In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.
As Magic Leap prepares to ship the Magic Leap One later this year, the company is putting its focus on mentoring developers and creators to build a content ecosystem for the spatial computing platform.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.
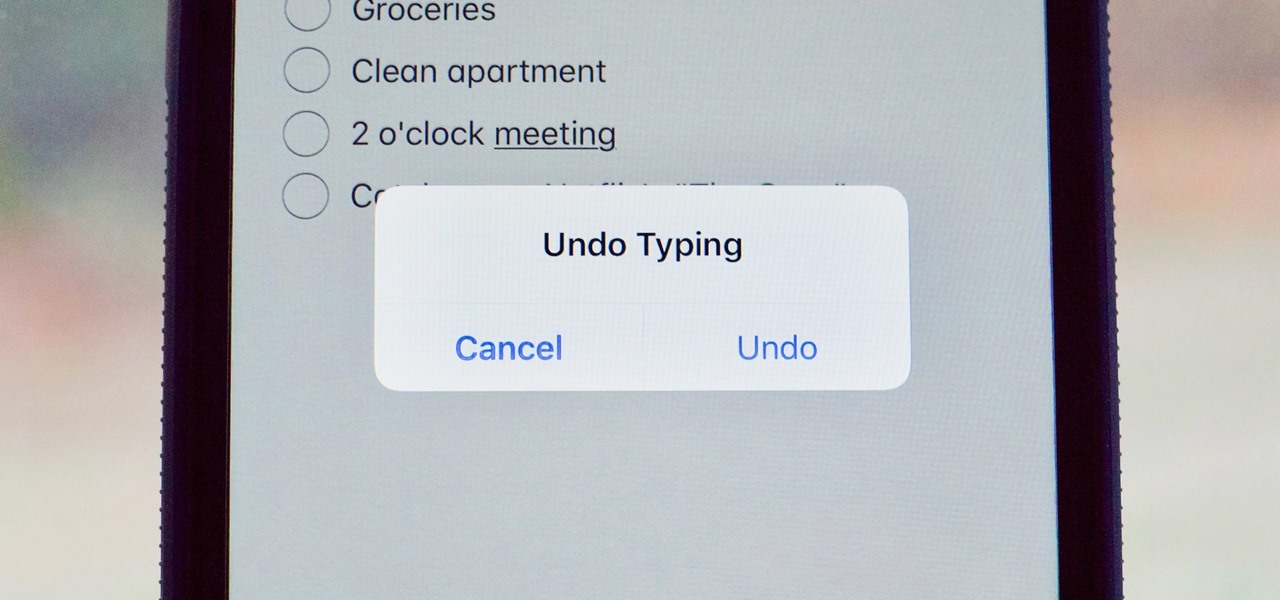
Many of us use the Notes app to jot things down in a hurry. Most of the time, that's no big deal. However, the faster the typing, the higher the chance of error. If you happen to make a typo, or if you accidentally delete that chart you worked so hard on, there's an easy way to undo the changes.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

The Guardians of the Galaxy have to be the most fun superhero team to have at a Halloween party. They dance, they break the rules, and they definitely have the grooviest music. So the Guardians are a great bunch to pick from for your Halloween costume — or even for a themed group costume. Just imagine the badass vibe when you all walk into a venue together with Star-Lord blasting "Cherry Bomb" from a portable speaker. Here's a roundup of some of the best Guardians of the Galaxy costume guides...

Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the blood, diabetes, and high blood pressure.

The Massachusetts Department of Public Health (DPH) issued a health alert for a Boston mumps outbreak, on Monday, June 5th, to healthcare providers and local boards of health. There have been 12 reported cases of mumps during the recent outbreak. The affected residents' symptoms occurred between March 24th and May 31st, and 10 of the 12 had symptoms after May 9th. There have been 35 confirmed cases of mumps in 2017 in Massachusetts, and "nearly 300" suspected cases in the continuing outbreak.

The sun-drenched people of Phoenix can now sign up to ride in an automated car, for free, courtesy of Waymo. The Alphabet affiliate announced its "early ride program," which will (hopefully) demonstrate how self-driving cars will fit into people's everyday lives. Highlighting a challenge Nissan CEO Carlos Ghosn has spoken about that faces the driverless industry.

