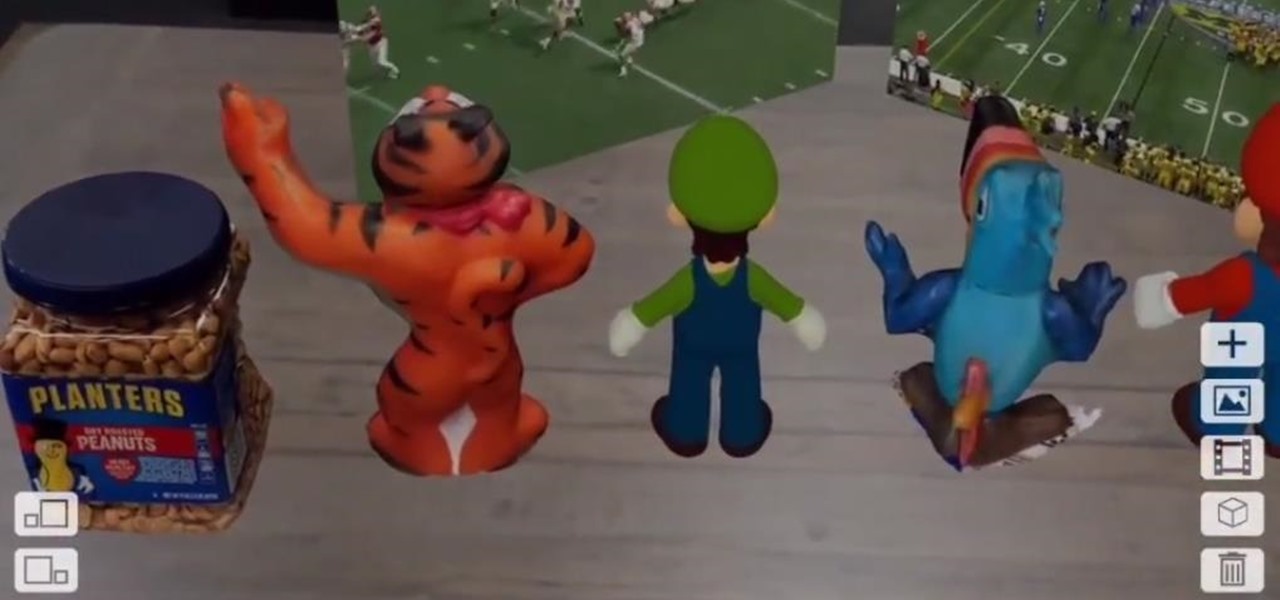After hosting millions of free 3D models online, Sketchfab is betting that augmented reality and virtual reality developers and creators will be willing to pay for premium 3D content.
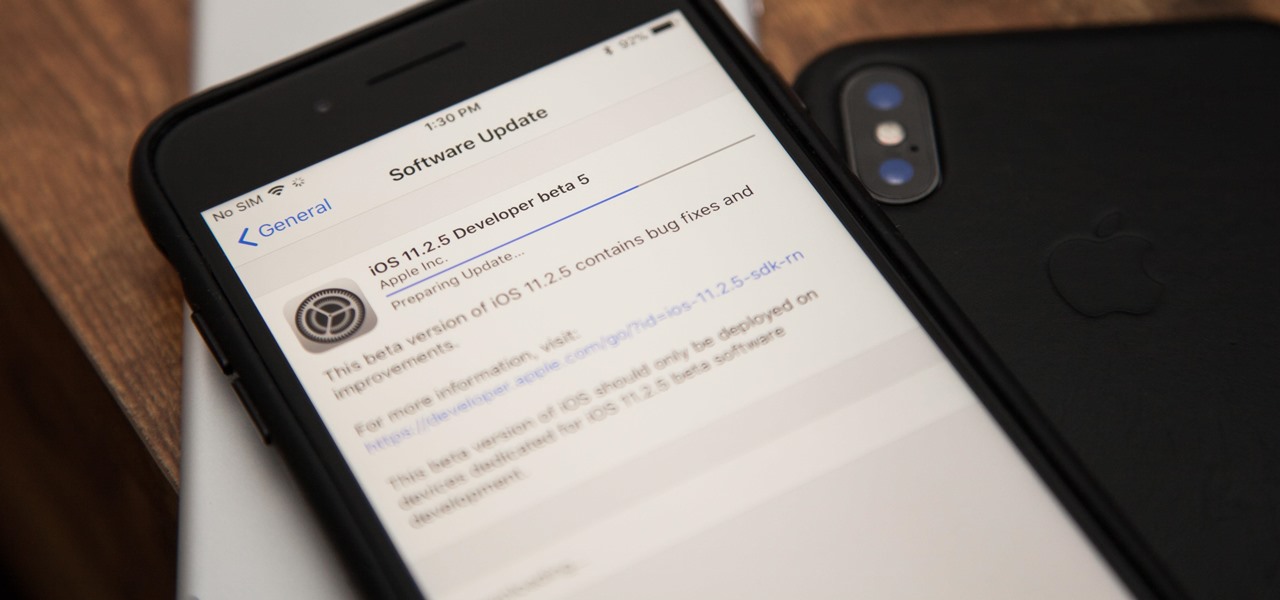
Apple released the fifth build of their iOS 11.2.5 beta software on Thursday to developers and public beta testers, just two days after the fourth beta. This quick beta release schedule may mean iOS 11.2.5 is almost ready for primetime.

