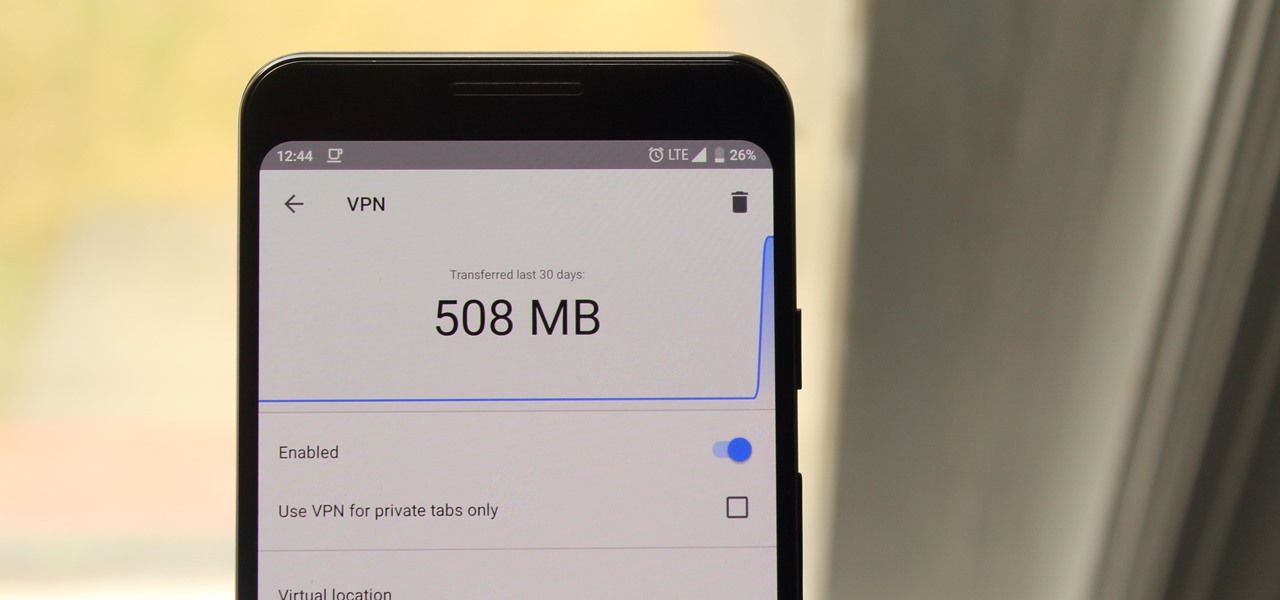
Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

Pushups are a great workout. But if you think you're ready to take it to the next level, you should consider incorporating backback pushups into your workout. The added weight will give your muscles added strength and give an exciting new take on a simple exercise.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

Felt food is a great substitute for unsafe toys for children. A real life mom gives tips in this video on how to create great felt food that her children absolutely love playing with! The instructions are easy: Use wool or wool-blend felt instead of craft felt; it feels nicer. The first thing you need to do is cut out the felt patters provided on the website. You will need a red half circle, and a four pointed star. Seeds can be added by tying French knots using white thread. The next step is...

