The Bridge tool in modo 202 is a phenomenal modeling tool for any workflow. This video will get you a quick ramp up to the full power of the Bridge tool in modo. The bridge tool allows seamless stitching between discontinuous areas of a mesh. See how to use it for any type of 3D modeling within modo.

Sow your wild oats! In this video, Jody Fath shares the expertise she gleaned from her eleven months backpacking around the world. In this video, you'll learn to plan for a long-term trip abroad. Learn how to determine what type of traveller you are, how to budget for your trip using online cost-of-living estimation and even how to pack in this great tutorial.

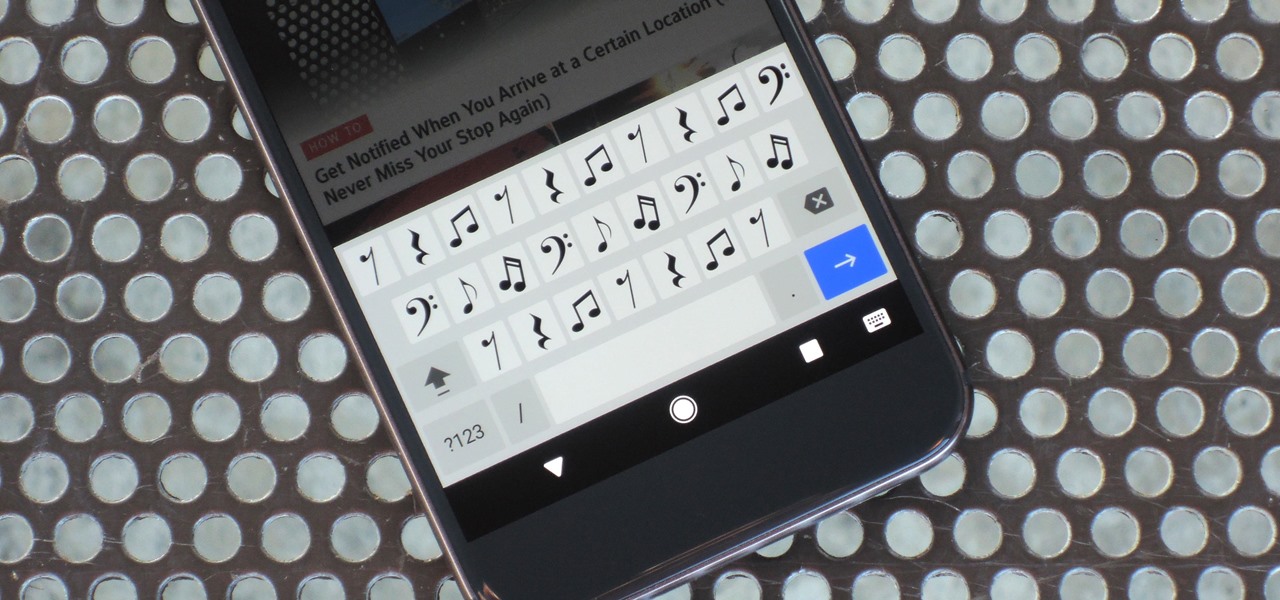
Watch this music how-to video to learn how to read musical notation or sight read. This instructional video is very detailed and includes types of notes, tempo, and the staff. Reading music will be easy once you've watched this helpful music notation tutorial video.
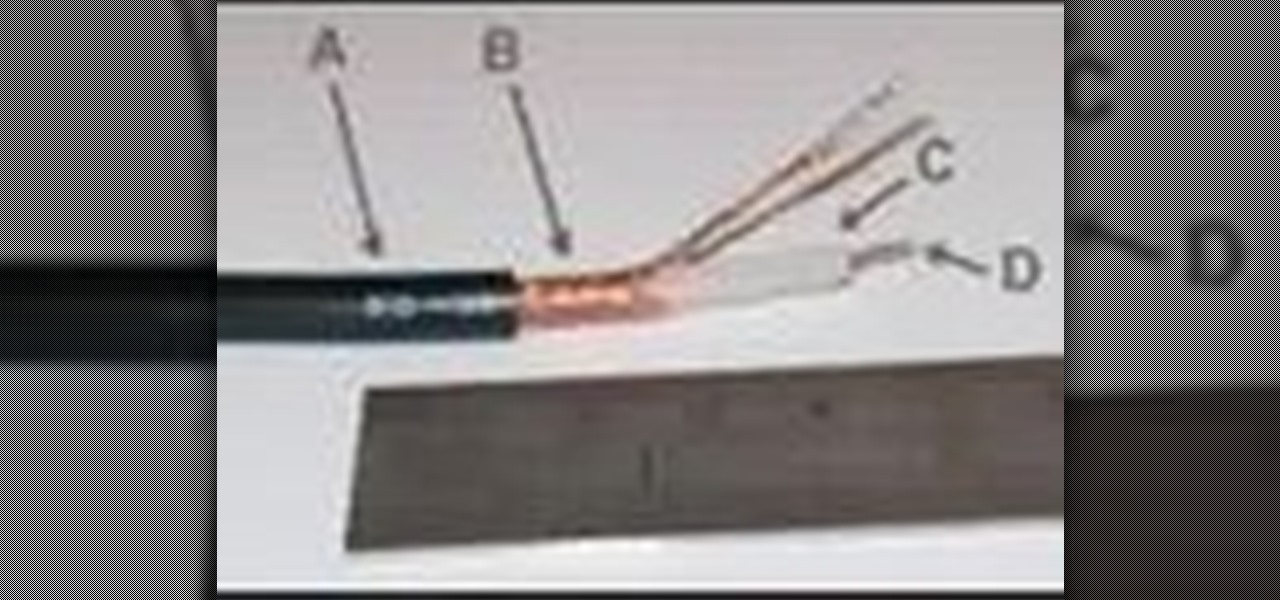
This video is about electrical wires. It describes common types, configurations of wire, and wire terminology. It explain the gauge system of rating wire size (diameter), circular mils, current capacity, and others.