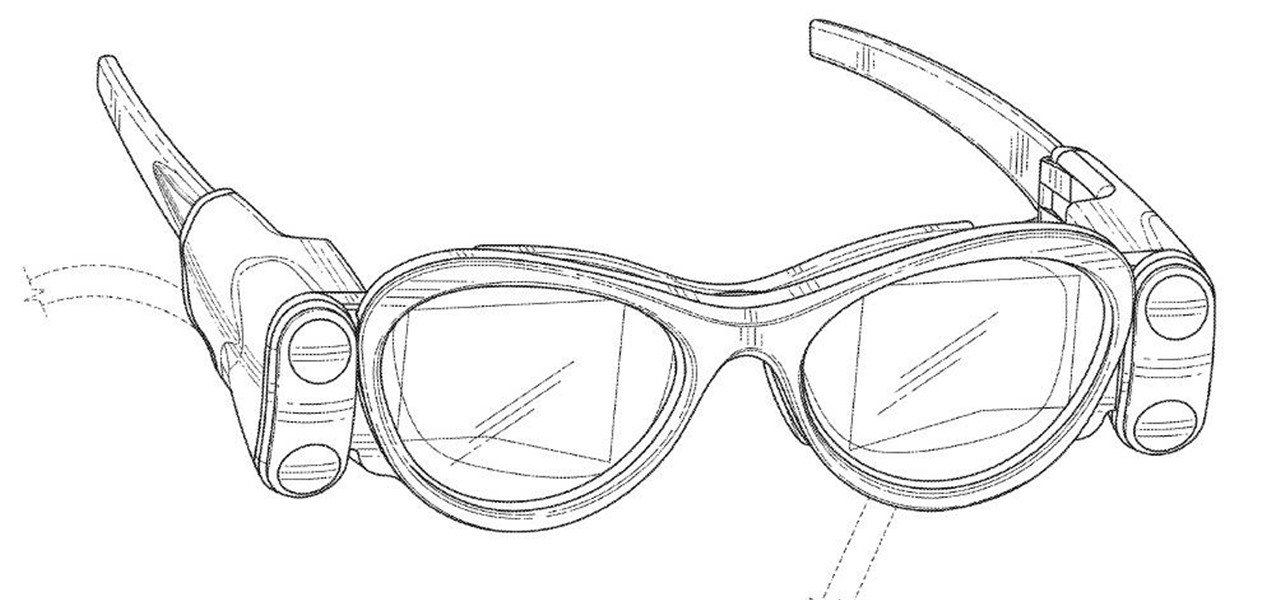
On Tuesday, original design manufacturer (ODM) Flex used the CES spotlight to help introduce a smartglasses reference design aimed at companies interested in bringing their own enterprise AR headsets to market.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Whether you're watching Netflix on your Android tablet, smart TV, or computer, the process for changing how subtitles and closed captioning appear is the same. Plus, when you customize the font, size, color, and the background, all devices connected to your Netflix profile will update — except for iOS and tvOS devices. A different process is necessary for an iPad, iPhone, iPod touch, or Apple TV.