If you ever wondered how to create a buy now button for your website this video shows how to do it using Photoshop. To do this open Photoshop and start with a new file. First draw a rectangle which will be now modified into the buy now button. Set the radius of the rectangle to forty pixels. Fill it with gray color. Duplicate the layer. Open the layer options of the duplicated layer and set the stroke position option to inside. Set its weight to 6 pixels and set its colors to light gray. Now ...
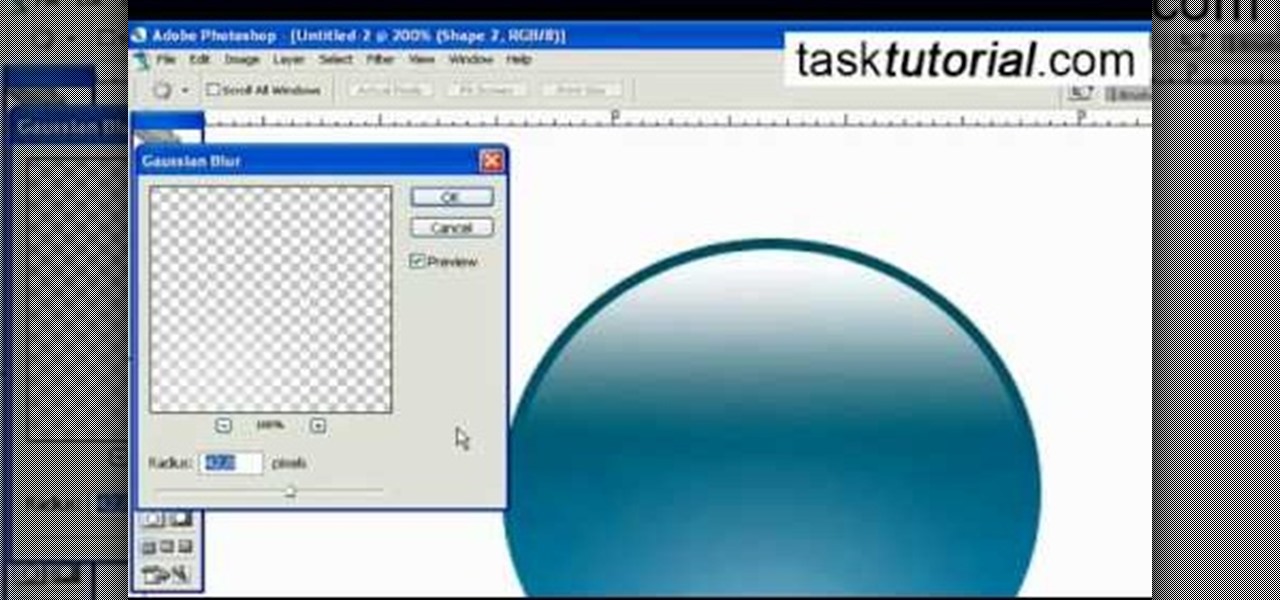
This video describes how to create an easy glossy button in Photoshop. This is done by "simpleretouch.com" website. First select the "Ellipse Tool" from the Photoshop tool bar and then drag it on the layer; it will give the ellipse shape in the layer. Select the "Blending options" from the "Layers" Menu by double click on the layer which is right below corner. From the blending options choose only the "Gradient Overlay" and in that we can choose color and its gradient as your wish. Now take a...

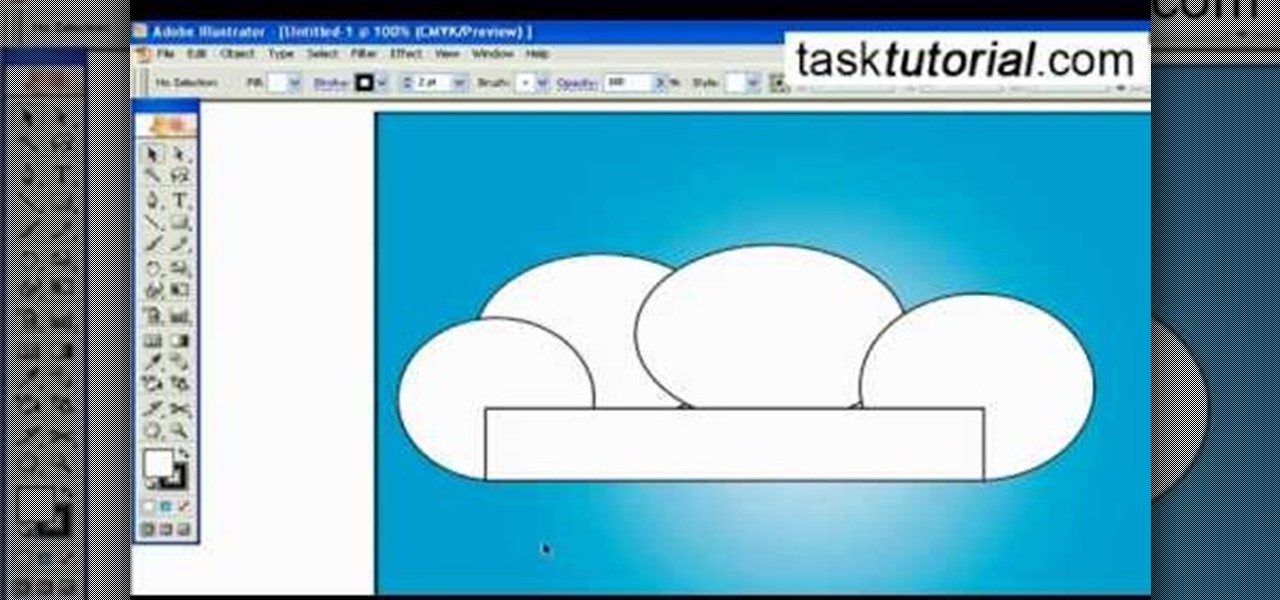
A great free video training from tasktutorial on how to create a cartoon cloud in Adobe Illustrator. All the project files are available to download for free at the Adobe website. First create a background: select the rectangle tool then create a new layer and draw a rectangle across the canvas. Now select the path, go to gradient and edit the it a bit until it's a shade of blue. Lock the gradient and create a new layer. Select white fill color and 2 point black stroke and draw a few oval sha...

