
How To: Inject Payload into Softwares via HTTP
Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory


Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop shoots an unarmed person, the police officer involved in this particular shooting is currently in jail, facing a potential murder charge.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

This tutorial is for everyone who has been waiting for a solution to stream web videos to a Chromecast by using an iPhone or iPad. It is easy as a cakewalk.
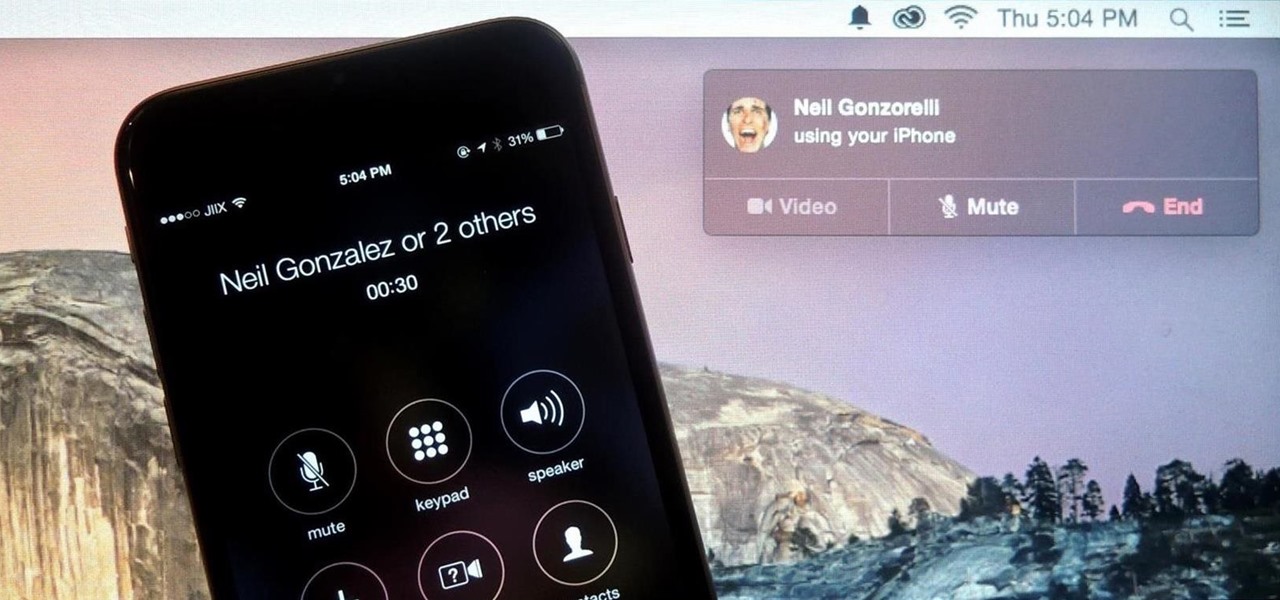
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

After about 3 weeks of working on it, I finally finished my Cookie Clicker! It's a concept that has been done before by sethbling and others, but I wanted to try and make something closer to the original since one of my subscribers asked me to. I think I delivered! Check my website for a download link (linked)

Every year, some overly ambitious neighbor down the street amazes the crowds with his DIY illusion costume. While these costumes certainly require more work than pulling a mask over your head, they do have that wow factor that others lack.

One day I was contemplating about a canard paper airplane design. After several attempts, here is what I got - the Eurofighter Paper Airplane.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

Welcome back, my greenhorn hackers!

Video: . How to Dye Weave Extensions Easy!!

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.

While the legality of secretly recording phone calls varies in each country, sometimes it's useful to have audio documentation of conversations you have on your Samsung Galaxy Note 2.

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

Website Design Tutorial for Xara Web Designer - graphics folder in designs gallery. In this web design tutorial learn how to add various graphics, modify colors and remix images to create your own custom icons or logos. The web design tutorial will put some of the concepts you learned in previous web design tutorials to practical real world use. If you need assistance using Xara Web Designer let us know and we will do our best to create web design tutorials to help you.

The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers.