The OnePlus 5T is a great device. However, for those of us in the States, we're pretty limited when it comes to OnePlus color choices. While we can pick one of two different spec models, both come in the same Midnight Black. Thankfully, OnePlus has just changed that, releasing a brand new color to our region — but it just sold out.

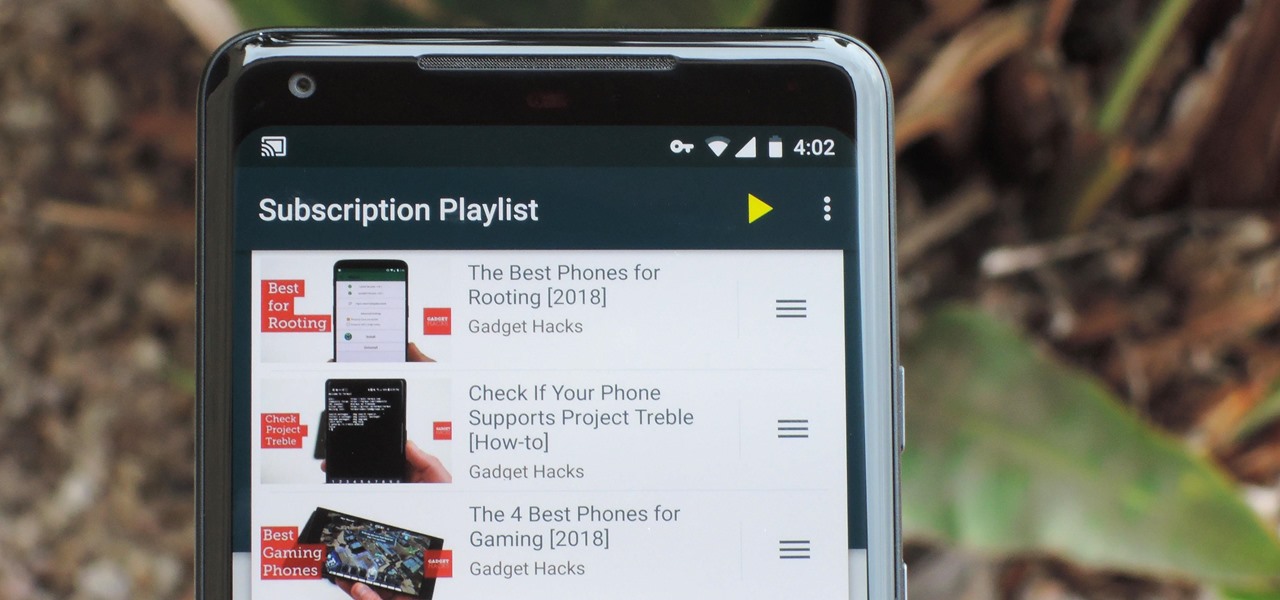
Sometimes I'm convinced Google has ADHD. They'll create a great product, then get distracted by the next moonshot and never put the finishing touches on their last project. Case in point, you can't just cast a playlist of your subscriptions from YouTube to Chromecast, even though that's how many people prefer to use YouTube.

If you want your own lightsaber, you don't need to be a Jedi or have kyber crystals in your possession; now, thanks to augmented reality, all you need is an iPhone and a rolled up piece of paper.

Apple released the third developer beta for iOS 11.2.5 on Wednesday, Jan. 3, and public beta testers got in on the action the following day. The update comes two full weeks after the release of the second beta, marking an extended update period of Apple. The second beta mostly brought under the hood improvements to 11.2.5.

In the midst of outlining plans to release Pokémon Go in China and debut its new Harry Potter game during the back half of 2018, Niantic CEO John Hanke turned to the dark arts by taking a swipe at the company's AR gaming competition.