Purchase a silver XBox 360 faceplate from your local gaming retailer. You can also remove the faceplate currently on your XBox 360.

This video demonstrates how to make a holiday punch needle ornament. First choose an ornament design and fit cross stitch fabric to a small embroidery hoop. There are designs on the CyberSeams website that can be traced onto the fabric. Put the fabric with the traced design into the embroidery hoop, thread the needle, dial it to "2", and begin punching the needle through the fabric to make the design. You can choose embellishments that can be sewed or glued on. When the design is finished, re...

Learn how to get a great rockabilly hairstyle. •First of all, curl up the hair using the le Angelique curls which are available in Pretty Choice and the link for which is available in the side bar. • And then use another curling iron which is also available in the same website and the information is also available in the side bar. •And then pin up the hair in such a way that it is closest to the forehead by finger styling just for the way it has to look. •And then she uses some bumble and bum...

Looking to fix your iPhone home button? Do you have a broken HOME button on your iPhone? In this video, learn how to get around it with an application called "mquickdo", formerly known as iHome for jailbroken iPhones. This also works for iPhone 1G or 2G and iPod 1G or 2G. Mquickdo allows you to use a series of finger swipes to function as the home button. This includes putting your iPod to sleep, going back to the home page, the double tap music menu, exiting an application, and more.

There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermitereaction.

In this tutorial, we learn how to use torrent software like uTorrent. First, go to the website, Burn OSX, and download their software, then install it. After this, go to isohunt. When you get to this website, type in the name of the item you are searching for. When you find it, click on it and it will start to download through uTorrent. When finished, you will be able to open up what you downloaded and then use it how you wish. It will then start seeding, which means that it is being shared w...

In order to bypass Megavideo and Veoh's viewing time limits you will first need Mozilla Firefox. To download Mozilla Firefox then go to Firefox and download the Mozilla Firefox browser. After downloading the browser you will need to install the add-ons. Go to the website Illumitux add-on in order to download the add on Illimitux, after downloading the add on then Mozilla will prompt you to close the browser window. Go ahead and close the window then re-open it. When you re-open it Mozilla wil...

Apple announced support for mobile driver's licenses and state identification cards in Apple Wallet back in 2021, and Arizona was the first state to jump on board in 2022. Fast forward to now, and only eight states let you add a driver's license or state ID to Apple Wallet on your iPhone and Apple Watch. It has been a slow rollout, but more states are coming or are at least showing interest.

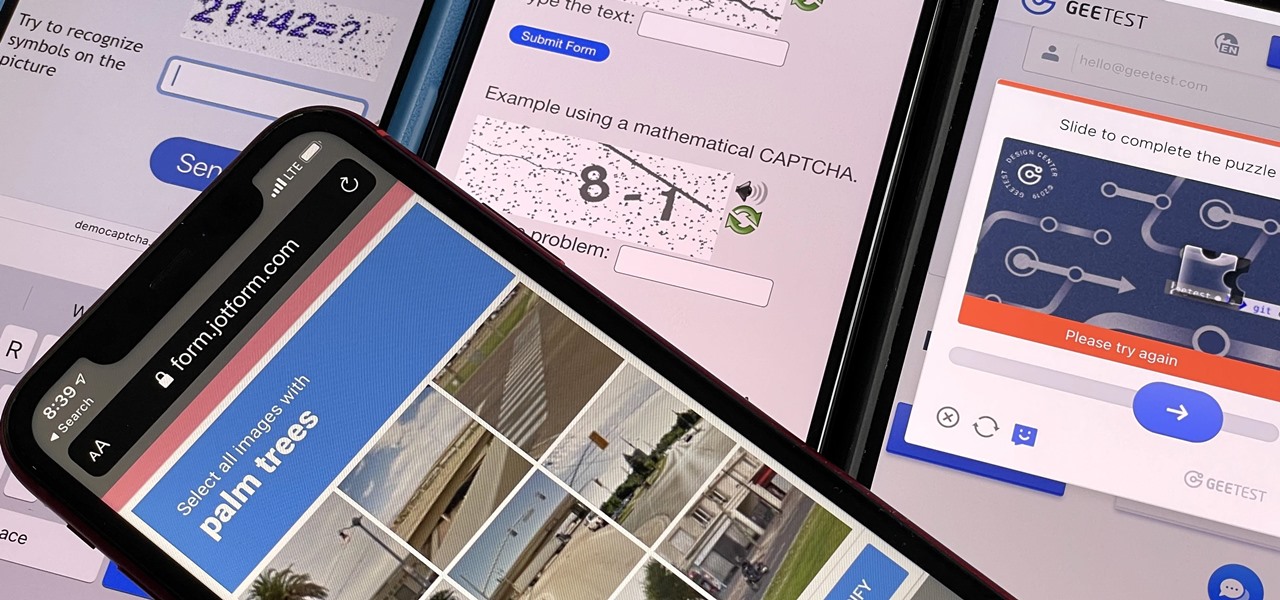
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

