A stack of light-as-air pancakes can make a weekend morning truly golden. While fluffy pancakes may not seem like rocket science, the reality is that there are many little details that can contribute to a pancake fail that's either too dense or too crumbly.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

We've had the pleasure of test driving the ASUS Transformer Book T100T for the last couple of weeks, and for a $400 Windows 8 machine, it's impressive to say the least.

If you're one of the lucky people who received the gift of terrible eyesight from your parents at a young age, chances are you ate an awful lot of carrots growing up. Though carrots are one of the top vision-boosting foods, they don't offer fast results.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Some people put up their holiday decorations as soon as Thanksgiving is over. Some wait until Christmas Eve. Right now, the only thing in my whole apartment that would tip you off is a tiny little fake tree on the counter. I've been planning on decorating all month, but I haven't quite gotten around to it yet.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

There's nothing like buying an awesome new gadget, but it leaves you with one problem (besides an empty wallet)—what do you do with the ones you already have? There are plenty of ways to put your old gadgets to use, but if you'd rather get rid of them, you may as well get something out of it, right? Here are five places where you can recycle your electronics and replenish your cash stash.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

The realm of science fiction isn't all lasers and cute green toddlers, sometimes alternate science history is sci-fi, too, as exampled by the Apple TV Plus series For All Mankind.

GameGuru was created for game enthusiasts who are not programmers or designers. By offering catalogs with thousands of royalty-free assets, GameGuru lets design novices bring their visions to life.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

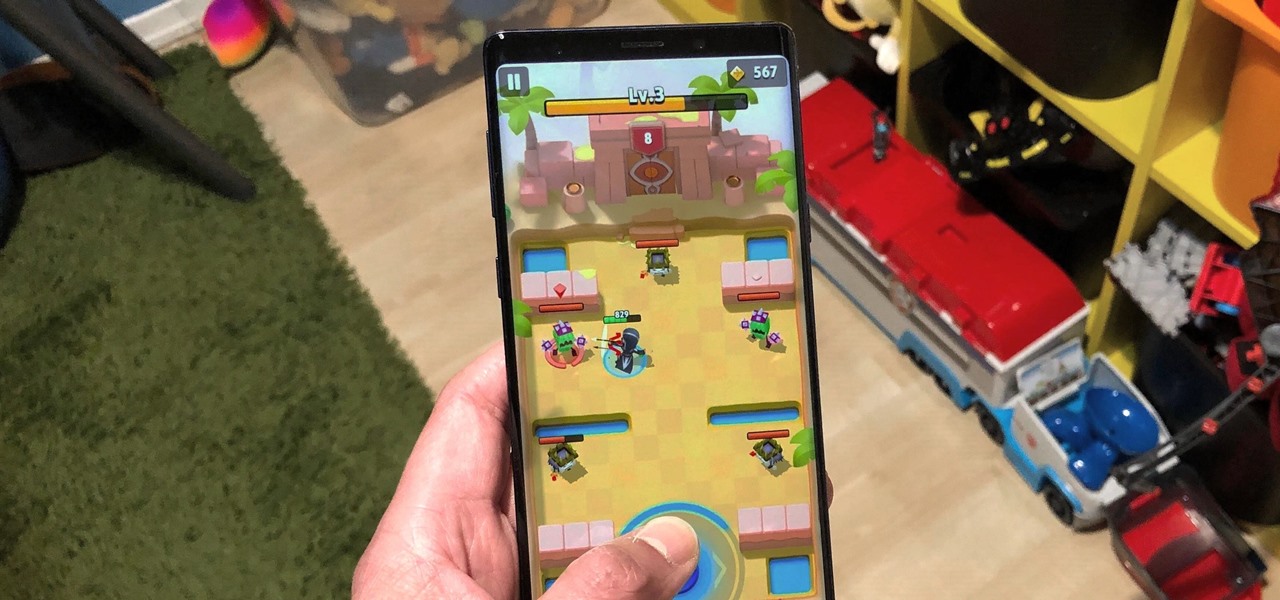
Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a limited time, to provide some much-needed fun during scary times.

One of the coolest aesthetic features of iMessage is its animated message effects. If you're like many users, you might even have discovered them by accident, where wishing your friend a "Happy Birthday!" or congratulating them on a promotion unexpectedly flooded your screen with balloons or confetti.

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.