Katy Perry is a certified sensation, and if she inspires you to play the piano then she's done at least one good thing today. This video will teach you how to play her single "Teenage Dream" from the eponymous album. You can even check out the sheet music at the creators websites here.
Wish finding Greasemonkey scripts were easier? With the Greasefire Firefox addon, it's super easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

The internet has been a massive financial windfall for millions of people around the world, and it can be for you as well! There are a lot of ways to make money on your couch by using the internet, and this video will show you five great ways to do it! These include making websites and forums, advertising, and gambling. If you're hard up for cash, give it a whirl!

Last week, the Library of Congress decided that it was officially legal to jailbreak mobile devices. Now, days later, we finally have a jailbreak for the iPhone 4, and it might be the easiest such process ever conceived. This video will show you how you can go to one website and jailbreak your iPhone 4 or iPod Touch in about 30 seconds. Do it!

The browser on your Android-powered cell phone offers numerous features that enhance your overall web experience. Some of the great features include double-tapping to zoom in, searching for text on webpages, sharing websites with friends, and copying and pasting. There's a lot more, so watch this video tip from Google to see how to fully enjoy your web browser.

One of the many cool GUI effects that you can create on your website using jQuery is the slide effect, whereby information can cascade out from one item and the other items on the page will slide up or down automatically. This video will show you how to create slide effects with jQuery and little bit of CSS3.

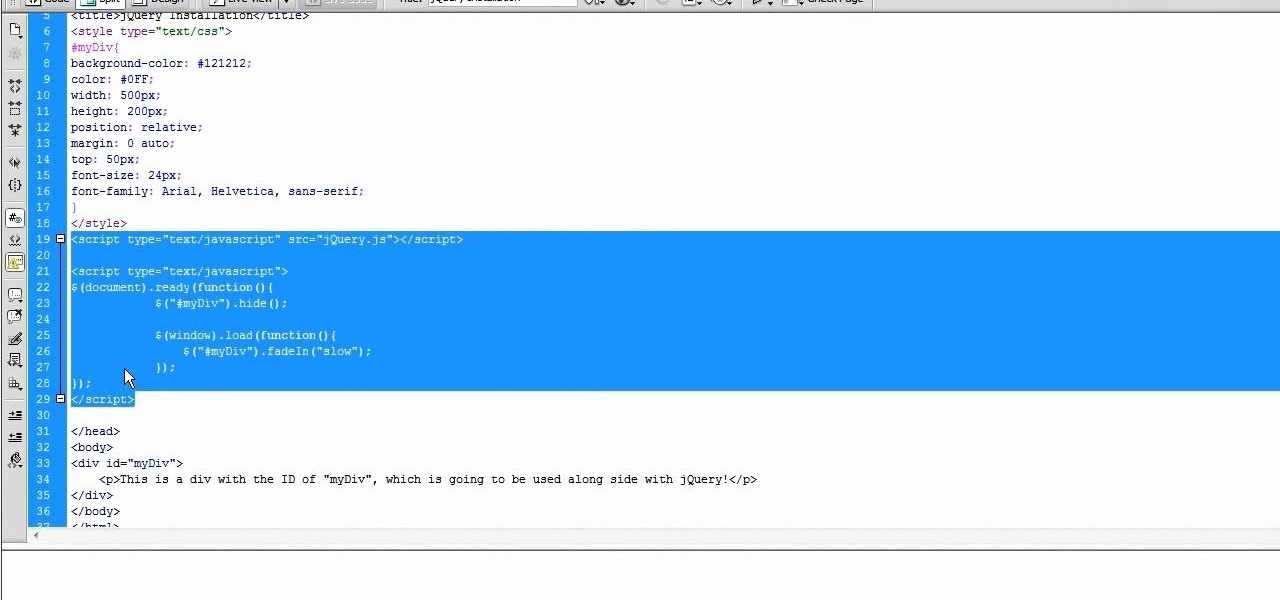
jQuery is a very powerful Javascript framework that makes making cool website interfaces much easier. This video will introduce you to the basics of using jQuery from installing it on your computer to creating your first simple element. You'll also learn the function methods that jQuery uses and how to inset jQuery into an HTML document.