52 year-old UniGeezer demonstrates four different types of drops with a Mountain Unicycle.

These techniques are important for playing any type of solo - here Charles Sedlak will show you how to do hammer-ons and pull-offs. And no, you don't actually need a hammer for this, and if you thought so, stop playing right now, put it down - you don't deserve that guitar of yours.

Choosing the right closet organizers can make organizing your closet a lot easier. So, Meghan Carter visited Master Simplifier and owner of the organization firm White Space, Cynthia Ivie, to discover which type of closet organizers work best.

Learn to restore four different types of files: deleted files, files from a damaged CD or DVD, files from a formatted hard drive, and files from unbootable hard drives.

We recycle cardboard, but Gomi Style is going to re-use the cardboard and create chairs with the fine found material. The gang at Gomi style made a two different types of chairs from tossed out cardboard, simple and easy

The dolly zoom shot is also known as the Vertigo Effect in filming. It's that dizzying, slightly unstable camera effect you see in shows like "Glee" and sometimes "The Office." It creates audience confusion, thus forcing them to keep watching in interest.

It doesn't matter what type of music you specialize in or plan to play because everyone needs to know how to strum. In this video Justin breaks down the process so well you'll be strumming rhythmically in no time!

This video is part of the grip it an rip it series with Tony Gwynn. Discussed is where to stand in the batters box, what type of bat to have, the proper stance, how to swing the bat and follow through. As Tony describes how to do each aspect of batting, he illustrates each one. Throughout the video, popups and sidebars appear with additional tips making it easy to understand.

For those of you who make paper airplanes, this video will show you different types of airplanes. From upgrading the basic paper plane, to showing you how to make the "tube plane" and "the swallow," Bre Pettis is obviously a paper airplane master.

Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

In this series of videos you'll learn how to draw with charcoal from a professional artist. Expert William Cotterell shows you what types of art supplies you'll need to get started, including various types of charcoal, compressed and pencil varieties, types of erasers that work best with charcoal, and the best types of paper for making charcoal drawings. He also shares tips for choosing a subject, understanding light, blending techniques, adding highlights, and using Fixatif to protect your w...

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

With the iPhone X, Apple introduced a brand new way for iOS users to interact with their iPhones. Gestures took the spotlight, as they very apparently replaced functions you would normally execute on the Home button. But swipes aren't everything for the new iPhone XS, XS Max, and XR. Don't believe us? Just take a look at the Side button.

It looks like the Huawei P20 Pro won't be the only phone with a triple camera for much longer. Rumors indicate the upcoming LG V40 ThinQ will share the same number of cameras. And just like with dual cameras, LG is showing that there is more than one way to arrange them.