Every Tuesday, Next Reality will give readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the Next Reality landscape, and will always know what's going on with new augmented and mixed reality tech and applications.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Warning: If you are eating and for some reason still decided to click on this article, turn around now. Maui, Hawaii health officials have reported finding at least six cases of angiostrongyliasis, a parasitic lungworm that infects humans. Colloquially, it's known as rat lungworm disease. And if you think that name is awful, just wait until you hear what it does to the human body.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

Have the sniffles? Yes. Does your head hurt? Yes. Coughing? Yes. Could you have influenza? Yes. How do you know the difference? With these symptoms, you could also have a cold.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Why did I write this when they're tons of scanning tools available.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

Since its introduction on the iPhone 5S, Touch ID has made unlocking Home button iPhones quick and secure. The second-generation iPhone SE brought back the beloved feature in 2020 but didn't take any steps to improve on the technology. So if you're rocking Touch ID and having trouble getting it to read your fingerprints, there are some things you can do to fix it.

Some people put up their holiday decorations as soon as Thanksgiving is over. Some wait until Christmas Eve. Right now, the only thing in my whole apartment that would tip you off is a tiny little fake tree on the counter. I've been planning on decorating all month, but I haven't quite gotten around to it yet.

It seems nowadays the word "easy" has taken on an alternate meaning. When I see "easy," I expect a quick and painless process, but when it comes to flashing or installing a custom ROM, easy means anything but.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

How to patch a hole in drywall / plasterboard / Sheetrock. Everyone at some stage in their life will need to patch a hole in drywall / plasterboard / sheetrock. Instead of doing some dodgy patchwork, watch this video to see how simple the job is. The steps are as follow in point form. This method is particularly suitable for holes that are larger than about 100mm or 4 inch's in size.

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities.

This is easier than the divisibility by 3 rule, but still necessary for those starting out with simple division in math class. You can use the divisibility rule to see if a number is divisible by 2, 5 or 10. This video will show you how simple it is!

This video is a collection of useful tips and tricks for solving the OLL (Orientation of the Last Layer) and the PLL (Permutation of the Last Layer) of the mighty Rubik's Cube.

Here's a neat and useful trick for you Vodafone users out there. In this how-to video, Stuart Miles demonstrates how to recover the number of the person who last phoned you and the time at which he or she called simply by entering *#147# on your phone's keypad and pressing send.

Increase the longevity of your makeup and make your eyeshadows last all day and night with this how to video. The products used in this makeup tutorial are as follows:

Here's a bunch of ideas from Threadbanger.com for all you slackers who waited until the last minute to make a Halloween costume.

Yuri Elkaim, personal fitness coach, shows you a five-exercise Bosu Ball workout that will tone your abs fast. The first exercise is a pushup on the Bosu Ball with the spherical side down. With your torso down, lift one leg up from the floor. Bring the torso down, then back up, and pull the raised leg into your body, then back out. Alternate legs each time, and do as many of these as you can. In the second, turn the Bosu Ball flat-side down and align your buttocks and back on top of it so tha...