The Unity 3D engine is not only responsible for facilitating the creation of 60% of AR and VR content but it also plays a significant role in producing the immersive stories that increasingly push the boundaries of cinema.

The 15-year-old star of the 1980s-inspired hit series Stranger Things, Millie Bobby Brown, may have (spoiler alert) lost all her powers as the character "Eleven," but in the real world, she still has augmented reality in her arsenal.

Apple revealed its newest line of iPhone models on Tuesday, Sept. 10, at its "by innovation only" event in Cupertino. While the release date for iOS 13 wasn't announced at the event, Apple issued a press release with the date. If you missed the event, you can still watch it from your computer, smartphone, Apple TV, and any other device that YouTube works on.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

As promised with its teaser from Build 2019, Microsoft has unveiled the details for its augmented reality version of Minecraft for smartphones.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

One the leading game developers for the PlayStation 4 and Oculus Rift platforms, Insomniac Games, is finally releasing its first major augmented reality title: Seedling for the Magic Leap One.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

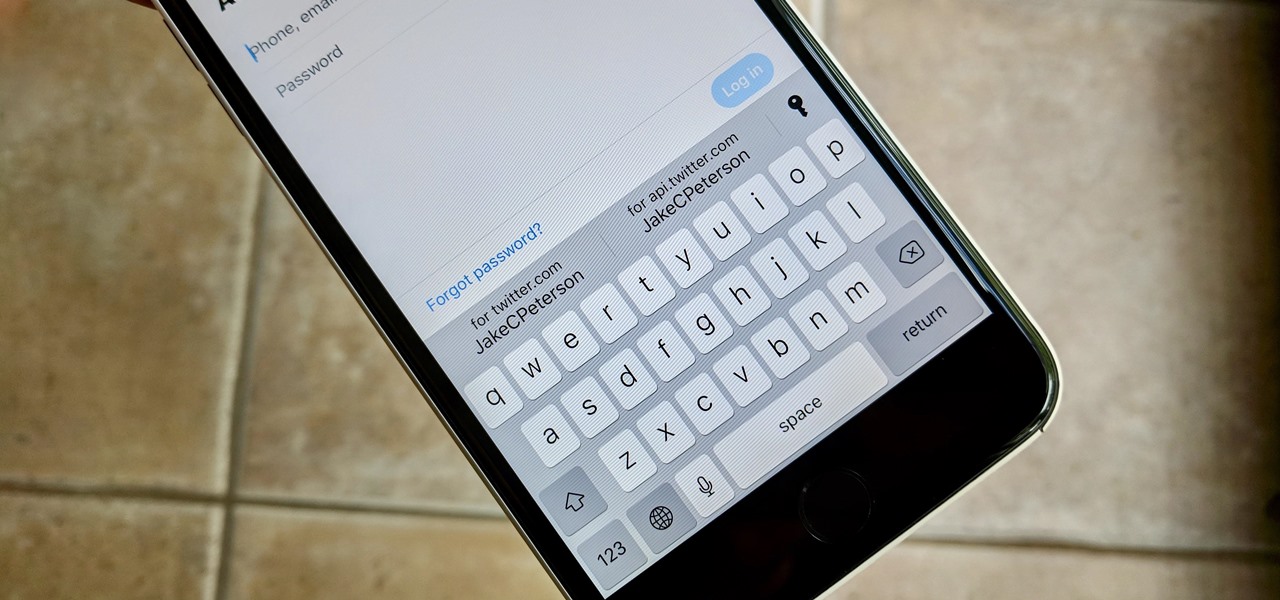
Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.