The rumors are still hot that Apple might include an 18-watt USB Type-C power adapter with the upcoming iPhone lineup so that there's fast-charging capability right out of the box. Leaked photos have surfaced that substantiate this rumor, though, they could also be fake. But how would ditching the old-style 5-watt USB Type-A power cube affect you if it's true?

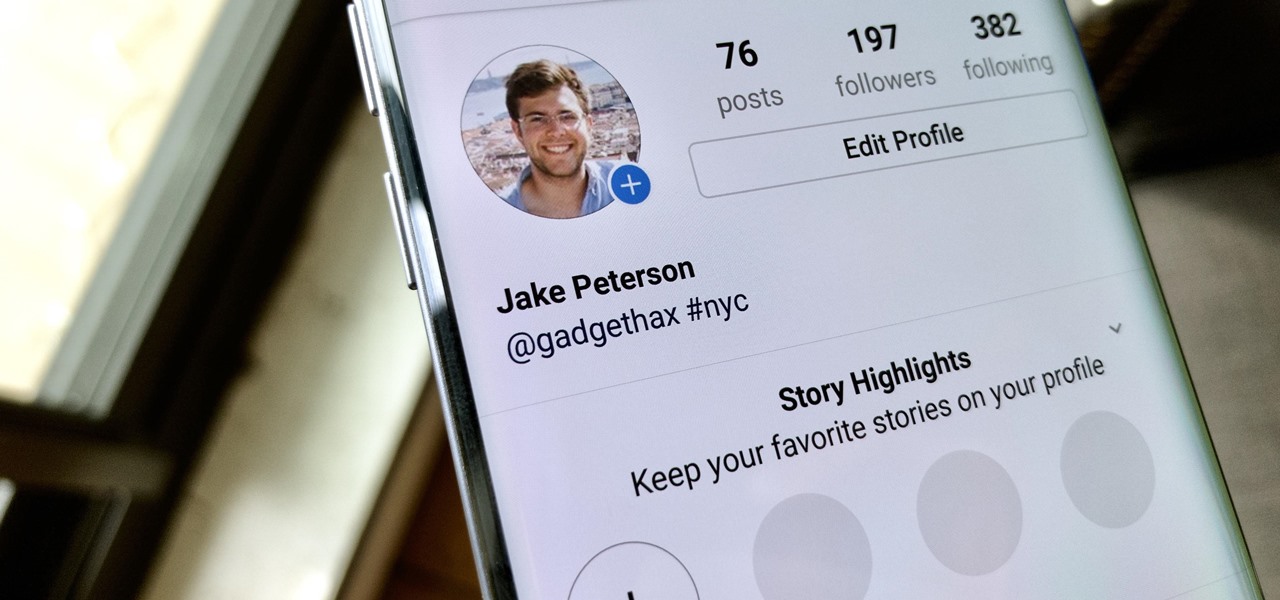
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

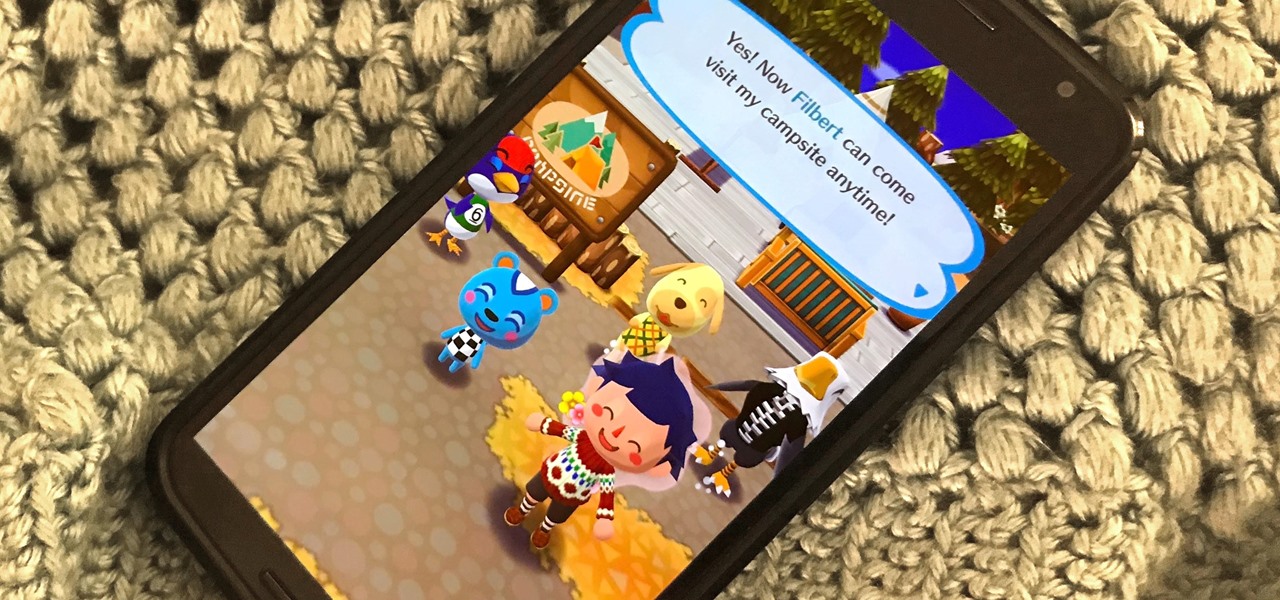
Friendship has always been a staple of Animal Crossing games, and Animal Crossing: Pocket Camp makes no exceptions. Check out this guide if you're interested in how to maximize time with your furry friends.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.