Isn't it amazing how quickly children can learn how to use technology that seems completely incomprehensible to older people? Nowhere is that more evident than in this video. It features a 12-year-old prodigy explaining the ins and outs of using jQuery, the popular Javascript library, in web development. At over an hour in length, this video goes into great detail and should teach you everything you need to get up and running in jQuery.

With help from this free video tutorial, you'll learn how to style list items with CSS. Whether you're using a fancy WYSIWYG (or what-you-see-is-what-you-get) page editor like Adobe Dreamweaver CS5 or a barebones text editor like Notepad, if you want to build websites, you'll need to have some understanding of HTML (for the structure of your web pages) and CSS (for their style). And this free coder's guide will get you started along that path.

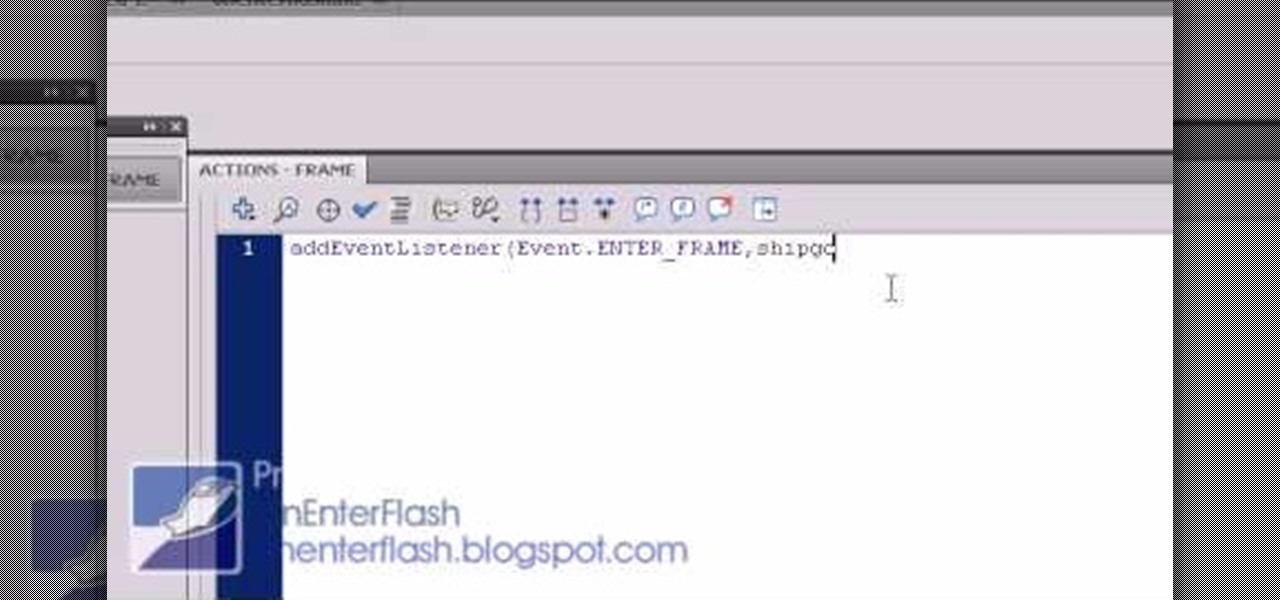
Scripting languages, like coding languages, are among the most complicated and daunting aspects of computer use to master. If you can do it, however, they allow you to do nearly anything you want with a computer. This video will introduce you to the popular scripting language Actionscript 3. This language is crucial to using Flash successfully to create games, movies, and websites, so get this stuff down and then go watch our other Actionscript tutorials!