The Force was awakened in many a household on Christmas morning this year, as evidenced by numerous recipients of newly unwrapped Star Wars: Jedi Challenges systems sharing their first lightsaber battles in augmented reality on social media.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

The knee-jerk reactions to Magic Leap's long-awaited augmented reality device, the Magic Leap One: Creator Edition, range from pent-up joy to side-eyed skepticism. That's what happens when you launch the hype train several years before even delivering even a tiny peek at the product.

Samsung's Galaxy S8 and S8+ are excellent smartphones that wowed critics and consumers alike. So, it's only natural that Samsung's followup, the Galaxy S9 and S9+, would garner significant anticipation. While we don't know everything about these devices quite yet, we do have guesses to some key points of interest, including when the device will be announced and even released.

Last week, Magic Leap CEO Rony Abovitz teased his Twitter followers with some "fun and cool stuff" to share in the coming days. On Monday, he made good on that promise, sort of.

These days, location-based augmented reality gaming pioneer Niantic is best known as the developer behind Pokémon Go, but the uber-popular mobile game was not its first foray into the AR gaming genre.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

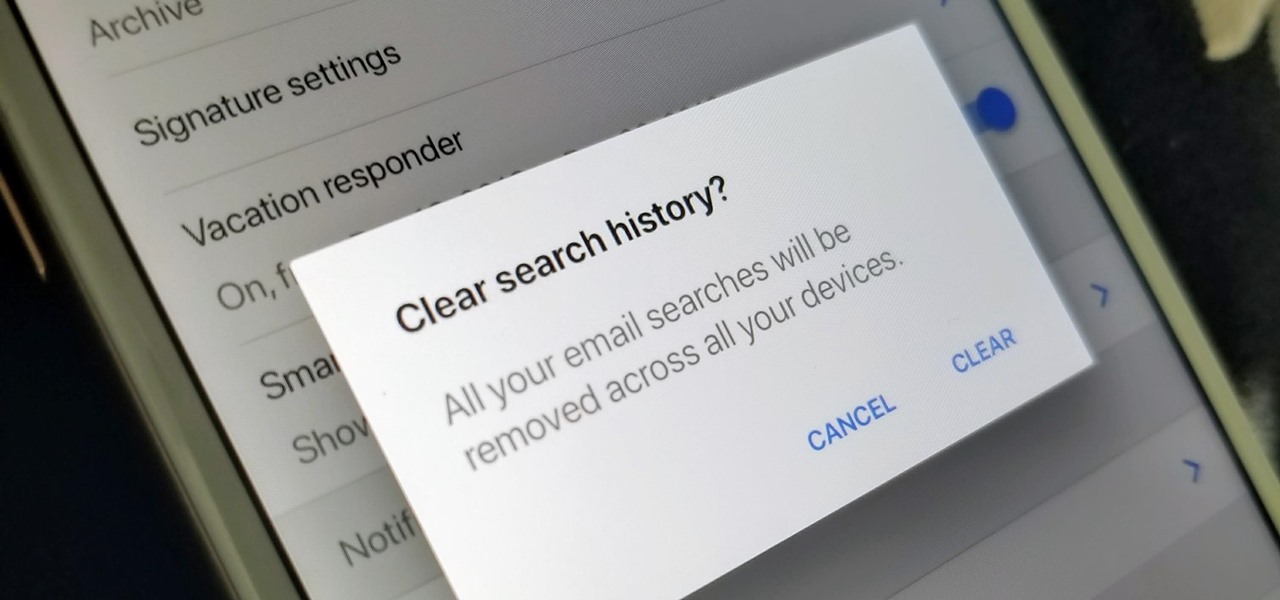
The Gmail app on both Android and iOS has a powerful search engine that helps you find any email with a few keywords. Even more impressive is Gmail's ability to remember previous search queries for future reference. However, this list of past searches can become extensively long and needs to be reset from time to time.

Just as the Transformers animated TV series of the '80s were basically half-hour commercials for toys, a new Transformers AR app for iOS similarly functions as a promotion for the latest installment in the film franchise.