Kik is an extremely popular messaging app, but it has a few annoying features that we all just sort of put up with. You can't turn off read receipts, nor can you hide when you're typing, and the photos you take with Kik's camera show up differently than ones you send from your gallery app. At least a couple of these features should be subject to change, but they aren't — well, not without some tinkering.

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

Android is a highly customizable operating system. Sometimes, we use these capabilities to add core functionality or streamline the user experience, but there are other times when customization is just about having fun and making your smartphone's interface more enjoyable.

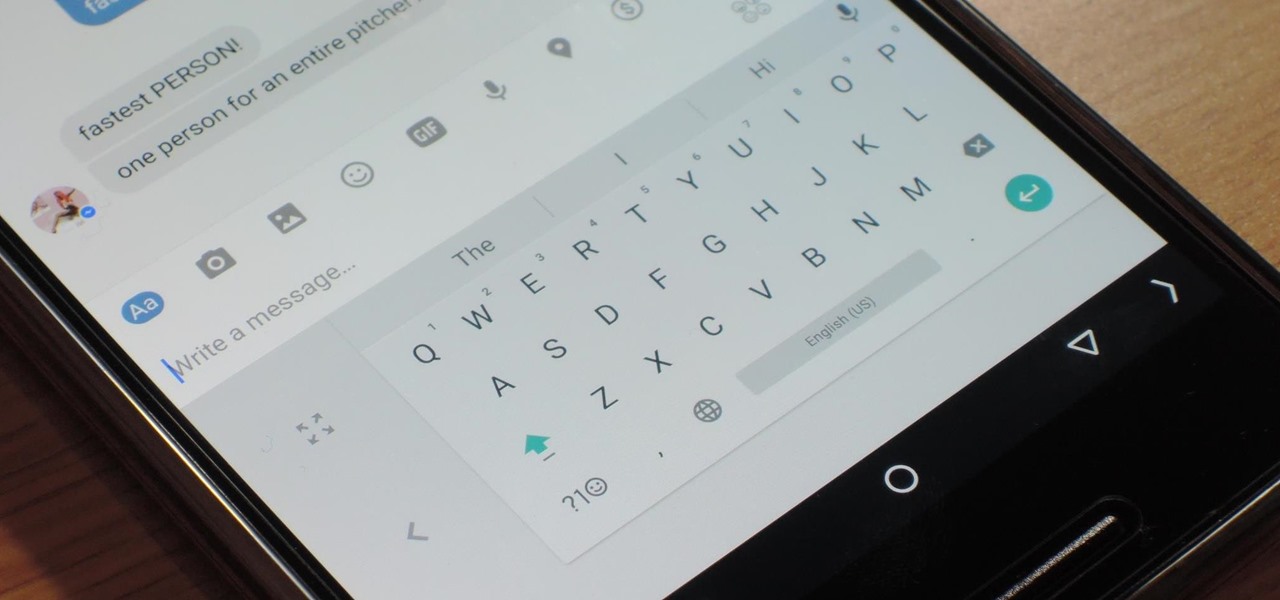
Google has added a number of new features in the latest update to Google Keyboard including a one-handed mode and a setting that lets you adjust the height of the keys. The update hasn't gone live on the Play Store yet, but you can download the APK right now for both 32-bit and 64-bit phones.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?