As we all know, our attention spans are much shorter now that we're accustomed to getting information and news in tiny snippets via text messages, tweets, instagrams, and other constant updates.
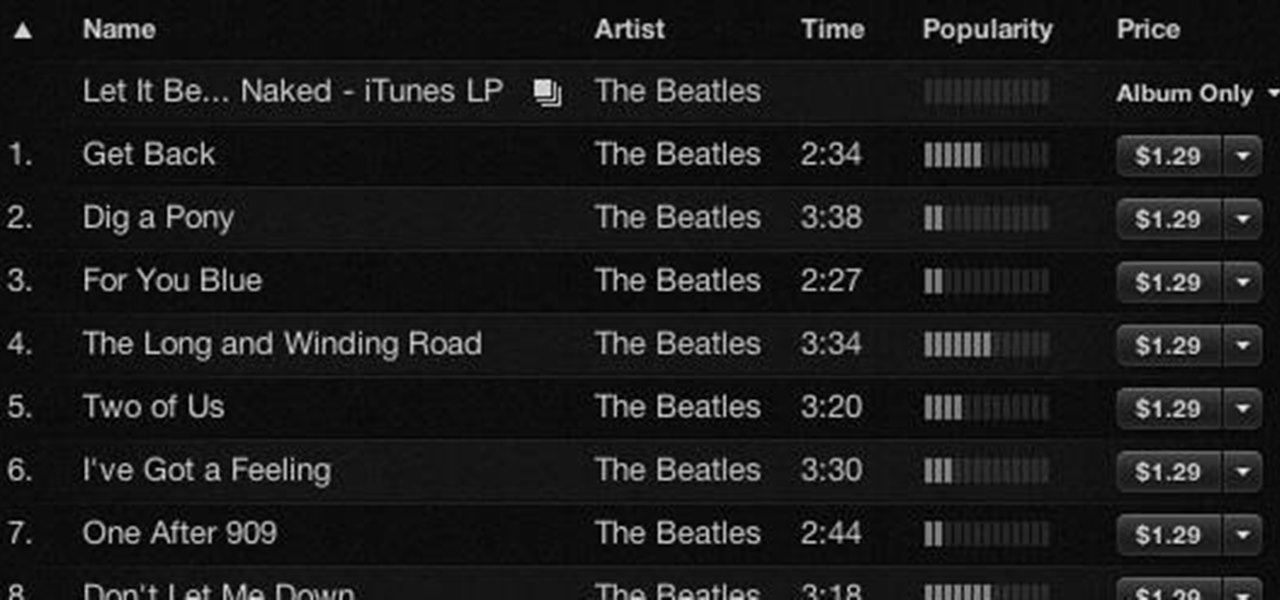
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

In this web design tutorial learn to create and delete layers. This web design tutorial for Xara Web Designer also covers deleting pages, deleting objects on different layers and re-arranging layers that have objects on them. A brief discussion about MouseOff Layer and MouseOver layer is also introduced in this Xara Tutorial. I would say this is one of the single most important Xara Web Designer Tutorials because layers allow you to do so many unique things with your website within Xara Web D...

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

First of all I am glad that I was able to find this website and become part of it. So far I love it. Recently Playstation created a competition where a person has to show how online gaming is good. Pretty simple right? You can enter with an image or a video, however I do not think that an image can really show the fun of online gaming. I have created a video which does show some of the good parts of online gaming and I also tried to keep it fun. I would really appreciate if you would have a l...

In this web design tutorial learn how to use the shape tool. In This Web Design tutorial for Xara Web Designer you will learn how to create straight and curved lines and smooth and cusp joins. Also this Xara Tutorial covers deleting and breaking nodes apart on a given line. The shape tool will allow you to make custom shapes and objects to give your website a creative boost.

Use the Xara Web Designer 7 Premium Mould tool to mould, re-shape and change perspectives of objects. The Xara Web Designer Mould tool will allow you to create some very interesting effects to make your website stand-out and have depth. Even the thumbnail shown for this web design video tutorial was created with the envelope tool. If you have ever seen the software boxes shown on various those are usually created with an envelope tool to give the box its perspective.

The upcoming web series "Crypto-Historians" does for cryptohistory what Indiana Jones did for archaeology. For those who don't know, cryptohistory is the study of supernatural or alien elements throughout history, and yes—it's a "real" field.

Earlier today, a meteorite flew over the Chelyabinsk region of Russia, triggering a shock wave that injured hundreds of people and caused damage to buildings and vehicles in the area. Witnesses describe seeing a bright ball of light streak through the sky followed by a loud boom as the 10-ton meteorite entered the Earth's atmosphere and exploded.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

This is a super cute girly pink punk nail design that is done in the backdrop of pink and black gradient - ombre nail art style!

Want to add cool, colorful effects to your photos without paying for filters or using Photoshop? A cheap glass prism (and some practice) is all you need to bend the light to capture images like the ones below taken by wedding photographer Sam Hurd. Sam uses a six inch triangular prism to catch the light and reflect images in front of his lens. The shape allows you to "twist the prism into creating a curve and bend-like distortion of your surroundings," which can create rainbow effects and mir...

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.