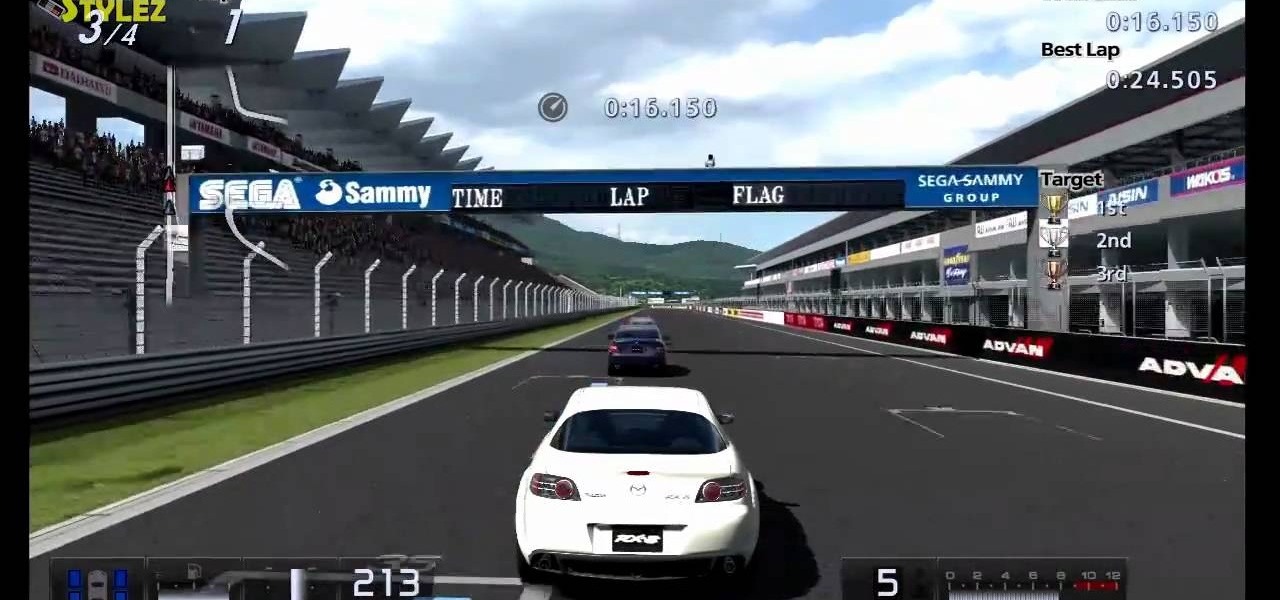
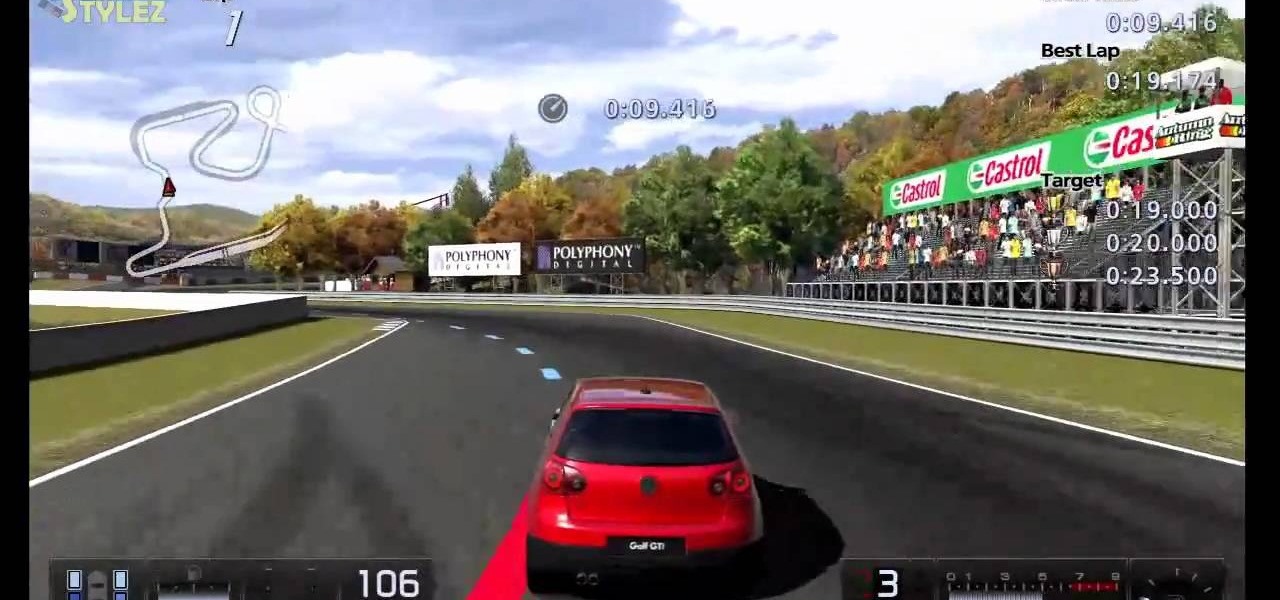
Don't you wish you could do this stuff out on the open road with your own vehicle? Alas, it will remain in Gran Turismo 5 on the PlayStation 3, where slipstreaming and drafting is totally possible (and legal). See how to earn the gold trophy on the ninth test (B-9) of the National B License Tests. To unlock these tests, simply buy your first car.