Creating cool animations is the bread and butter of Flash. This video will help you get started making them yourself for your website, video game, or movie. It explains how to animate objects, making them move around however you wish and form the basis of your animation. No source files needed, just make some circles and get started!

Adobe apparently did not plan for it's AIR protocol to lead to people turning their websites into programs, but it turns out that it is fairly easy to do. This video tutorial explains in great detail how to create an AIR application using Flash CS4. Topics include how to create a digital signature and .swf files that you will need to create the program.

Looking for a guide on how to create icons for your website? With the Adobe Photoshop, it's easy. Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from Tutvid. For more information, and to get started creating navigation bar-style web icons yourself, watch this graphic designer's guide.

Need to insert a scrollable gallery of thumbnails into your website or web project? You've come to the right place. In this tutorial, learn how to build a scrolling thumbnails video and take it to the next level by building a fully functional gallery with a bonus randomizer button. Learn about using variables and rounding numbers and navigating time lines within a flash movie with actionscript.

Whether you're new to Adobe's Creative Suite (and, by consequence, Flash Catalyst CS5) or a seasoned graphic design professional after a general overview of CS5's most vital new features, you're sure to be well served by this official video tutorial from the folks at Adobe TV. In it, you'll learn how to make transitions for your websites or rich internet applications using Flash Catalyst.

This simple tutorial takes you through the process of creating a widget from any list of videos from http://www.WonderHowTo.com. These customizable widgets can be created in various sizes and colors and then added to your blog or website. Enjoy.

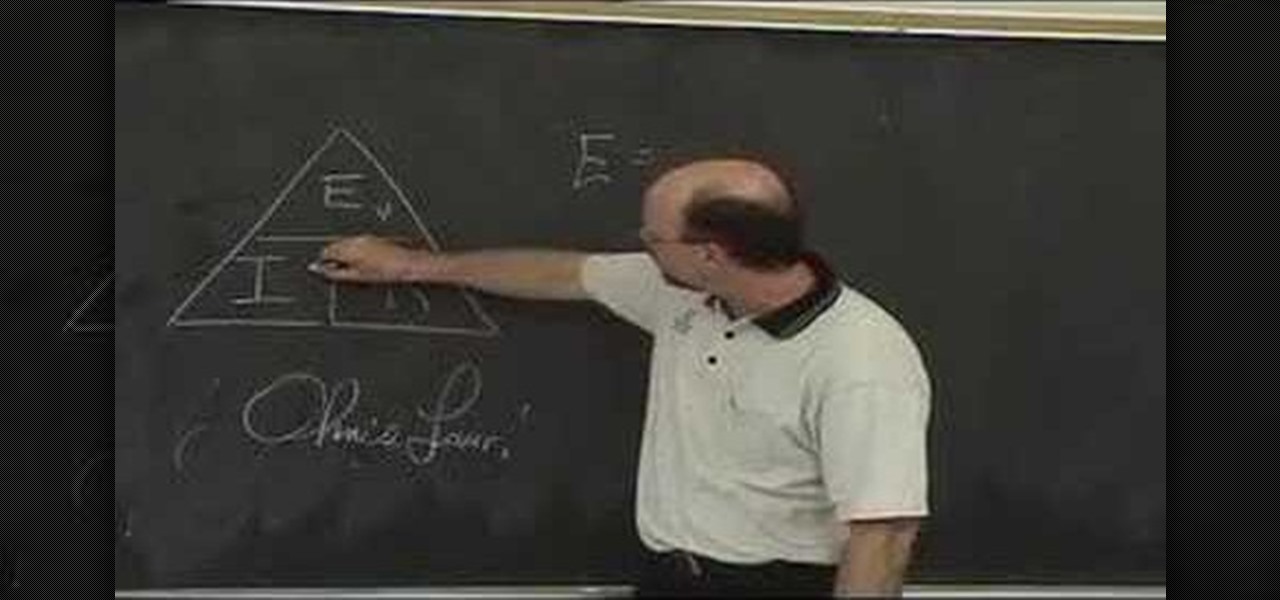
Watch this educational how to video to review Ohm's Law. This math and physics concept is derived from electric motive forces, intensity of current flow and resistance values of conductor. Watch and learn more about Ohm's Law.