If you're like me, you probably have a wishlist of Android games you'd love to buy, except the high price tags keep you away. A few bucks can feel like a fortune in the Google Play Store — you just can't bring yourself to pay that much. Well, lucky for you, Google Play has some serious discounts this Cyber Monday. There won't be a better time to buy these games, until next year, of course.

Death Road to Canada has finally arrived for Android, and it quickly took over our roundup for the best paid action games. Widely regarded as a top contender for the best video game of 2017, it came as no surprise when it easily surpassed all the other games in our list to grab the top spot for both Android and iPhone.

Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

Snapchat's popular AR lenses just got a lot more useful for businesses, as the company has now opened its Context Cards platform to sponsored content.

Live theater doesn't typically benefit from the kind of computer-generated special effects that big-budget Hollywood blockbusters deploy, but that could change soon thanks to Microsoft's HoloLens.

It was a good weekend for OnePlus 5T rumors — it looks likely the 5T will be first appearing in New York, and we got a spec leak that supports the rumors we've already heard. However, perhaps the best 5T news came from OnePlus' CEO himself: The OnePlus 5T may cost $600 or less.

The iPhone X is Apple at its most classic — they take away a key feature that seems odd at first, but usually, the change pans out in the end. So is the case for the long-lived Home button, whose last appearance may be on the iPhone 8 and 8 Plus. That begs the question — how do you use an iPhone without a Home button?

The first big update to iOS 11 since its release in mid-September just came out, so check your iPhone for a software update to iOS 11.1, because there are a few things you'll want from it. While there's no sight of Apple Pay Cash or Messages in iCloud, there are some significant improvements you'll need to know about.

The Pixel 2 has a number of new unique features. One of the most interesting is the Now Playing option to identify songs you hear on a daily basis. Now Playing displays the artist and title of songs playing in the background of your day and shows this information on the lock screen. While this functionality is incredibly useful, the song history is not saved anywhere on your phone.

If you were holding out on an iPhone X but still haven't bit the bullet on the $1,000+ price tag, it may be because you're not sure how it will feel in your hands compared to the iPhone 8 or iPhone 8 Plus, which are pretty much the same size as the last three iPhone models you know and love. We can help you figure this out, though, with a simple printout to compare phone sizes in your hand.

For those who enjoy the finer things in life, premium Scottish distillery The Macallan is bringing an augmented reality art gallery, viewable through the high-priced Microsoft HoloLens, to select cities in celebration of whisky season.

Last week, I tried out StackAR, a puzzle app updated to support ARKit where the AR features felt mostly unnecessary.

ARKit and ARCore generate excitement among various segments of the tech industry for spurring adoption of augmented reality with consumers via mobile devices.

When explaining augmented reality to the uninitiated, Pokémon Go is often cited as an example. For all its popularity, though, many players would recommend disabling the AR capabilities in catching Pokémon.

It's hard to believe iOS 11 was announced three months ago. In that time, we have downloaded multiple betas, experienced the Golden Master, and seen the new software in action on the iPhone X, iPhone 8, and iPhone 8 Plus. After all this waiting, however, the official release of iOS 11 and all its awesome new features, is finally here. Well, almost.

One of the byproducts of the success of Pokémon Go was the viral images that made the rounds on social media of people putting Pikachus, Charmanders, and their brethren in compromising positions. Snapchat has a similar claim to fame, most recently with the inexplicable popularity of the dancing hotdog.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

In June at the eMerge Americas investors conference, Magic Leap founder (and NR50 member) Rony Abovitz proclaimed that the launch of their flagship product was "not far away."

It's official! This year's iPhone release event is scheduled for September 12 at Apple's new campus.

CyberTimez and the Wounded Warrior Program, using the Vuzix M300 monocular smartglasses, are teaming up to help supply veterans with little to no sight. The overarching goal here is helping these injured service members to find a new level of independence in a sight driven world.

Advertisers must love when their commercials go viral. Take for instance the Esurance commercial where an elderly woman completely misunderstands Facebook jargon.