This is were things get interesting (and FAST!)— B-7, then seventh of the National B License Tests in Gran Turismo 5 on PlayStation 3. You'll be testing out your high-speed control of lines and throttle control. If you haven't yet, simply unlock these tests by purchasing your first car.

In this tutorial, we learn how to crochet a left handed magic heart potholder. This will only take you a total of around seven rounds to finish from the beginning. Start out with a chain one and then do six half double crochets in the loop and join. For round two, you will do a chain one and then two half double crochets between each previous half double crochet before joining. Round two will be 12 half double crochets in total. For round three, you will chain one and then do two half double ...

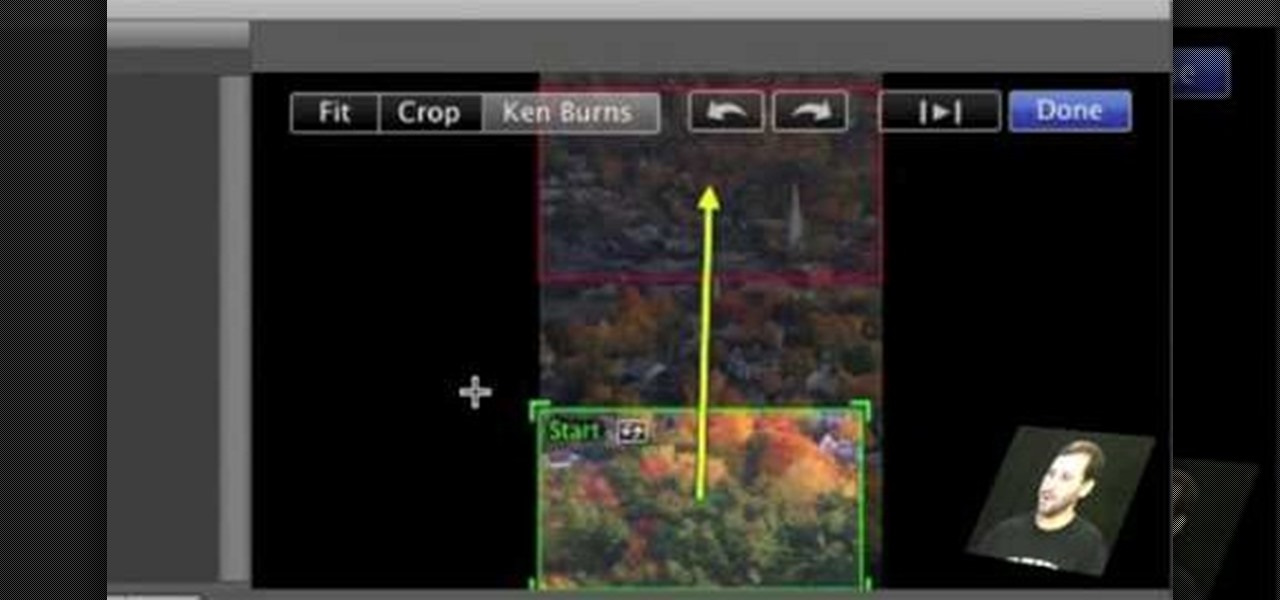
First open up the image by clicking on photo button or just drag the image from finder to the project area. Now click on the crop button or just press the c button, you will see a green and a red area in your picture. Now set the red area to where you want to zoom in and green area to where you want to start your zooming. Now set the green and red area in the picture as showing in the video and play it, you will see that the picture is zooming to where the red area was set. Now change the ima...

This video demonstrates how to make natural fiber rope using Douglas iris, a plant which is found along the Pacific coast from Santa Barbara from to Oregon. Before beginning, you should know that Douglas iris is poisonous when eaten, but it should be safe when you are handling it. The plant blooms every spring and dies every winter and has a brighter green color on top and a duller green towards the stalk, with a dark purple tint near the roots. You should collect plants which have died from ...

For roasted chicken, you would expect it to have a nice, brown crispy skin. You would expect it to be moist inside with great flavors throughout. By using the rotisserie function (very common in France) on the Cuisinart Brick Oven. Check out the recipe for this delicious herb-roasted chicken from Chef Hubert Keller.