When creating an aesthetically pleasing image, sometimes more is more. Blending images together and blurring the edges is a great method for creating desktops featuring multiple photos of hottie Sam Worthington, or simply for creating a pretty website background.

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

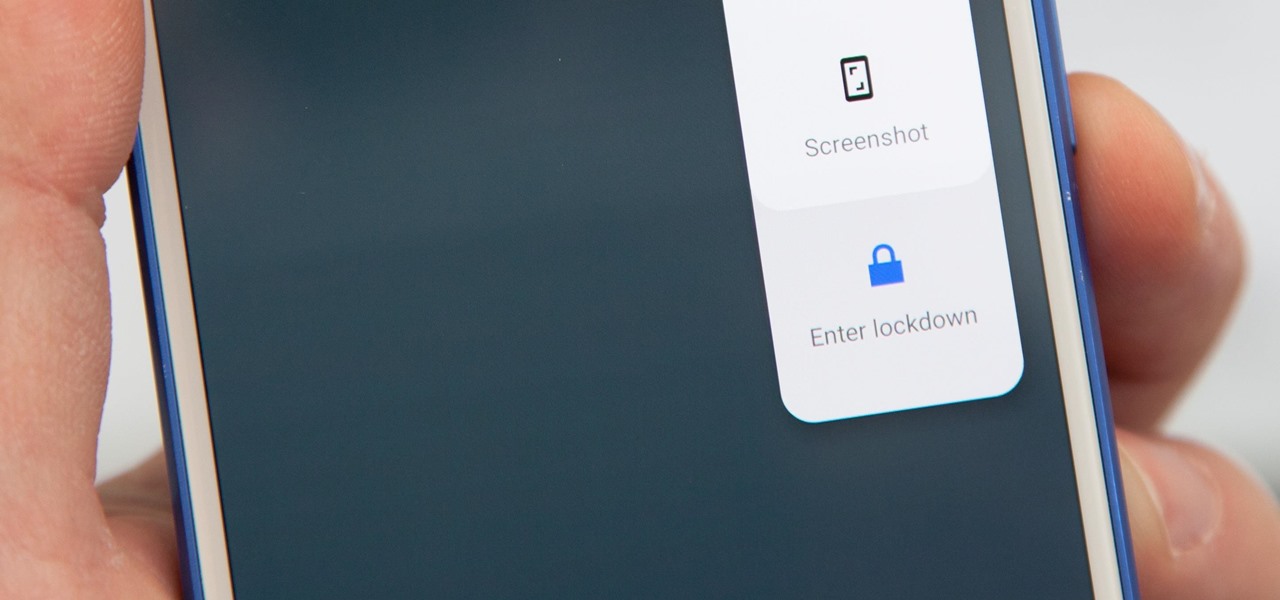
Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Patent holder Genedics, LLC has filed a legal complaint alleging that hand-tracking startup Leap Motion is infringing on its intellectual property.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The internet is full of fun, cool, and interesting websites. Bookmarks and favorites can help keep your favorite pages on hand, but they aren't the most convenient method. In iOS, Apple lets you save whatever webpages that you want to the home screen, so you'll have as easy access to them just as you do apps on your iPhone.

Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Having websites coded for mobile browsing is great for small screens, but if you have a Plus model iPhone or even the iPhone X, desktop versions of websites might show you more of what you want. Plus, there's the case of poorly designed mobile websites, where the desktop view is clearly the better option with more functionality and features. Luckily, asking for desktop sites in Safari is simple.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Update: August 1, 2014 Earlier today, President Obama signed into law the Unlocking Consumer Choice and Wireless Competition Act, making the act of unlocking your unsubsidized cell phone 100% legal.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.